Risk Assessment – Helping Businesses Determine High-Risk Customers

The 2008 financial crash was a pivotal event in shedding light on the detrimental impact of lacking strong internal controls to limit exposure to external risks.
Fortunately, today, companies are increasingly focused on developing a viable risk assessment protocol to measure exposure to risks and contain unavoidable situations before they happen.
Over the last few years, financial watchdogs have also started pressuring financial institutions, cryptocurrency exchanges, and payment gateways to maintain adequate and sustainable model risk management programmes.
A well-executed risk assessment digs into real-world risks and the specific controls an institution uses to mitigate their impact, allowing the board and management to make better, more insightful decisions.
This blog aims to highlight the risks associated with the financial sector and how banks can use risk assessment procedures and processes to overcome these challenges.
Why are Organisations Prone to Fraud Risks?
Covid-19 served as a catalyst for digital transformation, especially in the sectors of banking and wider finance, hacking techniques have further digitised and evolved to bypass such security measures.
Many organisations lack significant risk management frameworks despite growing cyber threats and ever-growing levels of fraud.
Unreliable risk assessments can harm an institution by providing inaccurate information. This usually occurs when:
- Risk assessment processes aren’t consistent across the organisation, leading to varying definitions of risk in each department and more potential risk exposure.
- Employees fail to identify potential risks because they fear it will negatively affect their performance.
- Employees don’t know what the risk parameters are.
- There is no ongoing process or reliable checkup to ensure that risk controls are valid throughout the risk lifecycle.
Misunderstanding Risk Assessments
Risk Assessment is often treated by businesses as a one-off event, followed by implementation of a solution gathered from the amassed data, and no further steps are taken- risk assessment should be a continuous process that correlates with ever-changing fraud dynamics.
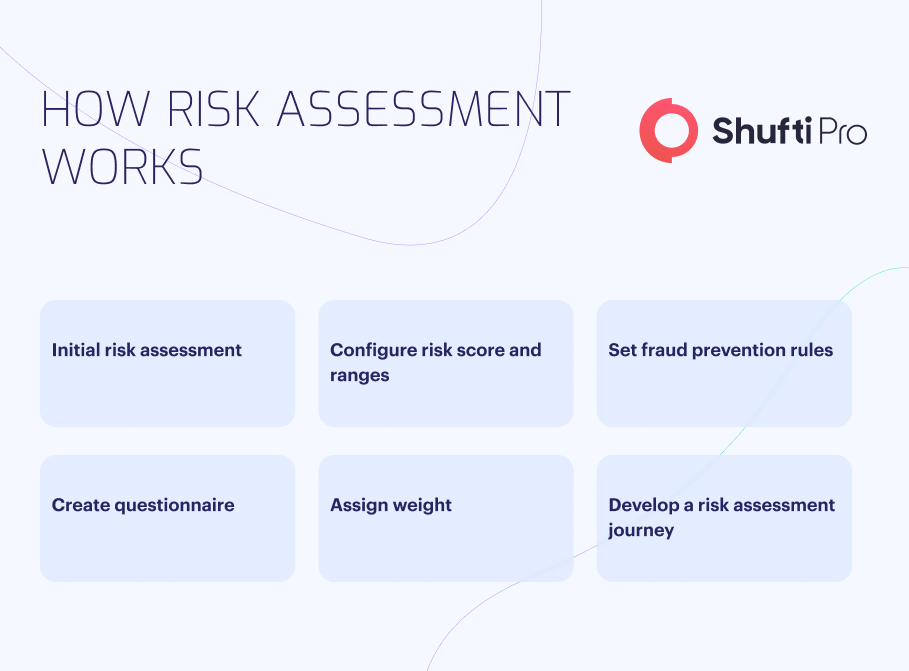
What is the Risk Assessment Process?
1. Risk Identification
Every institute faces its own risks and challenges, however they must ensure appropriate stat strategies are implemented to detect and mitigate such issues before reputational damages (and/or sanctions and fines) are incurred.
Here are some common types of risks that businesses can categorise:
- Breach of data resulting from cybersecurity
- Compliance risk
- Inherent risk
- Concentration risk
Think globally about the broad range of things that can go wrong at institutions of a similar size and type. A mid-sized community institution shouldn’t necessarily compare itself to a multi-national organisation, nor should it rely exclusively only on its own experiences. The guidance from federal regulators and the FFIEC can help guide this process.
2. Risk Evaluations
The evaluation process is an essential part of risk assessment, whereby the organisation will compare the results of the current risk analysis with the internally developed risk criteria. This shall act as a guide to help you take the necessary action on your part, such as:
- Take no action
- Treat risks accordingly
- Return to your internal risk assessment to gain further understanding
Risk profiling
It is also critical to conduct a thorough risk profiling of your users (individuals and businesses) to be sure you are not affiliated with any sanctioned individuals or organisations.
Utilise a number of omnichannel parameters as data points to perform customer checks and determine a score which will identify how risky it is to work with that entity.
The data points that businesses can collect are:
- Email address
- IP Address
- Phone Number
- Bin Lookup
- Transactional data
How to Develop a Customer Risk Profile?
You can verify potential new customers with the assistance of risk scores based on the personal information provided. Select numerous checks to prevent fraud, create customised risk questionnaires, and configure journeys for consumers with Low, Medium, High, and Prohibited risk levels.
The four components of conducting an in-depth risk assessment:
- Setting up risk ranges
- Fraud prevention checks
- Customised questionnaires
- Setting up the customised verification journey
Evaluate Customer’s Risk Aspects
Evaluating customers’ risk aspects can be done through email, phone number, IP address and behaviour. Set your customised scores to meet your business requirements.
Filter out invalid email addresses and dummy accounts that are not part of your company’s mailing lists
IP Address
Identify and match the IP address of a potential customer to verify their respective area & jurisdiction
Phone Number
Verify area codes and phone extensions to track your customers’ location and prevent sim-swapping fraud
Velocity
Refine risk scores based on the number of successful/failed verification attempts in a given time
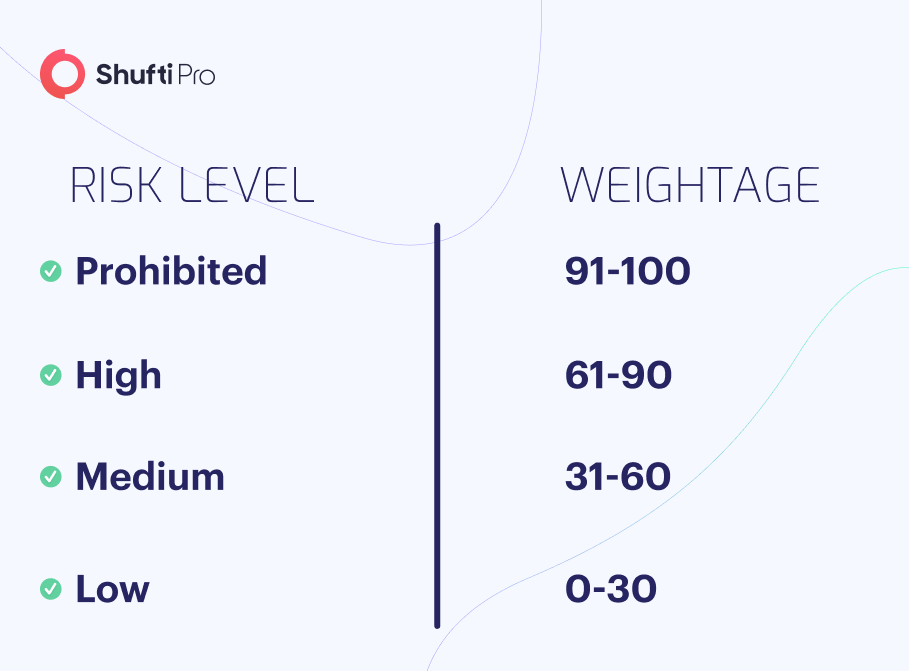
The risk calculations are dependent on the data the end-user provides, let’s assess this in further detail The following table lists the risk level alongside their assigned weightage, this is the weightage that businesses can specify for each risk level. A high and prohibited risk level is above 60 and 90.
3. Risk Treatment
Once risks are identified and assessed, an institution needs to understand those risks. It should consider various options for mitigation and settlement of a plan.
The plan should identify risk owners, typically departments or business processes. There also needs to be a risk manager tasked with remediation and implementation under a specific timeframe.
The institution should also consider establishing an early warning system using Key Risk Indicators (KRIs) and other regulatory monitored ratios or data so it is aware of when risks are evolving.
4. Ongoing Risk Monitoring and Review
Identifying, treating and evaluating risks is just one part of the strategy. Companies need to monitor risk continuously and have mitigation strategies in place to remain compliant with stringent AML regulations.
For example, politically exposed persons, people with influential power and links to the government, government officials, and politicians, should be reviewed for any potential risk on an ongoing basis.
The only thing permanent in today’s world is change, rapidly evolving to the ever-growing dynamics of the threat landscape is vital to remain compliant with strict AML laws.
High-risk clients pose a threat to businesses and hence should be checked regularly against the AML sanctions lists. Here are some benefits of ongoing risk assessments:
- Reduce your risk of dealing with a high-risk customer
- Remain compliant with KYC and AML laws
Steps to Strengthen Fraud Risk Assessment
Fraudsters and cybercriminals continuously change their tactics to remain one step ahead of businesses and governments. Once a method stops working, scammers will continue looking for new ones. The only way to combat fraud is if companies remain resilient and adapt to change as the only solution for risk assessment.
As such, organisations cannot and should not lay down their guard to manage risks. Companies need to regularly:
- Assess existing vulnerabilities and loopholes in the system
- Use internal controls for performance evaluation
- Induct experts from outside the organisation for a neutral vulnerability assessment
- Test risk assessment plans
- Educate employees for ongoing risk assessments
Conclusion
Although AI-based KYC solutions have managed to detect and mitigate fraudulent attempts, fraudsters will leave no stone turned to utilise sophisticated scamming techniques.
As such, we can say that fraud will not wither away anytime soon. However, legislation must continue tightening the screw on KYC and AML compliance. Businesses need to act now to ensure the following:
- Identify risks appropriately
- Have strategies in place to mitigate fraud
- Consider risk assessment as an essential component of ongoing KYC
- Have demonstrated ability in the implementation of the risk management framework
Shufti’s fraud risk assessment solution is built with your business in mind. Our forensic and anti-fraud experts help you create a customised score that aligns with your business goals and objectives. Shufti helps companies remain compliant and tightly grip their risk assessment protocols.
Need to know more about our risk assessment solution?











