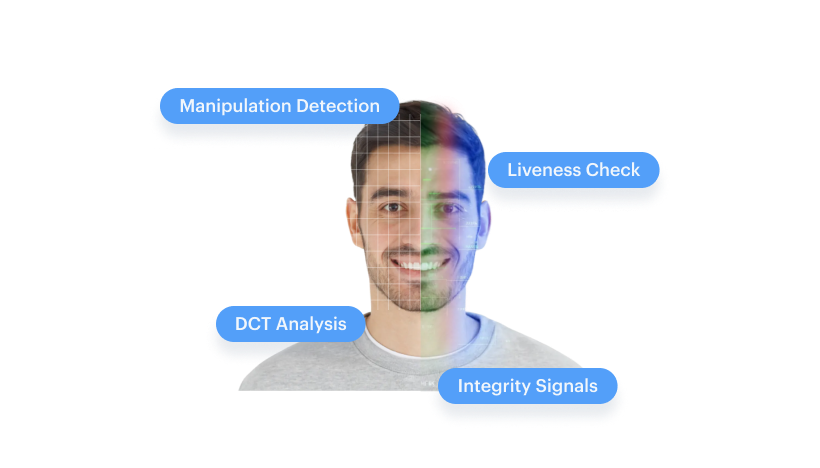
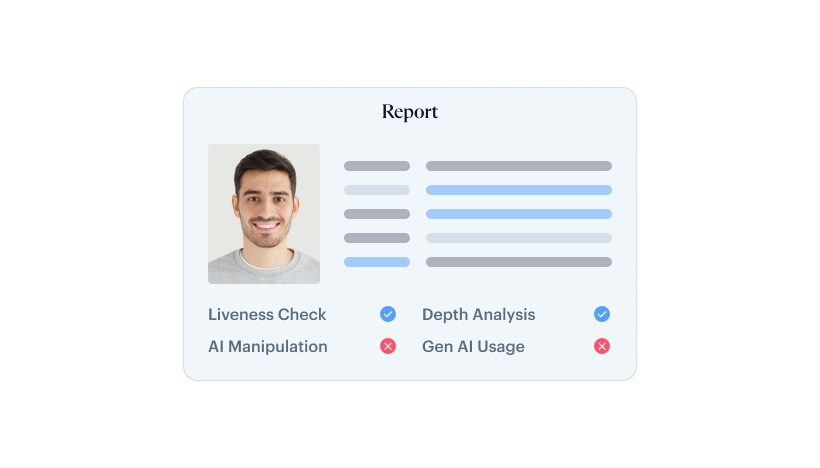
Deepfake Detection
Detect deepfakes that bypass visual checks
Deepfakes are designed to fool pixels. Shufti analyzes deeper signal artifacts using multi-stream RGB plus frequency-domain (DCT) detection, built to remain effective after compression, screenshots, and re-uploads. High-risk edge cases can be routed to expert review so decisions stay defensible.
Works across onboarding KYC, authentication step-up, account recovery, and agent-assisted verification, with audit-ready outputs.

The Growing Risk
Deepfake fraud is now multi-channel, face, video, and document
Real-Time Face Manipulation
Synthetic Identity Faces
Injection Attacks
Presentation Attacks
Document Manipulation
Real-Time Face Manipulation
Live face swaps and expression reenactment during video calls and verification. Modern tools track blinking, head motion, and lip movement, adapting dynamically during remote onboarding and agent-assisted verification. Built to fool both humans and visual-only detection.
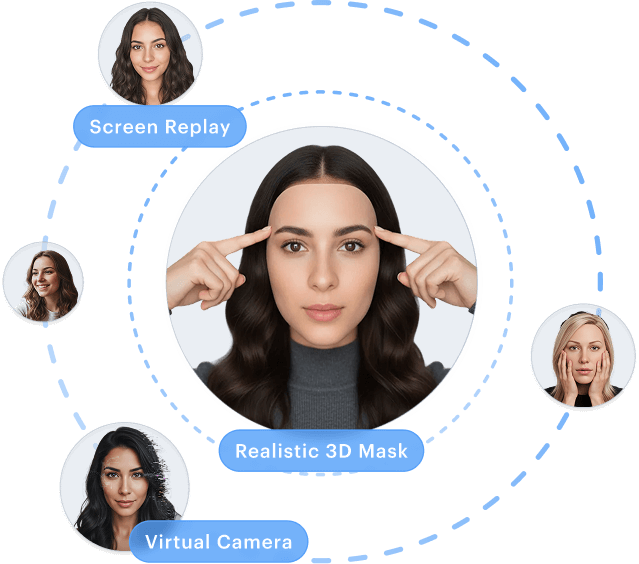
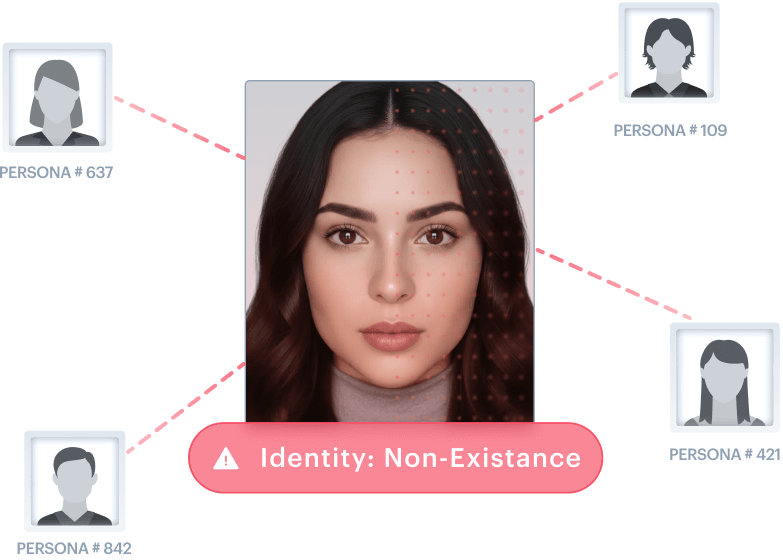
Synthetic Identity Faces
AI-generated faces that never existed. No real person to match against. Paired with fabricated data and documents to create complete synthetic identities that bypass checks assuming a real-world identity exists.
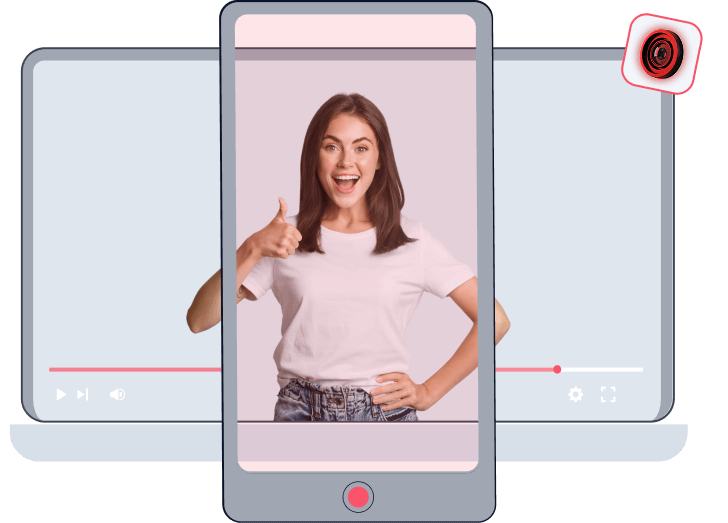
Injection Attacks
Virtual cameras, emulators, or stream substitution feed pre-recorded or AI-generated media directly into verification flows, bypassing physical cameras entirely. The attack targets the capture channel, not just the face.
Presentation Attacks
Screens, printed photos, masks, and video playback held to the camera to mimic a live person. Exploits systems that trust the capture source without validating 3D presence and device authenticity.

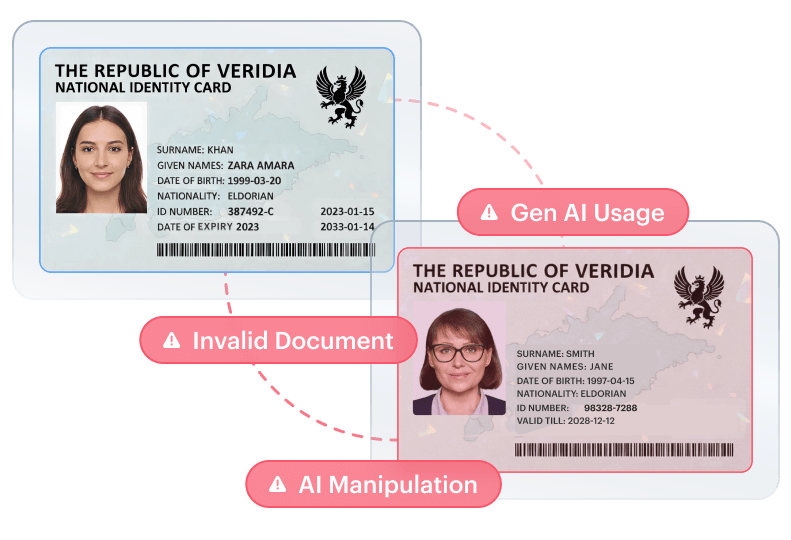
Document Manipulation
Altered or AI-generated documents designed to pass automated verification, data edits, image tampering, template imitation, synthetic creation. Often paired with face manipulation to complete a synthetic identity.
Beyond Visual Analysis
Why Shufti Detects What Others Miss
Multi-stream signal analysis
Shufti analyzes both standard visual signals and frequency-domain representations in parallel to surface manipulation artifacts that often persist after compression, format conversion, screenshots, and re-uploads. This is designed for real-world degraded media, not perfect lab conditions.
Designed for real-world media, not metadata
Detection is not dependent on EXIF, device metadata, timestamps, or file provenance. This reduces the risk of false confidence when attackers strip metadata or move content through social platforms and messaging apps.
Capture integrity for injection defense
Deepfake risk is not only what is in the frame, but how it enters the flow. Shufti adds capture integrity signals to help detect stream substitution patterns typical of virtual cameras and emulators, especially in step-up authentication and account recovery.
Continuous Threat Adaptation
As new generators emerge, detection must evolve. Shufti maintains an update pipeline that supports ongoing evaluation, retraining, and controlled model rollout so defenses keep pace with fast-changing synthesis methods.
Multi-Layered Liveness Architecture
End-to-End Verification Built to Defeat Deepfakes
Smart Liveness Detection
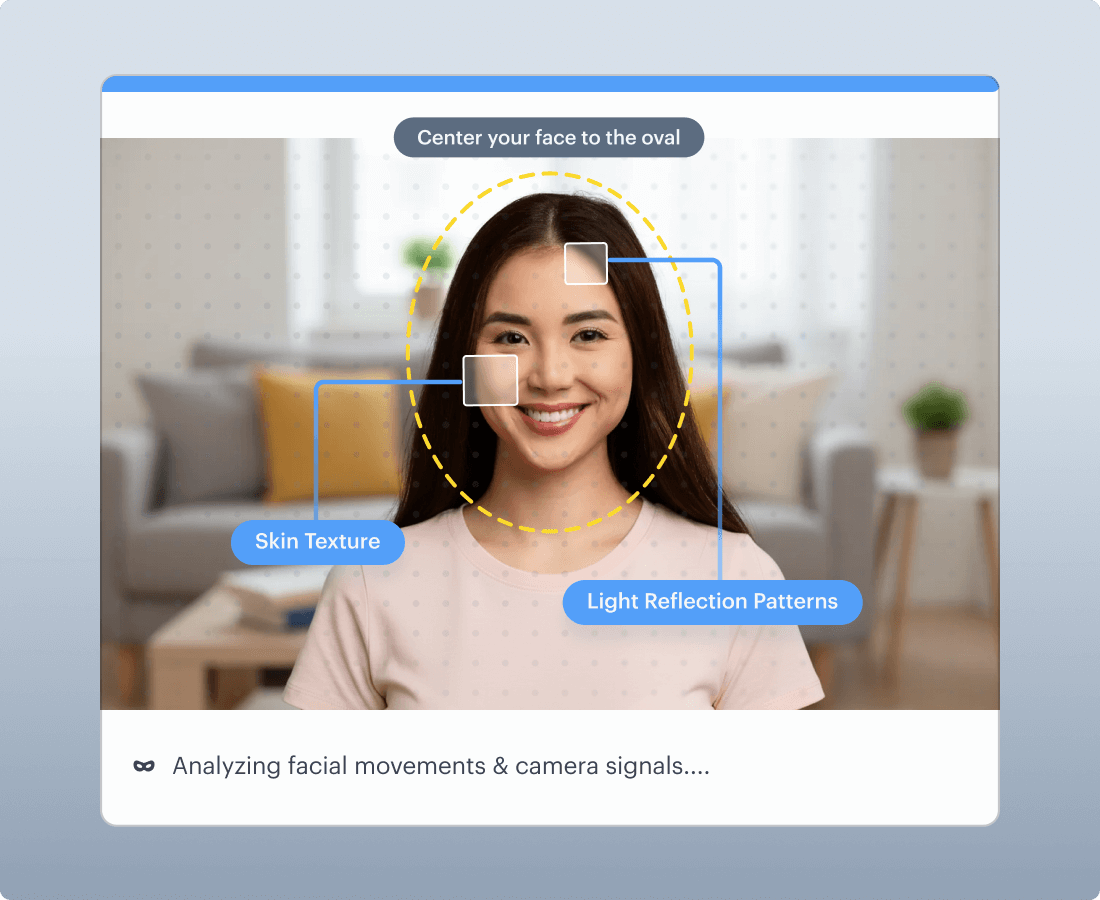
Passive Liveness
Runs in background, assessing light reflection patterns, skin texture, and depth cues to detect photos, screens, and masks. No friction added to verification flow.
Active Liveness
Adds controlled capture steps when risk is higher, such as account recovery, step-up authentication, and suspicious onboarding attempts. This helps reduce replay and scripted media attempts.
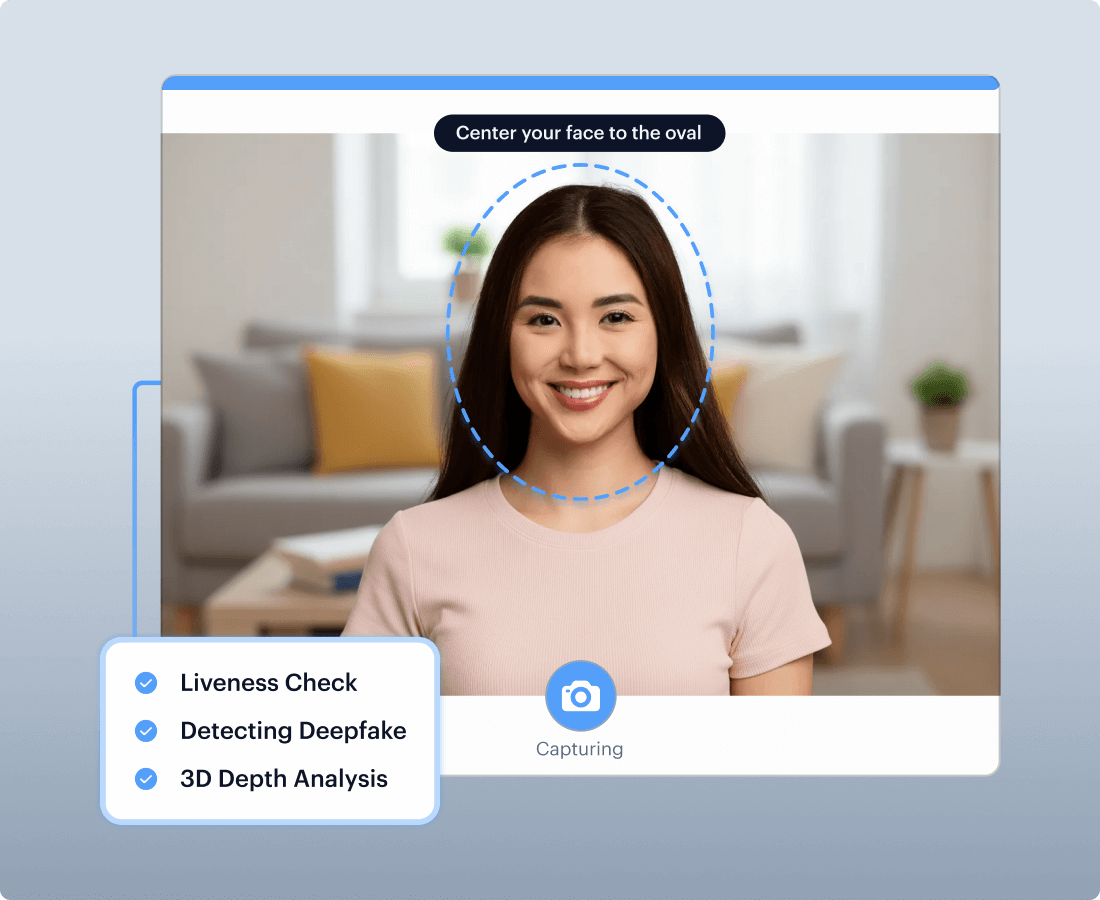
Video deepfake defense
Applies deepfake-focused analysis to video and frames to detect manipulation families such as swaps and reenactment, including patterns that survive compression and re-encoding.
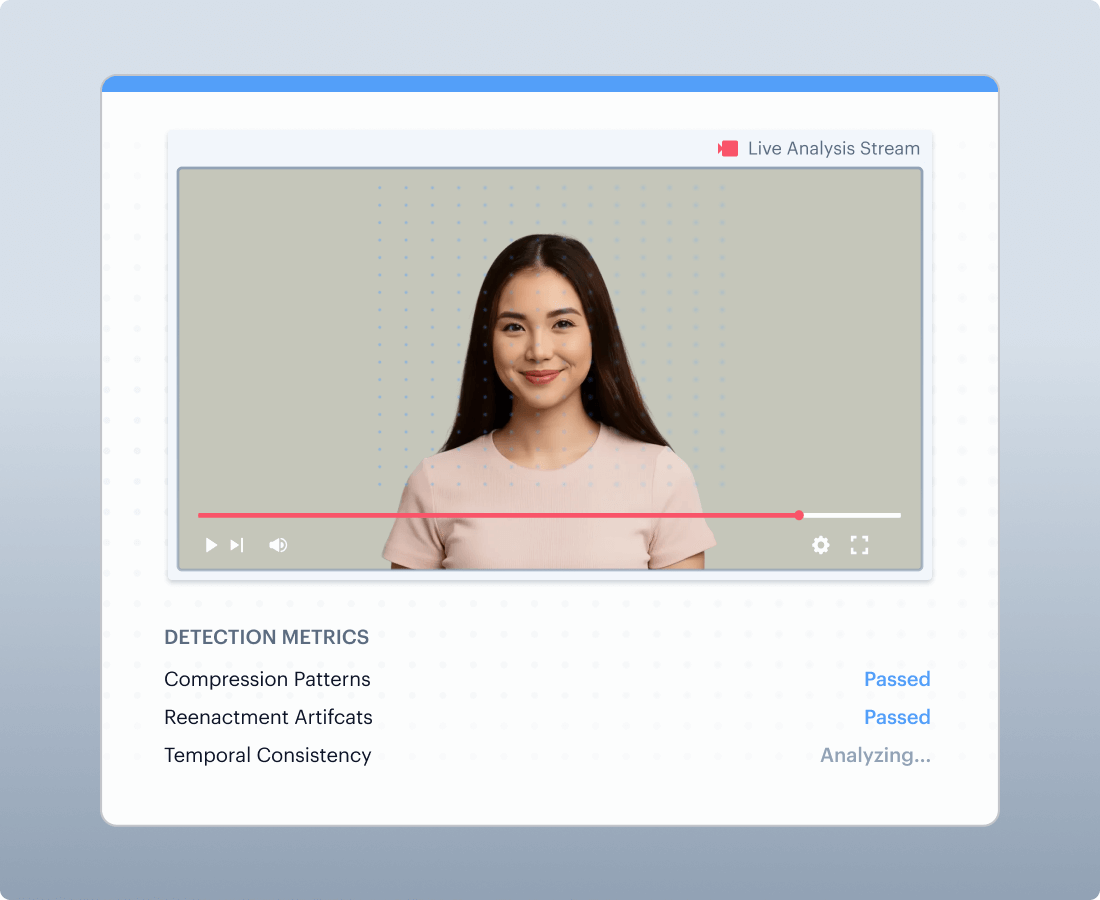
Deepfake & Injection Defense
Multi-stream RGB plus frequency-domain analysis is designed to identify generative artifacts that visual-only systems can miss, with added capture integrity signals for stream substitution risks.

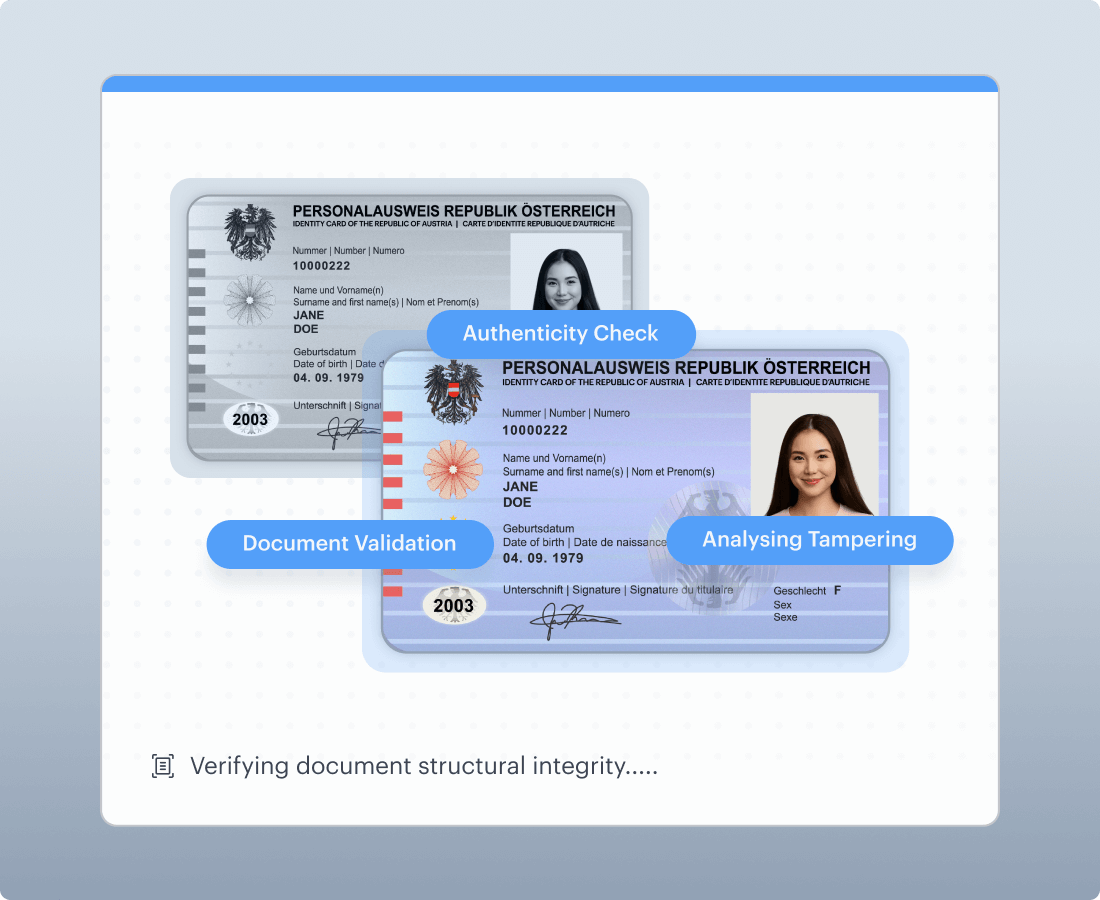
Document deepfake defense
Document verification can be attacked through tampering and synthetic documents. Document deepfake defense should be positioned as authenticity and integrity checks that complement face and video verification to prevent complete synthetic identity construction.






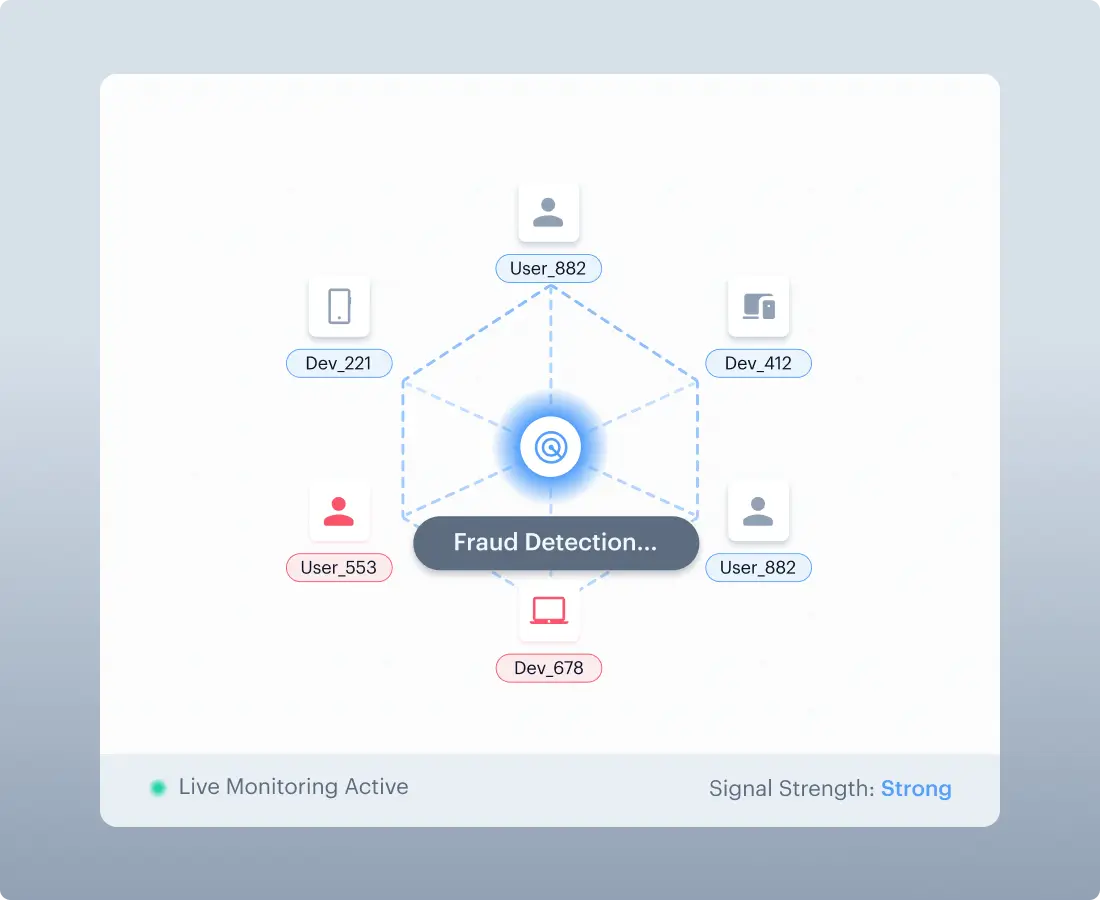
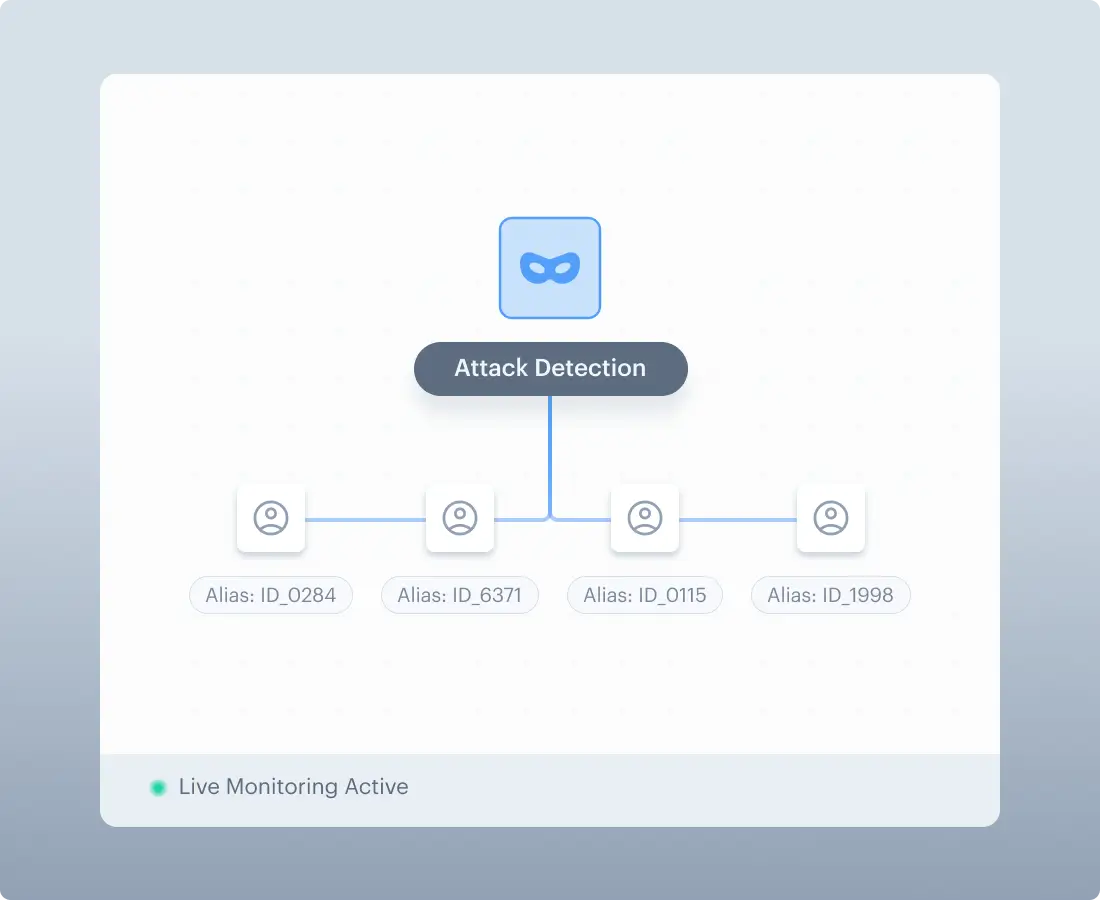
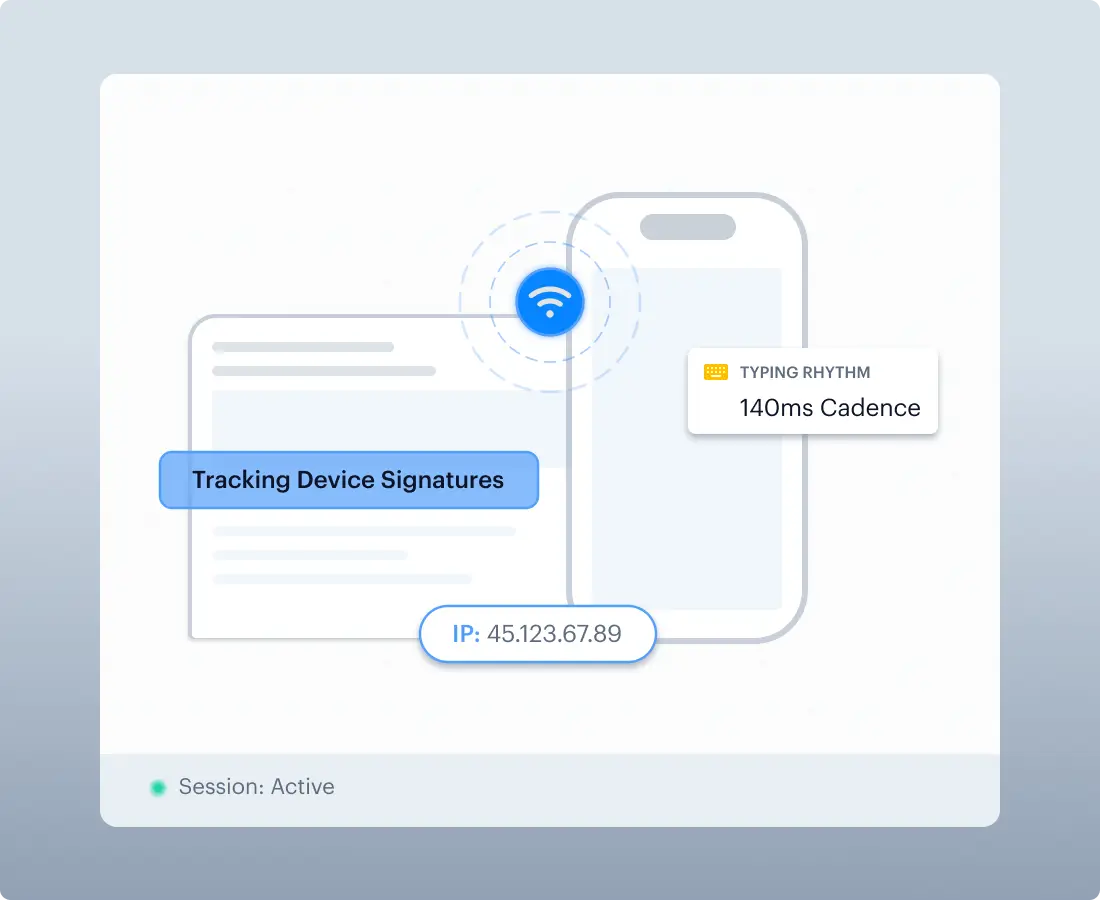
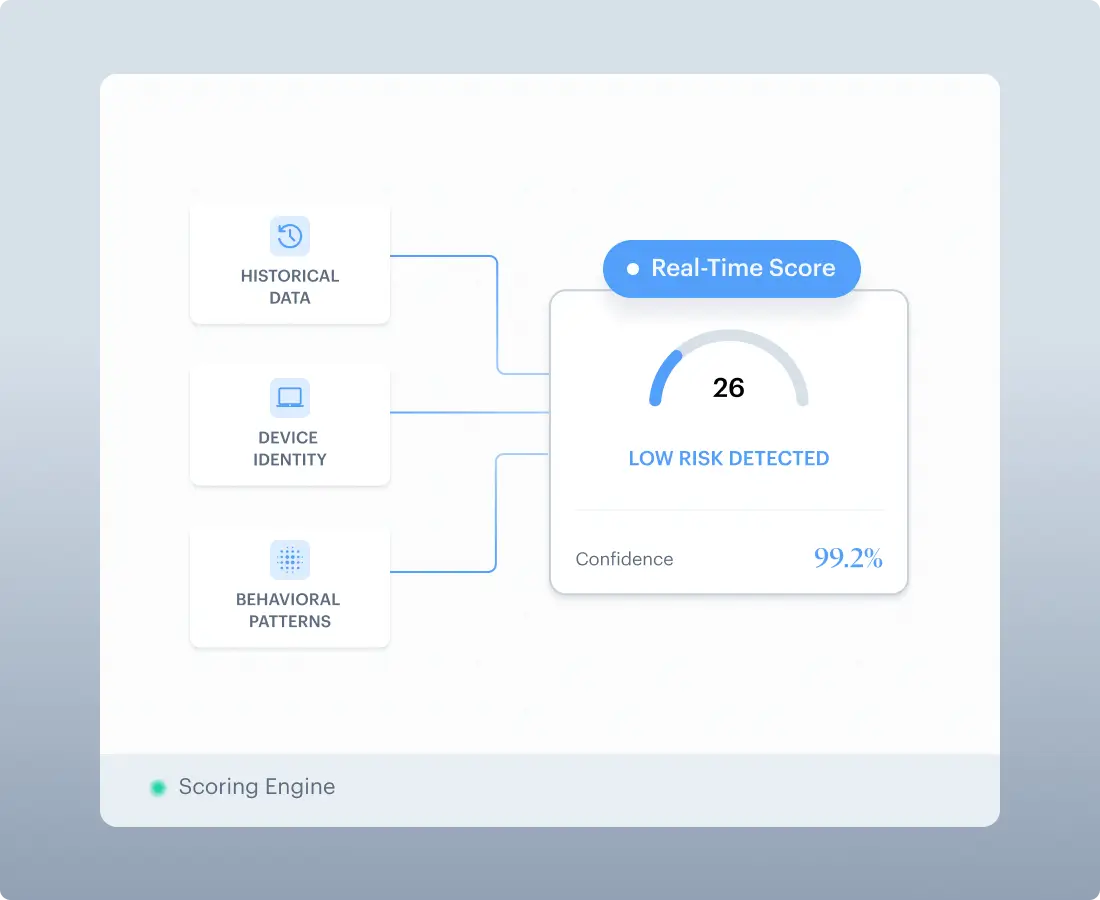

Cross-Session Fraud Intelligence
Fraud Ring Detection
Links attacks across users, devices, and sessions. Exposes
co-ordinated fraud operations that session-isolated detection misses.

Repeat Attacker Identification
Flags attackers returning with different identities through pattern correlation.

Device & Behavioral Fingerprinting
Tracks device signatures and behavioral patterns across verification attempts.

Risk Signal Aggregation
Combines cross-session, behavioral, device, and historical signals into unified fraud scoring.

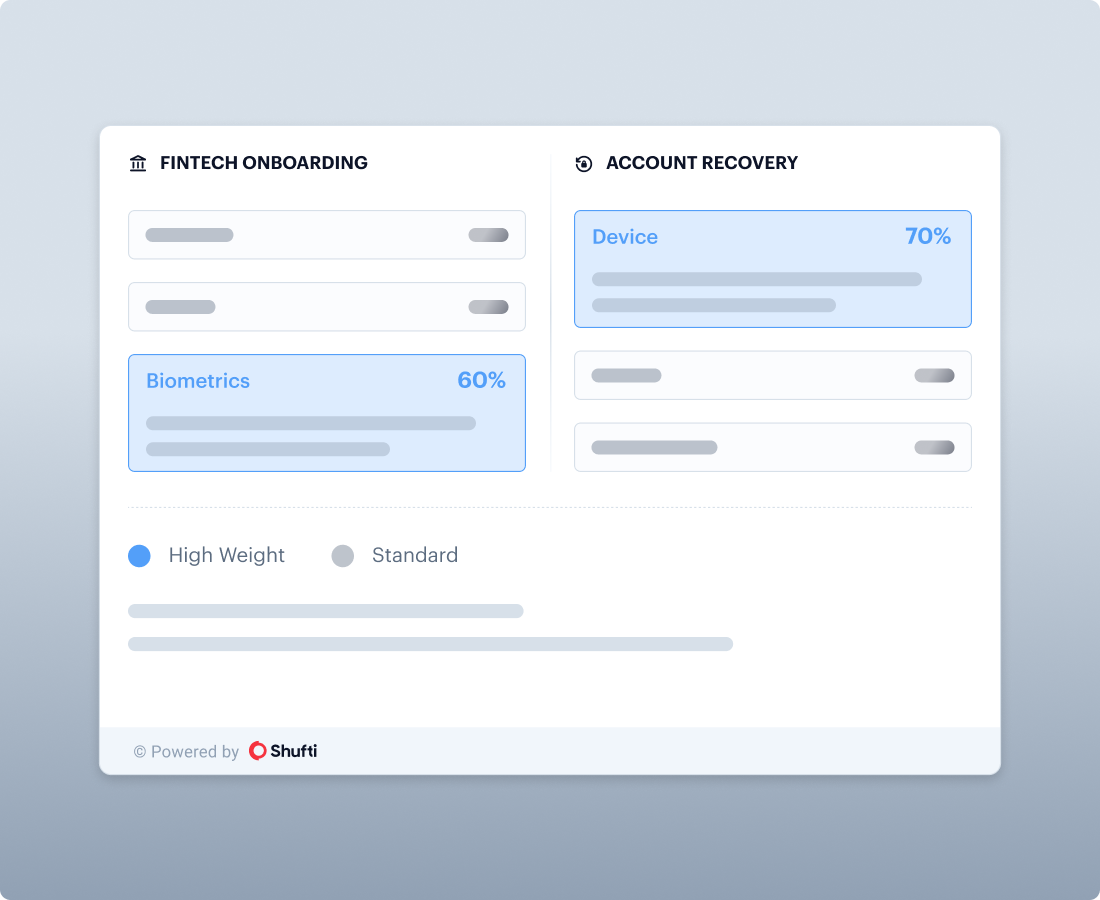
Flexible Deployment
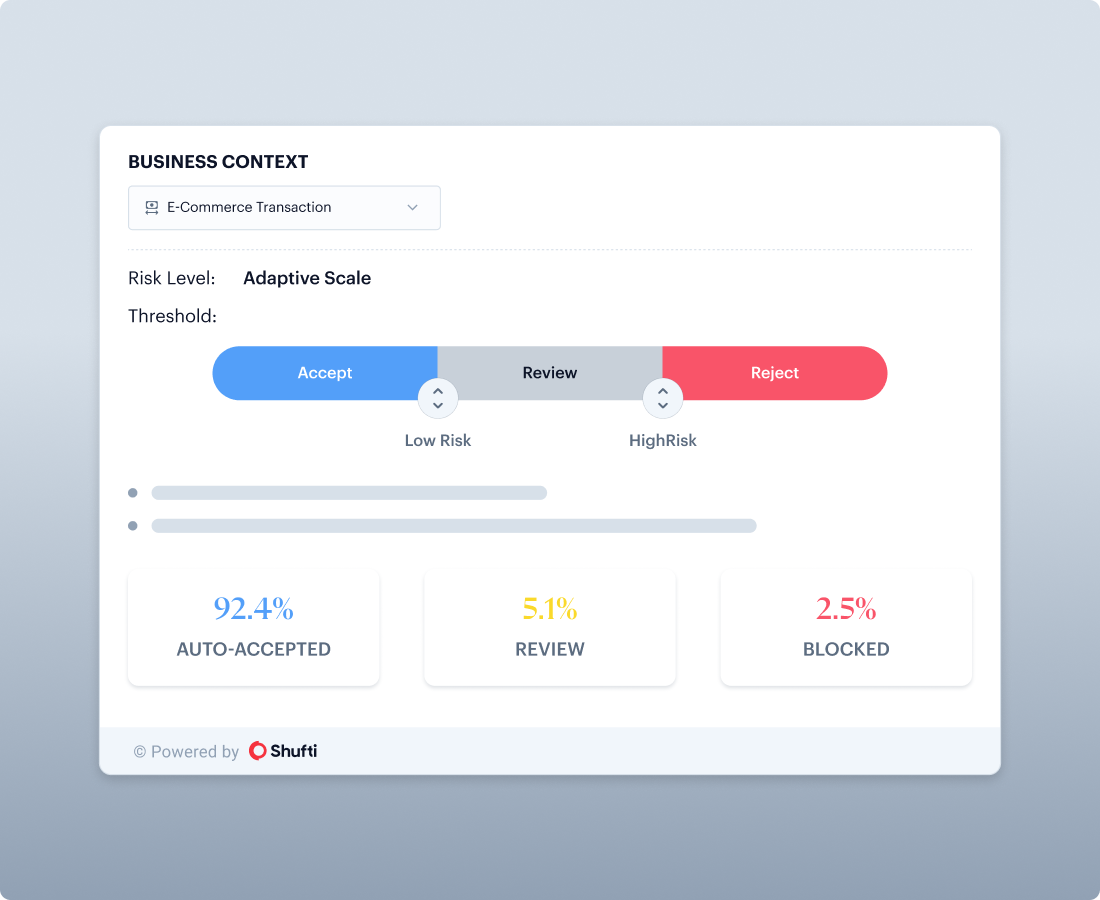
Adaptive Thresholds
Configure accept, review, and reject thresholds by scenario, onboarding versus authentication versus recovery.
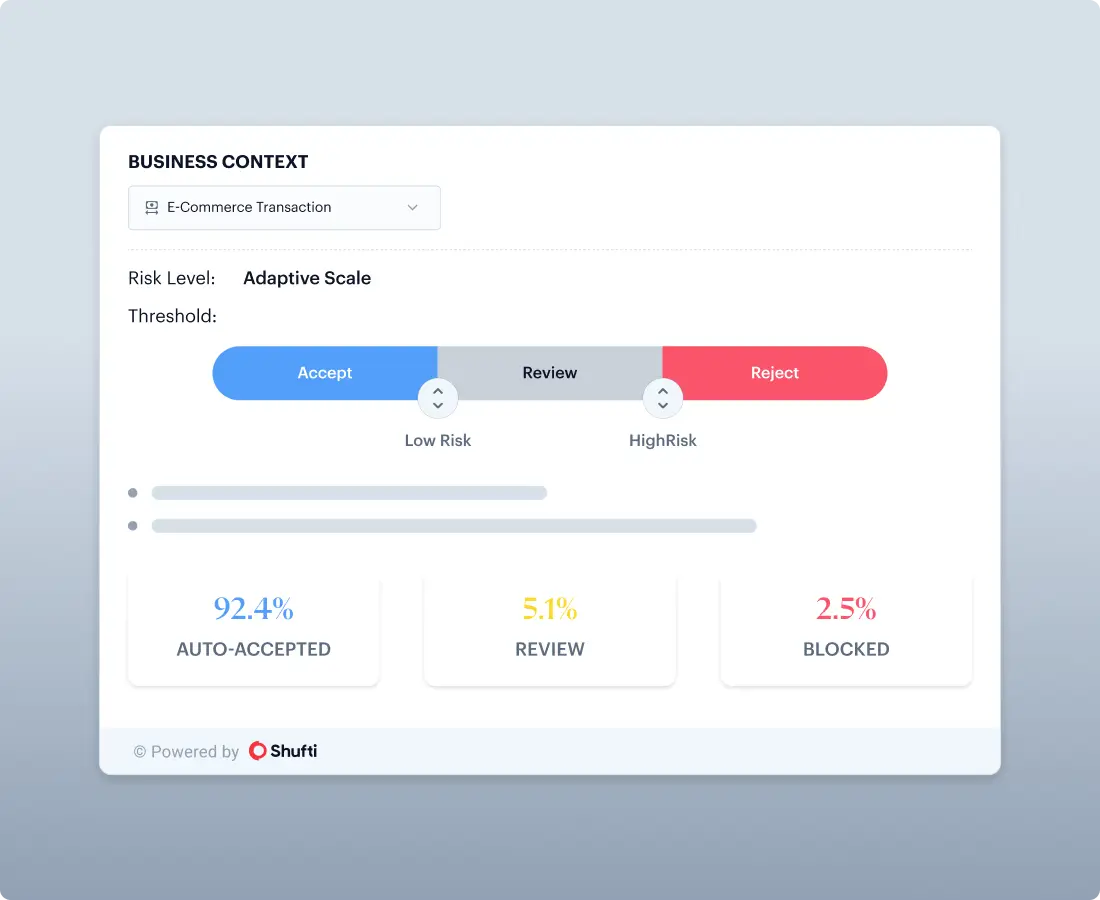
Policy Weighting
Tune which checks matter most per use case, without rebuilding flows.
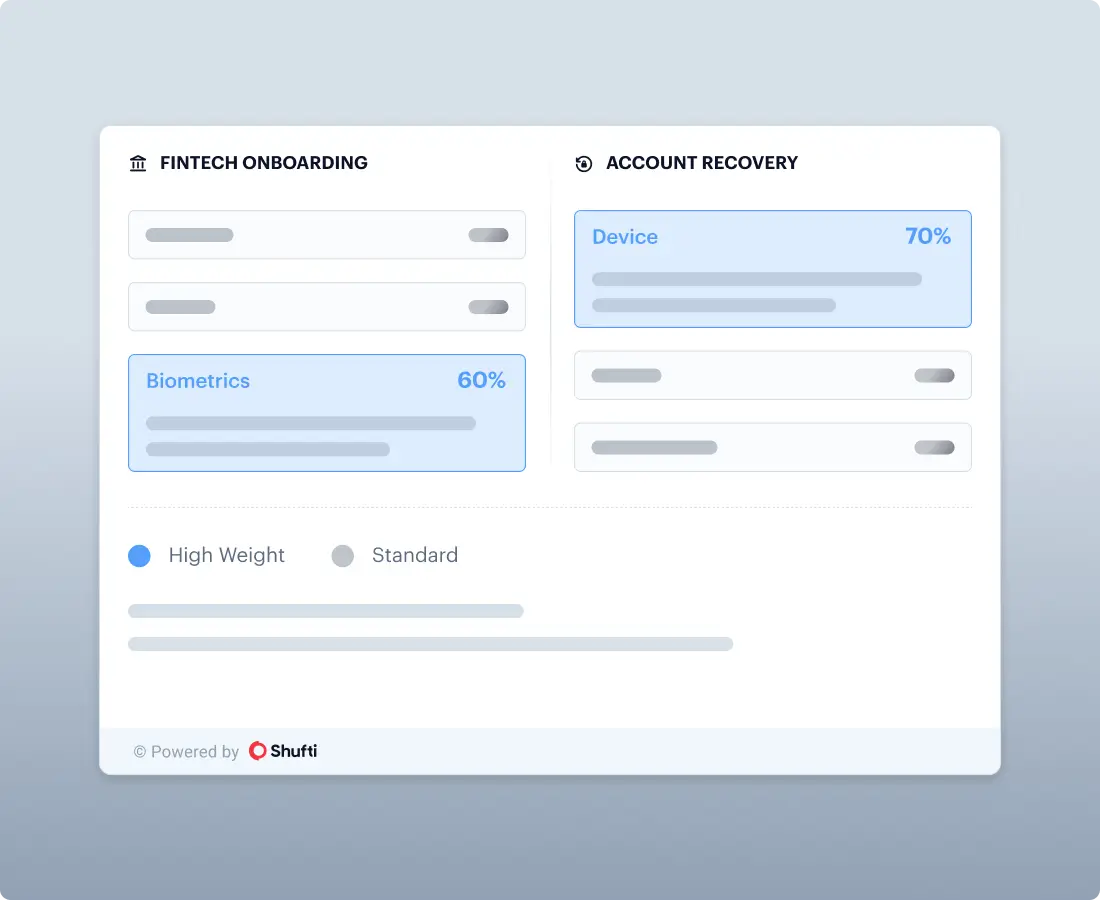
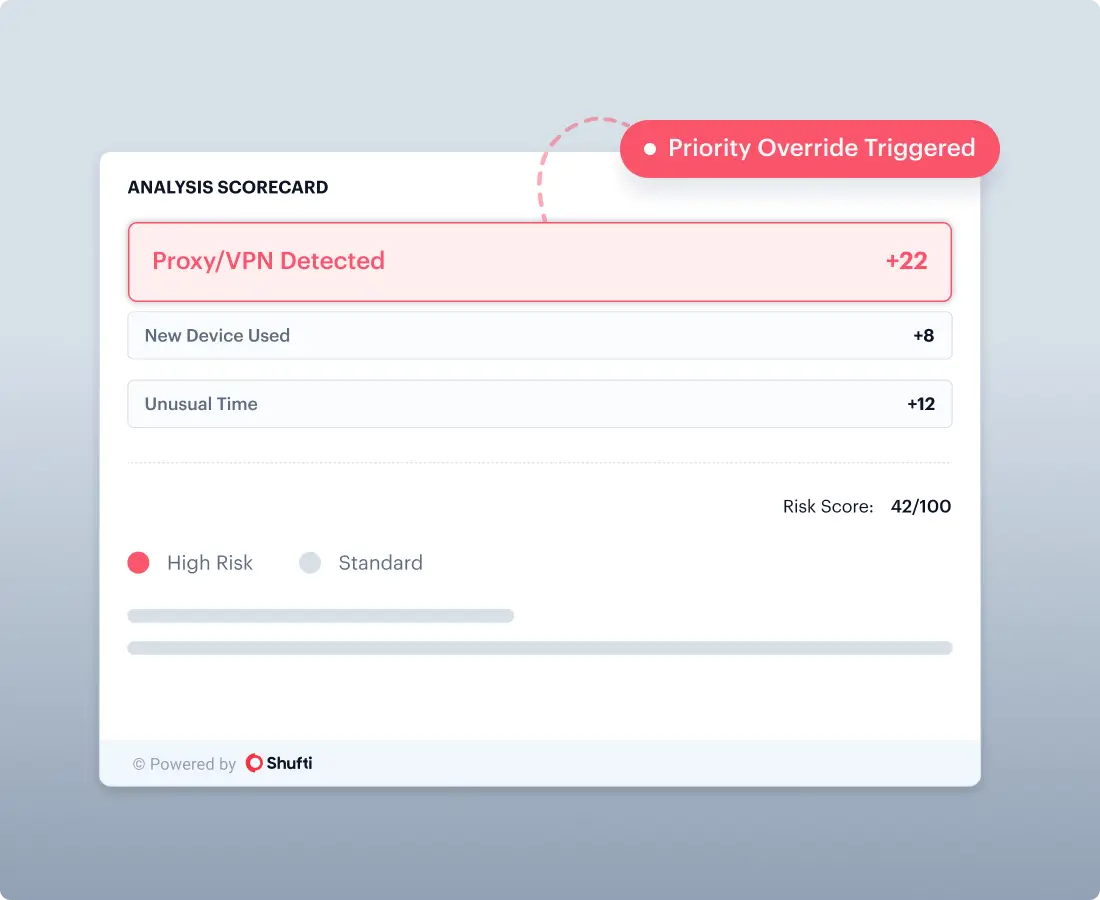
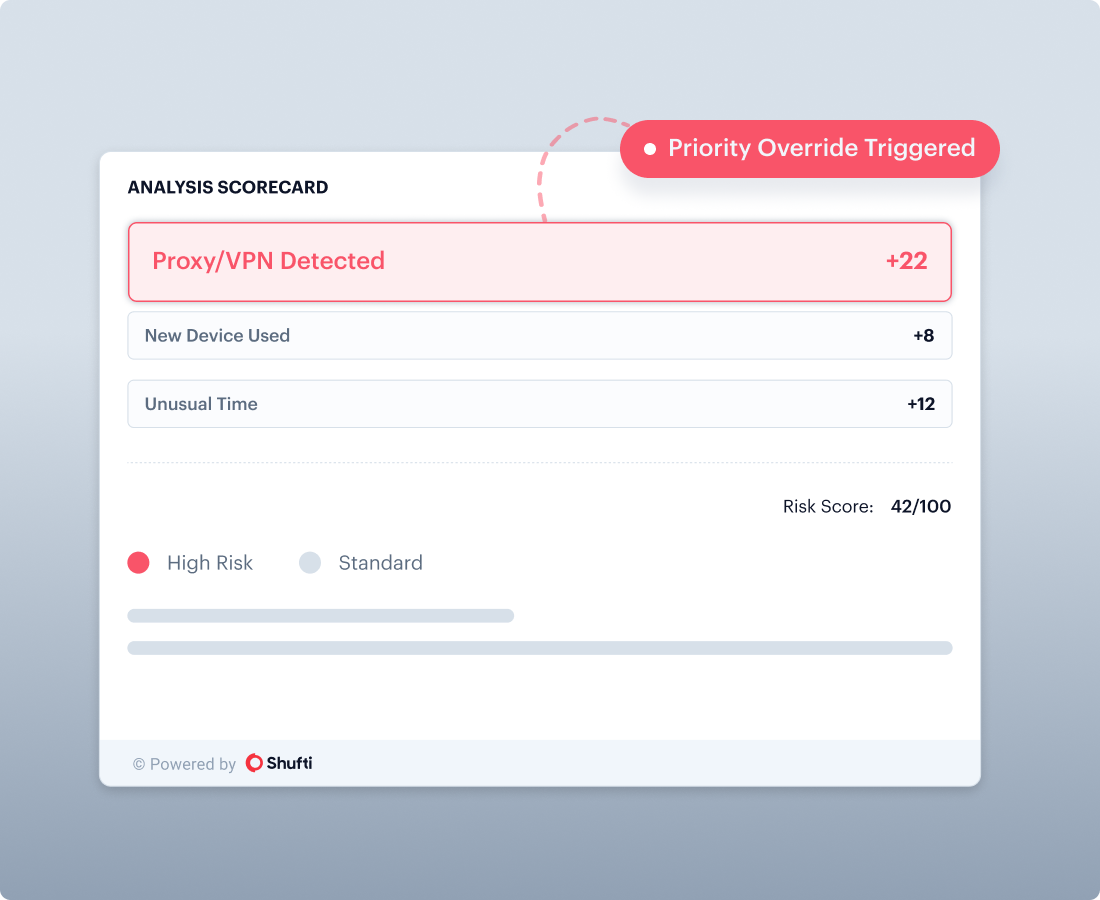
Override Rules
Allow high-risk indicators to force step-up or review based on your risk policy.
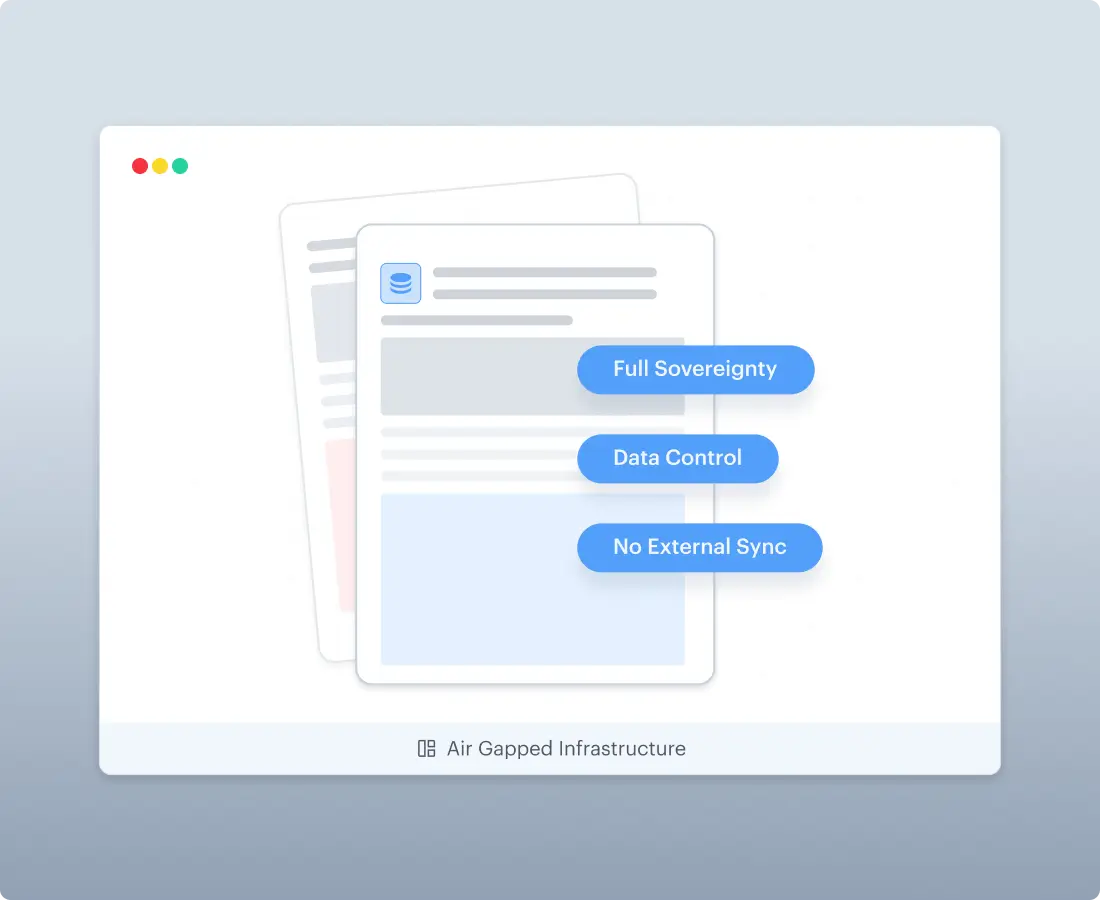
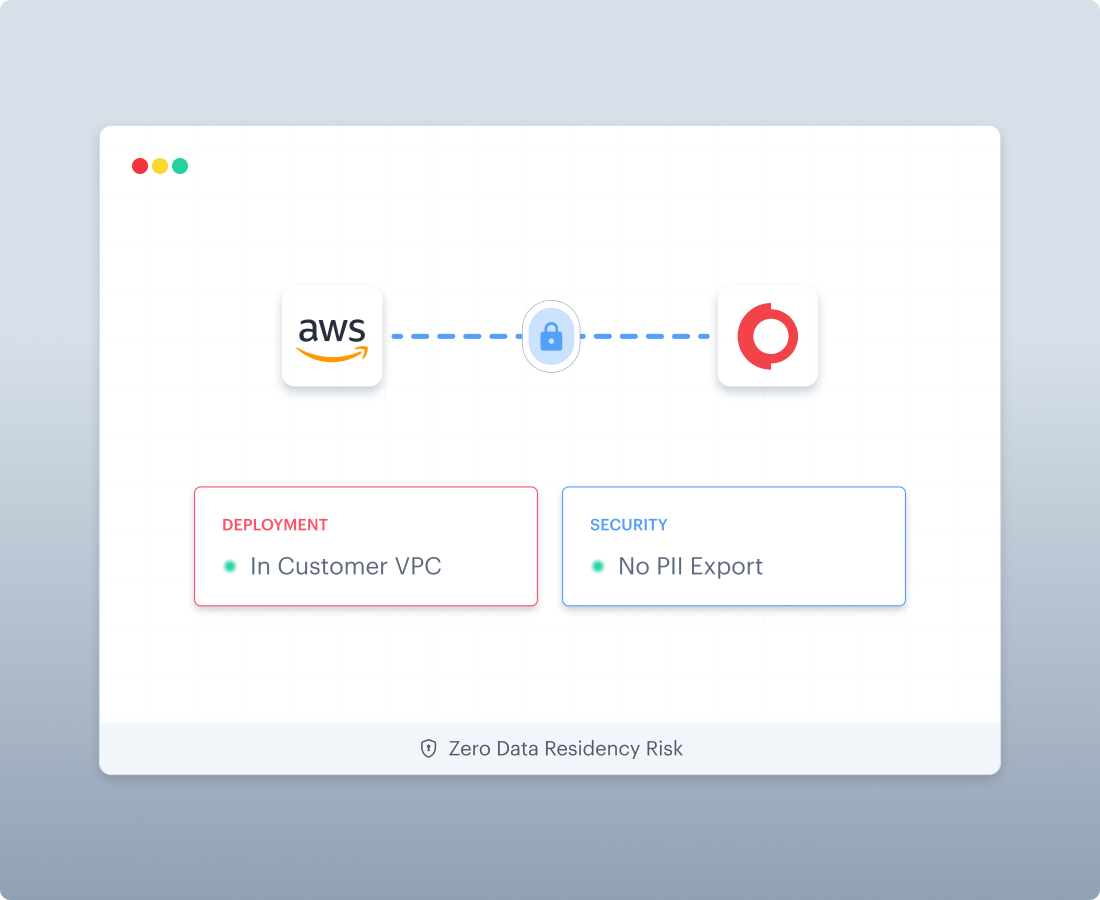
Deployment Options
Cloud, on-premise, and in-cloud deployments to support data sovereignty and operational requirements. AWS Marketplace deployment can support in-VPC processing when required by security teams.


 Explore Now
Explore Now