Implementation of AML compliance – Challenges and fundamentals

- 01 Information flow - the key challenge for implementation
- 02 Globalization of economic activities
- 03 Cross-border movement of funds
- 04 AML/CFT standard for effective information flow
- 05 3 major interventions of AML/CFT standard
- 06 Know your customer (KYC) system
- 07 Comprehensive Policies and Acceptance
- 08 A designated AML compliance officer
- 09 Ongoing Monitoring and Testing
With the advancement in security controls, financial businesses are becoming fraud and stress-free. However, every new thing comes at the cost of something and is not as easy to implement as it seems. The organisation heads invest time and money to efficiently replace their old processes. The stringent regulatory framework requires even more proficiency for implementation of stable anti-money laundering (AML) and counter-terrorist financing (CTF) compliance.
Information flow – the key challenge for implementation
It’s a known fact that businesses are always facing new challenges for the implementation of effective AML compliance. The significant challenge is to adequately obtain, maintain and transmit the relevant required information. Proper information flow is crucial and a prerequisite to executing AML/CFT laws and regulations. To ensure enforcement of law and prevent any possible violations, law enforcement authorities require proper information.
Since 1970, the government’s approach towards information for enforcement of laws has been disrupted due to interconnected technological developments and upgraded processes. The technological developments have resulted in the globalisation of economic activity and financial crimes. Not to forget that cross-border funds movement is intensely increasing, both in terms of volume and speed. Moreover, certain factors are fueling economic crimes to reach higher levels of magnitude crossing the national borders. This involves both global activities and processes.
Globalization of economic activities
The arising challenges for law enforcement authorities are because the law enforcement strategies were present only at the domestic level. When the activities and crimes crossed borders, the strategies worsened. The difference in the legal systems raised problems for the authorities since the foreign jurisdictions were applied to the procedures to safeguard their sovereignty.
The difference in legal and regulatory systems also induced another challenge for the authorities that was the discrepancy in the gathered information. The information-gathering processes varied from country to country, therefore law enforcement agencies couldn’t guarantee if reconstructing the money trail would be possible after going through foreign jurisdictions.
Cross-border movement of funds
With globalisation and intense cross-border fund flows, criminals excessively started using trading channels to circulate their assets and reinvest them without getting detected. It became crucial for law enforcement authorities to acquire financial and transaction information. The traditional processes weren’t efficient to meet the requirements of law enforcement authorities.
Apparently, the traditional methods were slow and required an evidentiary threshold which wasn’t needed at an early stage of the detection process. Apart from limitations to access the information, some of the information that authorities needed to reconstruct the money trail wasn’t even gathered by the financial institution and businesses. For instance, banks and other financial institutions didn’t always maintain records of verified customer data related to wire transfers.
AML/CFT standard for effective information flow
To address the challenges identified, AML/CFT standards were introduced. The 40 recommendations of FATF presents a comprehensive set of instructions. These recommendations can address the challenges regarding inefficient information flow that law enforcement authorities face in tracing the financial crime.
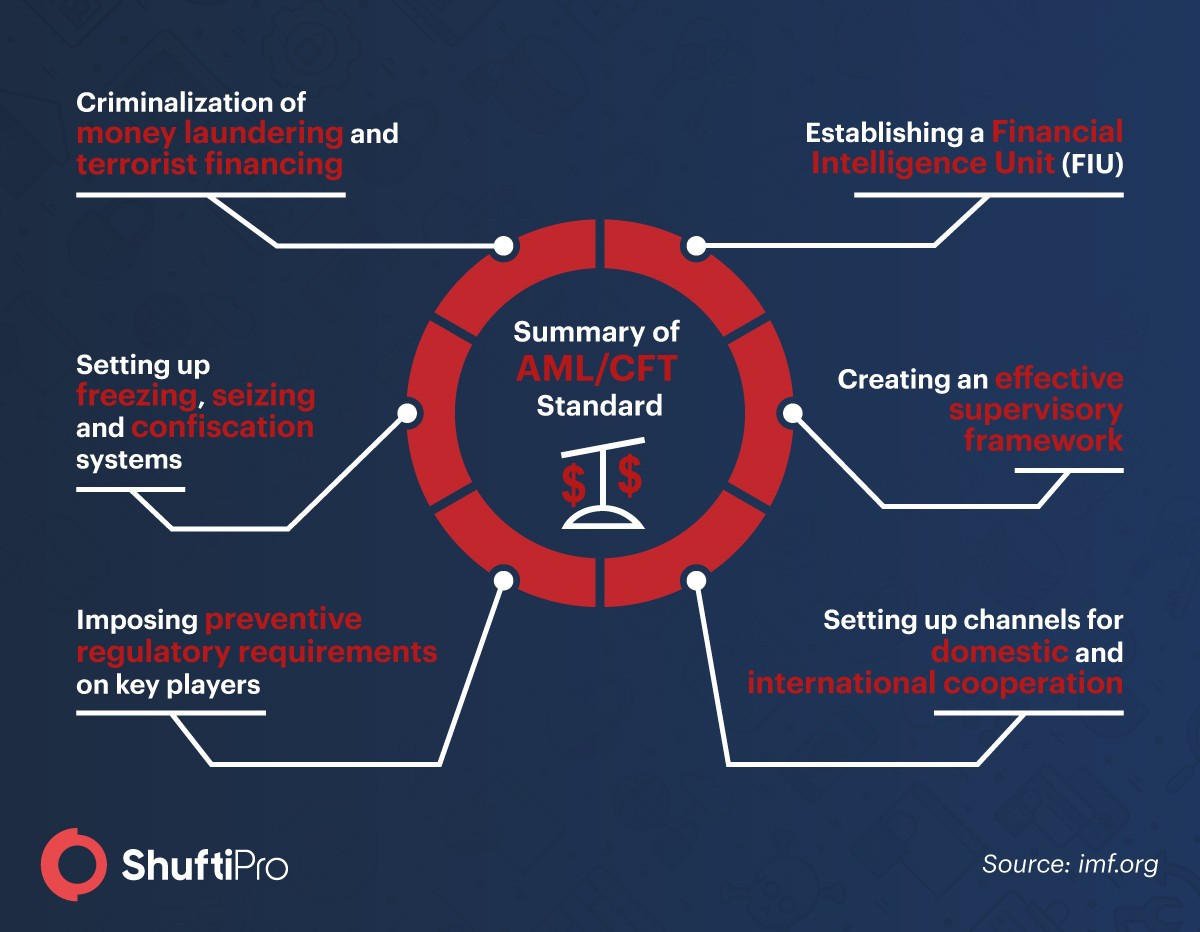
AML/CFT standard systems facilitate law enforcement agencies to achieve multiple objectives that include:
- Financial crime detection by pursuing money trail
- Removal of profit out of crime through expropriation
- Identification of professional or third-party money laundered who provide services and platforms to criminals to launder money without getting detected
- Targeting the heads of a criminal organization (such as terrorist financing, drug trafficking) that are not under the limelight
- Most importantly, protecting the integrity of the financial system and making it crime-free.
3 major interventions of AML/CFT standard
To successfully achieve these objectives, the international AML/CFT standards focus on three major interventions that the countries must adopt, these include:
- Imposing the obligations on the key players of the business world that deal with transactions; it includes, banks, financial institutions, real estates, casinos, etc. These institutions are mandated to gather and verify certain pieces of information about the transactions being processed.
- AML/CFT standards obligate the above-mentioned institutions to keep a record of the gathered information for a specific period. Also, these record, when retrieved by the authorities, must be in a timely fashion.
- Creation of a legal environment to enable the secure sharing of information between various parties with the purpose to fight against financial crime. This category address the challenge of information flow.
Fundamentals of AML Compliance
The world is changing and regulations are becoming more stringent. AML compliance is a term every business is familiar with. But just knowing it isn’t enough, instead of relying on the definition only, the fundamentals must be taken into consideration for an efficient AML compliance. Here are some key functions that every financial business must-have:.
Know your customer (KYC) system
Customers are the assets of any organisation, therefore, their risk assessment must be conducted before onboarding them. Not, just at the time of on-boarding but businesses need to re-evaluate whenever there’s some update in the information or any new possible risk. Henceforth, KYC program is vital for any business to successfully comply with AML/CFT regulations. With the KYC process in place, there are several questions that institutions can cover, including;
- Who is the person? Is the provided information correct?
- Is it safe to onboard him/her?
- What type of activities do they want to perform in future? etc.
Through customer identification program and customer due diligence, not only the identity of the customer can be verified but the risk associated with an individual can be identified before onboarding.
Comprehensive Policies and Acceptance
Written policies and procedures are important that cover the full spectrum of AML compliance guides. As financial institutes need a solid proof for each of the components of AML so these have to be easily accessible to everyone including relationship managers, branch managers and other financial salespersons. Because of competing demand and lack of commitment many businesses suffer a lot.
The Board of directors and CEO commitment to the policies means real hands-on dedication to ensure that every person takes compliance seriously and views it as part of their duties instead of relying on the compliance department only.
A designated AML compliance officer
Supervision of any work is requisite in every organisation. When it comes to efficient AML compliance, a compliance officer must be there to monitor all the AML processes. A designated compliance officer should have adequate knowledge and resources available to support the financial institution’s compliance program readily. By this, it means that company CCO does not only need personnel but also needs a real investment in technology to implement AML for organizing financial information, customer data, and filtering transactions.
Ongoing Monitoring and Testing
Financial institutions need to become more flexible for monitoring and auditing of their compliance program. An AML program provides many metrics to measure the compliance program by generating lots of data. With every passing day, the trend is changing and the processes must be timely updated to meet regulatory needs. Independent evaluations and testing should be conducted and reported to senior management annually.

 Explore Now
Explore Now













