Geolocation Technology and its benefits for KYC Verification

KYC verification has come a long way from simply authenticating the official identity documents of end-users. The need to verify customers placed at remote locations required KYC service providers and ID verification services to adopt technologies that can easily track the geographical location – or geolocation – of an end-user even before a KYC check starts off. KYC verification has a lot to benefit from Geolocation technology as it can help KYC software to not only track the location of verifying end-user but adds an additional layer of security in fraud prevention. But first we tell you how geolocations help identity verification and can be integrated into a Know Your Customer solution, let us explain to you what is geolocation and how it works?
What is GeoLocation?
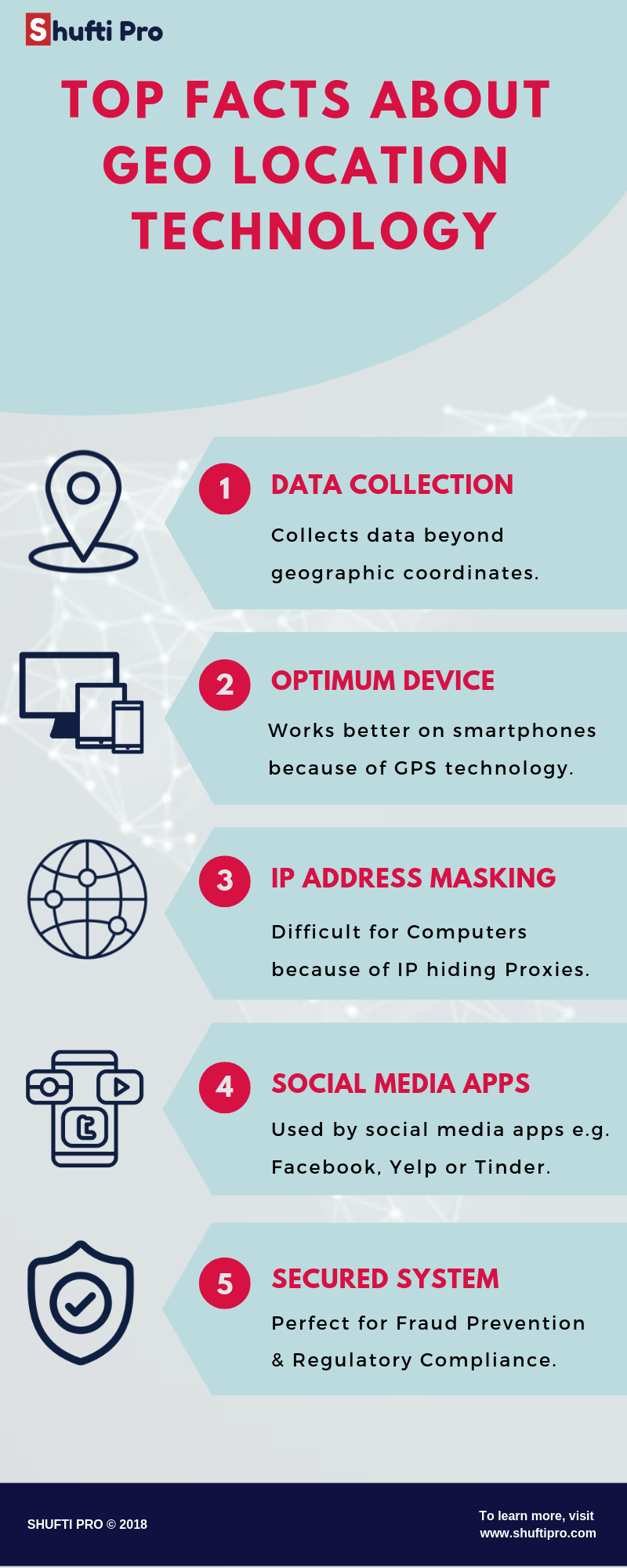
GeoLocation is the practice of finding the geographic location of an object. Most of the time a smartphone or personal computer is used to track the location of the object or person in question. Interestingly, unlike many geo-positioning systems that are mostly used to provide geographic coordinates (horizontal & vertical coordinates), the information collected by Geolocation technology is much more actionable.
Apart from geographical information, Geolocation services provide information about the country, time zone, zip code, area code, address, proxy information, and network information. Geolocation collects a variety of data to determine this information via data sources including OP address, Wi-Fi addresses, radio frequency identification, Global Positioning System and GSM/CDM cell IDs.
How Does Geolocation help in KYC?
A typical KYC provider can use geolocation technology to help its customers in providing a specific set of identity verification services, in addition to identifying that whether they belong to same country or location that they claim to. KYC compliance becomes easier and KYC solutions are easier to process because of geolocation technology. Identity theft protection gets a shot in the arm while fraud prevention becomes nearly effortless with the help of geolocation technology.
Fraud prevention via geolocation technology
Online fraud prevention can become easier if the online sellers and vendors can identify the location of the person. Even if a real person is momentarily trying to access a service portal from a new location, the system automatically detects the change of location and requires online users to verify their identity.
With ID verification and many other KYC services available at the dispense of Shufti customers – one of the most renowned KYC provider – verifying the identity of incoming users become entirely hassle-free.
KYC compliance made easy
In many online businesses and web services, it is essential that incoming user belongs to a certain location, in order to get registration. Whether it is an ICO registration process, a gambling website or even a gaming platform, compliance regulations made it necessary to not allow citizens from certain territories. Moreover, in some cases, it is also imperative for the security of a venture to not allow users from certain countries. Geolocation backed KYC software – such as Shufti – can help navigate these murky waters to avoid entrance of users from restricted countries and regions.

 Explore Now
Explore Now