Two-Factor Authentication – A Firewall Against Social Engineering Attacks

Businesses and financial institutions around the globe often report concerns of financial crimes being initiated by the exploitation and manipulation of sensitive information. As per recent trends, a significant spike in fraudulent transactions and account openings was indicated, a majority of which were sourced by social engineering. With criminal entities using sophisticated techniques for gaining access to confidential information, firms are showing an increase in susceptibility to cybercrime.
Taking full advantage of the COVID-19 situation and remote business operations, cybercrimes in 2021 topped the charts with a total of 5,258 data breaches. Social engineering attacks are seen targeting the loopholes and technical vulnerabilities in digital platforms of businesses and financial institutions to extract confidential data for use in illicit activities. Social engineering cyber crimes such as phishing attacks in the form of Business Email Compromise (BECs) and spear-phishing are almost 80% effective in breaching sensitive data and causing financial losses to businesses.
How Secure is Two-Factor Authentication?
Two-factor authentication provides an additional layer of security to protect online business accounts. Since 2FA requires an additional code apart from the username and password, it is quite secure in restricting access to sensitive information. In case of hacked passwords, 2FA filters out criminals by requiring a code sent via email or mobile number.
A staggering 6.95 million web pages were created in 2020 for phishing, with the IT and the financial sectors being among the commonly targeted industries. Greece and Romania experienced a rise in social engineering attacks, but the top countries where these scams are prevalent are Russia, the US, and the British Virgin Isles. Moreover, fraudulent bank account openings in European countries saw an increase of 1.4% in the last year.

Adverse Effects of Social Engineering on Businesses
Company addresses and uniquely identifiable information of legitimate businesses are used in socially engineered attacks to make the emails appear important. Since slight alterations in characters are often ignored in business communication via email, these phishing attacks are usually successful in getting access to sensitive data. These advanced criminal tactics result in decreased productivity for businesses, as well as financial losses through fraudulent transactions. Apart from dealing with these problems, businesses have to invest additional amounts for recovery from damages. Although businesses usually recover from the monetary losses due to social engineering attacks and even pay the recovery costs, the permanent stain on their reputation adversely affects businesses for years to come.
Companies struggle to rebuild the lost trust of their customers and partners once a cyberattack disrupts their business. That being said, getting new customers also becomes significantly difficult for businesses that become part of the headlines for having become the victims of data breaches. For these reasons, businesses now strive to improve their security measures through two-factor authentication instead of focusing solely on providing services. Business meetings, transaction details, collaborations, and internal communications are sensitive records that fraudsters aim to access through socially engineered cyberattacks. When companies invest in recovering from data losses, there are not only additional financial implications but also significant productivity gaps.
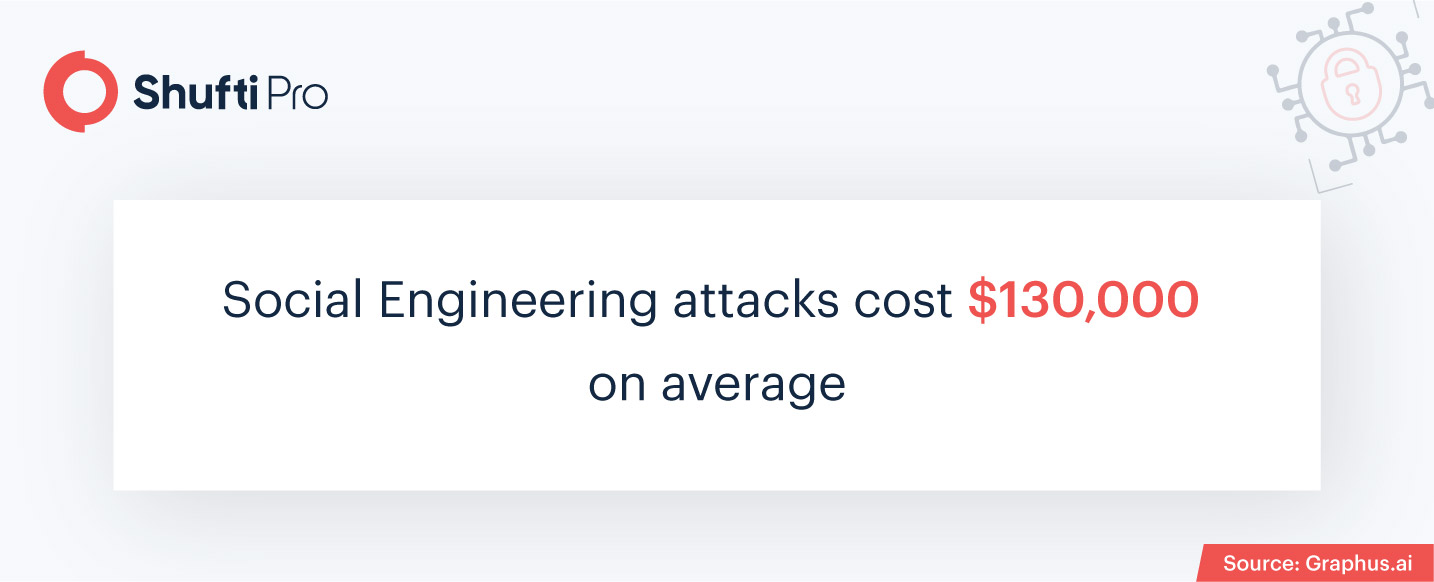
Compliance Penalties Adding to Financial Losses
The already prominent issue of financial losses due to social engineering was further augmented with the COVID pandemic, where remote business operations empowered fraudsters with techniques to overcome verification measures. The lack of digital identity verification solutions has resulted in the intrusion of fraudulent entities in businesses, which consequently leads them to financial losses and compliance penalties. The same is the case with phishing attacks, where firms have to pay KYC/AML compliance fines as a result of data breaches and monetary losses. The 2021 LinkedIn data breach not only affected businesses due to exposed information but also sparked new social engineering attacks. With over one billion records sold on the Darkweb, cybercriminals were handed data to carry out new spear-phishing attacks.
Speaking of the overall increase in cybercrimes, statistics show that more or less 4000 cybercrimes are committed every day. Furthermore, new techniques of social engineering like Whaling target the upper tier of business employees, effectively manipulating millions of the company’s valuable funds. When it comes to recovery costs, there are additional amounts of AML compliance fines, which add up to a global cost of over $213 billion. It takes companies weeks and months to identify social engineering attacks, and in most cases, they learn about it when it’s already too late.
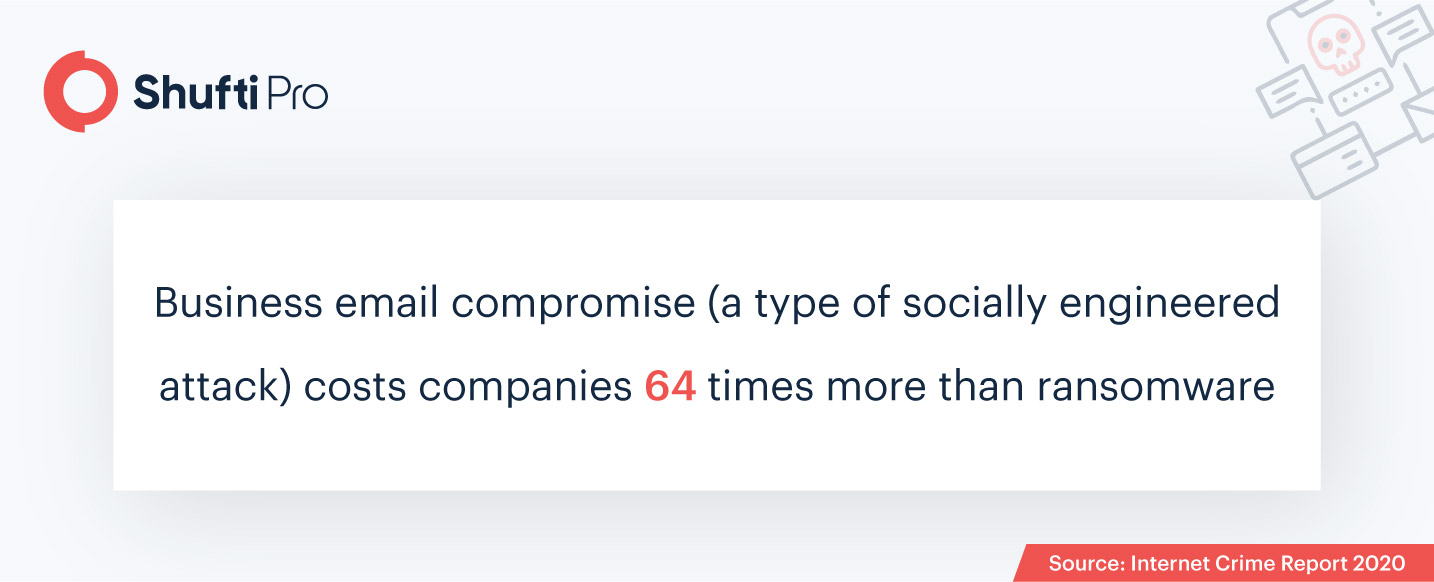
Prevention of Social Engineering Attacks
Business Email Compromise (BEC) is the most commonly used type of phishing attack, with losses adding up to $1.8 billion in 2020. These attacks compromise business and vendor emails to rake in money, and are reported to convert the illegally obtained funds to cryptocurrency to avoid getting traced. In order to combat these damaging cyberattacks, businesses implement two-step verification measures for authorizing access to business account information and other sensitive credentials.
In this scenario, the ‘prevention is better than cure’ strategy can come in handy. Instead of paying incident response teams after they become victims of a phishing scam, businesses must initially secure their communication mediums by incorporating two-factor verification. Ultimately, the battle against financial fraud can only be won when businesses also empower their digital platforms with technology-driven authentication solutions and level the playing field.
How Two-Factor Authentication Solves the Problem
With the losses due to financial crime soaring up to $60 million in 2020, staying one step ahead of cybercriminals has become essential for businesses. Two-factor authentication is a solution to secure business communications through emails and other platforms in order to protect confidential information from data breaches. 2FA enables businesses to eliminate fraud and overcome social engineering attacks by incorporating an additional requirement of a one-time code. These authentication solutions enable businesses to detect fraudulent activity beforehand and protect their financial assets as well as their reputation from being damaged.
This auto-generated random code, usually comprising four characters, is sent via registered email or SMS, allowing only the legitimate personnel to log in. Security departments in organizations must be encouraged to enable 2FA for all internal and external business communication, including emails and the particular applications being used within the workplace. In the cases where credentials are obtained by cybercriminals through phishing, smishing, or whaling, the additional code requirement stops them in their tracks.
The Bottom Line
To wrap it up, the looming threats of social engineering attacks targeting technological weak links in digital business platforms call for improvements in security measures. Cybercriminals getting access to intelligent techniques for automation and hacking have resulted in the loss of sensitive data, causing businesses to shut down. Shufti offers two-factor authentication for the protection of business accounts and keeps company information from getting into the wrong hands.
Learn more about the applications of two-factor authentication in business!

 Explore Now
Explore Now













