Identity Verification vs Authentication: The Key Differences

Organisations today face significant concerns regarding data breaches and identity theft. Nearly 15 million data records were exposed globally during the third quarter of 2022. This figure had risen by 37% more than the previous quarter as criminals have become more resourceful and have found greater means to bypass verification checks. Additionally, scammers have shifted their focus towards compromising companies rather than individuals, aiming to gain access to confidential data. Thus, verifying customers during every interaction has become for businesses in this digital age. This objective is accomplished by combining two complementary approaches: identity verification and authentication.
Verification vs Authentication
Let’s delve into their comparisons across three key aspects:
- The Objective of Identity Assessment: Verification aims to establish the authenticity of customers by utilising various signals to validate their identity. On the other hand, authentication determines whether customers should be granted access to specific services or data.
- The Nature of Collected Data: Verification primarily focuses on transitioning offline identities into online platforms. To accomplish this, companies typically examine data that verifies an individual’s physical identity, such as government-issued IDs or selfies. In contrast, authentication emphasises proving identities and ensuring consistent user identification during login attempts. This method relies on data that may not directly match the user’s identity, such as passwords and 2FA codes.
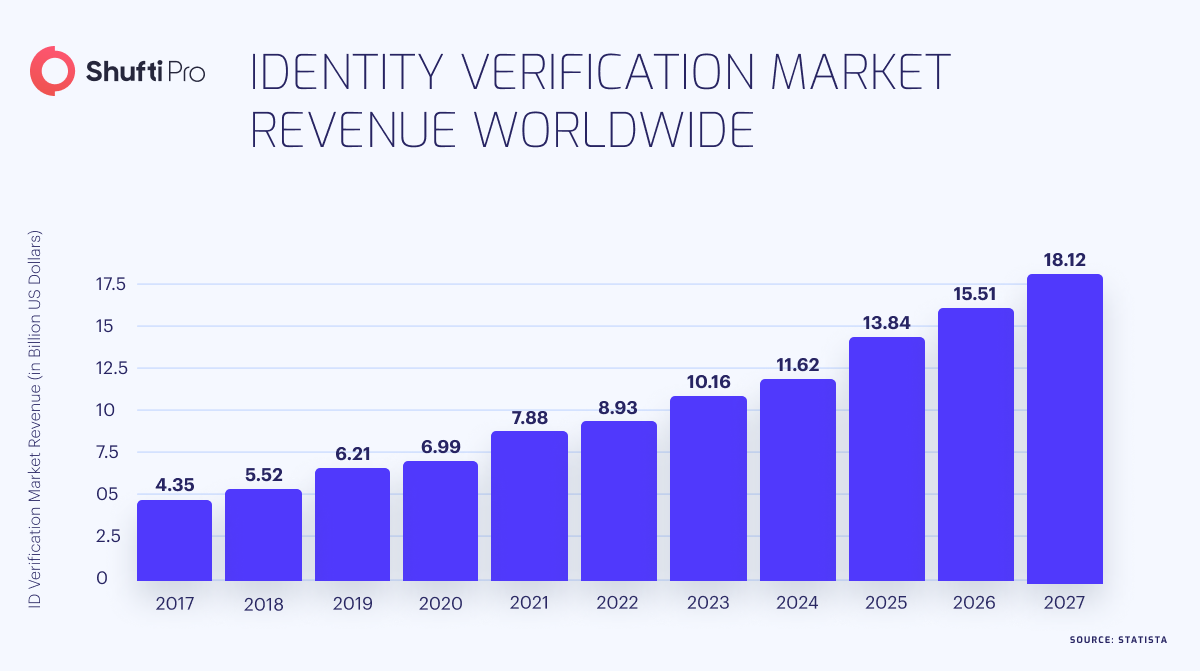
Diving Deeper into Identity Verification
Identity verification refers to ensuring a customer is who they claim to be. Different organisations may employ diverse methods for validation. For instance, one company may require users to provide their date of birth and Social Security Number (SSN) during onboarding, whilst another may request users to submit a photo of their driver’s licence and capture a selfie for identity confirmation. The advent of secure data capture and processing technologies has facilitated the rise of online identity verification.
Standard Methods to Verify an Individual
Businesses utilise a diverse range of indicators, called signals, to authenticate identities and check the accuracy of individuals’ claims.
These signals encompass various types:
- Active Signals: These signals are actively provided by the individual, including their details such as name, SSN, government-issued ID card, self-captured image, and supporting documents.
- Passive Signals: Passive signals involve information gathered about the individual, such as their IP address, device characteristics, or browser fingerprint, which is collected without their active participation.
- Behavioural Signals: Behavioural signals encompass indicators linked to user behaviour, including actions like hesitation, distraction events, and whether a person is using developer tools, copy/paste functions, or autofill features.
- Third-party Signals: These signals are derived from official lists, such as watchlists, adverse media reports, risk reports related to phone usage, and Politically Exposed Persons (PEPs) lists.
Different Methods of Identity Verification
Businesses have various options to choose from whilst considering identity verification solutions. Among the commonly used methods of identity verification are the following:
- Government ID Verification: This method typically involves users uploading a photo of their government-issued identification, such as a driver’s licence, passport, or other applicable ID, which is then subjected to verification. Often, it is combined with other verification techniques, including database checks and selfie verification.
- Digital ID Verification: With the increasing digitisation of identification documents, some businesses opt for digital ID verification. This entails accepting Mobile Driver’s Licences (MDLs), e-passports, and other IDs with Near-field Communication (NFC) capabilities. This approach provides users with more flexibility and streamlines the verification process.
- Document Verification: Document verification enables firms to collect additional documents besides government-issued ID cards. These documents verify different aspects, such as an individual’s address, employment history, income, and business documentation.
- Database verification: Database verification enables comparing user-provided information against authoritative databases, often managed by entities like the Department of Motor Vehicles (DMV) and the Internal Revenue Service (IRS).
- Selfie Verification: Selfie verification mandates users to submit one or multiple selfies, which are subsequently compared to the photo in their government-issued ID for authentication purposes. This method is usually used to combat identity theft.
The Process of Identity Verification
Businesses should identify crucial moments requiring identity verification, such as account registration, fund withdrawals, and account information changes.
- Users are asked to provide evidence supporting their identity.
- The provided information is utilised by businesses to verify the authenticity of the individual’s claims.
- Equipped with this verified data, businesses can make well-informed judgments and decisions based on risk assessment.
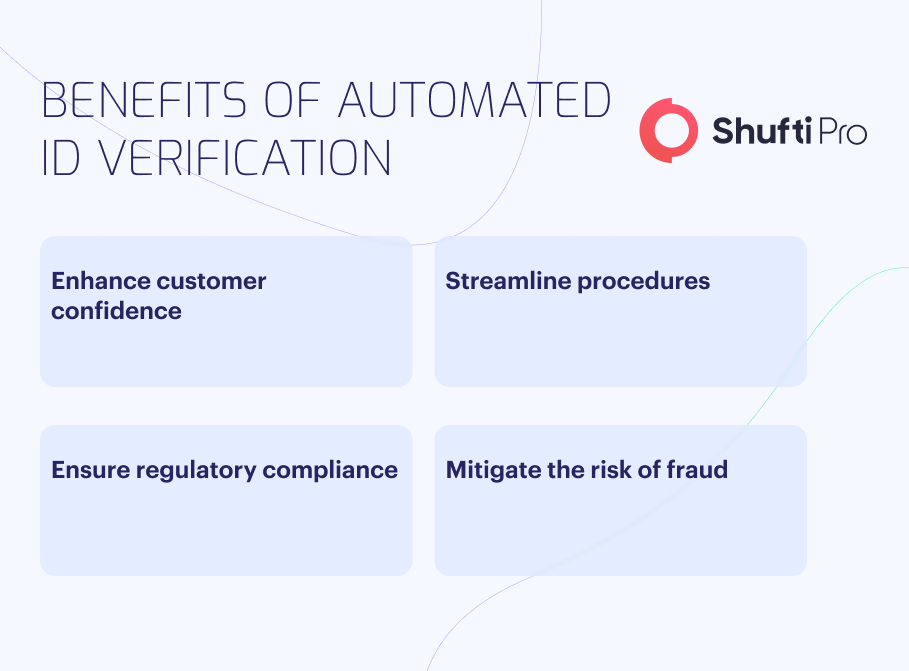
Top Benefits of Automated ID Verification
- Enhance Customer Confidence: Implementing automated identity verification processes instils customer trust in business operations. When customers know that thorough verification is performed for new accounts and high-value transactions, they perceive that the company is actively working to minimise fraud risks. This, in turn, enhances their confidence in securing their personal information and assets.
- Streamline Procedures: Digital identity verification solutions simplify and expedite customer document submission. Tasks that took days or months can now be completed within seconds, resulting in improved conversion rates and a more seamless user experience.
- Ensure Regulatory Compliance: Anti-Money Laundering (AML) and Know Your Customer (KYC) regulations mandate firms to validate user identities. Non-compliance can lead to penalties or substantial fines, even if unintentional. Implementing comprehensive identity verification processes helps businesses meet regulatory obligations and ensure adherence to compliance requirements.
- Mitigate the Risk of Fraud: Reliable verification solutions help enterprises mitigate the risk of identity theft and fraud. By leveraging solutions that cross-reference against authoritative data sources, businesses can effectively assess potential risks and make informed decisions based on accurate information.
Are there Specific Regulations for Identity Verification?
A basic standard for identity verification that can be applied universally does not exist. However, IDV requirements can vary significantly based on several factors, including:
- Industry: Different industries are subject to different laws and regulations about identity verification. For example, financial firms and online marketplaces must abide by KYC and AML regulations. Federal agencies and businesses collaborating with them must follow the guidelines outlined in NIST Special Report 800-63-3, which outlines IDV implementation requirements.
- Jurisdiction: Various jurisdictions have unique laws and regulations, which may encompass identity verification requirements. Whilst some rules may have similarities across states or countries, they can also differ significantly. Companies must understand and abide by the regulations specific to the jurisdiction they are operating in.
- Age Restrictions: Firms that sell age-restricted products, including alcohol, adult entertainment, tobacco, etc., must adhere to regulations focusing on age verification.
- Individual Risk Profiles: All businesses face different types and levels of risk. Consequently, these risk profiles are vital in determining the appropriate verification methods.
Understanding Identity Authentication in Detail
Identity authentication determines whether a user is authorised to do a given task. Businesses employ four primary methods to authenticate customers:
- Passwords: Despite discussions about their obsolescence, passwords are widely used. Email addresses combined with passwords are used for single-factor authentication.
- Two-factor Authentication (2FA): 2FA offers an additional layer of authentication. This usually involves a unique code generated and sent through SMS when a user tries to log in. Individuals must give their username, password, and 2FA code to get access.
- Knowledge-based Authentication (KBA): KBA requires users to answer “secret” questions created during the initial account setup. It is usually used in conjunction with different authentication methods. Typical questions involve details like pet names or mothers’ maiden names. The ideal KBA answers are accessible for the user to remember but challenging for others to guess.
- Biometrics: Biometric authentication checks a user’s identity through unique physical traits like fingerprints to allow them to unlock a laptop or phone.
What Value Does Authentication Offer for Businesses?
Businesses can mitigate the risks associated with account takeovers and identity fraud by comparing provided factors with the initial data used during account opening. Furthermore, authentication processes contribute to a streamlined customer experience, enabling them to access accounts or carry out transactions seamlessly whilst maintaining security. For example, Single Sign-on (SSO) allows users to remember a single set of credentials granting them access to various accounts. Robust authentication procedures have the potential to enhance customer satisfaction, reducing the likelihood of customers seeking alternative companies for critical transactions.
How Can Shufti Help?
Shufti offers an AI-powered ID verification solution to 230+ countries and territories and supports 150+ languages. Our robust IDV solution verifies identities within seconds and helps firms comply with KYC and AML regulations.
Still confused about how an identity verification solution keeps scammers away?

 Explore Now
Explore Now













