How Social Security Number (SSN) Verification Works?

- 01 What Is A Social Security Number
- 02 What Is SSN Verification?
- 03 What are the Three Essential SSN Verification Methods?
- 04 Is SSN Verification A Sufficient Check for KYC by Financial Institutions?
- 05 How To Verify An SSN Online
- 06 Social Security Identity Verification for Compliance and Security
- 07 Secure Your Identity With Trusted Social Security Identity Verification
Ever wonder what truly keeps identity theft at bay in today’s digital world? It depends on matching multiple data points, including the unique identifiers, that help verify the identity of a person. In the context of the United States, it is called a Social Security Number (SSN).
In plain terms, the SSN definition is a single nine-digit government-issued number used to report wages, determine eligibility for benefits, and serve as a unique identifier during regulated identity verification.
The accuracy and legitimacy of an SSN can mean the difference between welcoming a genuine customer and facing costly fraud. If protecting your users against data theft is what matters the most, then mastering SSN verification is also indispensable for businesses.
In a world where fraud continues to evolve, SSN verification is one of the ways to keep employees safe against identity theft and help AML obligated sectors comply with KYC regulations.
What Is A Social Security Number
The Social Security number (SSN) is a nine-digit number exclusive to the United States, issued to American residents and citizens. SSN was introduced in the 1930s as part of the initial system for tracking wages and the disbursement of benefits.
Today, social security-based identity verification is used by businesses in multiple capacities. Financial institutions often use SSN verification for onboarding new customers, and citizens use it for access to healthcare and other social security benefits. Many organizations use SSNs for conducting background checks as well.
What Is SSN Verification?
The primary purpose of SSN verification is to confirm if a person’s SSN and core identifiers, like name and date of birth, match with Social Security Authority records. It is to be noted that SSN verification doesn’t always mean identity verification, but it can be a component of it.
For businesses focused on seamless and compliant onboarding, SSN verification can be used to flag inconsistencies in synthetic identity.
Accurate social security identity verification empowers organizations to authenticate new customers and prevent fraud. In highly regulated sectors, using a robust SSN verification is crucial.
The Federal Trade Commission reports a surge in identity theft, and over 80% of fraud detected in new accounts now involves synthetic identities. One way to tackle this threat of synthetic identities is by cross-referencing an SSN against various databases, including authoritative sources. Social security verification is a crucial defense pillar as it allows businesses to identify inconsistencies that serve as red flags.
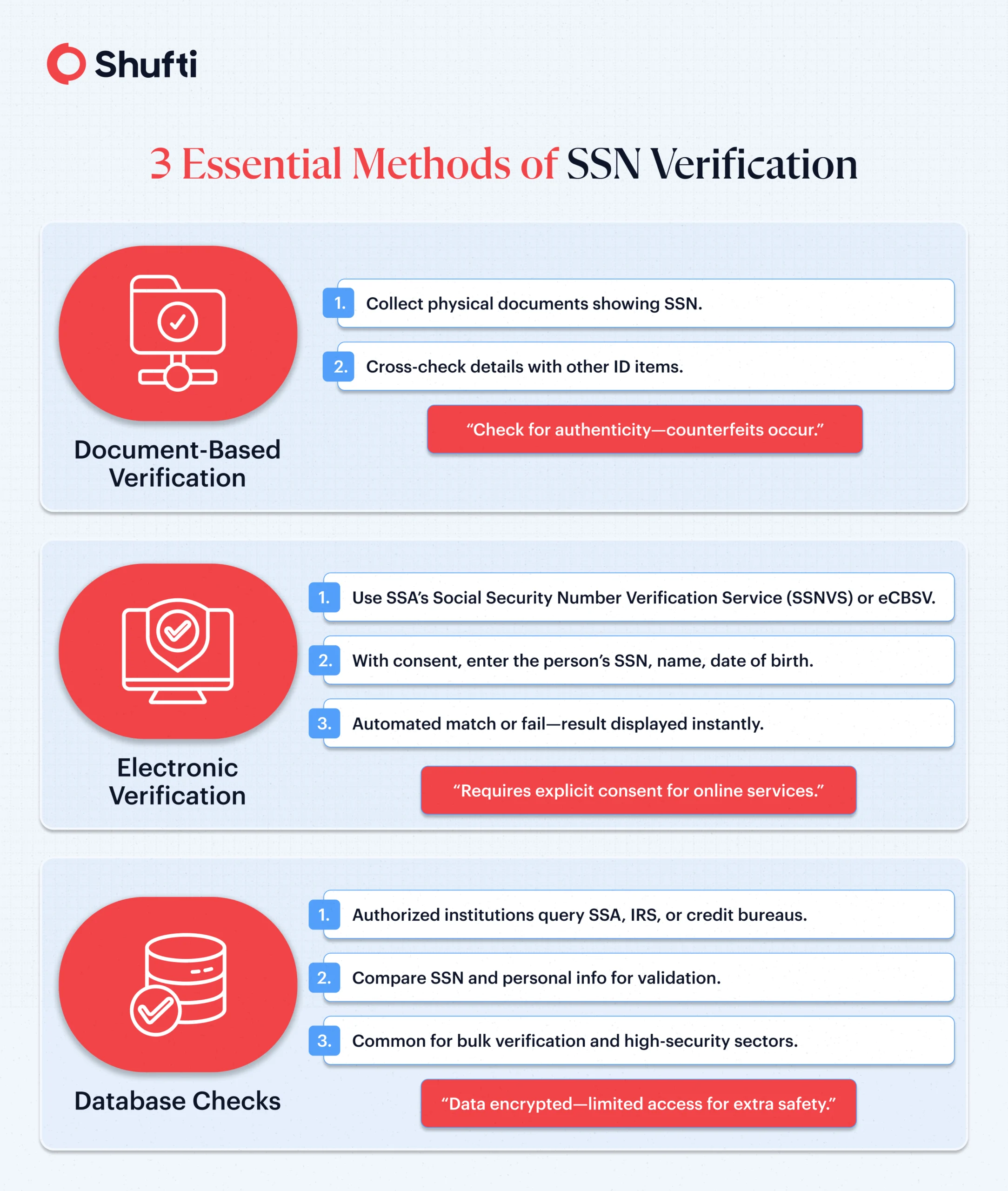
What are the Three Essential SSN Verification Methods?
While electronic verification is fast and helpful for quickly flagging inconsistencies or mismatches, it is essential to note that relying solely on this approach typically does not meet the full requirements of a robust Customer Identification Program (CIP) under U.S. regulations.
Most programs require a combination of verification methods, such as document-based review or biometrics, in addition to electronic verification, to help ensure comprehensive identity validation and compliance with anti-fraud and KYC standards.
-
Documents-Based SSN Verification
Document-based verification involves the use of various identity documents; these include the Social Security card, W-2 form, or SSA-1099 benefit statement, to verify that the SSN belongs to the same person.
Such documents are either verified solely, in some cases, in conjunction with other evidence, such as a pay stub or identity documents like a driver’s license. The choice of documents used depends on the purpose. For example, for employee background checks or for tracking of social security benefits, a pay stub from existing or previous employees can be used.
Other types, such as birth certificates, could be used in cases involving children or individuals who did not have other primary identity documents.
-
Consent-Based SSN Verification through eCBSV
Electronic verification of a user’s identity is becoming the norm in different jurisdictions. In the United States, the Social Security Administration (SSA) offers online SSN verification through systems like eCBSV (Electronic Consent-Based Social Security Number Verification).
Unlike informal tools, eCBSV requires consent and returns a simple ‘match/no-match,’ ensuring any SSN lookup by name remains compliant and purpose-bound.
eCBSV is a fee-based service; the Social Security Administration charges an annual tiered subscription fee from the permitted entities, such as banks or financial institutions. The fee depends upon the transaction volume, ranging from $5,100 for up to 10,000 requests to over $5 million for the highest tiers as of April 2025.
With the individual’s consent, an employer, bank, or other authorized entity can quickly verify whether personal details match the official SSA database. Apart from eCBSV, social security number lookup services and SSN validator tools also provide SSN verification.
-
SSN Verification through Databases
Database checks go even further. Institutions that are obliged to check or verify identities can access large, secure databases, including those provided by the SSA, Internal Revenue Service (IRS), or major credit bureaus. These permit SSN search by name, mass social security search, and advanced pattern search, which makes it more difficult to impersonate a person.
For individuals, the privacy of their credentials and their consent are two important factors during any SSN validation check. The law restricts access to a person’s sensitive information only through a written and explicit consent, ensuring its protection at the highest level.
Businesses and institutions relying on SSN verification need to execute it responsibly through trusted and encrypted channels accessed only for legitimate business purposes. This secures the identity holder’s data as well as helps organizations fulfill their regulatory obligation and nurture trust of those they serve.
Is SSN Verification A Sufficient Check for KYC by Financial Institutions?
SSN verification is effective, yet not infallible. Numbers can be stolen, forged, or abused, and the threat is only increasing as cybercriminals become more creative in their attacks.
Recent reports from the Federal Trade Commission (FTC) highlight that over 1.1 million incidents of identity theft were reported in 2024 alone, with Social Security numbers specifically flagged as a vulnerable target in data breaches and employment scams.
Even legitimate SSNs sometimes end up for sale on the dark web, matched with fake names or addresses, making robust, multi-step identity verification more important than ever.
SSN verification is most commonly used in sectors where a unique identifier is required. This includes regulated industries like insurance, banks, and other financial institutions. However, FinCEN guidelines for customer identification programs (CIPs) under AML compliance require more than just an SSN check.
To satisfy these requirements, firms need to adopt verification methods according to the level of risk they face in their business. These methods include verification of identity documents, followed by biometric authentication and a unique identifier (such as a Social Security Number) to vet each customer and defend against financial crime thoroughly. This approach, with different levels of verification anchored by the SSN, is better equipped to stand against today’s prevalent fraud tactics.
How To Verify An SSN Online
Online verification of SSN is quite a simple process; however, it depends on the core purpose of the business. SSN verification by an employer for wage reporting may be different from SSN verification for the sake of customer identity verification by a bank.
- Employers use Social Security’s Business Services Online to confirm that an employee’s name and SSN match, with date of birth being optional.
- Type in the name of the individual, date of birth, and SSN. The system will give a match of “yes” or “no”, indicating a match of the details.
- For bulk checks, employers (or their authorized submitters) can use SSNVS to upload batch files of up to 250,000 name/SSN records for W-2 wage reporting, speeding new-hire onboarding, and reducing manual errors.
Obtaining clear permission, registering all the checks, and employing authoritative systems in the name of social security checks are all part of the procedure to be followed.
Businesses using the various documents to verify the SSN must ensure the security of customers’ records if they are legally bound to keep them.
For this, they should never share SSNs via insecure means (like email, SMS, or paper), and strictly limit access to documents containing SSNs. A secure practice is that only authorized personnel with a legitimate business need should be able to view or handle these files.
This access control should apply to both digital records (stored in secure, encrypted databases) and physical documents (such as Social Security cards, W-2 forms, or onboarding paperwork) to help protect sensitive data from misuse or exposure.
Social Security Identity Verification for Compliance and Security
For AML obligated businesses, such as banks, financial services, insurance providers, and other regulated entities, compliance is not merely a box to be ticked, but a legal requirement.
Customer verification for compliance with AML and Know Your Customer regulations requires a robust identity verification process, which includes verifying the identity documents, biometric verification, and verification through a unique identifier.
According to guidance issued by the Financial Crimes Enforcement Network (FinCEN), institutions should collect and verify a unique identifier for each customer, which in the context of the United States is the Social Security Number, as part of their Customer Identification Program (CIP) for AML compliance.
Businesses should:
- Use secure storage and transmission policies for sensitive customer details
- Maintain up-to-date consent records, especially with electronic systems
- Follow due diligence — such as ongoing screening against fraud databases — for every identity verification step
Secure Your Identity With Trusted Social Security Identity Verification
For financial institutions and other regulated businesses, confirming Social Security details is essential for fraud prevention and compliance.
With Shufti, businesses first verify the person with a United States driver’s license, face match, and liveness. Then businesses corroborate SSN ownership using evidence such as an SSN card, W2, or SSA 1099, with the last four options to reduce exposure.
Shufti compares names and dates of birth a sources, flags inconsistencies, and, where permissible cross-checks identity attributes against authorized private databases under a clear permissible purpose.
Businesses gain an auditable trail for reviews. This risk-based approach to SSN verification and Social Security identity verification supports faster onboarding, early detection of synthetic identities, and strong KYC and AML compliance without slowing operations. To see how it works, request a demo!
Prepared to increase identity security? Explore actionable guides and verification best practices in Shufti’s customer due diligence resources — designed for readers who want practical solutions, not just theory.
Frequently Asked Questions
What does SSN mean?
SSN: Social Security Number is a nine-digit identification number used in the U.S.
How to check if my SSN is valid?
The official SSA verification services can be checked by checking your Social Security card and your important documents, such as W-2 forms.
What is to be done when your SSN is on the dark web?
Action: Report the SSA, place the account on credit watch, and review all financial accounts to investigate suspicious activity. Consider monitoring your credit and be aware of signs of identity theft.
How do you know whether a Social Security Number is counterfeit?
A bogus SSN can be different in official records, with an unknown date of issue or number, or can result in an error on verification. Verify information using official documents and trusted verification systems.

 Explore Now
Explore Now













