The Most Common Bank Scams and How e-IDV Can Help

Protecting customers against diverse types of fraud is a continual practice for banks and credit unions. Despite efforts made by the financial sector to address security concerns, scammers persistently seek new methods to exploit unsuspecting customers. These criminals use advanced solutions to guess a client’s card number, expiry date, and Card Verification Value (CVV) number. Once successful combinations are obtained, they are used to make purchases at different merchants, typically in small amounts, to evade detection by the affected cardholder. This is where Electronic Identity Verification (e-IDV) comes to the rescue.
Types of Bank Fraud
Criminals commit bank scams to get any person’s personal and financial details. These scammers employ various tactics to deceive people into disclosing sensitive information such as bank account numbers and passwords.
1. Overpayment Scams
As an online service provider or seller, you may be targeted by overpayment scams. This fraud typically involves receiving a counterfeit check or money order that exceeds the owed amount. Subsequently, the scammer requests you to deposit the funds into your bank account and then wire the difference back to them. Unfortunately, since the check or money order is fraudulent, you may be held responsible for a returned check fee charged by the bank. Furthermore, any funds you wired to the scammer and the product would be lost if you had already shipped it.
2. Check-Cashing Scams
The check-cashing scam exploits the goodwill and generosity of individuals. In this scam, someone approaches you outside a bank or financial institution and asks if you can cash a check for them. They may explain that they lack an account at that specific bank but urgently need the money.
One may willingly deposit the check and withdraw cash from their account to give the person their funds. However, the clearing process for the check can take several days. Therefore, the funds are held against your account when the check fails to clear, resulting in financial loss.
3. Unsolicited Check Fraud
Sometimes we receive an unexpected check in the mail. It may appear as a rebate check or a refund for an overpayment. Examine the check for any fine print on the front or back. You may unknowingly enter into a legally binding agreement by endorsing and cashing the check. Scammers use such tactics to deceive you into authorising memberships, loans, or other long-term commitments that could lead to significant financial consequences. Scammers rely on your instinct to view the check as free money and cash it without asking questions. Be cautious when dealing with any rebate or refund check you did not anticipate or request.
4. Automatic Withdrawal Scams
Automatic withdrawals provide a convenient method for automating savings, bill payments, and other financial transactions. However, scammers also exploit this feature for their illicit intentions.
Individuals receive a call or postcard informing them they won a prize or are qualified for a special offer. The scammers aim to get the numbers mentioned at the bottom of your checks to present them during verification to confirm your eligibility for that offer.
Once the criminal obtains your check and bank details, they initiate a demand draft, functioning similarly to a check but not requiring a signature. After receiving the draft, your bank transfers funds from your checking account to pay the scammer. Unless you closely monitor your daily bank transactions, it is possible to remain unaware of the scam.
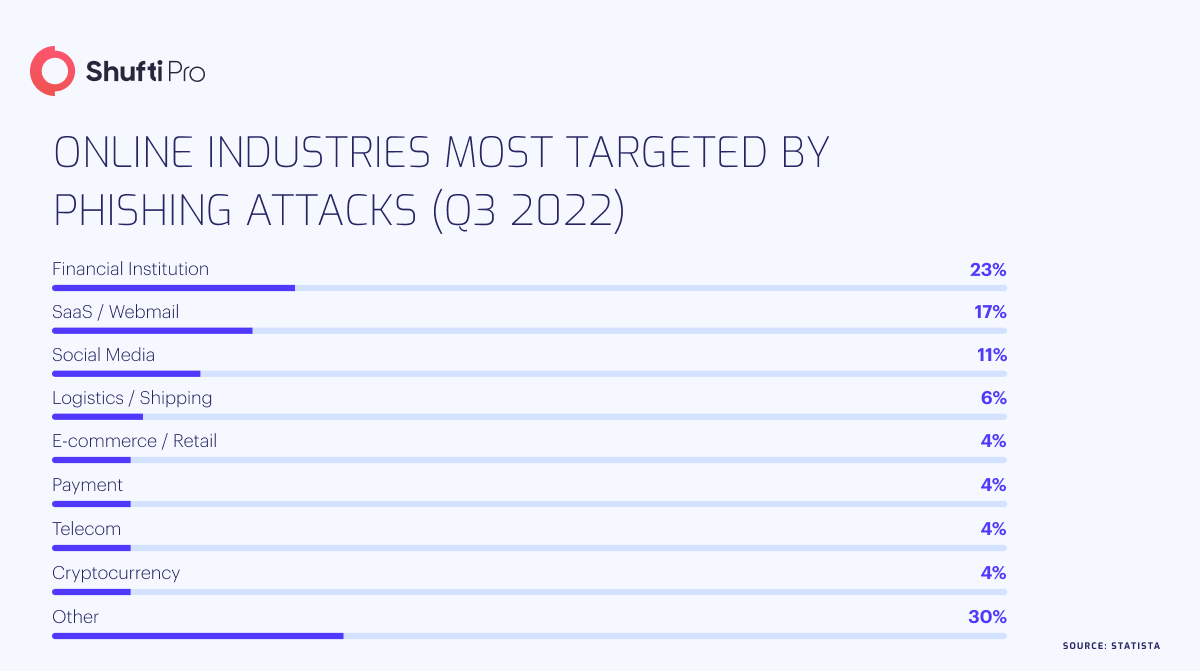
5. Phishing Scams
Phishing is a fraudulent technique in which scammers employ texts and emails to deceive individuals into exposing their personal information. They specifically target passwords, account numbers, social security numbers, and other sensitive details. The ultimate objective of phishing is to gain unauthorised access to your accounts, including email, banking, and other financial statements.
Phishing scams are prevalent due to the ease with which scammers can reach many people through email and text. Phishing texts and emails often mimic communications from well-established companies. Typically, these scams prompt you to click on a link and take action, such as verifying personal information. The message may mention an unusual activity on one of your accounts.
6. Government Imposter Scams
One prevalent bank scam involves individuals impersonating government officials. In this type of scam, you receive a call from an imposter who claims that you have won a prize and requires the fees for processing. The scammer may even threaten imprisonment if you fail to pay an alleged outstanding debt. It is essential to note that federal agencies will never contact you by phone to request payment. Scammers may employ fictitious agency names or misuse the terms of legitimate agencies to collect payments.
7. Charity Scams
Charity scams are another tactic frequently employed by scammers, taking advantage of people’s generosity. They impersonate charitable organisations and make calls soliciting donations for a specific cause. Criminals may manipulate the phone number to make it appear more legitimate.
Charity scams can often be identified by their vague claims and the absence of concrete information on how your donations will be utilised. Scammers may also use fictitious names that sound similar to legitimate charities to deceive unsuspecting individuals.
8. Employment Scams
Employment scams are a prevalent method used by scammers to exploit individuals and gain access to their financial accounts. These scammers falsely promise guaranteed employment opportunities but require an upfront fee as a condition. Moreover, they may ask for your bank account details to transfer commission payments. However, they intend to obtain your bank account details for illicit purposes.
Job scams are frequently initiated through deceptive emails, but scammers target individuals through phone calls and mail. In certain instances, job websites may unknowingly approve fraudulent job postings, unwittingly facilitating these scams.
e-IDV to the Rescue
Electronic identity verification plays a vital role in mitigating the risks associated with bank fraud. Here’s how e-IDV helps:
- Fraud Detection and Prevention: e-IDV solutions can detect suspicious activities and potential fraud in real-time. Anomalies, unusual transaction patterns, or changes in customer behaviour can be identified through advanced algorithms and machine learning techniques. This proactive approach allows banks to promptly flag and investigate suspicious activities, effectively preventing fraudulent transactions.
- Regulatory Compliance: e-IDV aids banks in meeting Know Your Customer and AML compliance. By verifying identities against databases and watchlists, banks can identify those involved in fraud, protecting firms from non-compliance fines.
- A Streamlined Customer Experience: e-IDV solutions also focus on delivering a seamless and convenient customer experience whilst prioritising fraud risk mitigation. Automating the identity verification process enables banks to reduce manual efforts, paperwork, and delays associated with traditional verification methods.
Overall, electronic identity verification enhances the security of banks by accurately verifying customer identities, ensuring regulatory compliance, detecting fraudulent activities, and preventing unauthorised access or account takeovers.
How Can Shufti Help?
Shufti offers a robust e-IDV solution that verifies individuals through unique ID numbers and is fully adaptable to location and language.
Here’s what makes our e-IDV solution stand out:
- Faster Processing Time: Collect, analyse, and authenticate customers’ data through an e-IDV process to verify identities within seconds.
- Effective Fraud Prevention: Use verified government databases to cross-check customer information, mitigating the risk of identity theft and fraud.
- Increased Conversion Rates: Offers clients an unmatched verification journey with a seamless process and faster onboarding than traditional KYC.
- Global Compliance: Robust data security ensures businesses adhere to mandatory data privacy regulations whilst meeting your firm’s compliance requirements.
Want to know more about how robust e-IDV solutions help banks mitigate the risk of fraud?











