The Definitive Guide to Anti-Money Laundering & Countering of Terrorist Financing

In this modern globalized era, money launderers, terrorist financiers and other criminal elements came up with a slew of resourceful ways to accomplish their malicious desires. It is a common practice of these groups to misuse the services of legitimate businesses such as banks and other Financial Institutions (FIs) to convert ill-gotten gains into ‘good money’. Whereas, to counter such criminal activities, FIs rely on procedures and systems that aim at acquiring customer knowledge.
One of the major issues is that most legitimate entities turn out not to be compliant with the AML (Anti-Money Laundering) regulations. This increases the probability of bad actors to finance terrorists and drug dealers. Any legal entity that knowingly or unknowingly became part of money laundering or terrorist financing will suffer from enormous regulatory penalties. Therefore, it is crucially important for FIs to establish a strong internal system of controls that, even when criminals are using the best effort and abilities to elude the rules. It allows them to identify fraudulent entities and unusual money flows.
What is Money Laundering?
Money laundering is a process wherein criminals attempt to hide and obscure the ownership and origin of their proceeds of criminal activities whereby avoiding prosecution, confiscation, and conviction of the criminal funds.
When an entity makes substantial profits, it finds ways to use or save funds without moving the attention of inspectors on underlying suspicious activity or on criminal entities that are doing so. In money laundering, criminals disguise their sources of money, change the form or transfer it to a place that seems less likely to grab attention. Embezzle funds are converted into good money to ‘enjoy it’.
Palermo Convention or United Nations Conventions Against Transactional Organized Crime states money-laundering as:
“The conversion or transfer of property intentionally knowing that it is a proceed of crime, to conceal the illicit origin of money or helping an individual who is involved in predicate offence and wants to evade legal consequences of his action.”
“The concealment of the true source, nature, location, movement, ownership, property or disposition, intended that it a proceed of crime.”
“The acquisition, ownership or use of property, which at the time of receipt was known that it is a proceed of crime.”
Financial Action Task Force (FATF) is an inter-governmental body established in 1988 by a group of seven industrialized nations to combat money laundering. FATF cleared the notion that money laundering only takes place with cash transactions. Actually, it’s not the only case. Money laundering can be performed by any medium virtually, could be a financial institution or any business.
Sources of Dirty Money
In simple words, money laundering means “the conversion of dirty money into good money.”
Following are some of the sources of dirty money:
- Drugs and arms Trafficking
- Criminal Offences
- Gambling
- Smuggling
- Bribe
- Online fraud
- Tax evasion
- Kidnapping and many more…
Methods and Stages of Money Laundering
Money laundering involves three stages; placement, layering, and integration.
-
Placement
This process is the movement of illicit funds from its source. At that time, the origin is manipulated or concealed. This process is followed by money circulation through FIs, shops, casinos, legal sector, or other businesses (both abroad and local). In simple words, in this phase, illegal funds get introduced into the financial system.
The process of placement includes many other methods:
Currency Smuggling: The physical movement of currency out of the country.
Bank Complicity: When FIs are involved with criminal entities such as drug dealers or organized criminal groups. This makes money laundering an easy process. Lack of AML procedures and checks also pave ways for money launderers.
Currency Exchanges: Foreign currency exchange service providers open ways for money launderers for seamless currency movements.
Securities Brokers: The money laundering process can be facilitated by brokers by structuring enormous funds in such a way that it conceals the original source of illicit money.
The blending of Funds: A small number of illicit funds are blended with a huge deposit of legal funds.
Asset Purchase: Assets are purchased with dirty money. This process is the most common method to hide dirty money. The real estate sector is misused by money launderers and real estate agents knowingly or unknowingly facilitate bad actors.
-
Layering
This process involves the transfer of funds to several accounts or FIs’ accounts to further separate the original money source. This makes complex layers of transactions that help conceal the source and ownership of illegal funds. Hence, makes it difficult for law enforcement agencies to track the money flow.
The methods of layering include;
Cash Conversion into Monetary Instruments: After the successful placement of money into FIs or banks, proceeds are transformed into monetary instruments. In this, the banker’s money orders and drafts are involved. Material assets are bought with this cash and sold locally or abroad. In this way, assets tracking becomes more difficult to trace.
-
Integration
In this process, laundered money is moved into the economy through the banking system. Such money appears just like business earned money. In the integration process, laundered funds are detected and identified through informants.
Integration methods include;
Property Dealing: Among criminals, property sale to hide dirty money is a common practice. For instance, criminal groups buy properties using shell companies.
Front Companies and False Loans: Front companies, incorporated with secrecy laws in the countries are used by money launderers that lend them laundered proceeds that appear to be legitimate.
Foreign Bank Complicity: Money laundering is conducted using foreign banks. It gets hard for law enforcement agencies to point them out due to their sophisticated systems.
False Invoices: Import/export companies create false invoices and have proven to be an effective way of hiding illicit money. This method includes the overvaluation of products to justify the funds.
What is Terrorist Financing?
The processing of funds to facilitate criminal activity. It involves financial support to non-state actors or terrorists.
This is today one of the major threats we are facing. Who knows, if our services are used for terrorist financing? Even, sometimes the legally earned money is also transferred for the financing of terrorism.
For terrorists, no matter how small the money amount is, it is a lifeblood for them.
Just like money laundering, terrorist financing is a predicate offence. Early detection and immediate counter steps are the only ways to combat it.
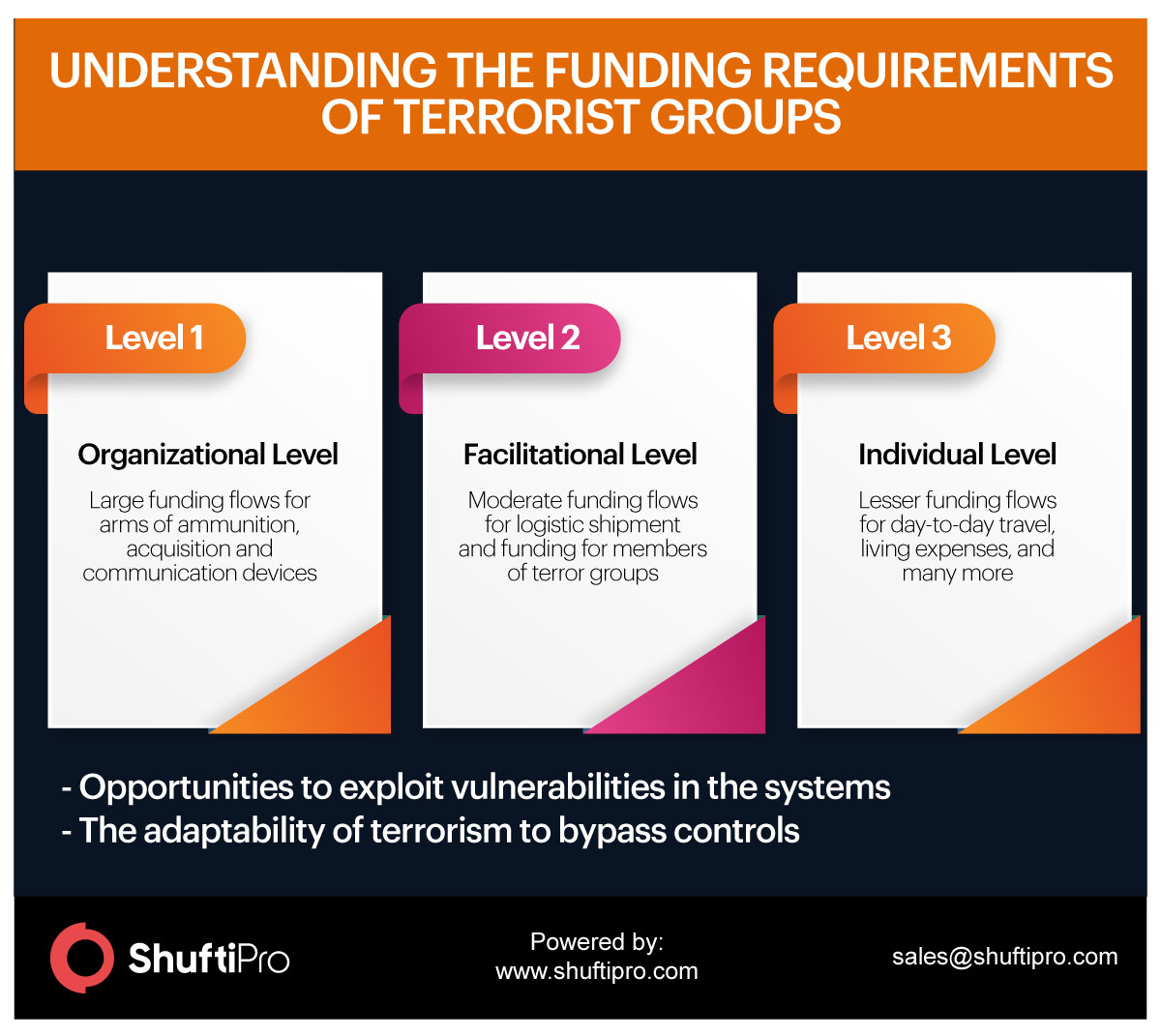
Concerns of Countries and Governments around the World
United Kingdom
MLR-2017, the Money Laundering, Terrorist Financing and Transfer of Funds (Information on the Payer) regulations came into force in the UK on June 26, 2017. The new regulation of the UK is tightening the reins on money laundering in resourceful ways.
To combat money laundering, UK regulations include identity verification of customers before providing services to them. AML compliance is mandatory when it comes to screen the customers against Politically Exposed Persons (PEPs) list, sanction lists, the high-risk customers’ records, and updated criminal databases. In addition to this, employee training is also declared mandatory. Previously, regulations covered only casinos holders which now extend to all gambling providers.
China
Anti-money Laundering (AML) regulations in China primarily focus on KYC (Know Your Customer) verification of customers through identity verification protocols. China’s government has issued AML/CFT regulations on online financial institutions. FATF report for the People’s Republic of China states that China has a strong understanding of money laundering and terrorist financing risks.
In AML/CFT regulations of China, legitimate entities are required to verify their customers with identity proof (such as government-issued ID cards). In addition to this, regular identity checks are declared important in case of a change in records of beneficiaries or regulations. In the case of any suspicious transactions crossing the minimum transaction threshold, it should be reported immediately to the relevant authority. China is taking stringent measures in the AML compliance program to combat money laundering and terrorist financing criminal activities.
The United States of America
In the USA, Bank Secrecy Act (BSA) is residing. With several amendments, this act is quite detailed and covers broad perspectives of money laundering risks of financial institutions. BSA was designed to identify the source, volume, and movement of laundered money and monetary instruments. According to BSA, banks and other financial institutions are supposed to report transactions over $10,000 through currency transaction reports.
Not only this, CDD processes are mandatory for businesses operating in the USA. AML screening of customers against several criminal databases are updated records is necessary to comply with AML regulations. Additional federal laws are passed to strengthen the rules and regulations under BSA. Anti-money laundering programs in the USA come up with changes and scope will be extending with time.
Canada
FINTRAC, Financial Transactions and Reports Analysis Centre of Canada has recently released a final version of rules and regulations that depict amendments in the regulations to Proceeds of Crime (Money Laundering) and Terrorist Financing Act (PCMLTFA). The changes in Canada’s regulations ensure the compliance procedures and policies to be significantly stringent.
According to these regulations, the financial services industry needs to be dynamic in nature for the reduction of money laundering and terrorist financing activities. Virtual currency services and digital payment methods have opened ways for fraudsters to transfer their embezzled funds across the world. Moreover, regulations extend to prepaid card issuers, virtual currency providers and foreign Money Services Businesses (MSBs).
Risks for Banks and Financial Institutions
Money laundering and terrorist financing affect the overall economy of the world. As regulated entities such as banks and financial institutions are primary sources that deal with the money in a country. These entities are opportunities for fraudsters through which they can transfer ill-gotten gains in different corners of the world. There are several risks associated with the maintenance and supervision of banking relationships to which FIs and employees should be aware of. The interconnection of banks should be secure and well-organized to track the unusual flow of transactions. Otherwise, regulatory scrutiny can subject hefty penalties which include monetary fines, imprisonments, business abandonment temporarily or permanently and assets freezing.
What are KYC and KYB?
Know Your Customer, KYC is a process of identity verification of the customers. It is part of Customer Due Diligence (CDD). To combat high-risk customers, identity verification plays an important role. KYC is the term most commonly used in banks and financial institutions for customer verification. Now, it is needed for almost all industries because of the extended scope of fraudulent tricks and region.
Also, to comply with the obligations of global and local regulatory authorities, businesses need to verify their onboarding customers. To verify the credibility of customers, the KYC verification process makes sure that the person is actually who he says he is. Not only customers, but the scope of KYC extends to agents, businesses, corporate entities, and third-party verification. This is what we call ‘Know Your Business’ or KYB.
KYB involves the verification of businesses your company is dealing with. This is important to verify that your business operations are running in association with honest and registered entities. To avoid regulatory fines, verification of Ultimate Beneficial Owners (UBOs) is declared mandatory. AML regulations of FATF have explicitly stated UBO screening importance for businesses to combat money laundering and terrorist financing.
What is EDD?
Enhanced Due Diligence (EDD) includes additional information of customers as compared to the one collected during the CDD process. To combat the risks of high-risk customers in an organization, thorough screening is performed. In-depth verification of customers is conducted by verifying their identity, not only by collecting personal but also financial information. Following is the EDD information that is collected at verification time:
- Business/ occupation
- Financial status
- Income
- Location
- Private/corresponding baking information
- Continuous transaction monitoring, etc.
Enhanced Due Diligence Factors
High-risk Customer Factors
- Verification of customers if they are foreigners or non-residents
- Personal vehicle information of legal identities
- Verification of customers if their relatives or family members are in the list of PEPs
- Businesses that are cash-intensive
- Risk assessment of company against AML policies and parameters
Geography Risk Factors
- Countries that lack AML/CFT practices and are prone to money laundering and terrorist financing.
- Countries that lie in sanctions lists or have high criminal records
- Countries that are blacklisted for facilitating criminal activities
- Countries that do not lie under the hood of FATF members, etc.
Importance of Watchlists and PEPs
Bad actors are spreading all around the world. Your business that is providing services across the globe should be well-aware of the policies and regulations under which businesses operate. Similarly, your businesses should know high-risk entities of friend countries. Updated records of criminals, money launderers, terrorist financiers, online fraudsters and hackers, and several other watchlists should be maintained issued by law enforcement agencies, to verify each onboarding customer and secure the organization.
In addition to this, identities should be verified against the list of PEPs and their relatives to make sure that no fraudulent identity is facilitated through your legitimate businesses. In case of any discrepancy, businesses can be subjected to inevitable heavy regulatory fines. Hence, it is a regulatory requirement as well as a security concern for the protection of business from malicious entities in the financial system.
Reporting Suspicious Transactions
In a financial system, any suspicious transactions should not be ignored. To prevent money laundering and terrorist financing activities, on an immediate basis, transactions should be reported. Under the requirements of regulatory authorities and anti-money laundering laws, reporting entities are supposed to submit Suspicious Transaction Reports (STRs). It should be reported regardless of the number of fraudulent transactions. A suspicious transaction is:
- That appears unusual
- Appears illegal
- Transaction performed above the specified threshold
- Frequent transactions from one identity
- With no clear economic purpose
- Shows indication of money laundering or terrorist financing
Discussed in the AMLA section, failure in reporting an STR is an offence which can be subjected to a regulatory fine.
Indications of Money Laundering
The features below are recorded in the money laundering case studies that came onto the surface after investigations:

Conclusion
Anti-money laundering and countering or terrorist financing is the responsibility of every business and employee of a country. Strict regulatory requirements came into force as a result of its adverse effects od money laundering and terrorism financing on the global economy. Fraudsters that are violating the legitimacy of financial institutions should be tackled by all means. This very first step is the scrutinization of organizations against AML policies and procedures. The government can impose heavy criminal and civil penalties as a result of violations of regulatory obligations.
Before the law, ignorance is not even an excuse.

 Explore Now
Explore Now













