7 Ways to Protect Business and Remote Staff from Cybercriminals

- 01 Cybersecurity Tips for Companies and Remote Workers Amid Covid-19 Lockdown
- 02 Check for Security Vulnerability
- 03 Protection for Malware/Ransomware
- 04 Use of VPNs
- 05 Cloud Storage
- 06 Deploy Identity Verification Solutions
- 07 Educate Employees about CyberSecurity
- 08 Software Updates & Strong Passwords
- 09 In a Nutshell
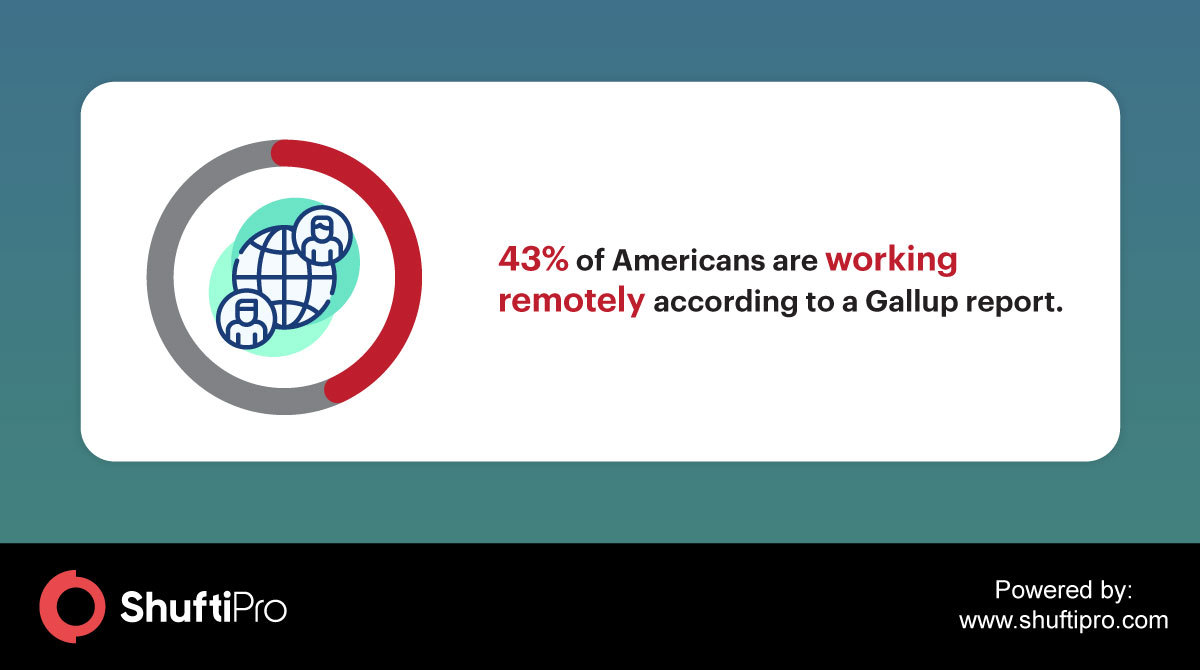
Businesses are facing ‘new normal’ as the workplace has shifted from offices to homes amid coronavirus pandemic. This has made many businesses keep running but added vulnerability too as the company’s data is being accessed from different servers and locations. Remote work is a trend that is being widely adopted in this pandemic to keep businesses operating but companies need to take steps to safeguard their data and team members against cybercriminals taking advantage of the current situation. In this blog, we’ll discuss some preventive measures that businesses need to take to prevent cyberattacks during coronavirus pandemic.
Cybersecurity Tips for Companies and Remote Workers Amid Covid-19 Lockdown
Businesses need to go on, work has to be done, so effective security measures have to be observed for businesses implementing WFH policy. Due to the current crisis, employees are pushed to work from their homes and get their work done effectively in inconducive environments and protect company data from unauthorized access. Cybercriminals are smart and will not let a good crisis go to waste. They will do whatever they can to exploit data and hardware device security vulnerabilities that can arise due to remote workers.

Here are some ways businesses can protect cyberattacks while implementing remote work policy:
Check for Security Vulnerability
To detect vulnerabilities and offer solutions, ethical or white-hat hacking is the act of legal penetration testing done by a cybersecurity expert on organizations’ information systems. Relevant solutions are suggested based on that hacking for enhanced cybersecurity. Ethical hackers must be hired to check for potential security threats. Moreover, this gives companies a better sense of understanding their security vulnerabilities so that they can implement more robust defense measures to prevent data breaches.
Protection for Malware/Ransomware
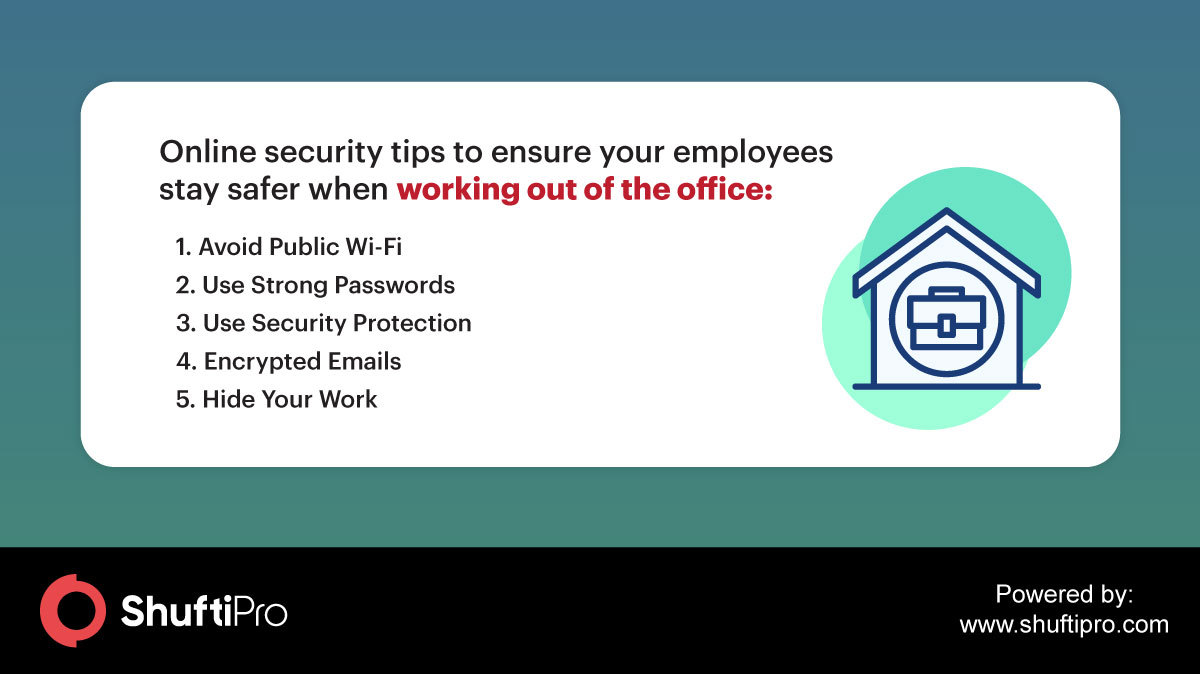
Malware is malicious software that allows the cyber attackers to gain control of the desired computer or system. Ransomware is a type of malware in which the attacker demands a ransom to give control of the computer or system back to the victim who is the rightful owner. If the victim fails to pay the ransom, the hackers release small amounts of data to force the victims to pay. Remote employees can protect themselves against such attacks in the following ways:
- Always inform the company’s security experts when moving or using a different computer than the one provided to them.
- Avoid using open public Wi-Fis.
- Do not open suspicious emails or attachments.
- Always update all software and use reputable antivirus software or firewalls.
Use of VPNs
A virtual private network (VPN) allows organizations to safely connect to a computer when they are using a less secure network. Using a VPN offers privacy and protection for company’s data from being accessed by unauthorized sources.
Cloud Storage
Companies should use cloud-based services authorized by security experts to store data and encourage their remote workers to do so. In case the computer malfunctions or is stolen, this will protect any kind of data loss.
Deploy Identity Verification Solutions
Identity verification solutions assist businesses to comply with Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations. To mitigate the risk of scams while working remotely these solutions play a vital role. Knowing who you are dealing with is an uphill task but it is very crucial especially when you are operating online. Moreover, as the staff is working from their homes how can the businesses be a step ahead to properly secure the company from fake identities? Digital ID verification solutions provide contactless technology to conveniently carry out cumbersome procedures of KYC, KYB, and AML. This technology provides a remote solution by authenticating identities and other businesses in real-time using document verification and biometric technology. Knowing your employees remotely through biometric identification service can harden your WFH process.
With a face verification solution using a 3D liveness detection feature, you can always authenticate an employee working from afar.
Read More: Working from Home Spikes Demand for Digital Identity Verification
Educate Employees about CyberSecurity
Businesses must give awareness to their employees about the basics of cybersecurity such as phishing emails, ransomware, malware, antivirus software, avoiding using public Wi-Fi, etc. There should be an emergency response team that remote workers should contact when something suspicious takes place. As it is said that a stitch in time saves nine.
Software Updates & Strong Passwords
Remote workers must update their software to the latest version in line or the security team should set your system to update automatically when there is a new version available. This will save businesses from falling in the pit of scammers. Moreover, strong passwords must be used by remote workers to minimize the chances of being hacked. There are many online password generators that individuals can turn to create strong passwords using upper case and lower case letters, numbers, and symbols. To reduce the probability of being hacked through brute-force attacks the passwords need to be changed periodically.
In addition, 2-factor authentication is strongly recommended to avoid unauthorized access in case if the hacker has got your credentials.
In a Nutshell
These are unprecedented times in which both businesses and the government are still navigating their way around this Covid-19 pandemic. It is through these tough times that cybercriminals will exploit those businesses who drop the guard. It is the duty of both businesses and employees to protect private data from falling in the wrong hands.

 Explore Now
Explore Now













