Fight Fraud Proactively and Reduce Fake Customer Accounts With Shufti’s AI-powered ID Document Forgery Detection

- 01 Document Forgery - Everything Businesses Need to Know
- 02 History of Document Forgery - A Detailed Overview
- 03 Document Forgery in the Digital Landscape [2022 Update]
- 04 Why do Fraudsters Fake Certain Documents?
- 05 Capturing and Validating Identity Documents: A Decisive Moment
- 06 Forensic Document Forgery Detection - A Refined Measure
- 07 Forensic Document Verification - How is it Performed?
- 08 Some Regulations Against Document Forgery
- 09 Canada
- 10 What Role Does Document Verification Play in Compliance?
- 11 How Shufti Can Help
Bank statements, land documents, and social security checks are frequently forged. Document forgery used to be quite a challenging task before digital transformation took its hold on the global economy. In today’s social media age, data scraping and photo editing tools are making it easier to gather personally identifiable information that can be used to design a fake document. However, the practice of creating fake documents to manipulate legal systems is not a new concept. Document forgery has a long history that costs businesses billions of dollars annually in losses, penalties, and brand reputational damage.
Often, there is a prank element with document forgery which is why forgery detection solutions have become a critical part to identify such fraudulent attempts, yet debates about the validity of documents are often long drawn out controversies. Recent advances in how to identify ID documents forensically have also highlighted the need for more sophisticated and informed methods to overcome the challenge of authenticating refuted information. However, technology is evolving these procedures making them smarter and more robust. This is great not only for businesses but also unfortunately also becoming favorable for criminals who are looking to manipulate banks and other institutions.
Document Forgery – Everything Businesses Need to Know
Document forgery is a serious crime that involves the creation of fake ID documents to give the appearance of legal significance that is not true.
The most common types of forged documents are:
- Passports
- Driver’s licenses
- Checks and Financial Statements
- Invoices and Contracts
- ID cards and birth certificates
There are numerous kinds of techniques to forge a document, including falsifying information or replacing the images in the authenticated documents.
Top 3 types of Document Forgery
- Freehand Simulation: This is when a document forger tries to replicate the handwriting, signature, or design of legit identity documents.
- Tracing: Duplicating handwritten text, official signatures, and document designs through transmitted light or carbon tracing, in which a criminal places a sheet over the original documents to make identical forged copies.
- Electronic Manipulation: Using photoshop or any other photo editor to copy the signatures imprinted in legal documents and then paste them into fake copies, as well as manipulating other information.
History of Document Forgery – A Detailed Overview
The art of document forgery is as old as the alphabet. This crime has been practiced since ancient times in every country around the world where writing existed and paper-based identity or financial documents were used for legal activities and transactions. Various laws and regulations to fight the document of grey can be traced to 80 BC when the government of Rome prohibited the creation of false land transfer documents. Forgery was also prevalent in Europe in the middle ages but with time laws were introduced to restrict such criminal activity in every developed country. Yet, over time it became challenging to detect sophisticated forgeries attempts.
In 1562, the Government of England passed a law prohibiting the forgery of public records and officially sealed documents especially as it related to land.
In 1726, with the expansion of these laws, false endorsement on unsealed private documents was declared a capital crime punishable with the death penalty. Hefty fines, imprisonments, and pillory were also among the penalties for non-compliance.
In 1819, the Government of England issued one-pound currency notes made with simple pen and ink inscriptions on ordinary white paper which increased the number of forgery cases. Over the next seven years, nearly 94,000 criminals were arrested and 7700 of them were sentenced to death for making fake pounds.
In 1823, the Government of the United States came up with a principal federal forgery law to prohibit forgery or the manipulation of legal documents for the purpose of gaining financial benefits. The American Law Institute’s Model Penal Code of 1962 simplified and clarified the elements of forgery and became the standard for defining forgery-related crimes.
Famous Document Forgeries that Changed History — Almost
History is full of cases where document forgery, falsification, and manipulation affected governments, businesses, and individuals. Many papers believed to be authentic looked legitimate until they were later proved to be fake. Paper-based documents have existed for centuries to govern every aspect of society, from literature to history to law. Since then, criminal masterminds have intentionally created duplicate or fake versions of famous and government documents to reap personal and financial gains.
Here are some of the famous cases of historical forgeries along with their climax – a time when document falsification and forgery were eventually exposed globally;
Shakespeare Forgery
Sometimes criminals don’t create fake documents for money. William Henry is an example of a manipulator who forged documents to get public attention. The forger claimed to find a stack of plays and several letters written by the famous writer William Shakespeare in 1975. As Henry belonged to a trustworthy family, people began to believe that the documents were legitimate. In practically no time, the fans of the famous writers agreed that the letters were indeed written by Shakespeare. Meanwhile, when the letters and stories began to get published, many people reached with suspicion. Once the public had the opportunity to verify the writing, it became crystal clear that it was an elaborate fraud. Years later, the convicted forger confessed and was eventually held answerable for his blatant fraudulent activity.
Adolfo Kaminsky Forgery
Not all document forgery activities were carried out for personal gains. Adolfo Kaminsky, a teenage freedom fighter trapped in occupied France after World War 2, is an exceptional example. The boy tried hard to understand how dry cleaning chemicals worked to create fake documents with the aim of saving the many Jews held captive in Nazi-ruled areas. Adolfo even worked with the French Resistance after they were released. The forger had expertise in dry-cleaning as well as sound knowledge of other general chemicals, which was necessary to recreate crucial documents such as birth certificates, marriage licenses, and food ration cards.
Hitler Diaries
In 1928, the German Federal Archives at Coblenz contacted Bundeskriminalamt with a request to confirm the authenticity of several historical documents. These official papers, allegedly written by Adolf Hitler, had been offered to stern, a West German magazine, which was interested in purchasing them. However, after a journalistic campaign, the Federal Archives were told that Hitler’s diaries could be provided to them for free if they established expert opinions that would not leave any doubt about the authenticity of the documents. An initial forgery analysis revealed that all the documents were examined in daylight which showed a lesser white effect than is found in common writing papers used today. Furthermore, under UV light examination, all the document samples disclosed fluorescence typical of white dyes but which was completely different from the chemical composition of the original documents. The examination results confirmed that the documents were most certainly forged by a criminal named Konrad Kujau.
Document Forgery in the Digital Landscape [2022 Update]
For decades, forgers have been targeting businesses, government institutions, and individuals to manipulate them for personal gain. The same frauds are still being performed today but we hardly hear about them because big brands do not like to publicize when they’re defrauded. Unfortunately, humans naturally find such criminal news and stories exciting, which is why they often garner vast attention. While these criminal cases have great potential to inspire today’s fraudsters, most modern forgers are making efforts to find creative new ways to commit this age-old crime by leveraging the latest techniques and technologies.
Today’s sophisticated fraudsters risk their freedom for many good reasons. The rewards of successful forgery attempts are enormous because digital commerce has made the impossible quite possible to potentially make millions at a click of a button. Digitisation and technological transformation have accelerated which fraudulent activities are conducted and evolved in terms of the types of scams that are now occurring. Simply put, document forgery is now widely considered a white-collar crime that is affecting businesses worldwide.
Nowadays, data is also considered a form of currency as the proliferation of personally identifiable information including bank details, financial credentials, ID numbers, and other private information opens a way for fraudsters to defraud the system. Large-scale data breaches including account takeover scams and Card-not-Present (CNP) fraud continue to occur resulting in the theft of countless personal and financial records each year. Often, the abducted data is being used to create fake documents which are further used to open bank accounts, credit cards, claim insurance bonuses, and much more.
The rapid development of eCommerce solutions and the willingness of global customers to shop online have also prompted fraudsters to carry out document forgery activities for personal benefits. On another hand, technological transformation is also aiding criminals to carry out their malicious acts. Shifting from providing bad checks to replicating credit cards, they now have instant access to vulnerable data available over the net, especially the ID documents commonly being sold all over the dark web. According to various experts, in this digital era, every 22 seconds, a new victim is being victimized. Unfortunately, this trend is not showing any signs of slowing down, making it a much bigger issue worldwide than ever before. The United States FTC also claimed that it received 2.8 million fraud reports in 2021. Thus, as technology is evolving, so is fraud, with estimates showing fraud rates will continue to increase over time.

Why do Fraudsters Fake Certain Documents?
Document forgers actively seek out certain countries with lower security levels and weak regulatory systems to try their luck. Particularly, Identity card documents have a higher exposure to forgery because in many countries the national ID documents have fewer security features such as watermarks, holographic patterns, unique inked stamps, etc, which is like winning the lottery for fraudsters. Some countries have electronic identity cards that can be simply printed out on a piece of paper. Such documents have little or no security features, except maybe a QR code.
Legal Loopholes
Many countries across the globe have certain loopholes in their laws that provoke fraudsters to falsify documents without facing legal actions or penalties. For example, Article 327 of the Russian Criminal Code clearly states that the manufacturing or forging of legal documents for the purpose of use or sale is illegal. However, if the systems fail to prove that the documents are forged for use or to sell, the cases can’t be prosecuted. That’s why fraudsters use such shortcomings in law to forge documents knowing they’re highly unlikely to be held accountable.
No Privacy Awareness
The severity of data privacy and protection laws for securing sensitive information varies country-wise. In Europe, there’s a strict data protection law called “GDPR” yet only 67% of EU citizens are even aware of it. However, the situation in other countries across the globe is way worse. For example, only half of 54 countries in the African region have adequate data privacy and protection laws, unfortunately leaving millions of people helpless in case of a data breach.
Citizens not Following the Law
Countries where people are not following laws are more prone to criminal activities as compared to jurisdictions where regulations are strictly enforced. According to the WJP Rule of Law Index 2020, the people of Denmark, Finland, and Norway are the most law-abiding. On the other hand, Cameroon, Cambodia, and Venezuela are among the most exposed countries where the law is not enforced properly resulting in an evident increase in Identity theft and document forgery cases.
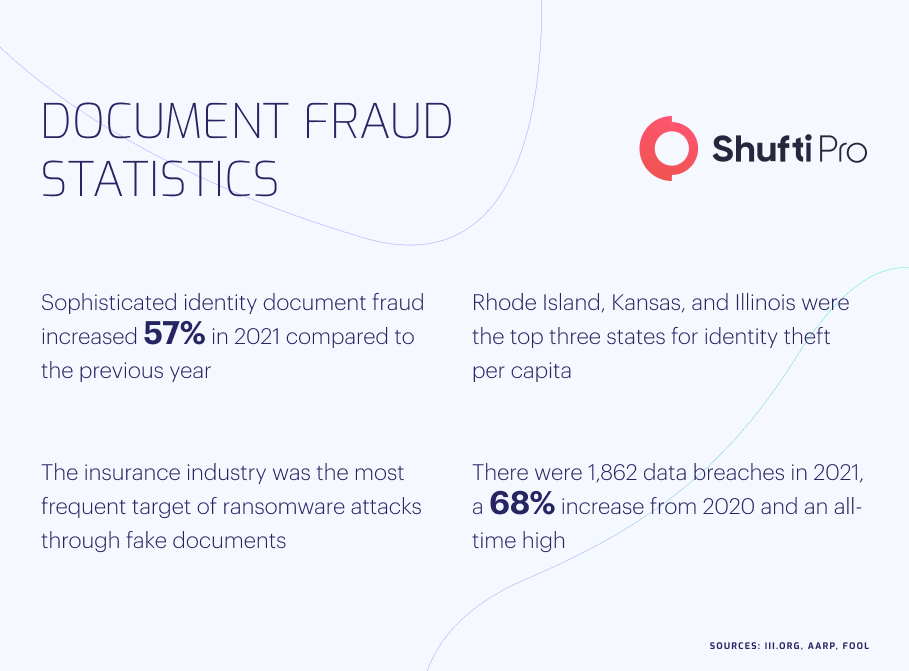
Capturing and Validating Identity Documents: A Decisive Moment
Nowadays, businesses are witnessing significant growth in remote services which has been possible due to the integration of emerging technologies. As a result of this, people are not required to visit an office or a physical location which is turning into a nightmare for businesses as remote services are allowing fraudsters to use other people’s identity information to create fake copies often processed using high-end photo editing software.
Rapidly-growing deep fake technologies are also paving new opportunities for criminals to carry out identity spoofing. Therefore, due to the increased risk of ID theft and document forgery, identity verification solutions used for physical and remote customer verification and document authentication are becoming more sophisticated.
Document security is continuously enhancing; ID documents such as passports, identity cards, and driver’s licenses are becoming more complex technically by incorporating top-notch security features like special protective drawings, holograms, and ink that changes when the light or the angle of inclination changes. For example, passports in many countries have some protective features now that only become visible when a light is reflected, or when they are exposed to ultraviolet light. On top of this, many identity documents also come with machine-readable codes that contain all of the essential information about its owner embedded within the document. Other than this, various countries have also introduced biometric-based official documents containing personally identifiable information including the photo and digital signatures embedded in them.
Forensic Document Forgery Detection – A Refined Measure
Emerging technologies have not only helped businesses with the security of their operations but also eased the ways for imposters to deploy more sophisticated techniques to manipulate security systems. A lot of digital service providers such as Walmart, Amazon, Paypal, Payoneer, and many others have incorporated regulations to verify their customer documents. Yet, conventional methods of authenticating documents are not liable to serve the purpose of restricting fraudsters from using forged identities. In the UK alone, customers lost £1.3 billion to fraudsters last year which shows a 27% increase from 2020. Therefore, it can be concluded confidently that existing document verification solutions are not enough to control advanced fraud methods which is why businesses need forensic authentication that is more sophisticated and has the capacity to fully counter modern-day scams.
Digital service providers such as technology companies, financial institutions, and immigration departments are at a high risk of document fraud. Imposters deploy forged documents to bypass security, claim the money, submit admissions to colleges & universities, or apply for visas to foreign countries. All online businesses can safeguard their customer onboarding system by incorporating forensic forgery detection techniques that leave no room for criminals to carry out such fraudulent activities.
Document Checks: Ensuring High-Quality Evidence
Documents such as identity cards, wills, contracts, deeds, stamps, bank cheques, and machine-generated files hold special security features that need to be verified in order to detect signs of forgery.
Official documents that don’t have high-security features like identifiable marks may contain hidden impressions. In case, when fraudsters try to replicate official papers by placing them under another document for tracing the genuine format, noticeable traces are left that can be easily detected. Even the discarded documents that were shredded may prove to be valuable for examination. In digital documents, the metadata of the electronic signature files is also examined for verification as it contains essential information about the owner.

Forensic Document Verification – How is it Performed?
Forensic document forgery detection can be carried out in two primary ways; either the examiner can perform a forensic exam in a laboratory or one can use a digital document verification solution. If a given agency lacks document forgery analysis capabilities and tools, it can simply outsource document forgery detection to a technology provider like Shufti.
Forensic document forgery detection involves the implementation of scientific rules in verifying document authenticity. To do so efficiently, technology companies and SaaS providers have come up with digital document forgery detection solutions.
In this modern era, the use of forensic sciences is rising, especially in legal and government sectors where no documents are accepted without thorough verification. By utilizing various techniques like handwriting validation, ultraviolet ray examinations, microscopic analysis, data extraction with OCR technology, and infrared imaging, a document is rigidly examined to detect signs of forgery if present. All major jurisdictions that address fraud seriously where document verification is required have formed a separate department distinctly for this purpose. Likewise, the American Board of Forensic Document Examiners (ABFDE) is the primary department overlooking document forensic operations in the US.
Some Regulations Against Document Forgery
Document forgery, identity theft, and other serious crimes are prevailing across the world, raising critical questions for regulatory authorities as well as businesses worldwide. Therefore, many countries have taken initiatives and are legislating laws to fight fraud proactively.
Australia
Under the New South Wales Crimes Act 1900, falsification of signatures is a serious offense where the penalties could be severe, including imprisonment for up to ten years. Other laws are also applicable if the documents turn out to be forged and are being used for personal gains. Section 235 of the Crimes Act states that if an alleged entity is found guilty of document forgery, with the intention of using or selling false documents to others, then it is to be held accountable. In addition to this, under the Australian Federal Law, there are serious consequences for forgery offenses. Under section 144.1 of the Commonwealth Criminal Code Act 1995, the convicted entity can face a penalty of ten years in jail.
Canada
According to Canadian Criminal Code 366(1), forgery is when criminals make a fake document, knowing it to be false, with the intention of using or selling it as a legit official document. Under the law, the prosecution can proceed on a summary or indictable basis. Indictable offenses are considered more serious than summary offenses and thus they result in heavier penalties. The maximum penalty for document forgery in Canada is set to ten years in jail, or have to pay a $5,000 fine on a case of summary basis. Forgery cases could become complex and the penalties can lead to serious consequences.
What Role Does Document Verification Play in Compliance?
Digital document verification is not necessarily required as a compliance standard even in regulated industries. However, they practice a manual approach to verify their client documents before onboarding.
The continued growth of digital services and expansion of online platforms has fueled the demand for remote onboarding and online verification to make the customer experience seamless. However, to meet client demands, various challenges for businesses are emerging to carry out identification manually which drives the need for digital document verification services.
One industry in which online onboarding services and regulations lead is financial institutions. After the world trade center tragedy and the formation of the Department of Homeland Security, along with the Patriot Act various other regulations were legislated to fight fraud, restrict money launderers, and halt terrorist activities.
In response to these activities, the following two major regulations were brought into the light which are incomplete without practicing document checks.
- Know Your Customer: This mandates financial firms to incorporate rigorous customer due diligence procedures, including effective digital identity and document verification measures that can determine the true identities of customers before getting them onboard.
- Anti-Money Laundering: These laws are intently legislated to curb money laundering and terrorist financing activities worldwide. This includes screening customers against financial crime databases, PEPs, and watchlists. In many countries, AML also requires KYC checks as well.
How Shufti Can Help
Identity documents are deemed to be legitimate sources of authenticating customers. Any kind of fraud associated with documents can result in serious consequences i.e. penalties or sanctions. It’s critical for digital businesses to incorporate document forgery detection solutions in order to meet KYC & AML compliance as well as fight evolving crimes. By having document forensic analysis in place, businesses can easily determine the signs of forgery and restrict criminals before getting them on board.

Shufti’s state-of-the-art document forgery detection solutions can easily identify all sorts of fake, illegitimate, and counterfeit documents in less than a second with 99% accuracy. Embedded with thousands of AI models and powered with OCR technology, our innovative document forensic analysis service can validate 3000+ document types while enabling businesses to onboard legit customers and ensure a risk-free experience.











