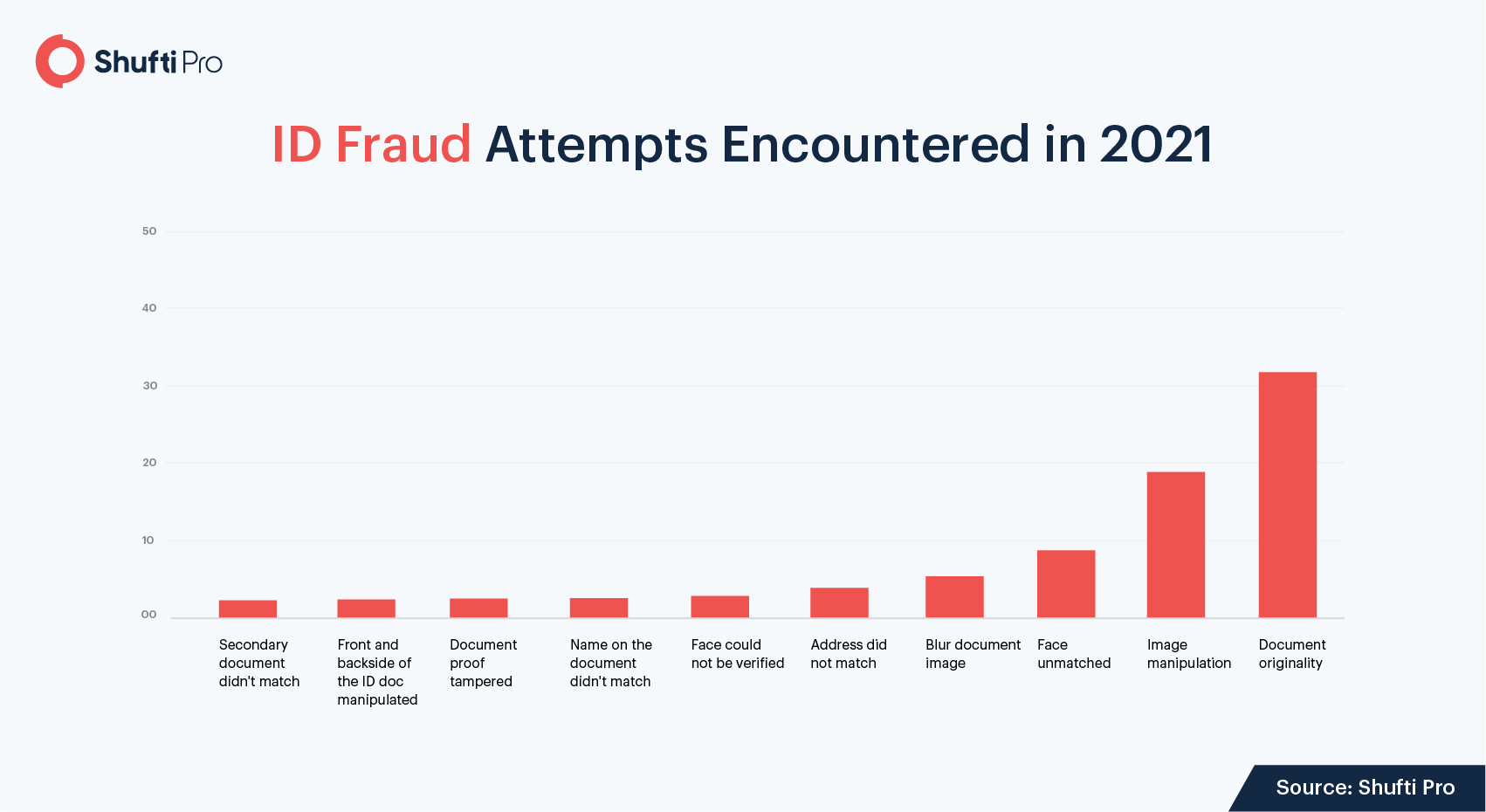
Top 5 Most Common Identity Fraud Attempts in 2021

Fraudsters in the post-pandemic world took complete advantage of rapid digitization. Bad actors became smarter and strategically stronger. Last year, Shufti encountered an approximately 3.36% increase in identity fraud and spoof attacks were on the rise. This year, the identity fraud statistics took us by surprise and new trends emerged. Fraudsters have ditched the 9 – 5 work cycle too and the remote working alternative has brought convenience for them. Bad actors used enhanced technology to tamper with ID cards, driver’s licenses and passports for dodging identity verification. Cryptocurrencies were the top trend in 2021 and not just for the sake of investments, but for illegal activities too.
With 2022 right around the corner, businesses must beware of the top 5 most common fraud attempts in 2021.
1. Blur Image on the ID Document
One of the oldest tricks in the book is to provide blur images of any document that is stolen. Bad actors did the same to manipulate the identity verification system. Thanks to enhanced AI, it took no longer than a second to notify about the fraud attempt. Apart from blur images of the uploaded identity document, bad actors tampered with the image on the ID document. The blurred faces and failed face verification were commonly reported.
2. Tampered MRZ Code and Rainbow Prints
Machine Readable Zone or MRZ codes are not easy to forge in identity documents. The encrypted data is the key to verifying an identity. Surprisingly, bad actors tried to mess with MRZ codes this year. Although they could not succeed in dodging the screening phase, they are ready to figure out a way to do so in the years ahead.
Forging of rainbow prints and holograms spiked high in 2021. Be it a driving license, national identity card or a passport, perpetrators used counterfeit versions. While verifying identity documents, the rainbow print detection failed since they were missing from counterfeit ID proofs.
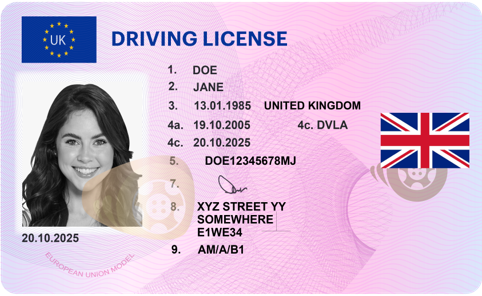
Here’s an original driving license
Here’s a forged driving license with no rainbow print

3. Expired ID Documents
Who wouldn’t want to use stolen or expired identity documents for verification when the motive is to create an account for illegal activities? Shufti accepts identity documents that have not expired and the secondary proof (a utility bill in most cases) must not be older than three months. However, expired documents and unavailability of secondary proofs helped us identify fraud attempts.
4. Facial Spoof Attacks
Deep fakes, face masks, and replay attacks are common spoof attempts that we encounter every year. However, these fraud attempts are more sophisticated now. By using artificial intelligence and machine learning algorithms, deep fakes have become more common than before. According to Cybernews, the number of expert-crafted deep fakes doubles every six months. Tampered videos of end-users were repeatedly used to manipulate the system. Fortunately, the system deploys thousands of AI models to verify an identity, making these attempts useless.
Recommended: Top 10 Biometric Technology Trends to Watch For in 2022
5. Different Primary and Secondary ID Proof
For higher authenticity of identity verification results, getting a secondary proof (usually proof of address) is better. It’s easier to forge an ID card or primary proof of ID but what about the secondary proof that bad actors overlooked? This year, verifications failed because many end-users (fraudsters) were unable to provide a secondary proof. In most cases, the provided primary and secondary proof of identity did not match.
Solutions to Fight ID Fraud in 2022
Shufti offers many solutions to businesses to prevent fraudsters from causing any trouble.
1. KYC Verification
KYC verification system is the answer to all your prayers. Backed by artificial intelligence and machine learning algorithms, the system verifies identities in real-time and takes about a second for the verification to complete. Here’s how the process goes:
- End-user uploads the government-issued identity document (ID card, passport, driving license)
- The document undergoes multiple checks to verify originality
- Then, the end-user uploads picture of their face for face verification
- Certain liveness detection and anti-spoofing techniques are used to verify the face
- Verification results are delivered in real-time and stored in the back-office
Recommended: A complete guide to understanding KYC compliance regulations
2. NFC Verification
With NFC Verification, ensuring a touchless identity verification experience is easier for businesses. The process is simple yet robust enough to prevent bad actors from fulfilling their illicit plans. Four simple steps and identity of the end-user is verified using a chip-based identity document.
- End-user uploads the chip-based identity document
- End-user taps the chip-based identity document on an NFC-enabled device
- Data on the document and in the NFC chip are matched
- Verification results are delivered in real-time
Suggested Read: NFC – Building New Grounds for Identity Verification
3. Video Interview KYC
Given the evolving regulatory landscape and strategically stronger criminals, Video Interview KYC is one of the most viable solutions to verify identities. The live interview makes it convenient for experts to combat fraud attempts. Here’s how easy it is to verify end-users on a live video call:
- End-user registers on the platform
- End-user and KYC expert get in touch on a live video call
- KYC expert interviews the individual for liveness detection
- End-user shows government-issued identity document on the video call
- Document is verified for any sort of manipulation
- Face of the end-user is matched with the image on the document
- Verification results are delivered
Suggested Read: Video KYC – Understanding the ‘what’ and ‘how’ [A short guide]
Key Takeaways
Unfortunately, perpetrators have taken the high road for their illicit gains. They are smarter and planning to stay one step ahead of businesses in 2022. Before we step into another year of surprises, it’s better to learn from the most common fraud attempts of 2021. Tampered MRZ code, blur images of identity documents, spoof attacks, expired ID documents, passport manipulation, and tampered rainbow prints are some of the techniques that have become hard to detect without enhanced AI. Businesses that lacked robust identity verification systems faced hefty non-compliance penalties along with loss of customers.
Before it gets too late, employ AI-backed identity verification and start onboarding legitimate customers in no time.