Making Knowledge Based Authentication Practicable for IDV

- 01 What is Knowledge-Based Authentication?
- 02 How Does KBA Verification Work?
- 03 What Are the Two Types of KBA Authentication?
- 04 What are the Key Industry Applications of Knowledge Based Verification?
- 05 How KBA Compares to Other Verification Methods?
- 06 Practical Practices for Implementing KBA in The System
- 07 Limitations and Challenges of Knowledge-Based Authentication
- 08 The Future of Knowledge-Based Authentication
- 09 Modernizing Identity Verification with Shufti’s Knowledge-Based Authentication
Have you ever faced a security question while authenticating a transaction or signing into your account?
It may have asked for your childhood best friend’s name, your mother’s middle name, or the name of the school you attended in kindergarten. These questions are examples of Knowledge Based Authentication (KBA).
Many organizations have been using KBA as a part of their account login process to validate that the individual is who they claim to be. Knowledge based authentication is more commonly used in industries where risk is moderate and high.
| According to FATF Guidance on Digital Identity (2020):
Knowledge factors: Something you know, such as a shared secret (e.g., username, password, or passphrase), a personal identification number (PIN), or a response to a pre-selected security question. |
While KBA may not offer the best security on its own, it proves to be effective when combined with other methods. However, it is crucial to understand what exactly KBA entails and how secure it actually is.
What is Knowledge-Based Authentication?
Knowledge-based authentication, or KBA, is a process of verifying the identity of a person through their personal information. It primarily works by asking questions only the real user can answer, which they have previously submitted for verification.
Organizations are seen more often using the KBA verification process as a mild security measure to prevent unauthorized access in the system. The central concept is that a person’s awareness of specific facts ultimately demonstrates their identity.
With the growing prevalence of automated bots and botnet attacks that mimic user behavior, KBA serves an added function. It verifies that the responding entity is a genuine human rather than an automated script. This approach relies on “something you know” to confirm who the user is.
KBA is an older verification method compared to fingerprint and facial recognition. However, it remains widely used for secure authentication, particularly to prevent or recover from account takeover (ATO) incidents and verify user access in online services.
How Does KBA Verification Work?
KBA supports secure access in several ways. It complements multi-factor authentication (MFA) for higher assurance in sensitive transactions and helps legitimate users regain account access when credentials are forgotten.
If someone forgets their password, they may need to answer security questions to regain access to their account. These security questions are set up when the account is initially created. KBA starts with the information provided when an account is set up.
The website or application, after accepting the login information, asks a relatively simple yet memorable question that also serves as proof of identity for that person. It allows users to choose and respond to a set of personal questions. Later, if they need to verify their identity, they simply answer those same questions. If their answers match, access is granted.
However, different platforms apply knowledge-based authentication using distinct techniques, as discussed below.
What Are the Two Types of KBA Authentication?
Knowledge-Based Authentication has two types: Static KBA and Dynamic KBA. Each method offers different levels of security.
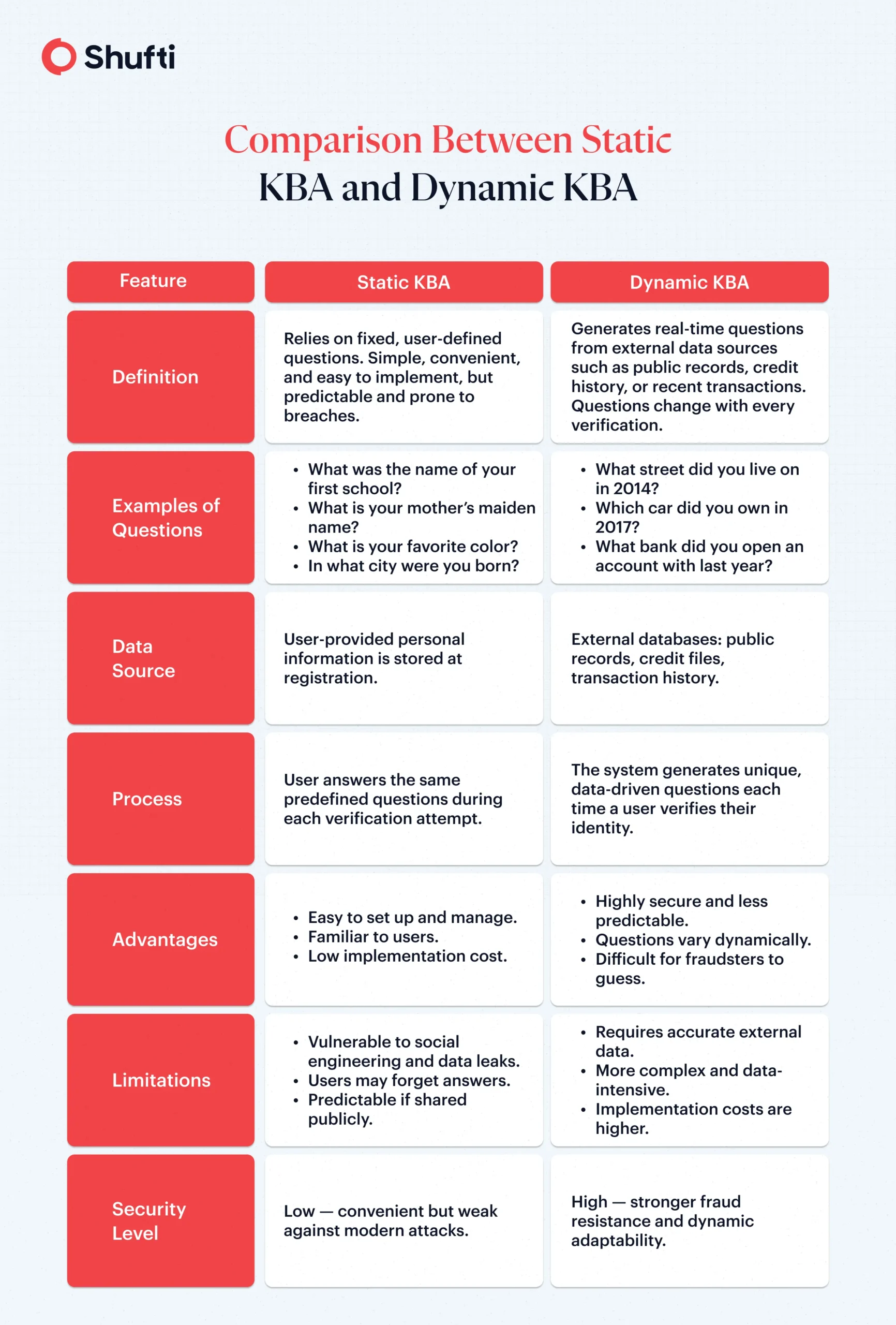
What are the Key Industry Applications of Knowledge Based Verification?
KBA remains a widely used and trusted identity validation method across several industries where confirming a user’s legitimacy is crucial. For example, U.S. tax forms and e-signature solutions often mandate KBA before authorization. Here are the sectors that require Knowledge-Based Verification:
- Banking and Financial Services
- Social media marketplaces
- New Economies
- Insurance
- E-Signature
- Document Management Platforms
- Legal Services.
- Telecommunications
- Utilities
- Government and Public Services
The method is popular because it is cost-effective and convenient. It is also easy to integrate with existing systems. Users can answer personal questions without needing new devices or biometric tools. This feature makes KBA practical for large-scale digital operations.
While KBA offers convenience, it should never be relied upon as the sole layer of security. Organizations need to evaluate their risk tolerance and the sensitivity of their data. Along with any compliance requirements, before implementing Knowledge Based Verification into their system.
How KBA Compares to Other Verification Methods?
Knowledge Based Authentication is one of several techniques used to verify identity, each with distinct strengths and weaknesses. For instance, passwords are the most common and simplest form of authentication. They also rely on what the user knows, just as KBA does.
A common way to verify identity is through biometric authentication. This method often uses fingerprints and facial recognition. While these methods are hard to copy, they raise concerns about privacy and reliance on devices.
Moreover, there is also a device-based authentication method known as One-Time Passwords or OTPs, which sends temporary codes to a registered phone or email address to verify the user.
Along with these methods, there are hardware tokens that generate secure codes through a physical device. They are highly secure but costly to deploy and easy to lose.
KBA is an affordable option because it requires no specialized equipment. Thus, to ensure strong protection, organizations frequently combine KBA with multi-factor authentication. For instance, a bank might use a security question alongside a mobile OTP to create multiple layers of security. This would effectively guard against unauthorized access and the potential threat the user might face.
Practical Practices for Implementing KBA in The System
To implement Knowledge-Based Authentication effectively, choose dynamic KBA whenever possible. It is more secure and adaptable than static questions. Also, the business must reduce the number of verification attempts to curb brute-force guessing and should always include KBA in MFA configuration to provide greater security.
Organizations are also equally concerned with privacy and data governance. Therefore, they are required to obtain user consent, ensure the protection of the sources of that data that generate challenge questions, and monitor the pattern of failed attempts to identify attempted fraud early.
Limitations and Challenges of Knowledge-Based Authentication
Although KBA is an affordable and widely used method of verification, it has significant disadvantages. Data exposure is one of the primary concerns because personal information on which KBA is based can be readily disclosed on social media or in hacked databases, thus losing its credibility.
Also, the use of static questions may create usability issues as the user may forget the answers or provide variations that result in unsuccessful authentications. In general, dynamic KBA depends on precise data aggregators that are not available in all regions.
More privacy laws, like GDPR, discourage keeping unnecessary personally identifiable information (PII). These laws show that knowledge-based authentication (KBA) alone does not meet today’s security needs and should be combined with other verification methods.
The Future of Knowledge-Based Authentication
With the development of digital identity verification, KBA is no longer the main form of security but rather a supplement to the verification. As AI-based fraud detection, behavioral analytics, and passwordless authentication have emerged, organizations are discovering new opportunities to verify user identities.
While KBA may not be strong enough on its own, it further augments the security of other authentication methods. The future of KBA may see a combination of traditional methods with modern, data-based verification.
Modernizing Identity Verification with Shufti’s Knowledge-Based Authentication
As the digital threats are evolving every second, the organizations have never been in greater need of more intelligent ways to verify users without compromising convenience.
Shufti Knowledge Based Authentication feature functions as part of secure multi-factor authentication. It also works alongside biometric verification to support legitimate account recovery in case of account takeover (ATO) attempts.
The platform creates real-time questions that are hard but based on trusted information, which helps reduce guesswork and lowers the chance of fraud. It also allows for easy MFA setup to enhance security and meet industry requirements.
Empower the business with Shufti’s intelligent and user-friendly KBA verification. Request Demo!
Frequently Asked Questions
What is knowledge-based authentication?
Knowledge-Based Authentication verifies a user’s identity through personal questions that only the legitimate user can answer.
What does knowledge-based authentication involve?
It involves asking predefined or dynamically generated personal questions to confirm the user’s authenticity during verification.
What is the main difference between static and dynamic KBA?
Static KBA uses pre-set questions, while dynamic KBA generates real-time questions from verified external data sources.
How are KBA questions generated?
KBA questions are generated from user-provided information or real-time data like financial, utility, or public records.

 Explore Now
Explore Now













