Securing Public Facilities with Touchless ID Verification Kiosks

Due to the coronavirus pandemic, social distancing became the utmost need of the hour. Given the rise in contactless means of communication, touchless identity verification is also an emerging trend these days. Verifying identities through traditional means was long gone when eKYC emerged. Now, the trend for contactless verification is increasing. Airports, arenas, and other public facilities are preferring touchless means of ID verification. Recently, Japan announced the use of face recognition technology at the Tokyo Olympics. The purpose is to trace any unusual activities and contact among individuals. Similarly, the majority of states in the US have touchless verification kiosks at the airports to ensure seamless identity verification.
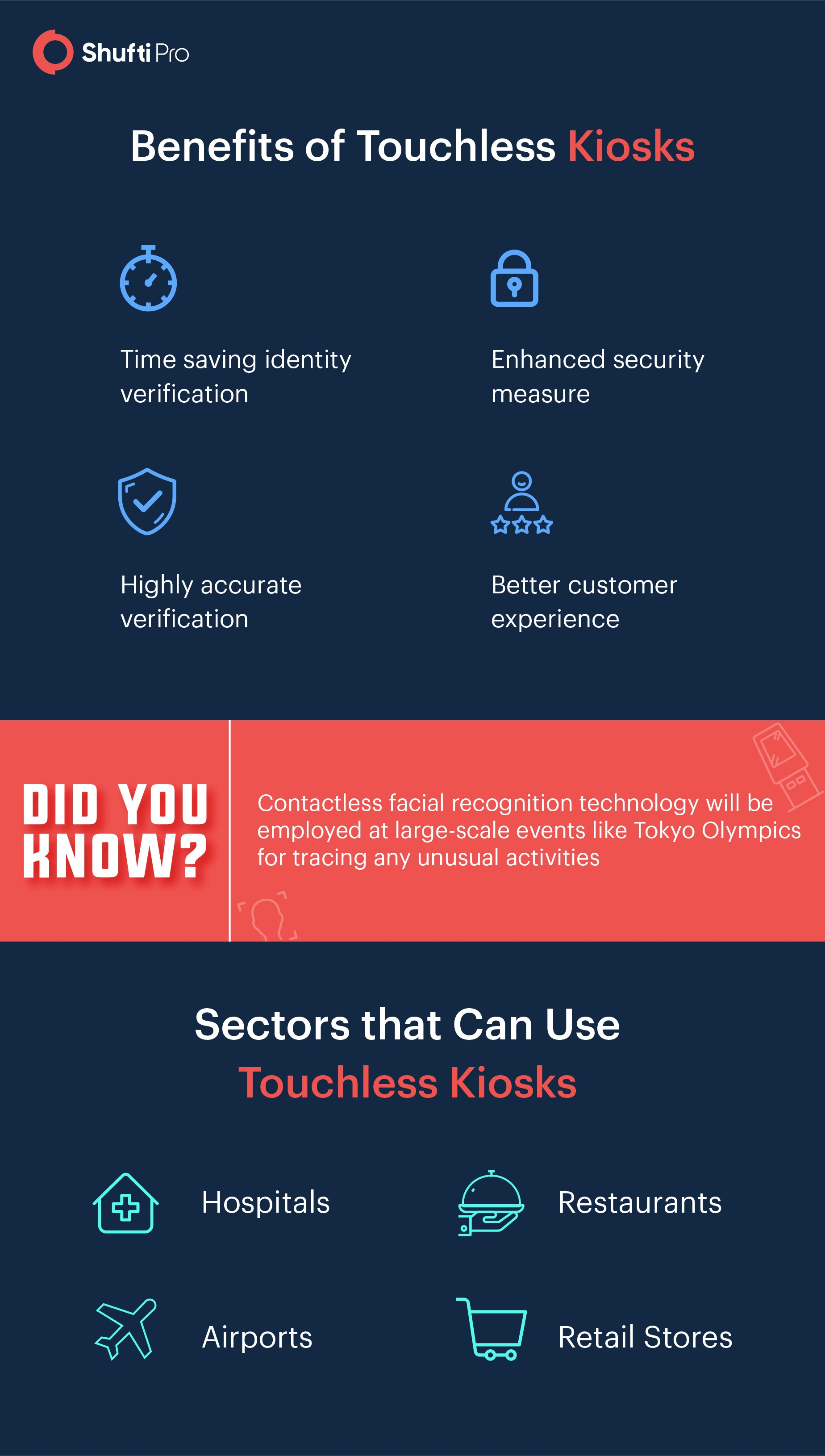
Touchless identity verification not only ensures social distancing but provides customers with a seamless experience. Read this blog to find out the what and how of touchless identity verification kiosks.
What is Touchless Identity Verification?
As the name suggests, touchless identity verification does not include any physical contact. The end-user does not have to visit the company or make contact with machines for submitting documents. Unlike the conventional method, customers can show their face and government-issued ID documents to the screen and get verified within seconds.
How Does Touchless ID Verification Work?
The process is very simple and takes few seconds for completion. With advanced Artificial Intelligence models, the contactless system verifies identities accurately and has the following few steps.
- First, the touchless kiosk is installed at security checkpoints of public facilities, arenas, airports, restaurant entrances, etc.
- The end-user signs up with their identity details remotely
- Upon arriving at the place, customers verify identities by showing identity documents. No physical contact is involved here
- the customer’s live biometric information is recorded and the verification is performed against the previously submitted information
- If the match is successful, the customer can enter the facility. Otherwise, the verification is declined and end-user cannot enter the place
The five simple steps hardly take a minute for completion. If the information submitted during registration is correct, the contactless kiosks require only five seconds to perform the rest of the verification checks.
ID Verification Checks Performed in Touchless Kiosks
The process is effortless and simple, and also verifies in real-time. However, it is important to know the various checks Shufti’s touchless kiosks perform for identity verification. In our facility, the contactless system performs document verification and three different biometric authentication checks for enhanced security. Let’s take a look at all of them.
Document Verification
This is the first check performed. Once your customers reach the security checkpoint, they have to show their government-issued identity document to the machine. The information provided for registering is cross-checked with the identity document shown to the kiosk. In case, the documents are not verified, further verification checks are not performed.
Biometric Authentication
Biometric authentication is an emerging trend for identity verification. Biometric authentication refers to the verification of behavioural and physical attributes of an individual. These attributes include walking style (gait), iris, pupil, palm, face, retina, and voice recognition. Touchless kiosks perform three different biometric authentication checks for better security. These three checks include face recognition, palm recognition, and voice recognition.
Face Recognition
Every person has a different face geometry that makes it easier for facial recognition system to verify identities. The images on the government-issued identity documents submitted during registration are verified with the face shown to the kiosk. The face recognition algorithms map facial features of the customer from the image and are authenticated with the face in real time.
Palm Recognition
The unique biometric traits on an individual’s palm are also used for biometric authentication. To access certain services, it is essential for all the individuals to perform palm-vein recognition and handprint recognition. Along with a variety of other techniques, palm recognition works as an extra layer of security on top of face recognition and voice recognition.
Voice Recognition
Voice recognition is another biometric authentication measure that works by digitising the voice of the customer into segments and matches it against the voice captured or produced as a sample of the customer. Voice being the sift biometric is perfect for contactless identity verification at public places.
Be it airports, hotels, or conferences, touchless kiosks can be of great help for your organisation in ensuring security and contactless measures at all times.
Shufti’s Touchless Kiosks Facilitating Your IDV Needs
Shufti strives hard to ensure higher levels of security of your company. Since the coronavirus pandemic has imposed social distancing on us, we are now providing touchless identity verification kiosks to large-scale events, airports, arenas, restaurants, and anyone who is wondering about better ways of verifying identities and avoiding physical contact. Shufti’s touchless kiosks have the following benefits for your company.
- We provide global support and contactless kiosk also verifies more than 3000 document types with 150+ languages
- Compliance with GDPR and PCI DSS data protection measures is ensured
- Screening is automated so there are no chances of manual delays
- State and international regulatory compliance is also ensured
- Real-time verification within five seconds
- Three types of biometric authentication checks for enhanced security
- A combination of several identity verification checks increases accuracy and credibility of this system
Summing It Up
Due to the Covid-19 pandemic, everyone prefers contactless means of communication. Verifying identities through traditional methods is no longer adequate in the digital world. Now, contactless methods of identity verification are preferred over the other methods. With the help of touchless identity verification kiosks at security checkpoints, you can enhance the security of large-scale events. Airports, restaurants, and retailers can make great use of this technology and secure their organisation from unusual activities. Our touchless kiosks employ document and biometric authentication for better security.
Get in touch with our experts today and know everything about touchless kiosks.

 Explore Now
Explore Now













