5 types of identity theft fraud and How businesses can prevent it?

Online identity theft has the fastest growing crime rate in the world. According to a report, only in America, more than 12 million Americans become the victim of identity fraud every year.
In this cyber focused 21st century, cool digital products and the internet opens a world of easy access to information, entertainment, knowledge and other services. But this cyber gateway also opens a possibility for personal information to fall in the wrong hands and anyone could become a victim of online identity theft. Even a simple looking interactive social bot could become a cause for leaking information to the third parties.
Cybercriminals particularly steal information and use it for malicious purposes such as getting access to bank accounts, credit cards and making online transactions on someone’s behalf. In short, identity theft may cause tremendous damage costing thousands of dollars and may take several months to resolve.
The worst consequences of identity theft includes causing severe reputation loss and damaging credit scores. In this article, we’ll shed light on what identity theft is and how businesses can help prevent losses due to online identity theft.
What is online identity theft?
Online identity theft is a serious crime and occurs when fraudsters steal another person’s personally identifiable information (PII) using malicious methods. PII includes someone’s identity or credit/debit card details. This information is then used for personal gains, often by making online purchases or selling information to the third parties.”
Where the old method of identity theft includes fraudsters going through trash cans looking for information or old bank statements, modern identity theft happens online.
Cybercriminals use various methods to access businesses or websites databases or infect an individual’s device to obtain sensitive information. There are five common types of identity theft, namely;
Criminal identity theft
This happens when a criminal pretends to be someone else in order to hide their personal information. By doing this, criminals try to avoid prosecution and hide prior warrants and conviction records.
Financial identity theft
Financial identity theft happens when criminals obtain someone’s financial information in order to obtain money, products or other financial benefits. Another threat from financial identity theft includes money laundering. Criminals illegally obtain personal information and use it to create accounts which are then used to launder money.
Typically, the purpose of stealing someone’s financial information is to conduct financial crimes online. Financial identity theft is the most common type of identity fraud.
Medical identity theft
Medical identity theft happens when a perpetrator pretends to be someone else in order to get health benefits, free medical care or getting restricted medicines. This is one of the most critical forms of identity fraud and probably the hardest one to find out. WHO finds medical identity theft to be a dangerous crime stating it as “The information crime that can kill you.”
Minor identity theft
Child identity theft represents a situation where fraudsters steal children’s identity information for numerous personal gains. According to a study conducted in 2017, out of all the reported breaches, 39% of the fraud victims were minors in comparison with 19% adult victims.
Most commonly, a minor’s personal information is used to get loans and apply for residence. In most of the cases, a minor’s identity is used by someone close to the minors.
High-tech identity theft
With the advent of technology, we enjoy a lot of facilities, however, on the other hand, criminals use technology to get access to personal information and use it for malicious purposes. High-tech identity theft has become one of the growing problems.
This type of identity fraud is most commonly used by hackers who install malicious software into computer devices to get access to public records and personal information.
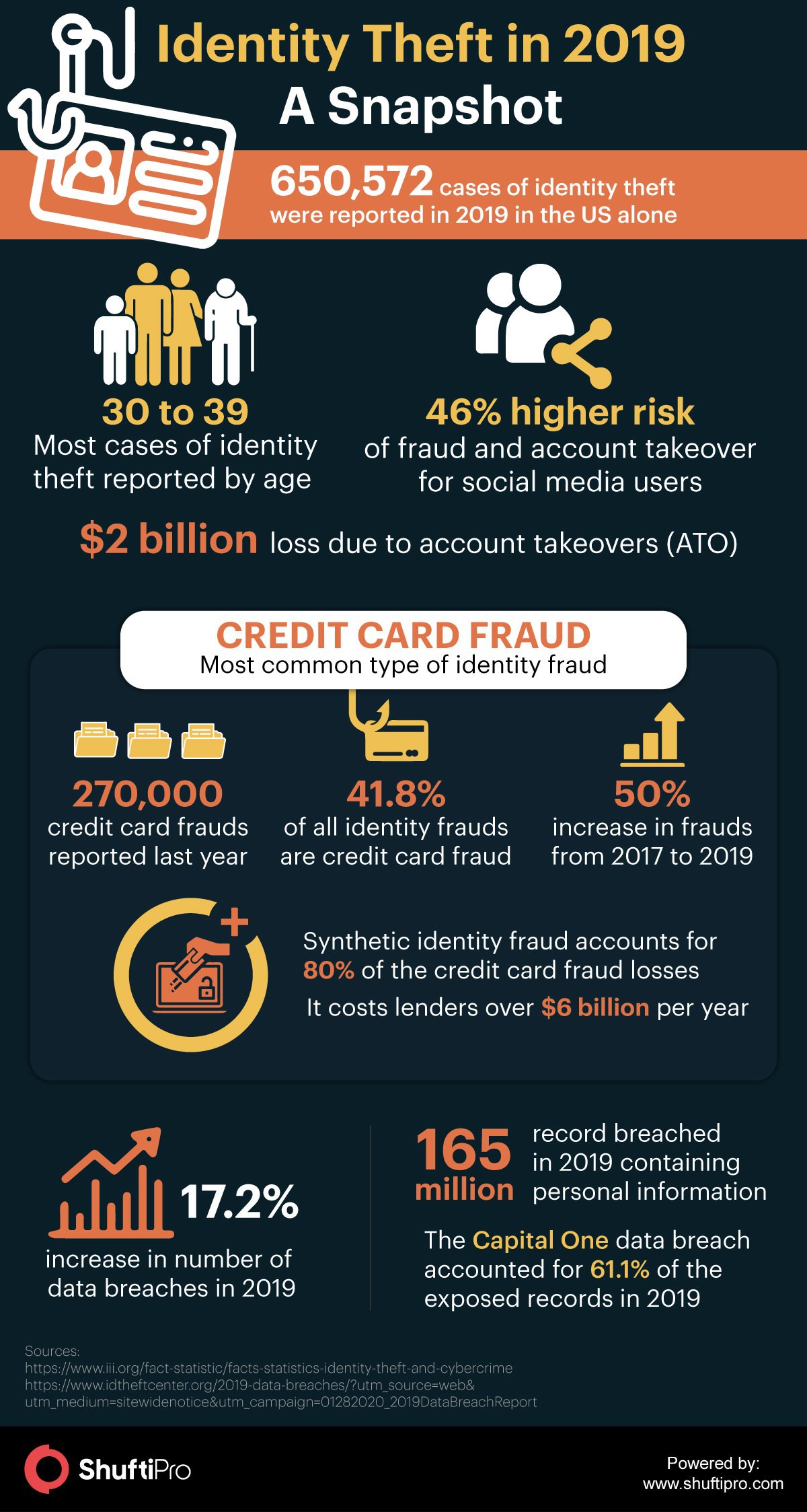
Most common methods of online identity scams
Although it’s difficult to identify a scam method that fraudsters may use but here are some of the commonly used identity theft methods:
Phishing
Phishing is a tactic used by fraudsters for sending emails to thousands of individuals with the purpose of tricking the recipients into performing an action. Hackers send these emails to random individuals but also target specific persons in some cases.
A phishing email tricks the recipients into opening a link that contains malicious software or redirecting to a real website look-alike and when the person enters their credentials into such sites the information is redirected back to the hackers.
The stolen information is then used to register credit card accounts or get access to the financial information of the victim. Even though it’s really hard to stop such emails landing into your inbox, by taking safety measures one could prevent becoming the victim of such attacks.
Imposter
In such attacks, fraudsters get access to someone’s social accounts and by pretending to be that very person tries to trick the person’s in the victims’ friend list to share their personal information.
Fake online profile
Scammers use different tactics to scam people online, one of these tricks is creating fake online profiles and pretending to be working for a bank or a financial institution. The scammers then send messages to people about their accounts, payment issues, and attach a link that takes the victim to a malicious website. These kinds of scams are increasing as more and more people are interacting online.
Pharming
Pharming websites are a bogus version of legit websites. Fraudsters have access to the website’s server and install a redirect address to the bogus version of the website. Upon surfing the bogus version, the user is asked to enter personal information. This information is then used to commit identity fraud.
How businesses could protect against online identity fraud?
Identity theft is a growing concern as cybercriminals are gaining ground and coming up with new ways to get identity information online. However, businesses can always stay a step ahead by adopting some precautionary measures.
Some of the precautionary measures that businesses could adopt are:
Adopt and adhere to stringent cybersecurity practices
In most of the cases, data breaches become the source for cybercriminals to attain PII. If online businesses adopt and adhere to strong cybersecurity practices, these data breaches could be prevented to an extent and by using high end-encryption the data could be protected. Adherence with data protection regulations such as GDPR and CCPA could help businesses securely maintain customer data.
Use online identity verification solution
Online identity verification is by far the most secure method to identify a legitimate user and deny fraudsters the access to use your platform for malicious purposes. Online businesses should adopt identity verification solutions to verify the identity of each onboarding entity. Businesses such as e-commerce platforms, online banking, and fintech could adopt online identity verification so that fraudsters won’t be able to use the stolen identity for making purchases or opening bank accounts for malicious purposes.

 Explore Now
Explore Now













