The Ultimate KYC Checklist for 2023 to Ensure Regulatory Compliance

Non-compliance cost businesses billions of dollars. Regulators have charged financial firms with eye-popping penalties over not abiding by Know Your Customer (KYC) and Anti-money Laundering (AML) regulations. For example, one of the significant AML fines from 2022 included Santander UK’s £108 million and Deutsche Bank’s $7.1 million.
The cost of not complying with regulations is high, and the latest cases show how significant it is to implement a robust Identity Verification (IDV) solution. One must understand the checklist before deploying a KYC solution to ensure compliance.
KYC Checklist: 3 Steps to Ensure Regulatory Compliance
There are many guides on effective KYC, and it becomes difficult to determine which to rely on. Here is the KYC checklist, a summary of what essential things one must know about their customers.
1. Customer Identification Program (CIP)
Scammers are perpetrating white-collar crimes and wreaking havoc on businesses. Almost $8.8 billion were lost to scams in 2022, making clear how important it is to know your customers for effective KYC compliance. The main goal of checking customers’ identities during account opening or client onboarding is to mitigate the risk of any kind of fraudulent activity and to better comply with regulations.
Section 326 of the USA PATRIOT Act requires businesses to deploy a CIP programme that must include the following:
- A written document of the programme
- Customer’s Personally Identifiable Information (PII), such as name, Date of Birth (DOB), address, and government-issued identity number
- Identity verification processes
- Recordkeeping
- Crossmatching with government lists
- Notifying clients of the following steps to be taken
All businesses must check that customers’ documents and the other details they have provided are legitimate to keep fraudsters at bay. Companies can deploy safeguards like Two-factor Authentication (2FA) and face verification to double up security. Furthermore, firms must check any customer’s source funds and thoroughly monitor high-risk clients, such as those on Politically Exposed Persons (PEPs) and other watchlists. They must check who the Ultimate Beneficial Owners (UBOs) are to check the nature of their relationship with the organisation. This is the key to abiding by KYC and AML regulations effectively.
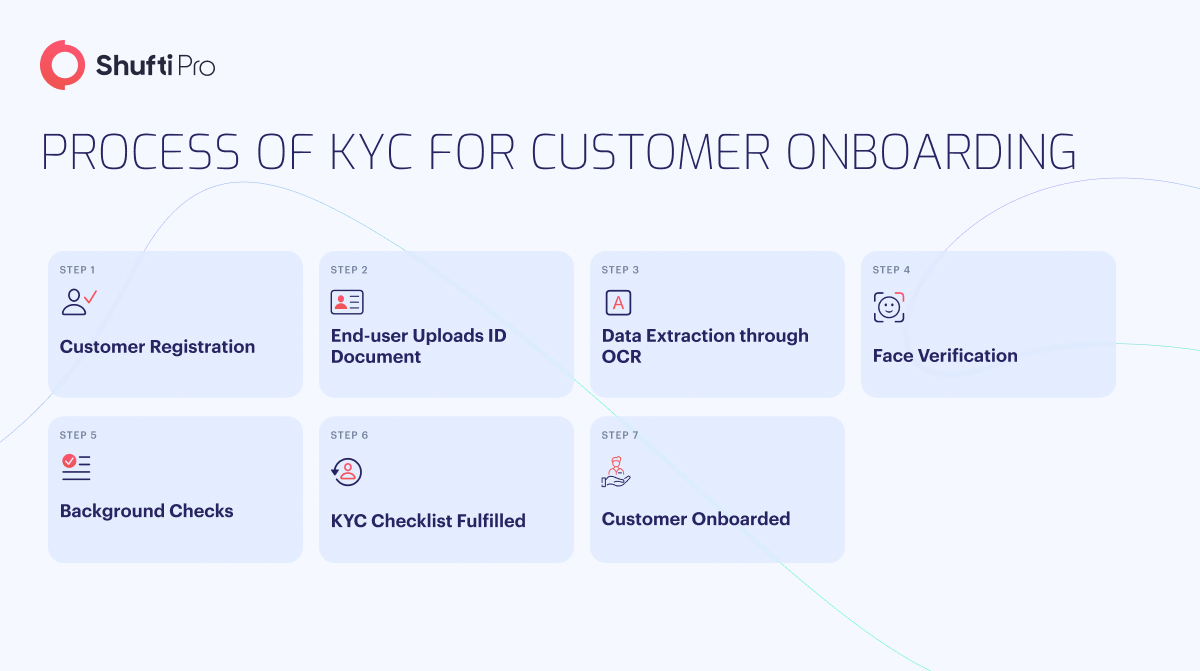
2. Customer Due Diligence (CDD)
One of the initial assessments made by financial firms is to check whether the client is trustworthy. This is where CDD proves to be a promising method that identifies high-risk clients and protects companies from exposure to heinous crimes.
Customer due diligence comprises three steps that include:
- Simplified Due Diligence: It is performed when the customer poses a low risk for financial crimes like money laundering or terrorist financing. The client is authenticated through PII; no further analysis is needed.
- Standard Due Diligence (SDD): The customer ID is cross-matched with the government database to authenticate their identity further.
- Enhanced Due Diligence (EDD): It is conducted when a customer poses a high level of risk for criminal activity. For example, businesses are required to perform EDD if a customer appears on a PEPs list, sanctions list, or watchlist or has adverse media coverage.
Here are a few practical steps for customer due diligence programmes:
- Determine the potential customer’s identity and location, and gather a comprehensive insight into their business activities. It can be easy to find a document with the customer’s name and address.
- Before digitally keeping any information about a customer or prospective customer, it is essential to determine what risk category they fall into and what kind of customer they will be.
- To determine if EDD is necessary, firms must do more than basic CDD and carry out the proper procedures. Because even low-risk consumers may gradually increase their level of risk over time, so this process may be ongoing. Therefore, performing due diligence checks on current customers every month can be helpful. Furthermore, when deciding if EDD is necessary, businesses should consider the customers’ location, occupation, expected transaction categories, dollar amount, and frequency. Thus, it is essential to keep comprehensive records of CDD and EDD for high-risk customers in the wake of a regulatory audit.
3. Ongoing Monitoring
A single inspection of the client is insufficient. Companies must implement a system that allows for continuous client monitoring. Financial transactions and accounts monitor continuously through predetermined criteria established as part of a client’s risk profile.
Aside from the customer and risk management approach, other areas to keep an eye on may include:
- Increase in activities
- Weird or unusual international activity
- Adding individuals’ names on sanction lists
- Adverse media coverage
If the transactions on the account seem illegal, businesses may need to submit a Suspicious Activity Report (SAR). Moreover, the best practices include periodic evaluation of the account and its risk. Other activities include;
- Is the current account information correct?
- Are the account’s personal finances comparable with its declared function?
- Do the amount and type of transactions match the risk level?
In general, the level of transaction monitoring relies on a risk-based assessment.
Where Does Shufti Step in?
Shufti offers an AI-powered KYC solution that is trusted globally. The IDV solution provider verifies identities within seconds and helps businesses keep scammers at bay. Shufti’s KYC solution prevents fraudulent activities and helps companies avoid fines by staying compliant with KYC and AML regulations.
Want to know more about how a KYC solution can help businesses ensure regulatory compliance?

 Explore Now
Explore Now













