It starts with choosing an Identity Verification Vendor that owns its Tech Stack
When selecting a KYC provider, one of the most crucial factors to consider is whether the provider has developed its own tech stack in-house or has assembled it by stitching pieces from already existing IDV vendor's services.
Users' Data Privacy
Vendors who have built identity verification engines from scratch offer multiple benefits, with the most important being the reduction of any risk of privacy breach due to their non-dependency on third parties.
Customized Verification Flows
Apart from minimizing the privacy breach risks, RegTechs that own their entire tech stack offer a powerful advantage of on-demand customization. They can adapt verification logic to region-specific regulations, build a customised verification flow according to business needs, and hence deliver a smooth and secure end-user experience.
Handling the Edge Cases
The most crucial advantage is handling edge cases. While most identity documents used for travel, such as passports, may comply with standards like ICAO 9303, not all the documents which can be used to verify identity adhere to these standards.
Rare or Non-standard ID Documents
IDs from smaller jurisdictions with limited digital templates, outdated passports or driver’s licenses still in circulation, and paper-based records like birth certificates from developing regions often do not align with standard verification models.
Complex Scripts and Multilingual Inputs
Documents in Arabic, Cyrillic, Chinese, or other non-Latin scripts, as well as mixed-script names and irregular date formats and region-specific address structures, pose additional challenges for OCR systems, leading to higher error rates.
Adaptability to Evolving Fraud Typologies
Defense mechanisms of businesses need to evolve in order to combat the latest fraud typologies, changing compliance regulations, and even to meet the needs of the diverse user base.
This implies that an off-the-shelf solution with static features can fall short of meeting such expectations. Identity verification providers with in-house technology and support of dedicated in-house teams, not only quickly offer customizable verification flows but also improve the solution's capabilities in response to evolving fraud typologies.
Reducing Costs on Reviewing False Alerts
Continuous improvement in fraud detection, driven by in-house research teams and analysts, contributes directly to lowering review costs. Identity verification vendors that consistently enhance their technology and are supported by dedicated human reviewers enable enable digital-first businesses to reduce the millions spent on managing false alerts.
Trust at Risk: How IDV vendors dependent on third party vendors result in users' data breach?
In 2025, an Italy-based ID verification firm confirmed that customer data was stolen, not from its own systems, but through a breach in its third-party vendor network, showing how outsourcing security can create hidden vulnerabilities.
Authorities reportedly claimed their own system wasn’t breached, but reliance on third-party vendors caused the data theft.
Vendors who own their tech stack vs those who don't
| Aspects | Off-the-Shelf Vendors | Vendors with In-House Tech Stack |
|---|---|---|
| On-Demand Customization | Third-party dependent vendors limit customization, making it hard to align verification workflows with specific user needs. | Independent Vendors offer tailored workflows and customized risk engines to meet client needs. |
| Control & Transparency | Off-the-shelf solutions act as black boxes, limiting visibility and creating dependency risks. | Full tech-stack ownership enables tailored solutions, transparency, and clear audit trails. |
| Privacy | Third-party reliance increases data exposure to breaches. | Sensitive User data stays within the company’s own infrastructure, lowering the risk of external exposure. |
| Accuracy | Borrowed-tech providers limit coverage for complex identity documents, such as those with non-Latin scripts, reducing accuracy | In-house vendors have developed a customer OCR engine that is fully compatible with new eIDs and continuously improved through R&D to deliver higher accuracy. |
| Cost | Dependency-based vendors raise costs with false alerts, errors, and rigid flows, leading to fines and customer dropouts. | Self-sufficient platforms cut errors, prevent fraud through R&D teams analyzing flag alerts and streamline onboarding, saving costs and reducing dropouts. |
| Response Time | Outsourced providers relying on third parties face delays, missed SLAs, and higher dropouts. | Vendors with in-house verification ensure faster, reliable checks that build trust and cut abandonment. |
Relying on vendors who don't own their tech stack creates limits, risks, and hidden costs across customization, transparency, privacy, accuracy, expenses, and speed. In contrast, outsourcing IDV Solutions from the vendor owning their tech stack gives businesses greater flexibility with tailored workflows, stronger data protection, improved accuracy, lower costs, and faster, more reliable verification, ultimately strengthening trust while reducing risk.
The chain of vulnerability every business must avoid
Additionally vendors that outsource identity verification to third parties introduces a new link in the
chain of vulnerability. Data is passed across multiple systems, increasing the risk of breaches, misuse, or
weak security at any single point.
All this risk lurks around in the background while users are forced to
navigate rigid, one-size-fits-all interfaces.
A vendor who owns their tech stack not only ensures to prevent users from data breaches but can also customize the User Interface according to businesses’ needs so that they can provide a smooth KYC experience to their customers.
Customizability tailored for your industry:
There is no one size fits all approach in identity verification; every industry faces unique regulatory, risk, and user-experience challenges. Businesses need verification systems that adapt to their specific workflows rather than forcing them into rigid, one-size-fits-all models. Tailored solutions ensure compliance, reduce friction for end users, and build trust across diverse sectors.
Customized User Verification Workflows
Shufti provides identity verification with customized UI/UX, tailored to each client’s platform, whether a crypto exchange, forex broker, or social media marketplace. The verification flow is designed to match the client’s brand and audience needs while ensuring compliance and a seamless onboarding experience.
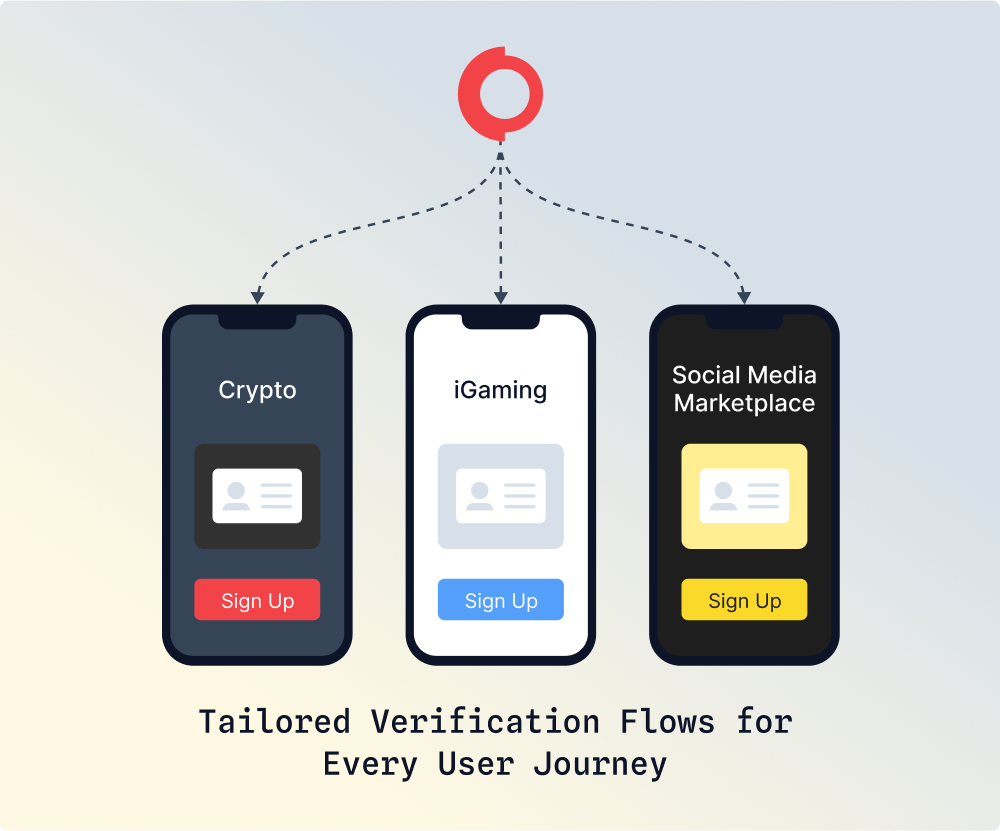
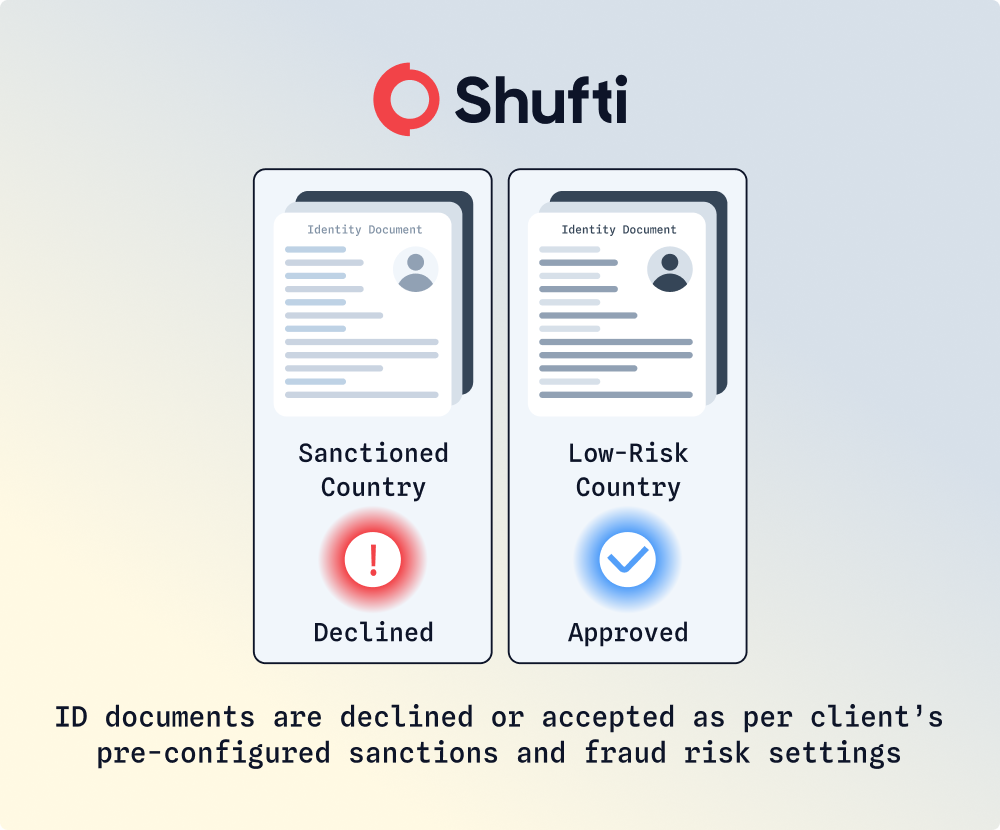
Jurisdiction Specific Risk Logic
Shufti’s risk engine automatically approves or declines users based on each client’s compliance policies and risk factors. For businesses with high-risk exposure, Shufti adjusts verification logic according to pre-configured risk thresholds and then verifies and declines documents accordingly. This ensures exchanges stay compliant by instantly rejecting high-risk submissions while allowing smooth onboarding for verified users.
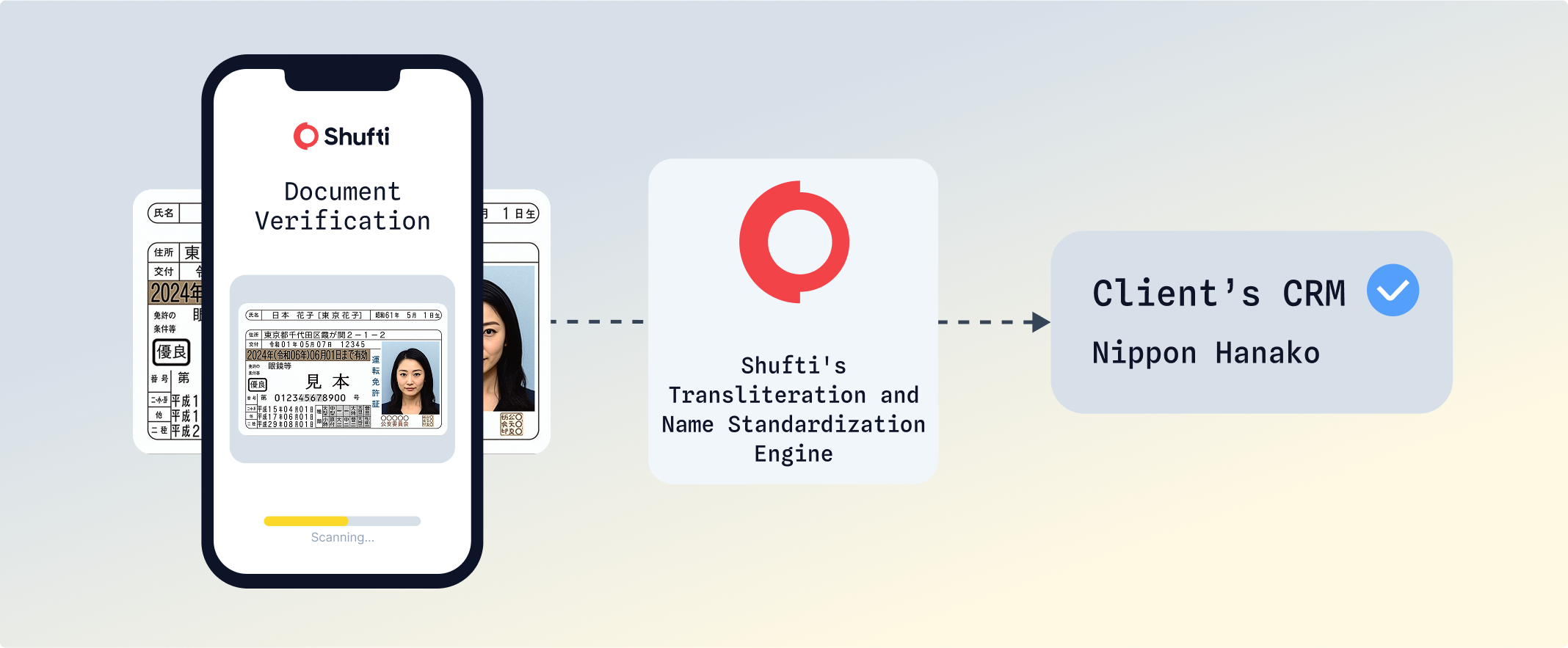
Transliteration & Name Matching for Complex Scripts
Global platforms often face challenges with non-Latin scripts, where transliteration errors and name mismatches can delay verification and frustrate users. A Japanese user named “日本 花子” may appear as “Hanako Nippon” on one document and “Nippon Hanako” on another. Shufti’s system accurately transliterates and auto-matches such variations, seamlessly pre-filling CRM fields to keep onboarding smooth.
How Shufti's proprietary tech, augmented by R&D teams, fills trust deficit?
Digital Identity is instrumental to the global expansion of businesses. However, as regulatory requirements differ, businesses need Identity Verification solutions that adapt to market-specific verification needs and incorporate the distinct regulatory risk logic of each country. Achieving the right equilibrium between verification and incorporation of regulatory risk logic demands continuous collaboration. Shufti leverages its in-house technology to deliver this adaptability and control. The solution works in close collaboration with clients to iterate, refine, and adapt systems in real time, ensuring both compliance and growth according to their evolving risk exposure and risk appetite.
Keeping Fraud Below 1%
- Shufti works in close collaboration with stakeholders to verify the edge cases.
- It learns from evolving fraud typologies and the Research and Development team’s manual reviews in the edge cases, ultimately keeping the false acceptance rate below 1%.
Saving the Cost of Analysing False Alerts
- Shufti's AI-powered tech is augmented by R&D teams, which reduces the businesses' cost of manually reviewing edge cases
- It trains itself on new fraud patterns, lowering errors and boosting ROI.
Compliance without Compromising User Convenience
- Real-world verification completes within 30 seconds, ensuring a fast and seamless onboarding experience.
- Shufti’s Fallback Intelligence enhances convenience, providing alternative verification paths to keep onboarding smooth even in edge cases.
Custom Verification for Complex Global Requirements
- Shufti’s in-house verification provides custom flows for social media, crypto, and fintech, ensuring smooth, compliant, and seamless onboarding worldwide.
- It supports global languages and scripts, accurately handling transliteration, for seamless verification.
Shufti Owns Its Tech Stack
- Shufti’s Identity Verification is entirely developed in-house, giving full control over technology and processes.
- Ownership of the tech stack allows Shufti to rapidly update systems in response to evolving fraud patterns, emerging threats, and clients’ requirements.