Harnessing the power of AML Screenings to Uncover Politically Exposed Persons [PEPs]

- 01 What are Politically Exposed Persons [PEPs]?
- 02 What are PEP Risk Levels?
- 03 Classification of Politically Exposed Persons
- 04 What is a PEP Screening?
- 05 The Importance of PEP Screening: Explained
- 06 Complexities Businesses Face During PEP Screenings
- 07 Best Practices to Determine Changes in PEP Status
- 08 PEP Screening Best Practices for Businesses in 2024
- 09 FATF Recommendations for PEP Identification
- 10 PEP Screening Regulatory Requirements in the US and UK
- 11 AML Screening for PEPs with Shufti
Since the last decade, governments and financial institutions have been trying to limit corruption, money laundering, immoral activities, and financial crimes globally. Finding a jurisdiction with little to no Know Your Customer (KYC) or Anti-Money Laundering (AML) regulations is tough. However, as technological advancements, globalization, and financial crimes increase, the movement of money and the fight against organized crime have become a significant concern among businesses, regulatory authorities, citizens, and governments alike.
PEP screenings have become one of the most critical branches of KYC and AML compliance guidelines, mandating businesses to perform enhanced due diligence checks on clients that fulfill the criteria of a PEP. The importance of determining such entities is undeniable as their exposure to potential risks of money laundering, tax evasion, corruption, and terrorist financing.
What are Politically Exposed Persons [PEPs]?
The acronym Politically Exposed Persons [PEPs] first emerged in the 1990s, known as Senior Foreign Political Figures [SFPFs], right after the world witnessed the biggest money laundering attempt called the “Abacha Affair,” which paved the way for PEP screening regulations, fueling regulatory efforts to develop strong anti-money laundering laws – aiming to restrict government officials, political officials and other high-risk entities exposed to greater risk of financial crimes.
However, as PEPs include high-profile entities usually linked to political parties, it’s challenging for businesses to develop PEP lists and risk profiles, as the criteria for defining and considering an entity as a PEP is very broad, and policies vary jurisdiction-wise.
The FATF’s Take on Politically Exposed Persons [PEPs]
The Financial Action Task Force is an independent intergovernmental authority responsible for regulating the global financial ecosystem while developing anti-money laundering and counter-terrorism financing regulations to limit the illicit use of financial institutions for money laundering activities. The watchdog has emerged with a series of recommendations and policies. According to FATF:
“A politically exposed person (PEP) is defined by the Financial Action Task Force (FATF) as an individual who is or has been entrusted with a prominent public function. Due to their position and influence, it is recognized that many PEPs are in positions that potentially can be abused to commit money laundering (ML) offenses and related predicate offenses, including corruption and bribery, as well as conducting activity related to terrorist financing (TF).”
The regulatory authority also suggests that businesses should screen PEPs’ close associates, partners, and family members by undergoing customer due diligence checks as a broader aspect of the PEP screening program.
What are PEP Risk Levels?
Every regulated business needs to implement or have a guideline while working with a PEP. After the initial due diligence, if a customer is discovered to be a PEP, companies need to opt for enhanced due diligence checks to detect further the risk associated with them. FATF’s recommendations include 3 risk levels for PEPs – low, medium, and high depending on the risk they pose. The categories are listed as follows:
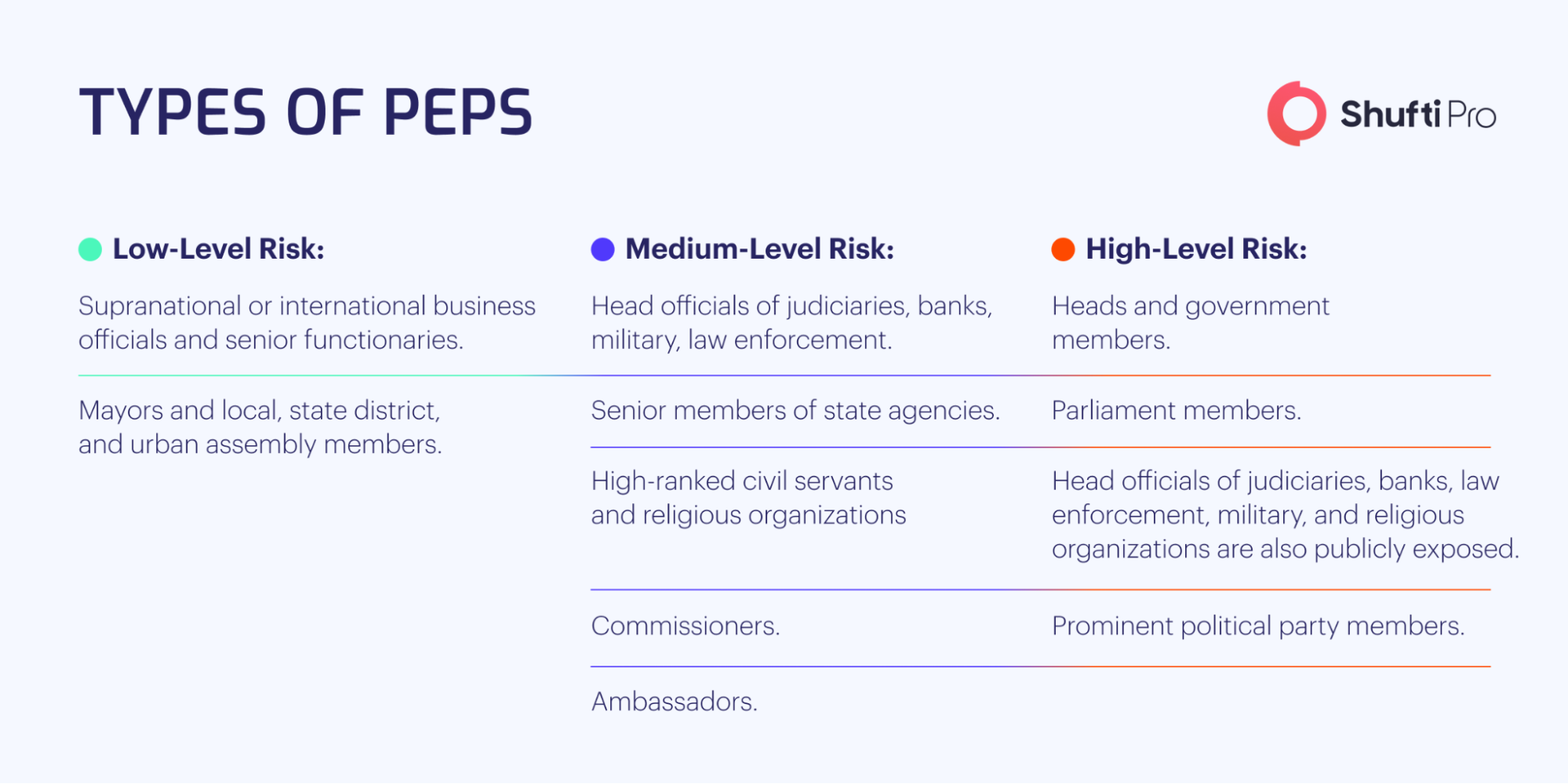
Classification of Politically Exposed Persons
Under the FATF’s anti-money laundering guidance, PEPs are classified into three categories, including:
- Foreign PEPs: People with prominent public services in foreign countries, such as politicians, government officers, or heads of state, etc.
- Domestic PEPs: Entities obliged to manage domestic public services, for instance, senior politicians, military officials, or senior executives of state-owned corporations, etc.
- International PEPs: Individuals designated at prominent positions across international corporations. This type covers directors, deputy directors, and members of the board or equivalent functions, etc.
What is a PEP Screening?
As per global regulatory authorities, screening PEPs is a viable process that aims to help financial and non-financial businesses avoid exposure to money laundering risks while meeting compliance and evading hefty fines for non-compliance. To help understand the workflow of PEP screening solutions, your business must have robust AML solutions in place that empower them to detect and deter the risk of onboarding a PEP.
Let’s take the example of customers who approach insurance companies to get insurance, and in the initial screening, they are detected as a PEP. In such cases, before onboarding, the company must opt for enhanced due diligence checks to further screen against adverse media and other government databases to ensure they have no history of crimes.
Screening PEPs is a crucial aspect of KYC and AML compliance procedures. Businesses are mandated to screen customers against PEP lists, watchlists, government databases, and other adverse media channels. By practicing this approach, financial firms can effectively identify, manage, and deter risk associated with PEPs, ensuring compliance with KYC, AML, and CFT regulations.
The Importance of PEP Screening: Explained
Corruption, money laundering, and tax evasion are significant issues governments face today. As per the World Economic Forum, it’s estimated that the cost of corruption has jumped $2 trillion, constituting approximately 5% of global GDP. The World Bank also states that individuals and businesses suffer a loss of approximately $1 trillion in bribes each year. In addition to these, the United Nations Office on Drugs and Crime (UNODC), also reported that around $800 billion to $2 trillion is laundered yearly, which comprises 2% to 5% world’s GDP. These statistics show that financial crime is prevalent, and today’s economy is at risk.
Thus, PEP screening is not only crucial for rectifying financial crime risks but also an obligation by law in regulated jurisdictions. For instance, the US Patriot Act obligates financial businesses to develop EDD checks along with a robust ongoing monitoring process to oversee SFPF activities, a subset of PEPs.
Complexities Businesses Face During PEP Screenings
Screening customers against global financial crime databases and sanction lists is a governmental and regulatory obligation; however, it is a challenging, cost-draining, and time-consuming task if carried out conventionally. There lies a significant risk of false positive document forgery, tempering with the experience of customers unnecessarily recognized as PEP, and missing the potential match – exposing businesses to hefty fines, sanctions, and reputational damages for non-compliance with negligence.
- Changing PEP Status: With time, individuals verified as PEPs can experience changes in political standing, affiliation, and positions. This means they can either become riskier or be declassified as a PEP. However, assessing this change can be difficult for businesses. Keeping a record of the changes while identifying new PEPs requires automated PEP screening solutions that can acquire the updated data promptly to ensure the screening automation’s effectiveness.
- Cross-Border Complexity: Businesses and financial firms operating internationally encounter the risk of onboarding or working with politically exposed persons from various jurisdictions with different sets of laws and regulations. However, meeting cross-border compliance and navigating the complexities become challenging for businesses to ensure accurate PEP screening.
- Data Privacy and Compliance: Businesses must carry out enhanced due diligence and handling of personal information, which requires compliance with GDPR or other data protection and privacy laws. Thus, companies need to have robust PEP screening systems that can align information collection, processing, and storage with compliance while ensuring security measures against data breaches and unauthorized access.
Best Practices to Determine Changes in PEP Status
Clients may get the status of a PEP in multiple ways, including changes in employment, political appointments, promotions, or electoral victories. However, it’s viable that businesses must be able to determine the change in risk profile as soon as it does. On the other hand, companies should also be equipped to determine the declassification of their customers’ PEP status. Here is how businesses can identify the changes in PEP status:
- Customer Due Diligence: As a regulatory obligation, businesses need to oversee PEPs and non-PEP activities on a daily basis, ensuring that the risk of crime is mitigated before it actually happens. To do so, companies must have rigid customer due diligence checks in place.
- Employee Training: Financial institutions and other firms need to arrange training sessions for their employees to make them capable of detecting changes in PEP status. In addition to this, the FATF also suggests companies must have ongoing training sessions with the involvement of compliance officers while incorporating day-to-day and real-world cases.
- Adverse Media: Companies can check online available information sources like adverse media platforms to closely monitor their clients’ PEP status before confirming them by official sources.
- Commercial Databases: These lists are available commercially to help businesses screen their customers to determine risk effectively. However, these databases can not be used in place for customer due diligence processes, and institutions may use these to further dive for enhancing PEP screening measures.
- Government PEP Lists: Like adverse media and commercial databases, businesses can access government PEP lists that consist of information related to public service officers recognized as PEPs to better understand their customers’ activities while determining PEP status in real-time.
The above-mentioned key considerations are effective measures that help businesses determine customer PEP status changes. It’s noteworthy that enterprises need to monitor declassification from PEP status. This means that when clients are verified as PEPs, if they step down from public or governmental service roles, the risk profiles and PEP status should be changed and treated as normal customers. In addition to this, businesses must also closely review factors when seeking to downgrade PEP status, for instance, links to current political parties, the level of corruption they are exposed to, and how long they have been offering services.
However, there is no time limit for PEP declassification. According to the FATF, the declassification process should be based on risk assessment, not prescribed time frames.
PEP Screening Best Practices for Businesses in 2024
- Businesses need to adopt a risk-based approach. If a client has been verified as a foreign or domestic PEP, businesses should initiate risk assessment and scoring models that can help them determine and undergo appropriate EDD levels.
- Acquire customer information from multiple authentic sources, as it is necessary to extract data from adverse media, sanction lists, and government databases with the intent to determine clients’ PEP status.
- Meet FATF’s compliance requirements by practicing rigid enhanced due diligence checks, establishing the source of funds for secure business relationships, and limiting the risk of getting involved in money laundering activities.
- Companies are recommended to search clients’ names in their native language to limit false positive results.
- Discover geographies to identify customer risks, as risks vary country-wise. Lower-risk jurisdiction helps businesses reduce the reviewing time of close associates and relatives.
- Integrate a robust risk assessment and scoring framework to assess the potential risk PEPs pose. However, for each risk category, businesses’ risk assessment model must be able to calculate the risk factors while building robust risk scoring and mitigation processes.
- Consider screening low-risk PEPs against only sanction lists while verifying medium-risk entities against sanction and regulatory actions. For high-risk PEPs, screen them against all available resources, including adverse media, government databases, watchlists, sanction lists, etc.
FATF Recommendations for PEP Identification
In addition to enhanced due diligence checks, the FATF has obliged financial firms and non-financial businesses to establish a comprehensive risk assessment and management framework to determine, assess, and mitigate PEP risk associated with PEPs. This framework should comply with regulatory policies and procedures that outline the businesses’ approach to effectively handling and deterring risk. Companies must also have rigid PEP screening systems that can identify PEP status in real-time.
The FATF also suggests that organizations must conduct ongoing transaction monitoring to ensure that the customers are not involved in syndicate crimes like money laundering and terrorist financing. An ongoing monitoring approach should be backed by rigid risk assessment checks to identify and eliminate any suspicious customer activity concerns while reporting them to local or international financial intelligence units.
Having social and regulatory responsibility, businesses need to arrange training sessions to equip their employees with capabilities to determine and assess the risk associated with their customers while raising awareness about the importance of PEP screening.
PEP Screening Regulatory Requirements in the US and UK
PEP screening requirements differ slightly in terms of regulatory and domestic obligations in both countries. In the United States, screening politically exploited persons is a crucial aspect of anti-money laundering and counter-terrorist financing programs. Under this obligation, businesses are mandated to align their PEP screening program with the Bank Secrecy Act and the Patriot Act’s requirements under the supervision of the country’s prominent regulatory authority, the Financial Crimes Enforcement Network (FinCEN). Additionally, companies must develop an in-house risk-based approach that should include customer due diligence for low-risk customers and enhanced due diligence for PEPs & other high-risk customers exposed to greater crime risk. If a customer is verified as a PEP, and the company has evidence regarding involvement in organized crimes, they must file a Suspicious Activity Report (SAR) to FinCEN.
Like the US’s requirements, PEP screening is a regulatory obligation comprising domestic and foreign PEPs. The United Kingdom has its own body, the Financial Conduct Authority (FCA), responsible for overseeing PEP screening programs while ensuring that companies are practicing AML laws effectively
AML Screening for PEPs with Shufti
Anti-money laundering screening solutions play a crucial role in determining and deterring the risk associated with customers recognized as PEPs. These high-risk entities are primarily exposed to political power and public funds, making them potential targets for committing financial crimes like bribery, money laundering, and corruption. Without an effective AML compliance framework, financial and non-financial businesses can unwillingly become part of organized crimes or facilitate PEPs in laundering their illicit gains.
Shufti’s anti-money laundering screening solution allows businesses across 240+ countries and territories to identify and verify their customers’ identities while helping them uncover risks associated with them. In addition to this, our solution is designed to help companies make informed decisions by determining the PEP status of customers and elevate their compliance efforts. By screening customers against adverse media and 1700+ global watchlists, businesses can determine clients’ potential involvement in money laundering or other financial crimes while taking appropriate measures to handle risk effectively.
How Shufti can help your business:
- Successfully detect financial crimes, including money laundering & terrorist financing.
- Meet global AML and CFT compliance.
- Screen customers against PEPs, sanction lists, and adverse media.
- Get access to 1700+ international databases.
- Verify customers’ identities with 99% accuracy while mitigating the risk of onboarding PEPs.
Shufti’s AML Screening solution is the first choice of 1,000+ businesses worldwide, helping them meet compliance, fight fraud, and accelerate trust across digital economies. Request a demo today and try Shufti’s AML screening service to identify high-risk customers and mitigate risk effectively for compliance and reputation.

 Explore Now
Explore Now













