Combating 8 Prevalent Biometric Fraud Through a Single AI Solution

Considering how criminals are attempting new strategies to “steal a face”, companies are no longer satisfied with traditional security checks and access mechanisms. Instead, they are seeking advanced biometric facial verification solutions – ones that utilize liveness detection. While this feature has proven to be considerably effective in combating facial spoof attacks, not all liveness solutions are equally capable. In this blog, we will be taking a look at the eight prevalent types of biometric frauds that have been recorded so far, and also provide insights about the one solution that can tackle all of them.
What Are Biometric Frauds?
Biometric fraud refers to any attempts made by a perpetrator to misuse biometric data or spoof biometric systems. The recurring problem of biometric fraud has become a primary concern for industries worldwide, particularly finance and banking. Some common types of biometric fraud are video replays, photo attacks, deepfakes, and many more.
Spoof Attacks Against Facial Recognition Technology
Amongst the numerous biometric technologies available today, facial recognition has gained particular prominence. The surging popularity of “selfies” has contributed to the adoption of facial recognition, showing that consumers are comfortable using this method of verification.
On the downside, the technology has also appealed to cybercriminals as it provides them new means for gaining illegitimate access and monetary benefits. Here’s a list of the most prevalent biometric frauds that are targeted at facial recognition systems.
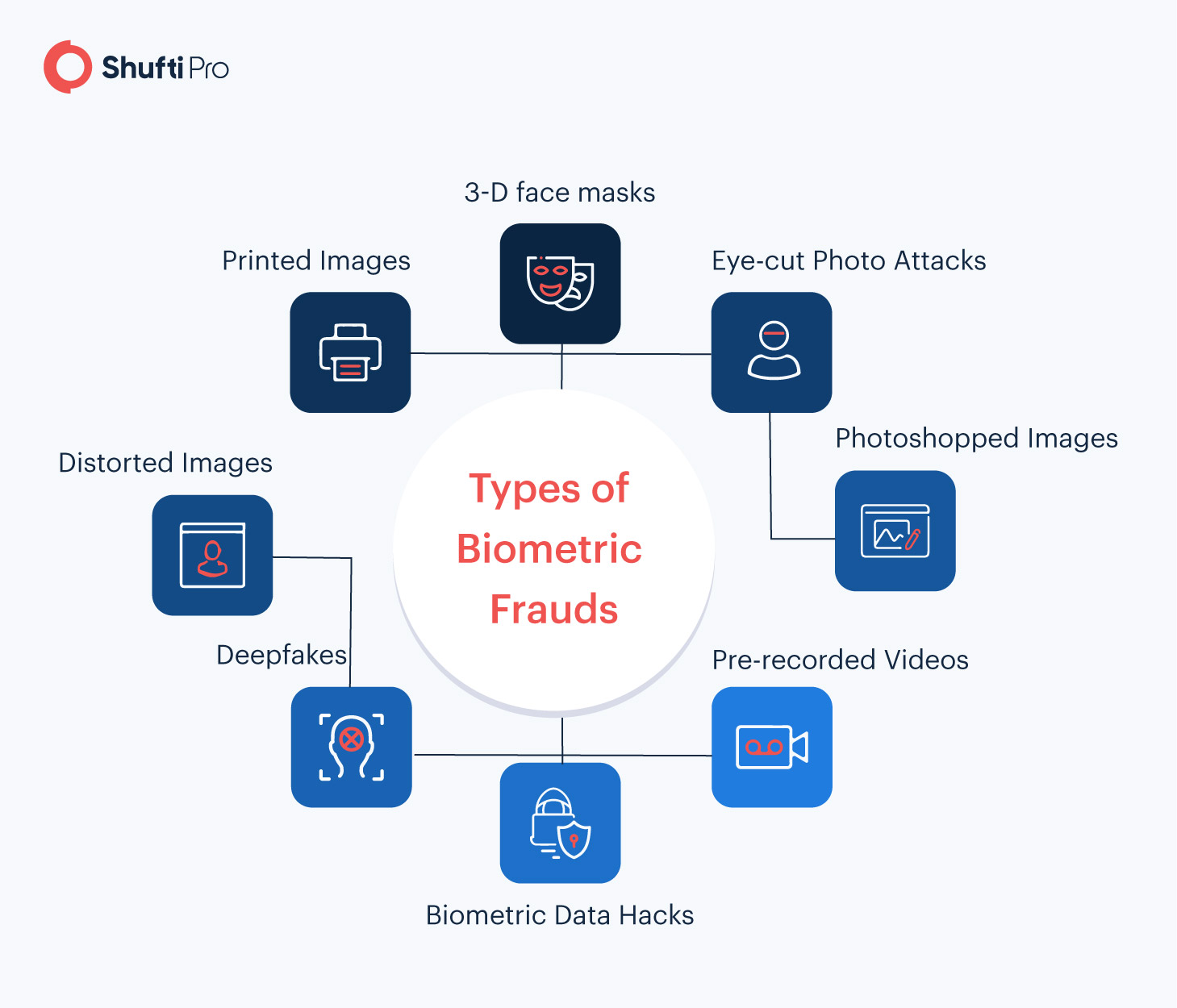
3-D Face Masks
When it comes to spoofing biometric facial recognition technology, wearing a 3-D face mask is the oldest trick in the book. Fraudsters have used silicone masks to deceive identity verification systems on numerous occasions in the past, particularly to hack into accounts. Facial recognition solutions must have the capabilities of micro-expression analysis to detect this threat.
Back in 2018, a Forbes study revealed how 3-D face masks were used to spoof the facial verification system of four android phones. For banks and other financial institutions, this poses a major threat as fraudsters can easily use 3-D masks to bypass initial identity checks during the customer onboarding stage. This can lead to countless risks of fraud, including identity theft, account takeovers, and mass data breaches.
Printed Images
This technique involves the use of someone else’s photo to fool facial recognition technology. The image can be easily obtained online, printed, and then displayed through a digital device to impersonate another person. If the integrated facial recognition solution does not have the feature of liveness detection, it can easily be fooled through this technique.
Eye-cut Photo Attacks
In this scam, fraudsters cut out the eye regions of a printed picture to exhibit blinking behavior. The printed photo could be of another person, whose confidential data would likely be compromised if this manipulation is left undetected. Facial recognition technologies that lack sufficient analysis of a person’s facial attributes can easily be spoofed through eye-cut photo attacks. 3D depth perception helps identify such spoofs as it is not possible to mimic varint facial depth on a straight page.
Distorted Images
To spoof the liveness detection feature of a facial recognition system, printed images are bent and moved in different positions and angles. As a result, inadequate biometric systems detect the image as a real person, paving the way for numerous crimes to be committed.
Photoshopped Images
Face verification typically allows customers to get verified using two methods: by uploading an image as proof of identity or getting scanned in real-time through a webcam. Fraudsters try to find a loophole in this system and upload photoshopped images to avoid being identified through facial authentication solutions.
Deepfakes
Deepfakes are fake audios or videos that are altered through machine learning technology and are used to impersonate someone else. The threat of deepfakes is increasingly gaining prominence, particularly after a UK-based energy firm’s CEO was tricked into transferring USD 243,000 to a criminal – all through a deepfake. Apart from this, countless other sectors have also voiced their concerns regarding deepfake technology.

Banks and financial institutions need to utilize robust facial biometric solutions that include advanced features of 3-D depth perception and liveness detection. Without these, deepfake videos and audios would be left undetected, allowing criminals to carry out numerous financial crimes.
Pre-recorded Videos/Replay Attacks
A more sophisticated method of tricking the facial recognition system involves the use of a looped video of a victim’s face. In this approach, facial movements recorded in the video are made to appear natural to successfully pass liveness detection. Compared to an imposter holding a printed image, this facial spoof attack is more difficult to detect.
Biometric Data Hacks
Cybercriminals cause the recurring dilemma of database hacks for financial institutions that store customer data online. In the event a biometric database is breached, victims face challenges from two ends. First, their confidential data is compromised. And secondly, the stolen biometric data is used to commit other crimes such as account takeovers, identity theft, and much more.
Want to learn more about biometric fraud and its predictions for 2021? View our Global Identity Fraud Report!
A One-stop Solution For Biometric Fraud Prevention
The AI-powered face verification solution offered by Shufti provides companies with a robust mechanism for minimizing the threat of biometric fraud. In particular, facial spoof attacks are detected in a matter of five seconds, and that too with an accuracy rate of 98.67%. The solution allows businesses to reduce the number of false negatives, ensure that legitimate customers are rapidly onboarded, and use AI technology to detect numerous spoof attacks.
Listed below are the key features of the face verification solution that makes it stand out.
Liveness Detection
Liveness detection refers to the ability of a biometric system to detect if the image of a face is real or just another spoof artifact. Shufti’s face verification solution leverages liveness detection to verify the end-user’s physical presence and facial movements. This reduces the probability of successful facial spoof attacks and the rate of false acceptance.
Micro-expressions Analysis
The face verification solution uses AI models to detect subtle micro-expressions of the end-users. This feature allows companies to enhance the detection of deepfakes, replay video attacks, and other similar spoof attempts.
3-D Depth Perception
Using 3-D depth analysis the face verification solution effortlessly detects spoof attacks such as silicon face masks and fraudulent printed or photoshopped images. This is accomplished through a detailed analysis of the three-dimensional geometry of the end-users face.
Human Face Attributes Analysis
By analyzing the facial characteristics of an individual, the face verification solution easily filters out imposters. This involves the verification of attributes such as the distance between the eyes, the shape of the lips, the width/length of the forehead, and much more.
AI Mapping Techniques
AI mapping techniques have the ability to detect eye-cut photo attacks, 3-D masks, and numerous other facial spoofs. It involves the use of machine learning and AI models to map the end-users face and ID document photos for highly accurate verification.
Take a look at our White Paper to learn how biometric technology is reshaping identity verification.
Conclusion
To detect the ever-increasing facial spoof attacks, a robust verification system is required that leverages AI models. Without features such as liveness detection, 3-D depth perception, and AI mapping, fraudsters can easily infiltrate the system, wiping out millions of dollars from a company’s bottom line. Shufti’s face verification solution not only provides rapid authentication but offers an effective mechanism for biometric fraud prevention.

 Explore Now
Explore Now













