The Emerging Threat of DeepFakes and the Role of Video KYC

With technological advancement, cybercriminals are revising their strategies to commit fraud. Criminals are using deepfakes to launch a cyberattack in this digital era. Recent survey results unveiled that 66% of cybersecurity professionals surveyed have observed the incorporation of deepfakes in cyberattacks. This marks a 13% surge compared to the previous year. Email emerged as the dominant delivery method in 78% of these attacks. Thus, video KYC is a powerful tool, effectively addressing these evolving challenges.
Understanding Deepfakes
Deepfake technology utilises sophisticated artificial intelligence and machine learning algorithms to generate realistic videos, audio recordings, images, and text-based content such as SMS or written materials. This advanced technology enables the creation of media that closely mimics the appearance and voice of real individuals. The realistic appearance of deepfakes makes them particularly potent in executing “social engineering” operations, aiming to deceive individuals into disclosing sensitive information, unknowingly participating in financial fraud, or granting unauthorised access to corporate networks.
Deepfake attacks are an evolution of spear-phishing and business email compromise scams, falling into a newly recognized category of criminal activity called “business identity compromise” by the FBI.
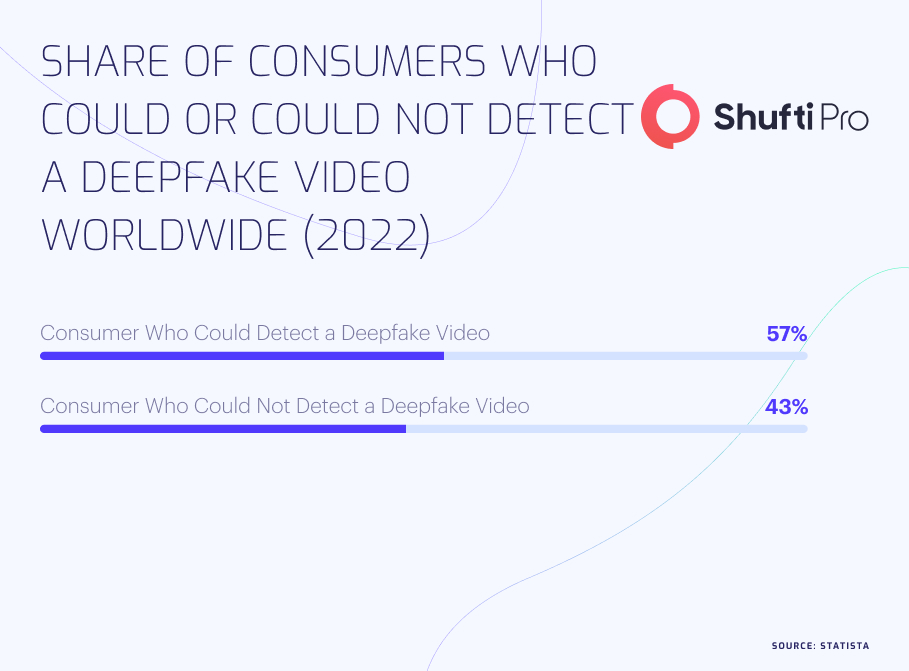
Recent Stories of Criminals Using Deepfakes
Let’s have a quick recap of some recent stories where criminals used deepfakes:
Scammers employed deepfake hologram technology to create a deceptive virtual representation of a cryptocurrency chief communications officer. This hologram was then utilised during Zoom calls to deceive cryptocurrency executives, coercing them into divulging confidential information unknowingly.
Using real-time voice cloning techniques, criminals successfully imitated a director’s voice from a Dubai bank. They managed to trick a Hong Kong bank manager into transferring $35 million to the criminals’ organisation. The counterfeit voice was so convincingly authentic that the manager “recognised” it during the phone conversation.
In a separate incident, an organisation unknowingly hired an individual posing as a remote employee who had fabricated a false identity using deepfake technology and stolen personally identifiable information. The criminal intended to gain unauthorised access to the company’s network and sensitive data under the pretence of providing technical support.
Hackers resorted to sending falsified voicemails, replicating the voice of a CEO, with requests for employees and external suppliers to contribute to charitable or disaster relief causes or make investments via manipulated websites. Unbeknownst to the recipients, these fake websites redirected the funds to offshore accounts controlled by hackers.
Additional cases included third-party phishing, where hackers infiltrate or establish counterfeit marketing email services or social media profiles to dispatch phishing emails. Furthermore, Search Engine Optimisation (SEO) phishing techniques have been employed, involving creating fraudulent websites and manipulating key search terms to ensure the counterfeit site appears higher in search results than the genuine one.
Video Verification to the Rescue
The increasing adoption of virtual solutions in companies to facilitate remote work amplifies vulnerability to such crimes. Over the past few years, the FBI and its Internet Crime Complaint Center (IC3) have issued multiple alerts, emphasising the importance for organisations to familiarise themselves with deepfake attack techniques. These warnings serve as a reminder of the need to stay informed and vigilant in the face of emerging threats. One of the best ways to mitigate the risk of such scams is by deploying robust video verification solutions. They not only protect against deepfakes but are promising solutions for businesses in several ways, such as:
1. Secure Onboarding Procedure
Ensuring a secure and trustworthy customer onboarding process is crucial for enterprises. The integrity of this process is vital as it can determine whether a customer poses a potential threat to the business or may become a victim of illicit activities. Video KYC plays a significant role in verifying the identity of customers, thereby preventing criminal acts and unauthorised resource utilisation. In cases where there is an attempt at impersonation or submission of forged documents, the keen observation of an expert during a video call can help identify fraudulent activities. Consequently, the verification process detects such instances, halts the onboarding process, and reports unauthorised authentication.
Video KYC services operate in real-time, providing valuable customer support during onboarding. The inherent and interactive nature of video interaction enhances reliability. Any weaknesses in customer identity verification could expose the business to risks. The entire verification procedure is completed swiftly and securely within minutes. Customer identity details are securely stored in the backend system for future reference and verification. By eliminating potential vulnerabilities, Video KYC ensures a transparent onboarding process that safeguards against fraudulent activities.
2. Prevention of Identity Theft
The expansion of digital services has led to a significant rise in online identity theft, posing a growing security concern for enterprises. According to the financial report released by the Federal Trade Commission (FTC), there were approximately 651,000 complaints related to identity theft, resulting in nearly $1.7 billion lost in internet fraud cases.
Among various types of identity theft, payment card fraud was the prevalent technique employed by online fraudsters. A notable incident occurred in 2019 when MasterCard’s Loyalty programme in Germany suffered a major setback due to a privacy breach, jeopardising the identities of millions of individuals. Today, financial corporations face an elevated risk of identity theft due to synthetic account openings and data violations. Online businesses are adopting advanced measures to prevent data loss while conducting identity verification to counter this pervasive threat.
Incorporating comprehensive video KYC services proves invaluable in identifying instances of identity theft. These services often leverage artificial intelligence algorithms, offering superior detection accuracy compared to human expertise. Automated processes can effectively trace stolen card data by matching it against backend databases. Video KYC solutions are crucial to a company’s defence against online fraud, reducing identity theft risk through transparent and easily implementable verification procedures.
3. A Seamless Customer Experience
Creating a positive customer experience is paramount for businesses, directly influencing their market reputation and customer loyalty. This, in turn, impacts the company’s cash flow and conversion rates. Both startups and established corporations prioritise their customers’ satisfaction. Video KYC offers a convenient solution for validating user identities without customers needing to visit verification sites or engage in time-consuming procedures physically. Customers can now verify their identities from their homes through live video sessions.
Furthermore, the process becomes even more efficient and accurate when automated verification solutions are integrated with video KYC. Users can validate their identity by presenting identification documents or verifying their faces using mobile phone cameras, allowing the system to authenticate the information. Establishing a communication channel with video KYC services is as simple as making a video call to a friend. By leveraging video call KYC verification solutions, enterprises can gain insights into their customers’ identities and deliver personalised content that aligns with their interests, ultimately enhancing the chances of acquiring new customers.
4. Decreasing Operational Costs
Achieving a consistent cash flow while minimising operational costs is crucial for corporations. Striking a balance between revenue generation and the expenses associated with operations is vital for business growth. Implementing video KYC solutions allows companies to reduce operational costs related to manual verification and administrative tasks, which would be challenging without an online identification solution.
Video KYC providers are actively working towards delivering cost-effective solutions for video verification, thereby increasing the likelihood of online businesses adopting their services. Maintaining a positive customer experience while simultaneously reducing KYC verification expenses is essential. By leveraging video KYC, companies can minimise client onboarding costs while saving on operational expenditures.
How Can Shufti Help?
Shufti offers a robust video KYC solution that leverages artificial intelligence algorithms to verify identities through a video call, mitigating the risk of deepfakes, impersonation attacks and other types of fraud. Our robust video verification solution helps companies comply with global regulations and avoid heavy penalties. Moreover, the robust identity verification solution provides customers a seamless experience, building a positive brand image.
Want to know more about how video verification keeps scammers away?