How to Prevent a Data Breach?

Global data breaches have surged in both frequency and financial impact. IBM’s 2025 Cost of a Data Breach Report found that the global average cost per data breach is $4.4 million!
What does this mean for businesses that hold and manage customer data?
IBM’s report makes one thing clear: compliance teams, Chief Information Security Officers (CISOs), and businesses must realize that data breaches are more serious than “just another IT problem.” Companies need to invest in proper data security frameworks with purpose-built solutions to counter data breach attempts and mitigate the cost of detecting and countering such cyberattacks.
To strengthen their defenses against such invasive attacks, businesses must first understand what constitutes a data breach, what causes it, and how to protect sensitive data.
What is a Data Breach?
A data breach occurs when sensitive, confidential information, such as personally identifiable information (PII), is accessed without authorization. Sometimes, even an accidental exposure of personal data can qualify as a breach under most data protection regulatory frameworks, such as the EU’s General Data Protection Regulation (GDPR) and the UK’s Data Protection Act.
Data breaches may also occur due to stolen credentials, unreliable third-party data security, outdated software, or internal bad actors. Through accessing and releasing sensitive confidential data to the public, such breaches disrupt the three main principles of data security:
- Confidentiality – by exposing personal information such as addresses, bank account details, and location.
- Integrity – unauthorized access to data can lead to tampering, theft, or manipulation that renders the data unreliable.
- Availability – disruption in the system can prevent legitimate users from accessing important information.
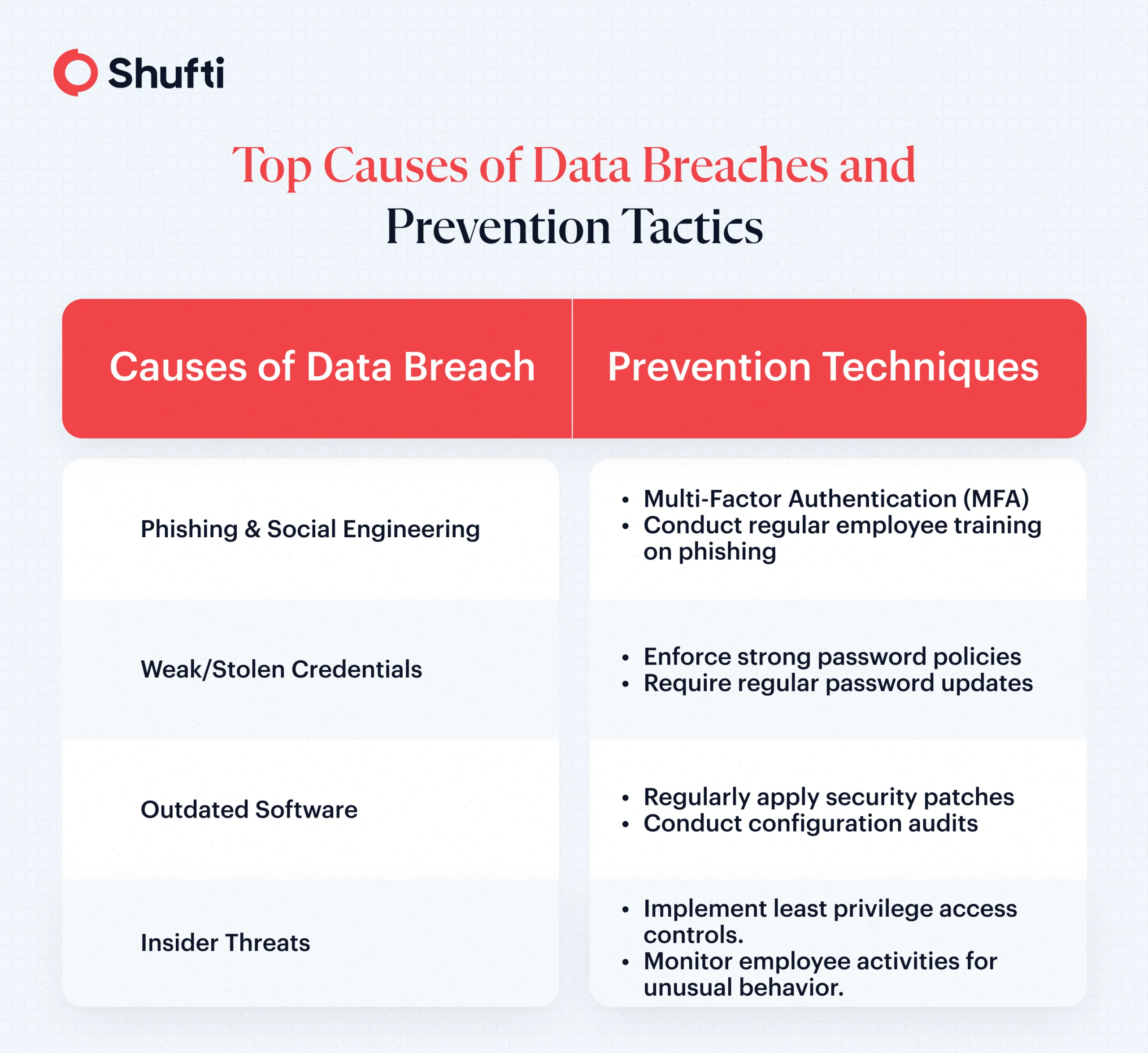
What Causes a Data Breach?
Even a well-established business is prone to data compromise due to human errors and procedural weaknesses. Companies are increasingly adopting advanced data breach prevention solutions to address different data breach types and identify common vulnerabilities, such as:
-
Phishing Attempts:
Phishing involves bad actors manipulating individuals into sharing sensitive personal information, such as account login details, through fraudulent and deceptive emails, messages, and calls. With phishing attacks accounting for 16% of data breaches in 2025, they have become a highly effective method for cybercriminals to infiltrate systems.
Phishing is often used in combination with social engineering tactics, in which bad actors deceive employees into granting unauthorized access to company systems.
-
Unauthorized Third-Party Access:
Unsecure third-party vendor connections are now one of the most exploited entry points for breaches. In fact, third-party vendor compromises were the second-most-common initial attack vector, accounting for 15% of all data breaches in 2025.
Such data breaches were particularly damaging to businesses, costing an average of $4.91 million per incident. This expense includes the combined costs of detection, investigation, and recovery efforts for each breach.
-
Weak or Stolen Credentials:
The rise in credential stuffing attacks, in which criminals use stolen login credentials from previous data breaches on one platform to gain access to sensitive data on another, continues to pose a significant risk. Employees often reuse passwords across multiple platforms, making them easy targets for cybercriminals.
Credential theft is often a precursor to larger attacks, allowing hackers to move undetected within the system for extended periods.
-
Outdated Systems:
Misconfigured and outdated systems are particularly vulnerable to cyber attacks. Bad actors routinely exploit this vulnerability in cloud-based systems as more and more businesses provide cloud data storage without the necessary data security in place.
Furthermore, businesses rarely update their data storage systems. Cybercriminals exploit this lax attitude towards data storage with constant attack methods that have been used before. Since the system is rarely updated, the vulnerabilities are rarely patched.
-
Internal Threats:
Internal threats to data storage in the form of malicious or negligent employees continue to be one of the most expensive causes of data breaches. In 2025 alone, internal threats to data storage have cost an average of $4.92 million per breach, making them the costliest threat vector for businesses.
The rise in remote working introduces additional complexity to this problem, as employees routinely access company systems from diverse, often unsecured, networks.
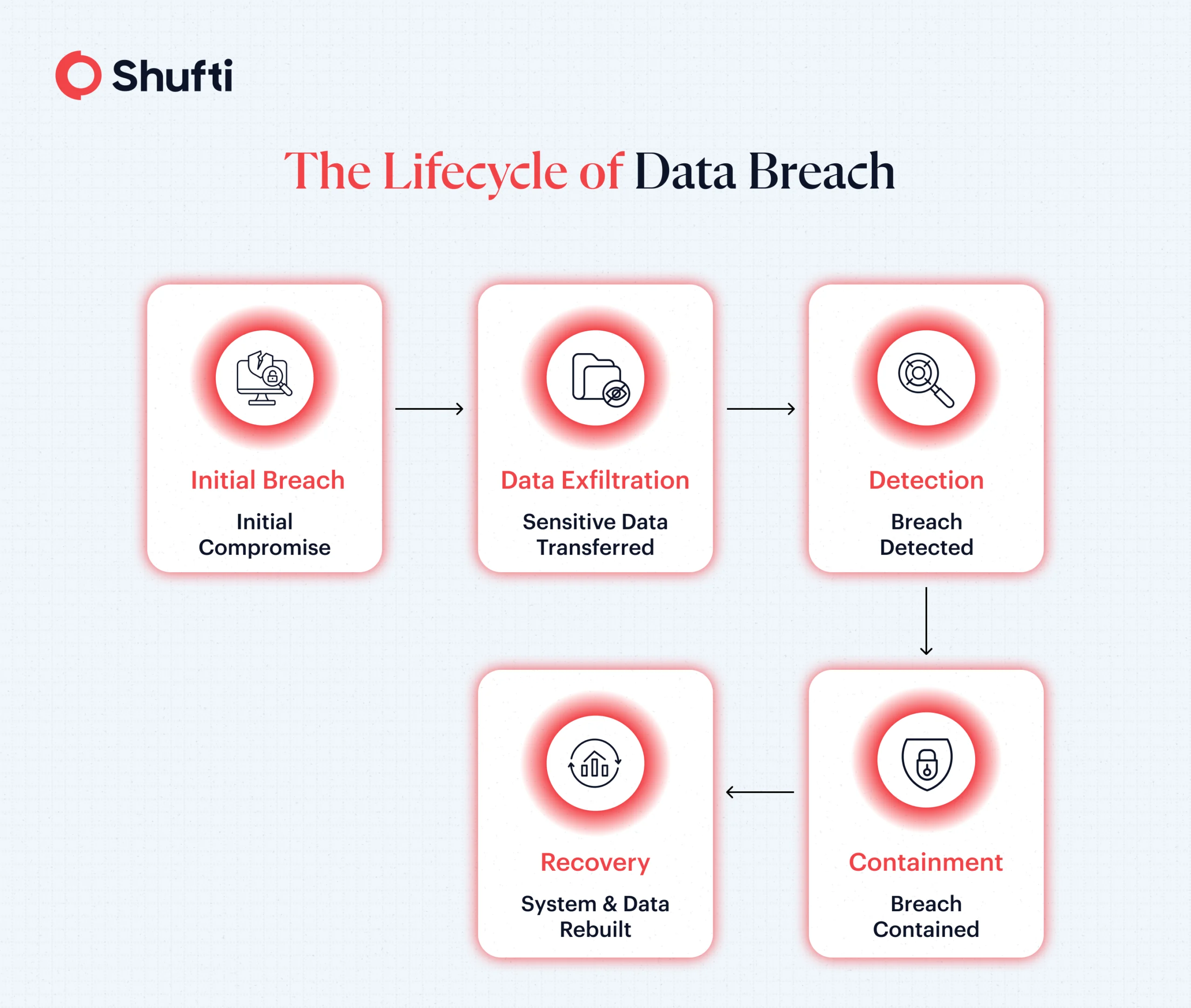
Data Breach in the Real World
Recently, a high-end French retailer suffered a cyber-attack that compromised customer data, including names, contact information, and purchase history. The realtor revealed that an unauthorized third party had accessed systems and gained access to sensitive data.
Although the breach did not expose financial details, the retailer warned of potential phishing attacks that could follow, with bad actors now having enough customer information to initiate such attempts.
How to Prevent Data Breaches?
The very first preventive step businesses must take is to carry out a comprehensive risk assessment of their systems to identify any potential vulnerabilities. Once gaps have been identified, businesses can develop a data breach prevention strategy that is tailored to their risk exposure. Some proven strategies to prevent data breaches include:
-
Strengthen Identity and Access Management (IAM):
Enforce multi-factor authentication (MFA) and adopt the principle of least privilege, ensuring that users have access only to the data necessary for their roles. Additionally, restricting access to sensitive data can prevent data leaks and theft from unauthorized sources.
Regularly review and update access permissions to minimize unauthorized access.
-
Monitor and Secure Third-Party Access:
Limit vulnerability by prioritizing business partners that operate in-house and have full ownership of their systems, data, and infrastructure. Indirect outsourcing, whereby partners outsource tasks to third parties with inadequate cybersecurity, is a growing vulnerability. Vendors that do not rely on secondary subcontractors allow businesses to mitigate the threat of data breaches by reducing the number of initial attack vectors.
Additionally, businesses should vet third-party vendors carefully to ensure that their data security and protection measures meet industry standards. This verification may be done through audits, data handling agreements, or simulations with the third-party vendors’ network.
-
Automate Detection and Response:
Utilize AI-driven security tools to detect unusual activity in real-time. Automated data breach solutions help businesses speed up the response times to contain data breaches.
-
Frequently Update Security Patches:
Unpatched systems are among the most vulnerable entry points. Through regularly updating software, businesses can patch and close vulnerabilities before they can be exploited.
-
Train Employees on Security Best Practices:
Human error remains a leading cause of data breaches. Regularly training employees to recognize phishing attempts and to follow industry-standard data-handling protocols is necessary to reduce such errors.
Partnering with trusted data breach prevention services and tools that incorporate these strategies can strengthen data security. However, it is important to note that no preventive measure can guarantee one hundred percent safety from cyberattacks.
Building Trust Through Secure Verification:
Many businesses struggle to shrink third-party exposure while meeting GDPR timelines. Shufti helps reduce breach risk with:
- 100% in-house identity verification technology, reducing reliance on external tech supply chains.
- On-premises deployment for organizations that must keep verification data inside controlled environments.
- Independent validation: GDPR compliance, ISO 27001, ISO 27701, and QG-GDPR for data protection and privacy.
- Biometric authentication and MFA options that slot into enterprise IAM programs to restrict access to sensitive systems.
Request a demo to see how verification and access controls can be unified across onboarding and authentication.

 Explore Now
Explore Now













