Transaction Monitoring: Going Beyond AML Screening

Whether you are an accountant in Wall Street or a developer for Google, money laundering will not be a new term. Everyone knows that illegally transferring money or laundering illicit funds is a criminal offence, and authorities are continuously adding new regulations and taking stringent steps to stop this. Last year, a document named Financial Crimes Enforcement Network (FinCEN) files were leaked, revealing that suspicious transactions worth USD 2 trillion were recorded between 1997 and 2017. While the actual amount of laundered money cannot be calculated accurately, 90% of black money goes undiscovered, according to the United Nations.
Businesses have to put extra effort and find technologically advanced ways to detect and combat money laundering in order to comply with the global AML/KYC regulations.
What is Transaction Monitoring?
The process through which financial institutions check customers’ transactions for illegal, high-risk or doubtful activity, is called transaction monitoring. It is a continuous process performed by advanced software in real-time that analyses the customers’ background and financial data.
Customer Verification and Screening is Not Enough
Traditionally, businesses conduct customer due diligence to verify customers’ data, business relationships and perform risk assessments/background checks on them. Customer information is verified through know your customer processes at the initial time of onboarding. During this process, KYC verifies the identity by analysing their government-issued identity documents. KYC checks the authenticity of IDs and then uses that data for creating customer profiles, this proves that the customer is authentic and eliminates the hazards of identity theft.
After this, the customers are screened against AML watchlists and PEP (Politically Exposed Person) lists provided by the different local and international authorities.
Customer due diligence is performed at the following events;
New Business Relationship
While onboarding new customers and establishing a business relationship, companies make sure that the customer is not a high-risk entity and not giving fake data.
Regular Transactions
CDD is performed while facilitating regular transactions or at an occasional point, for example, on an amount above the threshold limit or on customers from high-risk countries.
Suspicious Transactions
If the customer is suspected of money laundering or any other financial crime before, businesses must perform CDD checks.
Fake or False Documents
Customers providing their false data or using fake documents must be checked through CDD.
AML Risk-based Approach
CDD measures are risk-based, companies access the AML risk of each customer and make their due diligence process accordingly. Most customers are checked through only standard due diligence where their identity is confirmed, and business relationships are verified. If the customer possesses low risk, the standard due diligence may be appropriate, but it should be assessed that the customer is actually low-risk.
Today, money launderers use more digital platforms and know how to bypass the normal verification processes. One customer might not be high-risk but could have the intention to launder money through your platform. The traditional system marks such a customer as low-risk and applies standard due diligence, only to discover later that illegal transactions have been made by them. In July 2021, British authorities seized USD 250 million of cryptocurrency in an alleged money laundering case. Detecting these cases of money laundering requires continuous and ongoing monitoring of transactions.
2020 -The Year of Highest Recorded AML Fines
If businesses do not comply with the regulations or fail to prevent money laundering through their channels, financial regulators can issue fines or impose sanctions on them. A drastic rise in AML fines was observed in 2020 as financial crimes increased during the pandemic. According to Kroll, authorities issued USD 2.3 billion fines on money laundering in 2020, which is five times more than 2019.
The various methods of money laundering used by criminals in 2020 highlight the growing challenge that every business is set to face in the upcoming future. Owing to this, law enforcement agencies have included non-financial businesses under the AML framework, as well as the real estate sector and precious stone dealers. For the first time, AMLD4 (Fourth Anti-money Laundering Directive) addressed Designated Non-financial Businesses and Professions, applying AML regulations on them just like the financial sector.
Additionally, the US and Europe are drafting new legislations focusing on cryptocurrency exchanges and other FinTech related financial crimes. This will give a new perspective to businesses in how they deal with their customers in future.
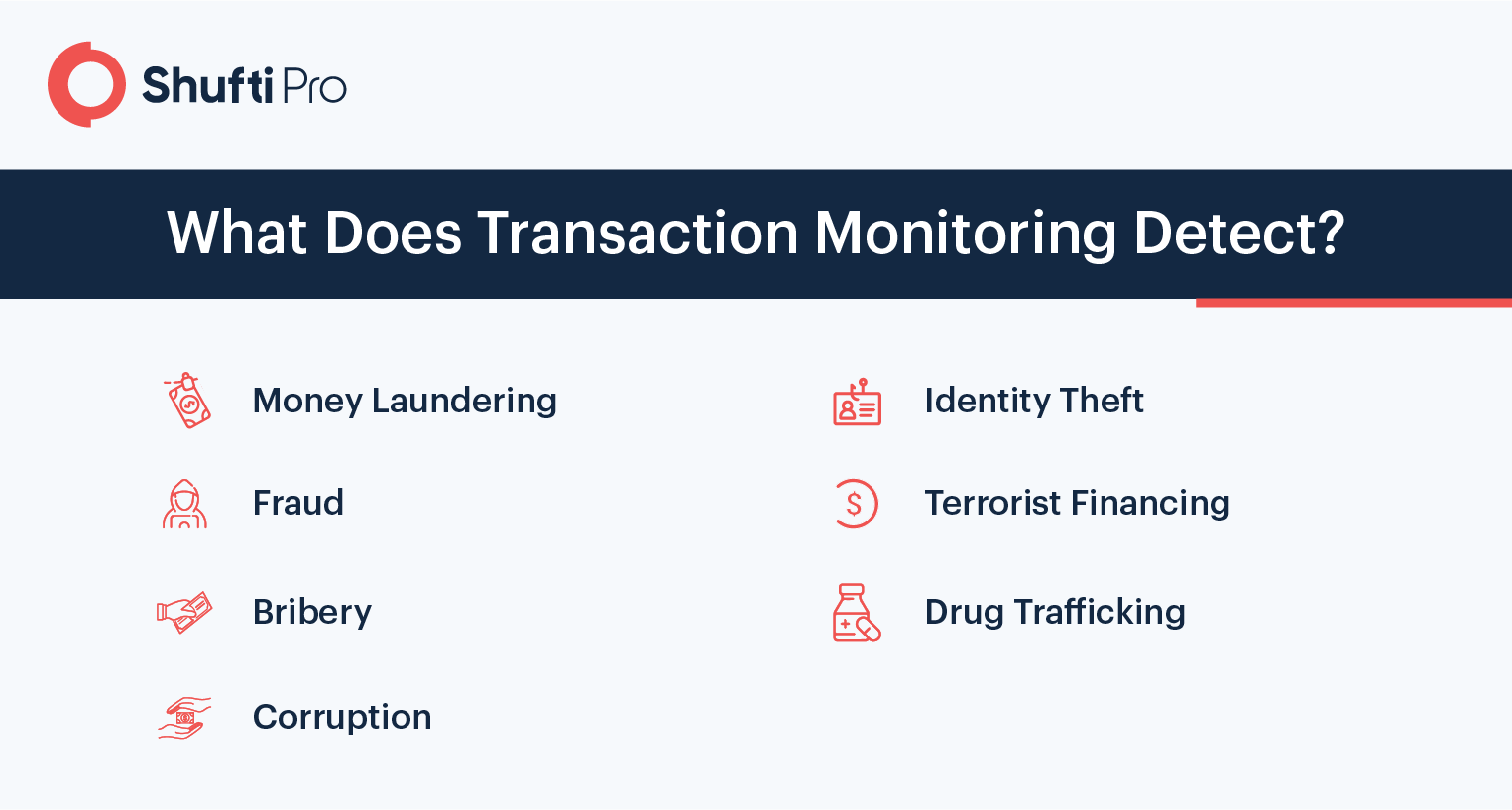
Checking Customer Activities Through Transaction Monitoring
Financial businesses process millions of transactions on a daily basis, thus checking each transaction manually is not practically possible. Instead, they can monitor the flow of all these transactions by using automated transaction monitoring solutions. AML transaction monitoring is now a legal requirement for businesses, they set the transaction threshold as per their requirement. The system generates an alarm if any transaction triggers that rule and the compliance department is informed, which then takes required steps. Transaction monitoring helps in reducing false-positives by analysing the customer profile to differentiate between normal and suspicious cases.
Currency Transaction Report
Banks are obliged to file a currency transaction report for every transaction exceeding USD 10,000. Banks do not inform customers about filing their CTR, if the customers refuse to process after being informed, a suspicious activity report must be filed.
Suspicious Activity Reporting
Under the Bank Secrecy Act and FATF 40 recommendations, financial institutions are required to file SAR for any doubtful transaction. Suspicious behaviour may refer to any transaction that raises triggers for money laundering or other fraudulent activity. SAR is filed when a transaction passes a certain level, or in case of high-value cross-border transfer and other unusual account activity. SAR helps governments to be aware of modern money laundering attempts and make legislation to combat them.
What Shufti Offers
Shufti offers an AI-powered Anti-money Laundering solution that screens customers’ data against watchlists and verifies their business relationship. The real-time screening solution helps in compliance with all financial and data privacy regulations of all states.
Want to know more about how Shufti’s AML solution?

 Explore Now
Explore Now













