Breaking the KYC Remediation Cycle through a Risk-based Approach

Banks have paid more than USD 30 billion over the past few years due to ineffective policies to combat criminal activities. Furthermore, AML breach scandals add to the costs, which is why nearly every country has launched a stringent approach to KYC/AML enforcement. As a result, banks and FIs are once again stuck with large KYC and CDD backlogs. Why does the finance sector encounter all these issues anyway? One of the major reasons is the scale of tasks like collecting, validating and regularly updating the information of millions of customers. It is not only time-consuming, but complying with frequently changing regulations is another obstacle. In addition to this, organizations have numerous inefficiencies in the customer onboarding processes that often lead to challenges in KYC remediation and ultimately, the need for reliance on regular reviews increases.
In this blog, we are going to discuss the traditional KYC remediation cycle that must be broken to improve the process, combat criminal activities and ensure effective compliance with the changing regulatory landscape.
What is KYC Remediation?
KYC remediation refers to getting rid of inaccurate customer information that financial institutions might have ignored for years. In other words, KYC remediation is the process through which organizations acquire customer information, conduct risk assessments and update client profiles. The process allows businesses to identify the risk elements associated with a customer.
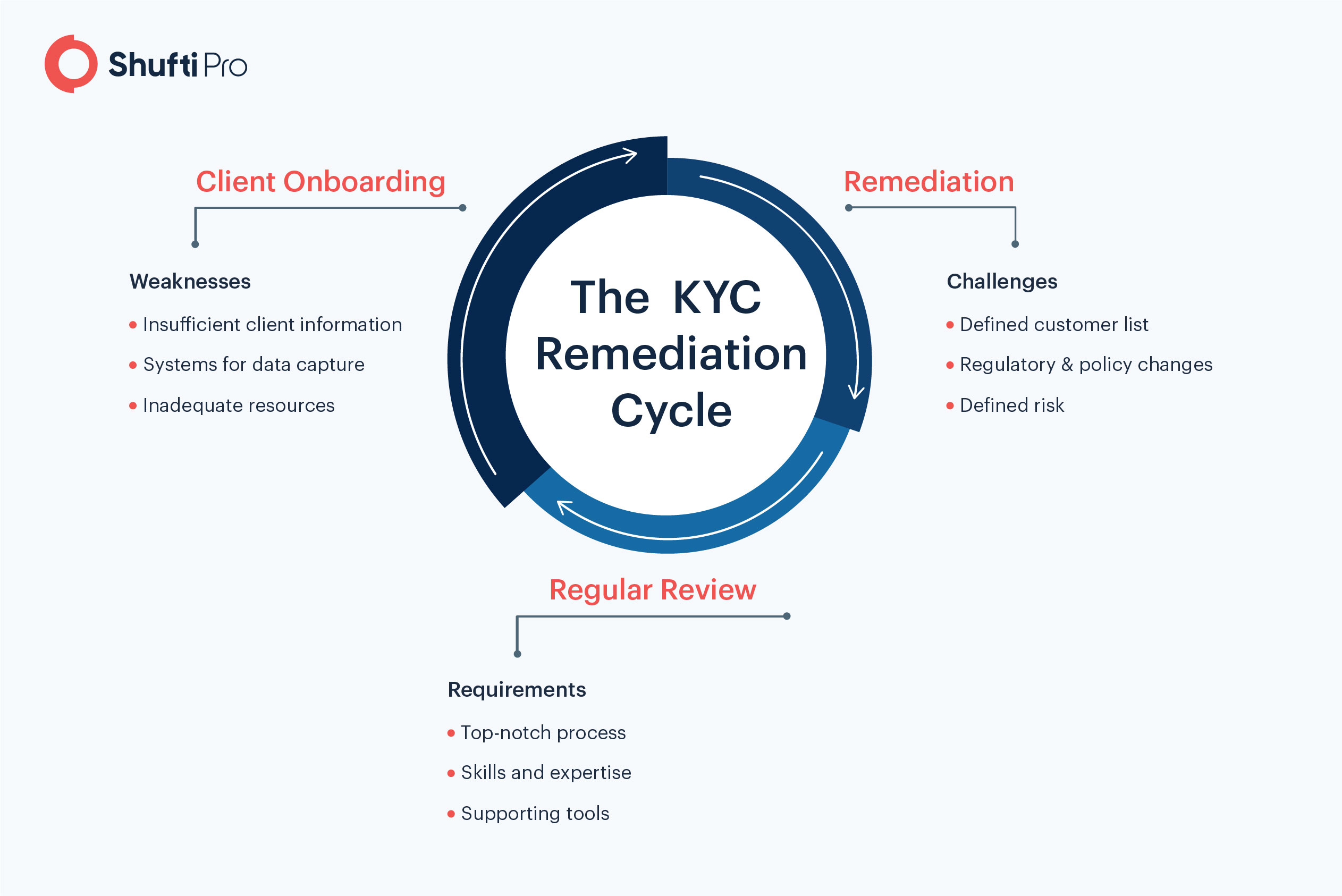
The KYC Remediation Cycle
The KYC remediation cycle is a common issue that financial institutions are trying to break. A survey showed that almost 90% of the businesses conduct KYC remediation, and more than 50% of the companies conduct it multiple times. Nonetheless, businesses are still facing probes for ineffective know your customer and anti-money laundering policies. The question here is where does the actual problem lie that leads to hefty penalties every year? The customer onboarding process is generally weak that leads to challenges in the KYC remediation process.
Ineffective Onboarding Process
It all begins with a weak customer onboarding process and the issues can be:
- Inadequate resources
- Outdated methods for acquiring customer information
- Lack of experienced personnel
- Poor systems to update the information regularly
Suggested: Shufti’s Insights on Enhancing Customer Onboarding Experience
Obstacles to KYC Remediation
Obstacle |
Reasons |
| Data | Producing a client list, unavailability of existing clients’ data, no data privacy and protection rules, and file prioritization |
| Systems | Multiple onboarding systems, inability to capture required data, inadequate functionality to support review |
| Policy and Standards | No clarity in due diligence policies, continuous changes to regulations, desire to comply effectively in the blink of an eye |
| Process | Quality of the existing process, process scalability, governance |
| Resources | Manual process, knowledge capital, judgement-based decisions |
Challenges in KYC Remediation
The weak customer onboarding process results in numerous challenges to develop the perfect KYC remediation process. Although this is a fundamental requirement, companies have a lot of trouble in designing the procedure. Consequently, businesses set unachievable goals for the KYC remediation process. For instance, the amount of data that must be acquired may be too high and with manual processes, the end-to-end time required for review, contacting the client, obtaining additional data and updating it becomes a major challenge.
Companies have to be sure about the constant updates from regulatory authorities in the KYC and AML rules. Determining the parameters to tweak KYC remediation process as per regulatory updates is crucial for businesses.
Regular Review of Activities
A periodic review process refreshes the entire KYC profile of the customer. The frequency of the review activities depends upon the geography. For instance, businesses in Europe undertake this activity every three to five years, depending on certain triggers. On the other hand, the United States performs KYC remediation activities every year or two.
Find out more about KYC remediation triggers: Periodic to Perpetual KYC — The Changing Landscape in Banks
To identify trigger warnings, businesses need highly skilled staff that can continuously keep an eye on the transactions. Along with experiences personnel, there must be effective tools that can verify existing clients and update customer profiles.
Risk and Value-based Approach to KYC Remediation
Shufti’s Know Your Customer and Anti-money Laundering solutions are backed by AI and ML models, which are regularly trained to make sure companies can effortlessly screen customers according to global compliance regulations. Additionally, with ever-evolving regulations across the globe, there is no room for manual verification methods to maintain updated customer risk profiles. That being said, Shufti’s state-of-the-art solution can help you verify customers in less than 30 seconds.
Key Takeaways
With financial crimes at their peak, banks and other financial institutions are at a high risk of penalties. One of the key methods to avoid regulatory fines is maintaining updated customer risk profiles, and the best way to achieve this goal is to employ effective KYC remediation processes. Nevertheless, there are a lot of reasons that can lead to weak KYC remediation process and one of the main reasons is an ineffective customer onboarding process.
Want to know more about the best practices of KYC remediation best practices? Get in touch with the experts.

 Explore Now
Explore Now













