Difference between Identification, Authentication, and Authorization

- 01 Why distinction between identification, authentication, and authorization matter
- 02 What is identification?
- 03 What is authentication?
- 04 What is authorization?
- 05 How to reduce fraud and friction in the customer journey?
- 06 How Shufti Helps Secure Each Customer Journey from Identification to Authentication and Authorization
Identity verification for access management and know-your-customer (KYC) compliance can fail due to a simple mix-up of certain terms. Sometimes people treat identification, authentication, and authorization as the same thing. Conflating these distinct checks may result in applying controls that either can’t provide enough security/assurance or are unnecessary in a particular scenario. In both cases, the results can be devastating for an organization, whether it’s a security lapse or needless friction experienced by its customers.
Businesses and compliance leaders with a clear distinction of these terms can design the right checks, meet regulatory expectations, and deliver a cleaner customer experience. “Cybersecurity and smooth user experience are both necessary; one should not be at the cost of the other.” We will clarify each layer with examples and show how they connect across the customer journey, starting from onboarding, login, and subsequent account use.
Why distinction between identification, authentication, and authorization matter
Confusing identity proofing with login security can lead to gaps that invite regulatory actions and business losses. A firm may run a strong document check during onboarding, then rely on weak passwords later; the result is account takeover (ATO). Or a team may deploy multi-factor prompts everywhere, and the consequences are user friction and dropouts. Regulators expect a risk-based approach across the full lifecycle, which is also in the best interest of the business itself. That means knowing what each layer does, where it sits, and how it is tested. As discussed, clear separation also improves customer experience. When identity is proven once with high assurance, later sessions can be low-friction and still safe. When permissions are managed by role and reviewed often, change requests are faster and safer.
What is identification?
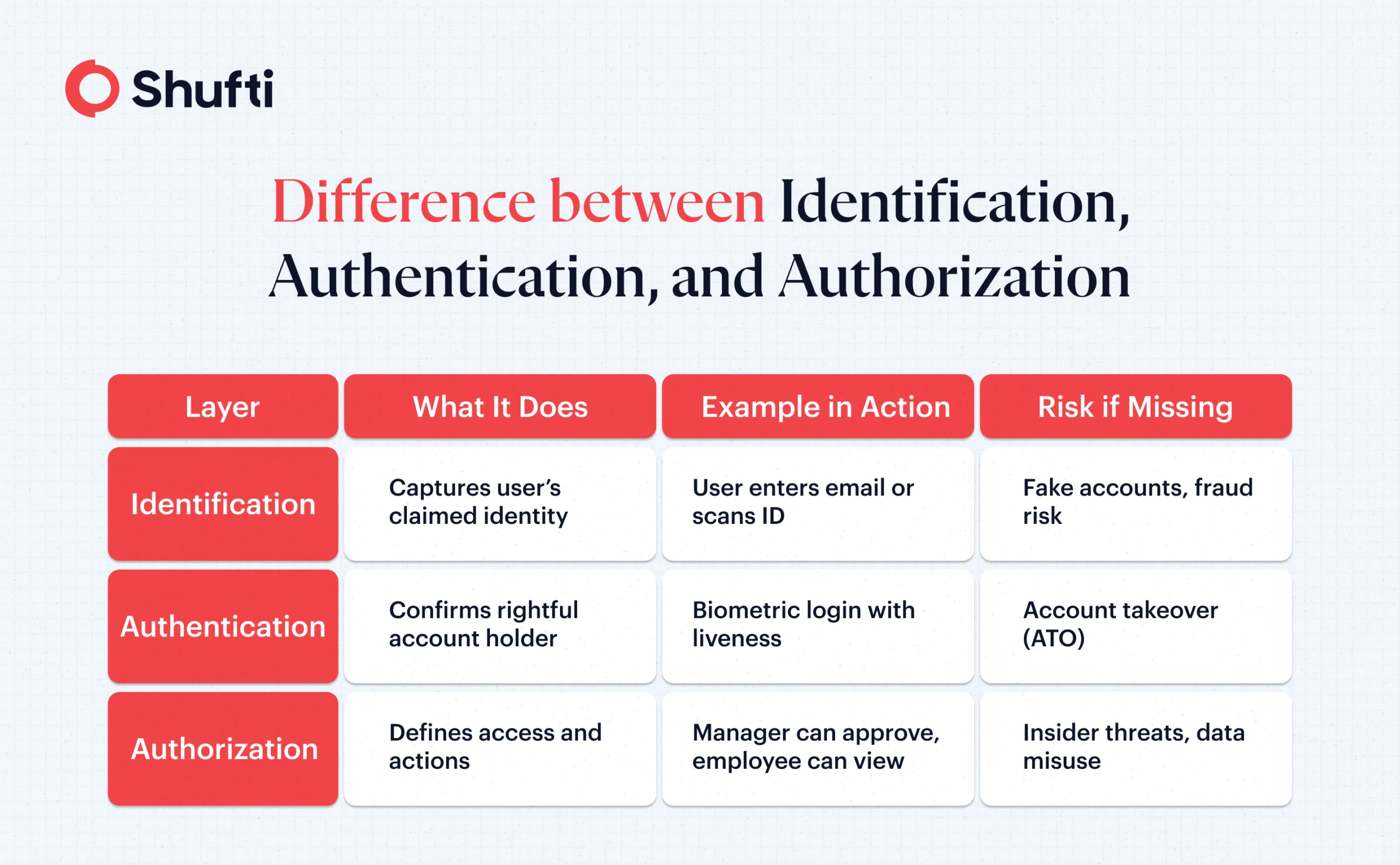
Identification is a way to prove who a user is. Imagine entering a secured workplace, accessing your healthcare records online, or ordering through an e-commerce website; in all such situations, identification is needed to determine if a person is privileged to gain access or complete a service request. Identification can be done through multiple data points, including a name, an email, a username, or an account number that the system recognizes. The purpose is to link and track an activity to a unique person or a profile. Different ways people identify themselves include:
- Typing your username and email to create a profile
- Scanning your badge to enter work
- Filling out an online form with your name and address
- Uploading a government-issued ID for age verification
- Linking social security or passport numbers for compliance
Digital systems often push for deeper identification, sometimes adding biometrics such as liveness detection or facial scans. When you read about identity fraud, the story often starts with someone tricking the identification process. That’s why reliable security identification is the first, but never the only, safeguard.
Why is identification important?
Correct identification is the first step in cybersecurity. Imagine someone opening an account in your name. Identification stops that and ties actions to real people. Banks require official documents, such as a driver’s license, passport, or social security number. These checks block impostors and help banks follow Know Your Customer and AML rules, reducing fraud and money laundering. Hospitals verify your identity using insurance cards, government ID, or biometrics to ensure the privacy of your medical records. In e-commerce, identification is crucial for making payments and completing deliveries to the right shoppers. Companies use ID badges to limit system access only to authorized people.
What is identity proofing?
While identification is a claim of who a person is, identity proofing confirms a real person or a real business behind that claim. In regulated sectors like financial institutions, this is KYC and CDD for consumers, and KYB for businesses. Typical methods in identity proofing include document verification, biometric selfie with liveness, database checks, and risk scoring/profiling. Though risk profiling isn’t a method of proving identity, it’s a way of determining what level of proofing would be sufficient in a given scenario. The goal is to bind a legal identity to an account with the right level of assurance.
For instance, a new fintech customer starts a mobile application. The app collects a user name or email for identification. The firm runs identity proofing and asks the user to scan a government ID, and confirms the validity of the document with an official database. A biometric selfie with liveness checks if the same person is present. Risk scoring evaluates document quality, velocity, device, geography, and matches against sanctions and PEP lists. If the risk is low, the account opens. If risk is high, enhanced due diligence applies. The firm retains records to satisfy audit and regulatory needs.
What is authentication?
Authentication proves that the current user is the rightful account holder. This differs from identity proofing, where the identity claim is verified at the start of a relationship or at the time of onboarding. Authentication ensures that only the rightful person, whose identity has been verified, has access to an account or profile throughout the user lifecycle. This is the control that blocks account takeover (ATO), preventing unauthorized access to an account and reducing the chances of fraud. If there were no authentication, fraudsters could easily misuse an account by obtaining login credentials without ever proving their identity.
Let’s explain it with an example of a fraudster who successfully gains access to a person’s bank account login credentials and attempts to log in from their device. The system detects an unknown device and asks for a selfie with liveness detection. Fraudster fails the liveness detection challenge, and the attack is successfully thwarted, even when credentials are compromised.
Common authentication methods include device binding, push prompts, and biometrics with liveness. Though passwords remain common, relying solely on them can be risky. SMS codes are also used widely, but they also carry known weaknesses, such as SIM swap, and should be used as a fallback rather than a primary method.
Why is authentication essential?
Every year, fraud losses are expanding as attackers adapt to new fraud typologies. In the U.S. alone, consumer fraud losses reached over $12.5 billion, marking a 25% increase from the prior year. Weak authentication is like leaving the door open for fraud, impersonation, privacy loss, and identity theft. Authentication is crucial in preventing malicious actors from gaining illegitimate access to accounts, finances, and personal information of users. Authentication methods paired with strong liveness detection features can effectively minimize impersonation, ATO, and other types of fraud. Authentication also upholds both industry and legal requirements, as different regulations require strong authentication for banking, healthcare, and online transactions. It helps earn user trust. When people know their accounts and data are secure, it builds trust and makes them feel more at ease and confident. It’s no accident companies worldwide continue to make authentication a top priority, from strong passwords to biometric scans, it’s essential protection in today’s digital world.
Types of Authentication Factors
A person can be authenticated in different ways depending on the situation, the risks involved, or legal requirements. FATF Guidance on Digital Identity mentions three different ways that can be used to authenticate a person:
- What you know (knowledge factors)
This means information that only you should remember, like your password, personal identification number (PIN), or answers to pre-selected security questions. For example, when you reset an account, you might be asked to confirm your childhood pet’s name. - What you have (Ownership factors)
This involves something you physically carry, such as cryptographic keys on hardware (like a laptop, mobile device, or a USB), an OTP generating software installed on a digital device like a mobile, or a key fob. - What you are (Inherent factors)
This refers to a person’s unique biophysical factors like fingerprints, facial features, voice, and iris patterns, as well as biomechanical factors (the unique way a person interacts with digital devices) like typing patterns, device holding angle, and screen swiping. These traits are nearly impossible to duplicate, which makes them especially valuable for secure environments.
What helps firms is combining these elements of knowledge, assets, and identity. It creates a solid security identification foundation that is challenging for fraudsters to overcome.
What are some common authentication methods?
Authentication methods are adapting to new digital threats, so today’s systems use a mix of approaches to keep users safe. Commonly used methods are:
- Single-factor authentication
This method uses only one parameter to authenticate a person’s identity, such as a password. - Multi-factor authentication (MFA)
Sometimes more than one factor is used for authentication, which requires two or more forms of identification, such as entering a password followed by a code sent to a phone. Malicious actors would need access to more than just your password if these checks were layered on top of one another. - Password-based authentication
Most people are familiar with this approach, which involves entering a password or PIN to unlock an account. It’s the most common but risky approach, as passwords can be stolen, guessed, or brute forced by fraudsters. - Biometric authentication
Systems recognize a person by their physical traits, such as fingerprints, facial scans, or unique voices. Biometrics make sure an identity isn’t easy to copy or steal, and they’re used everywhere from unlocking phones to logging into banking apps. - Token-based authentication
This method involves verifying the identity and then issuing a token, which can then be used to access an app or a website for one session or a limited time after that token becomes invalid. One-time passwords are also an example of token-based authentication.
Most companies don’t rely on just one method for authentication. Banks, healthcare portals, and secure workplaces may use multiple layers of security together to help ensure your account stays protected.
Imagine a returning user logs in with a passkey on a known device. The session inherits a phishing-resistant factor. The user later initiates a large transfer, the system detects a higher risk and prompts a step-up. Biometric with liveness confirms the presence of the rightful owner of the account, and risk is mitigated. Authorization policies then determine who can schedule, approve, or release the payment. Segregation of duties stops a single user from moving funds end-to-end.
What is authorization?
Authorization governs what an authenticated user can do. In other words, it manages the type and level of permissions granted to an authorized user. For instance, even a verified and authenticated user cannot modify their own account balance directly through their bank app, because they’re not authorized to do so. Authorization enforces least privilege inside applications and data stores. Least privilege access is a cybersecurity strategy that grants users only the minimum level of permissions necessary to perform a task, and nothing more than that.
Why is authorization important?
Strong authorization reduces blast radius and controls the damage, even if an account is compromised. Without the right level of authorization, private data of clients, sensitive information, or permissions are at risk of being misused by both internal and external threats. Authorization limits people from seeing things they shouldn’t, even if they manage to get past other safeguards. It also helps comply with laws that require firms to separate customer data from company records and maintain user privacy. When only those with permission may access private data or accounts, there is more confidence. Companies should routinely review and update permissions as roles and duties change. Authorization is how they stay ahead and keep both data and people protected.
What are different types of authorization models?
Different types of authorization models include role-based access control (RBAC), attribute-based access control (ABAC), and segregation of duties (SoDs) for sensitive tasks. The RBAC model organizes permissions based on roles, such as a manager can make changes to a file, whereas an employee can only read. ABAC models grant permissions based on attributes like geography and time, meaning an employee can only access a system from the office location and only during working hours.
How to reduce fraud and friction in the customer journey?
Regulators across the globe point to the same thing: to prove identity at onboarding with the right assurance. The following are some best practices to reduce fraud, protect privacy, and enhance trust throughout the customer journey:
- Prefer phishing-resistant Multi Factor Authentication, such as passkeys and security keys, while using SMS only as a backup.
- Use biometric checks with liveness to counter spoofing and treat it as a factor inside a broader flow.
- Bind sessions to devices and contexts, and raise friction only when risk increases.
- Add step-up authentication for high-value or high-risk actions while keeping low-risk tasks smooth.
- Enforce least privilege with clear roles and apply segregation of duties to sensitive processes.
- Review entitlements and permissions on a regular schedule, and remove access when roles change.
- Log identification, proofing, authentication, and authorization events. Retain evidence for audits and investigations.
- Re-verify identity when risk signals appear. Examples include device change, travel to unusual regions, or watchlist updates.
How Shufti Helps Secure Each Customer Journey from Identification to Authentication and Authorization
Identification, identity proofing, authentication, and authorization do different jobs. Each layer removes a different class of risk. Put together, they create a safer, more efficient, and reliable customer journey. Businesses must distinguish between these concepts and design controls to reduce fraud, meet regulatory expectations, and keep users moving.
Shufti enables firms to implement these controls and security with high assurance and lower friction. With these capabilities, compliance teams can prove identity at onboarding, authenticate users with strong and modern factors, and enforce authorization with confidence. Customers experience fewer unnecessary prompts because controls adapt to risk. Shufti works in close collaboration with compliance leaders, product owners, and security teams to build flows that fit risk and business goals.
To explore how an adaptable IDV solution secures each touch point of your customers’ journey, fortifying trust and driving business revenues, request a demo today!

 Explore Now
Explore Now













