Understanding the Key Role of Risk Assessment in the Crypto Industry

Cryptocurrencies are becoming a hotspot for scammers to perpetrate financial crime. Over 46,000 individuals have lost more than $1 billion to crypto fraud since 2021. To avoid unintentionally facilitating illegal practices within the industry, it is vital to establish robust systems, controls, and procedures. This is where the significance of cryptocurrency risk assessment becomes evident.
Conducting a thorough risk assessment is an essential procedure that enables organisations to proactively recognise and address potential vulnerabilities, allocate resources efficiently, and protect against financial crime risks in cryptocurrencies.
Financial Crime Risk Categories
- Customer Risk: Gain insight into customer risk by examining the types and volumes of transactions. Risk profiles can be assessed at both the individual and cluster levels, where clusters refer to groups of addresses associated with customers.
- Product Risk: Analyse the risk associated with particular crypto assets, considering factors like the secure storage of private keys or facilitating transfers.
- Transaction Risk: Analyse blockchain data to determine transaction risks. Whilst the information for cryptocurrencies like Bitcoin is readily accessible, obtaining transaction details for others like Monero may present challenges.
- Geographical Risk: Check the geographic factors linked to the client’s location or the operating base of particular exchanges or cryptocurrencies.
- Delivery Channel Risk: Assess the risk associated with various delivery channels, such as digital platforms and crypto ATM providers.
An Example of Crypto Risk Assessment
Consider a situation where a customer becomes a scam victim and uses cryptocurrencies for fraudulent payments. Due to the prevalence of cryptocurrency scams, this scenario’s probability is relatively high. The impact can be categorised as moderate.
Subsequently, the inherent risk of this scenario needs to be calculated. Assuming it is assessed as a medium risk, it becomes essential for firms to be cautious of it and have robust systems to prevent such incidents. Security controls may involve collecting customer data and implementing transaction monitoring rules and limits.
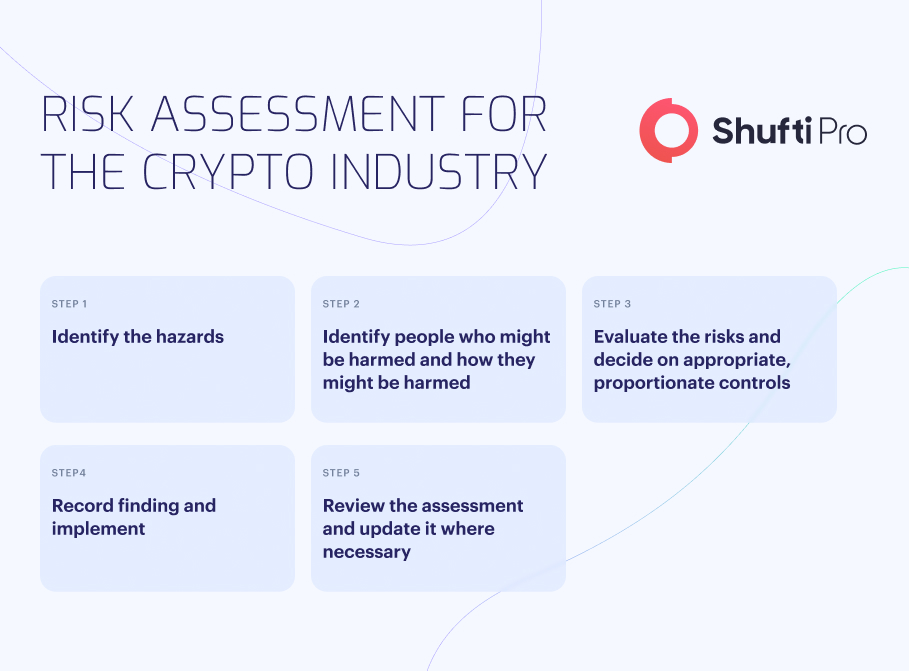
Key Elements of Risk Assessments
Once the primary areas of risk are identified, there are several things to consider during the risk assessment procedure:
- Specificity: Ensure that the risk discussed in the assessment is specific to the business and aligns with its anti-financial crime framework. Customising the evaluation as per your organisation’s need guarantees relevance and effectiveness.
- Format: Present the risk assessment in a logical and coherent format. Tools such as Excel spreadsheets help document risk calculations and stress areas of concern. This approach facilitates tracking and aids regulators in comprehending the assessment.
- Scenario Analysis: Evaluate financial crime risks in various scenarios by checking the probability of risks and their impact on the business. This assessment provides the current threats and facilitates prioritising mitigation efforts.
- Controls Assessment: It is essential to address the controls implemented to mitigate risks and evaluate their effectiveness. Merely stating that any company have systems in place is inadequate if they are not robust enough to reduce the identified risks.
Types of Risk Assessments
Risk assessments are conducted regularly at different intervals, including annual assessments, ad-hoc assessments, or continuous monitoring of customers.
Here are the common types of risk assessments:
- Enterprise Risk Assessments: These are conducted annually, and the goal is to identify risk categories like system risks, operational risks, cyber security risks, fraud risks, HR risks, and regulatory risks. Each category is further analysed to determine the specific level of exposure.
- Financial Crime Risk Assessments: These assessments are conducted annually and primarily focus on analysing money laundering risks. They closely examine customer geography, customer types, products offered, and distribution channels.
- Customer Risk Assessments: This assessment involves calculating customer risk scores based on various criteria, including geography, customer type, customer activity, and transaction history in blockchain or cryptocurrencies.
Benefits of Risk Assessments
Risk assessments offer numerous advantages to the cryptocurrency industry:
- Identifying Vulnerabilities: Risk assessments identify potential vulnerabilities, enabling proactive measures to address them before any civil, regulatory, or criminal scrutiny occurs. Understanding how criminals exploit specific products or services is crucial in preventing illicit activities.
- Resource Planning: One can choose the necessary mitigating controls once vulnerabilities are determined. This risk-based approach allows for formulating effective strategies and appropriately allocating scarce resources. Questions like “Which solutions are worth investing in?” and “What skills do AML analysts require?” help optimise resource allocation.
- Development Strategy: Growth and innovation are constant pursuits in the evolving crypto sector. Risk assessments guide decision-making, like analysing which new coins to list on exchanges. Leveraging insights from risk assessments supports organisational development efforts.
- Continual Dialogue: To create practical risk assessments, it is essential to have continuous discussions and include input and feedback from senior management, auditors, consultants, and stakeholders. This ongoing dialogue helps gather valuable insights and ensures the risk assessment process is comprehensive and well-informed.
Crypto Regulations in the US
Federal Law
The Financial Crimes Enforcement Network (FinCEN) classifies cryptocurrency exchanges as Money Services Businesses (MSBs) and considers them covered financial institutions under the Bank Secrecy Act. Federal law does not mandate MSBs, such as crypto exchanges, to perform an AML Risk Assessment. However, FinCEN encourages MSB management to document a Risk Assessment to establish a clear foundation for the MSB’s policies and procedures.
Demonstrating a “risk-based programme” becomes challenging without conducting an AML Risk Assessment. Moreover, FinCEN’s “September 2020 Advanced Notice of Proposed Rulemaking (ANPRM)” suggests the establishment of a requirement for all covered financial firms to maintain an “effective and reasonably designed” AML programme. This includes performing a written AML risk assessment as proof of an efficient and well-designed programme. When regulatory authorities identify deficiencies, AML Risk Assessments are frequently referenced in enforcement actions.
New York Law
Understanding the regulatory landscape in New York is crucial, as it is the only state in the US that mandates cryptocurrency exchanges to obtain a BitLicense. New York Law (23 CRR-NY 200.15) mandates crypto exchanges to conduct an AML risk assessment. Section B of CRR-NY 200.15 specifies that licensees must perform additional assessments annually or more frequently to adapt to changing risks and modify their AML programs accordingly.
The New York Department of Financial Services (NYDFS) urges firms to assess their inherent risk and have specific controls, including:
- Strengthening Know Your Customer (KYC) customer identification and verification controls.
- Conducting transaction monitoring to detect and analyse on-chain activity.
- Conducting sanctions screening to identify any on-chain activity subject to sanctions or restrictions.
Crypto Regulations in the UK
“The Money Laundering, Terrorist Financing and Transfer of Funds (Information on the Payer) Regulations 2017” (MLR) are the principal regulations outlining AML requirements and registration obligations in the UK. It has undergone various amendments to incorporate the EU’s Anti Money Laundering Directive 5 (AMLD5) in 2019 and the Travel Rule in 2022.
Moreover, the following laws may also apply depending on the nature and type of assets that a crypto firm handles:
- The Financial Services and Markets Act 2000 (FSMA) and the Financial Services and Markets Act 2000 (Regulated Activities) Order 2001 (RAO).
- The Electronic Money Regulations 2011 (EMRs) or the Payment Services Regulations 2017 (PSRs).
How Can Shufti Help?
Shufti offers a risk assessment solution to 230+ countries and territories that determine high-risk customers whilst complying with KYC and AML compliance regulations.
Here’s what makes Shufti’s risk assessment solution stand out:
- Swift 99.3% accurate verification
- 17+ IDV services, trusted globally
- User-Centric and Developer-Friendly UI
- Screening from 1700+ watchlists
- Regulatory-compliant solution
- Supports 10,000+ ID documents
Still confused about how risk assessment helps the crypto sector keep scammers away?











