The Complete Guide | Transaction Monitoring for Financial Institutions

With technological advancement, financial criminals have also been given a wider range of tools and mean to launder money whilst hiding their true identities. Detecting and monitoring money laundering and terrorist financing risks remains a persistent challenge, particularly for Financial Institutions (FIs) and many other firms. 2022 witnessed a 50% rise in global fines over failing to prevent money laundering and other financial crime. This is where an AML transaction monitoring solution comes in.
Understanding Transaction Monitoring in Financial Institutions
Transaction monitoring involves analysing the transaction patterns of customers to evaluate their financial profiles, investigating any unusual activities, and setting thresholds. KYT (Know Your Transaction) Verification is vital for FIs to identify and manage risks associated with customer behaviour and their counterparties. It allows institutions to detect unusual transactions and take appropriate actions, such as conducting further investigations or reporting suspicious activity to regulatory authorities.
There is no one-size-fits-all approach to AML controls during the complexity of transactional behaviours and challenges related to data quality and evolving money laundering techniques. FIs must adopt a holistic approach to mitigate the risks across their diverse business units and design controls tailored to specific business profiles, customer bases, and geographical footprints.
FIs are responsible for driving innovation and should consider providers offering robust transaction monitoring solutions to support their forward-thinking strategies. Regulatory bodies such as the UK’s Financial Conduct Authority and US regulators encourage technological innovation in AML controls. Leveraging entity resolution and network analytics is crucial for a successful risk-based approach at the group level.
By utilising entity resolution and network generation technology, financial institutions can identify risks, establish contextual information about unusual activities to enhance Suspicious Activity Reports (SARs) and mitigate risks more precisely. These technologies also enable investigators to analyse unusual transaction patterns more quickly, resulting in significant cost savings by reducing the time spent on each investigation.
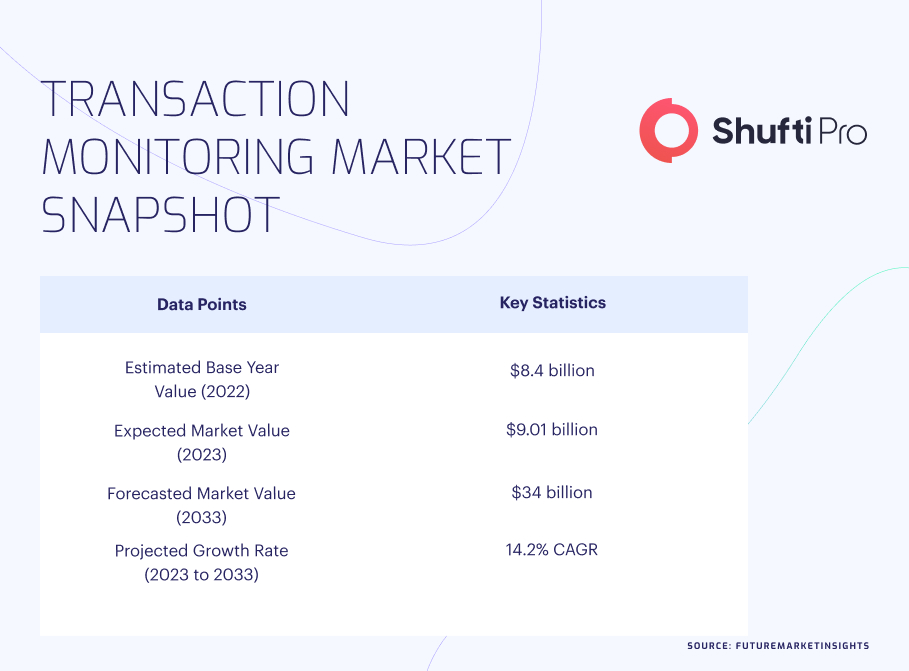
Transaction Monitoring Challenges
Transaction monitoring is crucial in ensuring compliance with Anti-Money Laundering (AML) and Combating Terrorism Financing (CTF) regulations globally, making it a top priority for banks. However, implementing an effective KYT verification system comes with compliance challenges, which banks must address at any cost.
Noteworthy challenges faced in transaction monitoring within the banking sector include:
- Anonymity: Online transactions provide a level of anonymity that is not present in face-to-face transactions. This anonymity can enable high-risk individuals to hide their identities while conducting transactions.
- Speed: Money launderers can exploit the swift nature of online banking services to rapidly move funds across accounts and jurisdictions, bypassing AML and CTF controls designed to detect illicit activities.
- Scale: Banks require a transaction monitoring solution capable of scaling their business. Using manual monitoring and verification processes can be costly, slow, and lead to customer dissatisfaction.
- Structuring: Money launderers may engage in transactions below the set limit to avoid reporting thresholds. They may use structured transactions across multiple accounts to hide their illicit intentions.
- Money Mules: Some criminals may enlist third parties, known as “money mules,” to carry out transactions on their behalf, aiming to bypass AML and CTF controls. These money mules are often vulnerable individuals incentivised or coerced by criminals.
Addressing these challenges is crucial for banks to ensure effective transaction monitoring and maintain compliance with AML regulations.
A Risk-Based Approach to Transaction Monitoring in Banks
Banks must adopt a Risk-based Approach (RBA) to a know your customer transaction monitoring solution. This approach entails conducting individual assessments of customers and implementing compliance measures that are proportionate to the risks they pose. Transactions involving high-risk customers demand more rigorous transaction monitoring measures, whilst lower-risk clients may require simpler measures. Accurate risk profiling of customers is vital for effective transaction monitoring. To support this, a comprehensive transaction monitoring solution should incorporate the following measures and controls:
- Customer Due Diligence (CDD): Banks should identify and verify the identities of their customers through appropriate due diligence procedures. This involves collecting relevant identification details such as names, addresses, dates of birth, and company incorporation information to assess transactions against established risk profiles.
- Sanctions Screening: Banks must screen their customers against relevant sanctions lists and watchlists to ensure they are not involved in transactions with individuals or entities subject to sanctions.
- Politically Exposed Persons (PEP) Screening: PEPs, including elected officials and government personnel, pose a higher AML and CTF risk. Thus, banks should continually screen their customers to determine their PEP status.
- Adverse Media Monitoring: A customer’s coverage in adverse media reports can also influence the risk level associated with a particular transaction. Banks should actively monitor various sources, such as screens, print media, and online platforms, for adverse media stories related to their customers. This helps maintain up-to-date and accurate risk profiles.
Implementing these measures and controls within a transaction monitoring solution enables banks to effectively manage risks and ensure compliance with AML and CTF regulations.
An Efficient Transaction Monitoring Solution
- Select a KYT compliance solution that aligns with your risk-based approach whilst catering to the diverse range of customers and transactions.
- Look for a KYT solution provider that offers easy set-up, such as those solutions with no-code rules configuration or comprehensive technical support for seamless integration.
- Consider solutions that generate reports encompassing comprehensive analytics to streamline the business’s reporting duties. This empowers businesses to effectively communicate with regulatory bodies by highlighting suspicious activities associated with money laundering, tax evasion, fraud, and other financial crimes.
- Businesses can consider choosing a single provider throughout the entire customer lifecycle, starting from the onboarding phase and extending to transaction monitoring. This approach facilitates the identification of criminals whilst enhancing the overall user experience for legitimate customers.
How Can Shufti Help?
Shufti offers an AI-powered AML transaction monitoring solution to 230+ countries and territories and supports 150+ languages. Our robust AML solution screens clients against 1700+ watchlists within seconds to mitigate the risks of money laundering and other financial crimes. Not only does it keep criminals away, but it also helps financial institutions comply with global regulations
Still confused about how an AML transaction monitoring solution keeps scammers away?

 Explore Now
Explore Now













