Source of Funds | A Critical Step in Mitigating the Risk of Money Laundering

As the world continues on a path of digitization, business operations persist to undergo significant transformations; simultaneously, this digital advancement has paved the way for more advanced means for criminals to commit and conceal sources of illegal income. Businesses’ incompetence in determining the source of funds is becoming the driving force behind the increased risk of money laundering and terrorist financing.
Identifying and understanding where the customers have obtained the money being used to make payments of investments is an integral part of the Know Your Customer (KYC) and AML compliance program, which is an essential component of restricting fraudsters. As money launderers use increasingly complex methodologies to hide the source of ill-gotten money, businesses must practice rigid anti-money laundering checks to establish the sources of funds.
Generally speaking, this means that your business needs to implement a myriad of KYC and AML screening measures, including customer due diligence, enhanced due diligence, transaction monitoring, ongoing monitoring and more – to ensure customers’ assets and data privacy concerns stay intact while contributing to the global fight against money laundering and terrorist financing.
What is a Source of Funds (SOF)?
Source of funds refers to the origin of earnings used in a transaction. It is closely related to the account utilized to initiate a payment and the source of money placed in that account. Companies need to put transaction verification checks in place relating to the source of funds to ensure that the customers are not converting their illicit gains or funding terrorist activities. This is one of the many essential steps businesses must practice to meet the EU’s Sixth Anti-Money Laundering Directive obligation.
However, determining the source of funds can be complex, specifically when transactions are carried out via shell or offshore companies. In these instances, companies must dig deep to comply with AML standards, developing facts ranging from how the company’s financial workflow works, who are the beneficial owners and where they invest finances.
Despite the complexities in establishing the source of funds, companies need to have rigid verification checks at their disposal that are enough to determine the source of funds as well as to meet AML obligations. However, failure to cope with these situations could lead to legal proceedings, hefty fines, sanctions and reputational damages.
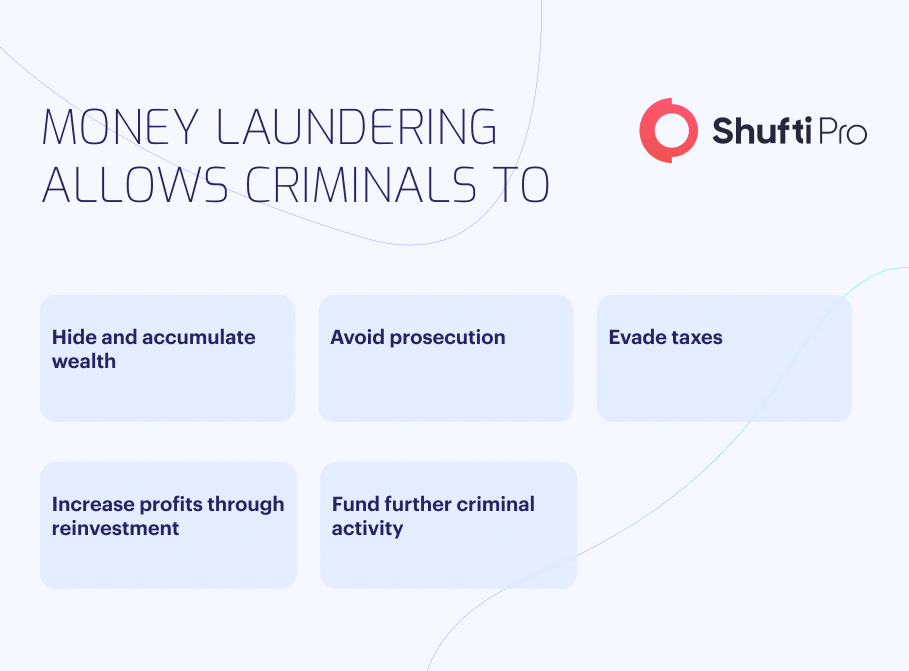
Why are SOFs Important?
Source of fund checks plays a critical role in the fight against money laundering, terrorist financing and other financial crimes since it helps businesses determine the red flags, ensuring the customers are involved in criminal activities. Source of funds is an essential yet neglected part of anti-money laundering recommendations legislated by the Financial Action Task Force (FATF). SOF is also a key component of the KYC compliance program, which comes under the enhanced due diligence approach, in which businesses are obliged to determine the source of transactions and check if it’s linked with crimes. While these are regulatory benefits, SOFs hold the potential to help any business. Ensuring that customers’ transactions are sourced from legitimate routes can safeguard businesses while limiting the risk of money laundering.
Diving deep, SOF can provide companies’ internal compliance teams with a clear picture of customers’ risk profiles, helping them investigate proceeds of crimes and suspicious activities while making informed decisions. In a context where the SOF doesn’t match the client’s risk profiles or established transaction activities, businesses are required to utilize the information to inform regulatory authorities while submitting suspicious activity reports.
An AML source of funds check includes the following parameters:
- Source of funds checks should be implemented, aligning them with customer risk profiles. Meanwhile, a greater level of due diligence must be applied to high-risk entities.
- To make SOF investigation effective, businesses need to collect additional documents as proof, an essential step in explaining customers’ involvement in criminal activities.
- The client bank statements should be analyzed to aid SOF enquiry.
However, one thing should always be kept in mind: not every suspicious transaction and financial dealing requires SOF investigation, and financial watchdogs do not recommend carrying out the process for every suspicious incident. The Australian Transaction Reports and Analysis Centre (AUSTRAC) states that the discrepancies in customer identification procedures may be better handled by triggering enhanced due diligence rather than undergoing SOF checks.
How to Conduct SOF Checks
It’s suggested that businesses take a risk-based approach to determine the source of funds. Companies can secure their resources by developing and considering customers’ risk profiles without implementing burdensome requirements on risk-free clients. For instance, politically exposed persons and high-net-worth entities are subject to more intensive SOF checks as they pose a more significant risk.
To do so is to determine if the finances used in the transactions came from a legitimate source or have suspicious patterns leading to money laundering. Often, SOF checks are triggered if the customer’s transaction exceeds a pre-defined threshold, such as carrying out transactions of more than $100,000 or multiple small transactions in a short period. These are some scenarios in which the transactions are potentially suspicious and linked with money laundering. Launching a source of fund checks can fuel investigation and effectively determine the authenticity of financial dealings.
Businesses can ask customers a series of questions to verify their source of funds, including financial documentation, proof of investments, past financial dealings and identity documents.
Regulatory Obligation to Establish Source Of Funds
To develop an effective program to determine the source of funds, businesses need to establish and implement appropriate know-your-customer checks to understand better who their customers are and what type of business activities they are involved in. Under the FATF’s AML risk-based approach recommendations, KYC measures must be proportionate to the level of risk customers pose. This means high-risk entities are subject to enhanced KYC and AML checks, while clients with lower-risk levels should undergo simplified due diligence.
The following essential components should be part of a KYC process:
- Customer Due Diligence: businesses must establish protocols to verify their customers’ identities in order to determine the risk they pose while making an informed decision about their source of funds. To do so, companies can request additional documents or information, including name, bank statements, date of birth, etc. Companies should also undergo the necessary steps to establish the link between customers and beneficial owners.
- Transaction Monitoring: companies need to monitor customers’ transactions and financial activities inconsistent with developed sources of funds. Firms need to stay vigilant to identify suspicious volumes or patterns in financial dealing, mainly originating from high-risk countries.
- Sanctions Screening: businesses need to screen their customers against sanction lists to ensure that they are not onboarding entities that are subject to international sanctions.
- Politically Exposed Persons (PEPs): elected government officials are exposed to money laundering risks, and businesses are obliged to assess their source of funds with greater scrutiny. Therefore, firms need to screen such clients rigidly in order to establish PEP status. In addition to this, businesses need to verify the close associates and family members of such entities.
Final Thoughts
In today’s complex regulatory regime, understanding and establishing sources of funds plays an indispensable role in safeguarding businesses’ as well as individuals’ integrity. However, it may appear as just another regulatory hurdle, but it’s crucial in identifying and curbing financial crimes while keeping an eye on high-risk financial dealings.
Shufti, a leading identity verification and anti-money laundering screening service provider, understands the importance of establishing the source of funds in fighting financial crimes. The company offers KYC and AML screening solutions across 240+ countries and territories, helping businesses worldwide meet regulatory obligations while ensuring risk-free operations.
By integrating our solutions, your business can easily establish the source of funds, monitor customers’ transactions, create clients’ risk profiles and report crimes to designated regulatory authorities – all under one platform. And whatnot, your firm can access a 1700+ watchlist, rendering 99% accurate screening results.
Want to learn more about how Shufti can help you meet compliance and fight fraud?

 Explore Now
Explore Now













