KYC/AML Compliance – A Roadblock for Money Mules and Illicit Fund Transfers

Cybercrimes are becoming increasingly complex and diverse in the era of digitization, with fraudsters using new technologies to dodge law enforcement bodies. Unfortunately, frauds are not restricted to individuals only. They are occurring at the corporate level through various schemes.
As more and more nations are moving towards faster and frictionless means for payments, fraudsters are able to route their illicit financial gains globally. This has increased the likelihood of money laundering and other financial crimes through mule accounts, which provides a safe way for money laundering to stay off the radar.
A Brief Overview on Money Mules
Money muling activity is not a new concept, but it has become more prominent in young people that were hit hard by the coronavirus pandemic last year. A money mule is a person who receives illicit money from a third party (generally a money launderer) in their bank account and then transfers funds to another account. In other cases, the money mule takes the money out in the form of cash and gives it to someone else, acquiring commission for it. Money mules are usually recruited by criminal activist groups through advertisements on job sites and social networking platforms where youngsters spend much of their time. The easy money attraction is attractive for them and the young ones end up providing their bank account information. Willingly or unwillingly, the victims become money mules.
18 Australians Suspected to Launder $2.6 Million
Recently, 18 Aussies faced criminal charges as they were suspected to launder $2.6 million through Australian banks. The federal police operation identified 27 money mules and third-party entities that were used by the criminals to transfer money in return for commissions. Among them, two were alleged as the leaders of the money laundering group. The 18 people were arrested by NSW, Victoria, and Western Australian police, while nine warning letters were issued informing the money mules to halt activities linked to money laundering. The Australian law enforcement bodies, financial analysts, and cybercrime experts were part of this sting operation that included regulatory bodies from 27 countries. However, they successfully stopped $2.6 million to wash out through local financial institutions.
1800 Money Mules Arrested in Money Laundering Crackdown
On December 1, the seventh European Money Mule Action (EMMA 7) came to an end after two and half months. Europol, the European Banking Federation (EBF), the FinCrime Exchanges along with 26 other countries collaborated to carry out a money-laundering crackdown. EMMA has been working since 2016 has aimed to identify money laundered and the sources of their incomes.
According to Europol, EMMA is the biggest global operation, where 400 financial institutions reported 7000 bogus transactions. As a result, lost 70 million euros and 324 money mule recruiters were suspected. Law enforcement agencies also claimed that third-party entities were used for money laundering as well as various digital frauds, consisting of phishing, malware, SIM jacking, romance, and e-commerce frauds. These claims were based on the leads brought up by police investigations. Money mules were mostly students, and immigrants to earn easy money.
Lloyds Banking Group Initiates “Pilot Scheme” to Combat Frauds
Lloyds Banking Group has launched a pilot scheme, while law enforcement authorities are using criminal proceedings to counter criminal activities and assist victims. The “frozen cash” came from money captured by the bank’s mule hunting team. In the first round of schemes, a capital of around £7 million was seized. According to the investigations, money mules allow fraudsters to route cash across the border using their bank accounts. However, mule hunting teams continuously analyze data to identify the signs of money laundering.
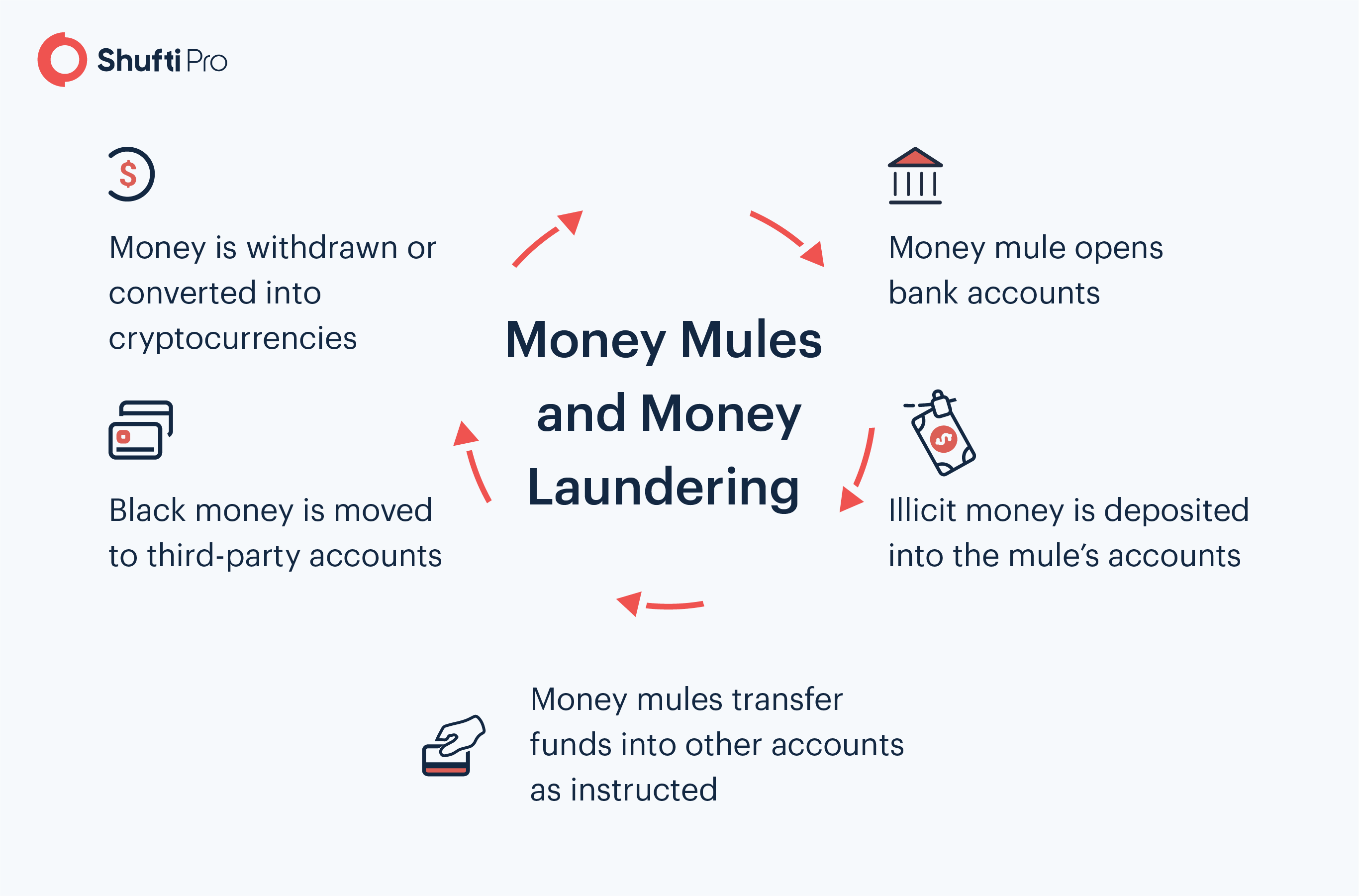
Workflow of Money Mule’s involvement in the Money Laundering Activities
Fraudsters recruit money mules by offering them high commissions or lucrative employment. Once they are onboarded, money mules are asked to open bank accounts with their own personal information. This strategy is practiced in order to conceal criminals’ identities, the source of illicit earnings, and to avoid identity verification procedures.
Alternate to mule accounts, criminals also open bank accounts using synthetic identities. In this regard, fraudsters utilize the abducted legitimate clients’ profiles in order to blend real and fabricated information. However, once money mules accounts are created, money launderers can use their black money to transfer into legit financial systems.
Red Flags to Identify Money Mules
False Job Offerings
- Money mules replicate legitimate businesses’ websites and create similar IP addresses to make fraud seem authentic.
- Bogus emails with false job offers are often awkward and badly written. However, the sender’s mail doesn’t match the organization’s name.
- Mules are usually portrayed as an international company seeking for local/national agents to act on their behalf, to avoid high translation fees and taxes.
- The job position involves transferring funds.
- The nature of work of false businesses may vary, but advertisements specify using third-party bank accounts to route money.
Instant Cash
- Criminals ask victims to move their funds through money mules bank accounts in return for high commissions
- The schemes to earn money are presented as having no risk, using acronyms of ‘legitimate money’, ’100% guaranteed’, and ‘same-day cash’.
- Criminals trick out third-party entities by saying how much others have already earned by doing this.
Ways Financial Institutions can Counter Money Mules
Money mules make the procedure of identifying and mitigating financial crimes more complicated. Hence, represent a significant need for AML, KYC, and CFT measures. Banks that fail to determine money mules using their services to move black money can experience hefty fines, reputational damages, and significant sanctions. Therefore, financial corporations have to assure that their customer identification programs can detect clients that are pawns of money launderers. To accomplish this, risk-based ID verification along with AML screening measures must be implemented.
Customer Due Diligence
The financial institutions and banking sector have to establish mechanisms of identifying and verifying the true identities of the customers along with the nature of business. Enhanced CDD is viable for detecting money mules that are opening bank accounts on behalf of third parties (money launderers).
Transaction Monitoring
Banks must monitor clients’ accounts and the nature of the transaction they are carrying out. This will help financial institutions to identify suspicious transactional patterns. Usually, money mules’ accounts are engaged in large transactions to move the illicit money.
AML Screening
AML screening is to be observed on customers because money mules may be acting on the instruction of PEPs or other high-risk entities. Screening against sanction list, PEPs list, and financial crime watchlist ensures that money mules are not onboarded. This practice also assists the banks to expose the clients that are in connection to money launderers and other financial criminals.
Final Thoughts
Money laundering has become a global concern. There is growing urgency to crack down mule operations, and regulatory bodies are doing their best to counter money launderers. Thereby, the financial corporation holds the key to exposing the money mule network. Conventional strategies of data analytics and transaction monitoring fail to see the broader picture of money mules activities, as fraudsters have learned to remain undetected. However, with the AI-based identity verification services are developed that are aligned with the KYC/AML regulations financial institutions can detect as well as diminish the money mule activities.
Want to know more about money mules and how to prevent them from entering the business ecosystem?

 Explore Now
Explore Now













