Why High-Risk Transactions Need Real-Time Identity Verification

- 01 So, what counts as a high-risk transaction?
- 02 Why is real-time identity verification non-negotiable now?
- 03 Where does risk concentrate?
- 04 How does real-time IDV work in practice for high-risk scenarios?
- 05 What best-in-class looks like (and how to get there)
- 06 What’s next for tech-based identity verification?
- 07 The Takeaway
- 08 Decreasing fraud and improving compliance with Shufti’s Transaction Trust Screening
While onboarding sets a baseline, real-time checks test it because risk isn’t a static parameter. If a low-risk profile is attempting unexplained high-value transactions to a high-risk jurisdiction, should a business act?
A customer may not exhibit all the risk signals at the time of onboarding. Very often, risk manifests the moment when money moves rapidly between accounts, chips are cashed out, or crypto is sent off-platform. That’s where high-risk transactions live, and where identity has to be verified in real time to assess risks, prevent fraud, and block unauthorized push-payments.
So, what counts as a high-risk transaction?
High risk is a contextual and dynamic phenomenon. Regulators expect firms to apply a risk-based lens to controls. This means to perform high scrutiny on transactions that are unusual for the customer, touch higher-risk geographies, involve high-risk products, or include parties who trigger sanctions/PEP/adverse-media concerns.
In the EU’s framework, ongoing monitoring explicitly requires checking that a transaction matches the customer’s known profile, and supervisors have pressed firms to define when that scrutiny must happen in real time, not after the fact.
Due to the rapid growth of e-commerce, the adoption of digital payments has expanded, especially card not present (CNP) transactions. CNP transactions are considered to be high risk due to their inherent vulnerability and have been consistently exploited to conduct fraud with stolen cards/credentials.
Similarly, virtual assets present higher risks due to anonymity concerns. Under the Financial Action Task Force’s Crypto Travel Rule, originator and beneficiary information must accompany a transfer immediately, which in practice demands identity assurance before the value moves. FATF’s June 2025 update to Recommendation 16 goes further, standardising what information must accompany cross-border payments and requiring tools that protect against fraud and error.
In short, a high-risk transaction is any movement of funds where your model says “elevated exposure”, and where regulators or scheme rules expect you to know exactly who’s involved before you approve.
Why is real-time identity verification non-negotiable now?
There are two forces that converge on a single requirement, which is identity verification in real-time in high-risk situations.
First is compliance with regulations. Risk-based AML requires ongoing, transaction-level scrutiny. In higher-risk scenarios, scrutiny has to be immediate enough to stop the transfer if needed. European banking and payments supervisors have been explicit that firms should codify the triggers that flip monitoring and verification obligations in real-time mode.
Second and equally important is business resilience. Fraud and mule activity concentrate in “high-stakes” moments like first payouts, large cross-border wires, account-to-account push payments, and off-ramp crypto withdrawals. Blocking a transaction after the settlement is expensive and erodes customer trust. Customer-friendly, instant step-up IDV at authorization time preserves good users’ journeys while removing the friction at low-risk transactions.
While stopping fraud has always been a priority for regulators, new regulatory developments have made it even more essential due to associated costs. The UK Payment Systems Regulator made most APP-fraud reimbursement mandatory from 7 October 2024 up to a certain threshold, an explicit nudge to prevent scams before they occur, not review them later.
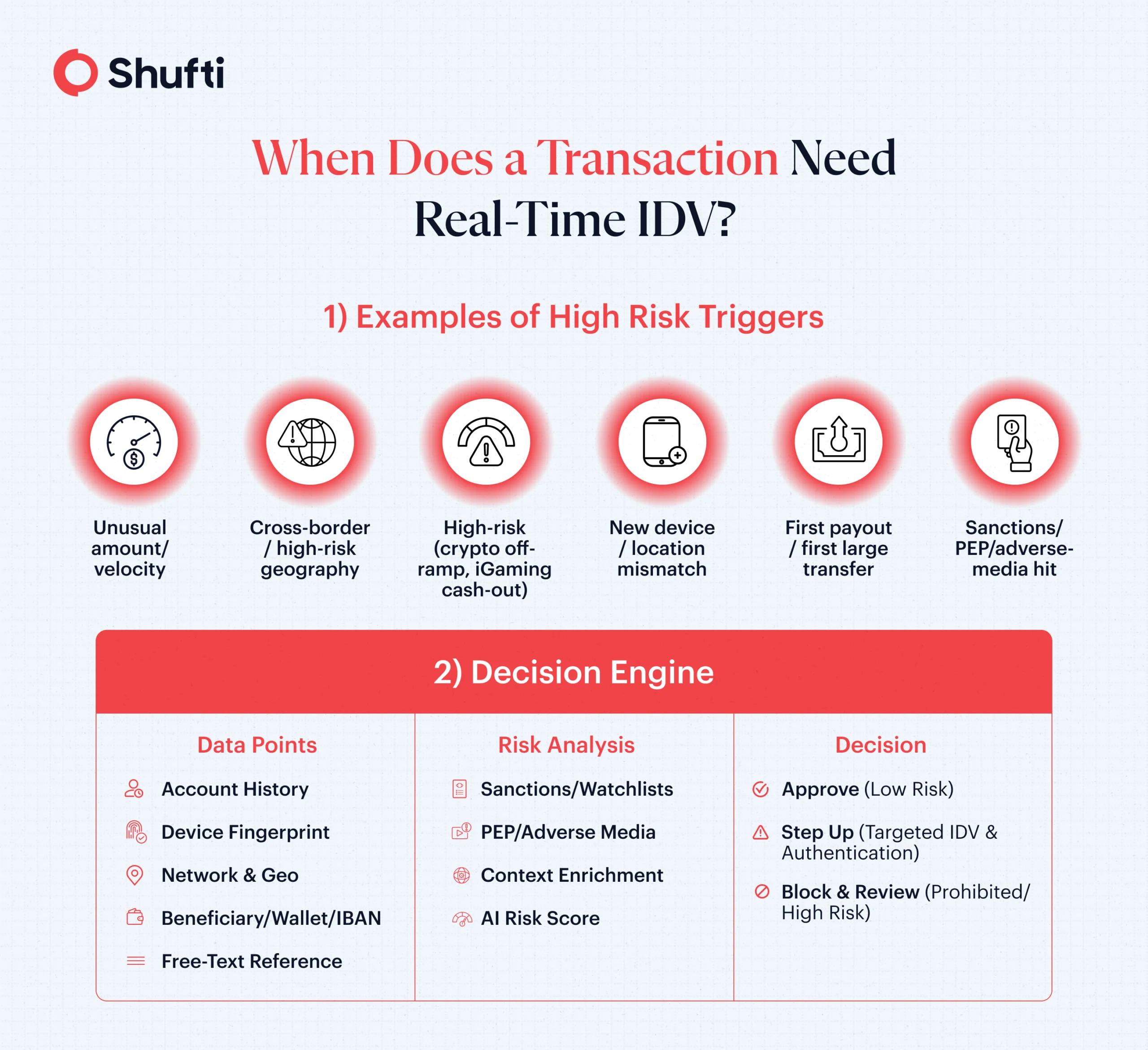
Where does risk concentrate?
Speed, cross-border connections, and the anonymity factor put certain sectors on the front line. This includes crypto/VASPs, CNP transactions and remittances (instant settlement across multiple payment systems), iGaming (high velocity and cash-like behaviors), and high-value goods/real estate (large, infrequent, opaque flows). Global risk assessments consistently flag these as priority areas for ongoing monitoring.
How does real-time IDV work in practice for high-risk scenarios?
What works in practice is layered and fast: verify the person, verify the parties, verify the pattern, without derailing the customer.
At the identity layer, the norm is to pair document verification with a biometric face match and liveness detection so businesses know a real human is present and the face matches the credential. Passive liveness is an example of hardening against spoofs and deepfakes while keeping the flow minimal. This is exactly what a business wants when a transaction tips into high risk.
When assurance must be maximal, firms add NFC “chip-reading” for ePassports and eIDs. Such cryptographic checks on the document’s secure chip are extremely hard to fake and fast to verify. Many businesses still reserve this for onboarding; the smarter move is to trigger it dynamically for specific high-risk transactions, such as where ATO is suspected.
Real-time eIDV/database checks supplement documents by cross-checking name/DOB/ID numbers against authoritative sources, helping catch synthetic identities and data tampering without adding friction. Video KYC remains the required route in some jurisdictions, and it can be invoked as a step-up only when risk justifies it.
Crucially, IDV at the point of risk is coupled with party screening (sanctions/PEP/adverse media) and transaction risk analytics. Screening can’t be left to batch jobs when a payout or transfer is about to clear. Screening needs to run before the transaction gets released. Meanwhile, AI-driven scoring uses device and network signals, velocity, geolocation, and history to decide whether to approve, block, or step up to stronger identity proof.
What best-in-class looks like (and how to get there)
A mature capability doesn’t hammer everyone with the heaviest verification all the time. It makes smart, real-time choices:
- Businesses should use standard verification for low-risk situations, then step up when a specific combination of risk factors appears. For example, a first-time large cross-border transfer to a grey-listed jurisdiction, a crypto withdrawal to a newly sanctioned wallet, or a payment where attributes like geolocation, device ID, or other attributes may imply a potential CNP fraud or account takeover (ATO). That step-up might be a passive selfie with liveness, or an NFC read where supported, or a short live video, whatever gives a business the assurance it needs for that moment.
- Screen the parties and fields (names, wallet addresses, IBANs, free-text references) before execution, not just overnight, so institutions can stop prohibited or high-risk counterparties in time.
What’s next for tech-based identity verification?
Plenty of capability is already on the shelf, just not yet widely wired into transaction flows.
Phishing-resistant step-up tied to identity proof. Many programs still rely on SMS OTP for high-risk payments. Swapping that for a biometric like liveness detection of the verified user, especially on first payouts, new devices, or cross-border wires, cuts ATO risks substantially.
Broader chip-level verification. NFC reads have matured, and they shouldn’t be confined to onboarding. Trigger them on high-value or first-time payouts, crypto off-ramps above thresholds, or cash-out requests in iGaming to raise assurance without blanket friction.
Sharper real-time triggers. Supervisors have asked firms to define when real-time monitoring is mandatory. Many teams can go further by making those triggers explainable: “Which combination of risk factors fired? Which control reduced residual risk?” That auditability matters when you’re defending a decision to a regulator or scheme.
The Takeaway
High-risk transactions demand real-time verification of who is acting and whether the payment should proceed. The compliance case is clear, and the commercial case gets stronger with every new fraud attempt. If a business can prove identity and screen parties in milliseconds, and escalates only when risk justifies it, it can prevent fraud without obstructing the legitimate transactions.
Decreasing fraud and improving compliance with Shufti’s Transaction Trust Screening
The practical path is to assemble proven capabilities and make them work at authorization time. Shufti’s stack covers the essentials for high-risk moments, which include real-time document + facial biometrics with iBeta Level 2 certified passive liveness. The solution also supports NFC chip reads for e-IDs/passports, eIDV, and Video KYC, where mandated, and sanctions, PEP, and adverse media screening.
Its AI-driven Transaction Trust Screening utilizes dozens of datapoints from users’ accounts, devices, and location, enriching it multiple times in under 15 milliseconds to trigger the right step-up only where necessary and ensuring an unobstructed flow of legit transactions. That balance is how you meet risk-based obligations without turning your product into a queue.
To see how Shufti seamlessly filters high-risk transactions, strengthening compliance and building fraud resilience, request a demo!