Blockchain and NFTs – Setting New Standards for Cybersecurity and Identity Management

Non-fungible tokens (NFTs) are an evolution over the emerging concept of cryptocurrencies. As finance systems are getting modernized, consisting of innovative trading and loan systems for different types of assets, ranging from lending contracts to real estate and artwork. However, by making digital representations of physical assets like painting, NFTs are the most advanced form right now to re-invention the finance infrastructure. Thus, the idea of representing physical assets in digitized form is not new, however, these concepts are combined with the significance of tamper-resistant blockchain of smart contracts.
Contrarily, blockchain and NFTs are also playing a crucial role in making the digital ecosystem secure, as fraudsters are becoming more sophisticated and are capable of exploiting cybersecurity systems. Thus, by utilizing the potential of blockchain technology and NFTs, an entirely new level of security can be attained.
Blockchain Technology – Revolutionizing Cybersecurity and Identity Management In Digital Ecosystem
Primarily, blockchain technology is the key driving force behind the success and emergence of cryptocurrencies. This technology is completely transforming the concept of payment gateways along with enhancing cybersecurity concerns. Blockchain technology utilizes cryptography to make transactional records that are unchangeable and can’t be tampered with. NFTs are also backed by this technology and are uniquely categorized through a cryptographic token that provides an extra layer of security by ensuring that each digital asset and transaction records are well- managed, easily being tracked and verified. In addition to this, NFTs are also designed to digitally represent physical assets, which has brought significant opportunities for businesses as well as individuals.
NFTs are now also being used to virtual depict something scarce, for example, in-game add-on features and other collectibles. Due to the unique identity of NFTs, they are providing more improving identification measures while enhancing cybersecurity. In addition to this, NFTs and blockchain technology are also empowering digital businesses to develop virtual ledgers to store cryptocurrencies and digital assets while maximizing security levels. However, the combination of blockchain and NFTs is considered the most advanced way of securing sensitive information and holds the necessary power to completely transform the use of the internet and cybersecurity.
Despite the fact, blockchain is the backbone of the digitization of payment gateways, it is setting new standards in the cybersecurity domain as well. By providing financial institutions and other businesses a decentralized platform to secure data, they tend to protect the companies through various cyber-attacks and financial losses. It also allows businesses to gather and maintain track of customers’ identities. Blockchain technology is signifying security innovations through the following aspects;
Security through Blocks: Blockchain basically works as a distributed ledger that stores and maintains a continuously growing list of client data records called blocks. Each respective block placed in the database is accompanied by a cryptographic hash of the previous block, a timestamp, and transaction data. The immutability feature of blockchain technology allows it to provide businesses and individuals with a sound sense of security and data protection. Other than this, it also backs businesses to determine and authenticate their identities before getting them on board and ensures data is not compromised.
Private and Public Blockchains: The concept of private and public blockchain is growing concerned nowadays. A private blockchain allows companies to communicate information without a designated central authority. On the other hand, the public blockchain databases are easily accessible to any individual in the digital ecosystem. However, both types of blockchain databases are highly secure and can not be exploited, as they deliver the maximum level of transparency. As a result, blockchain ledgers are becoming an ideal place to store digital data or assets.
Decentralized Technology: Blockchain technology allows both businesses as well as individuals to store cryptocurrency and private information in decentralized databases with a high level of encryption. With the decentralization feature, blockchain assures that hackers can get access to one’s identity. However, hacking attempts are impossible, as cybercriminals need to penetrate 51% of the blockchain system at once.
Smart Contracts: The emerging concept of the smart contract is getting global attention, as they are powered with blockchain technology that automatically handles the customer’s transactions and other dealings. They have attained customer trust by enforcing high-end security standards by being transparent and tamper-proof. Other than this, the financial firms are also using smart contracts to manage customer identities and PII. This also enables businesses to curb identity fraud.
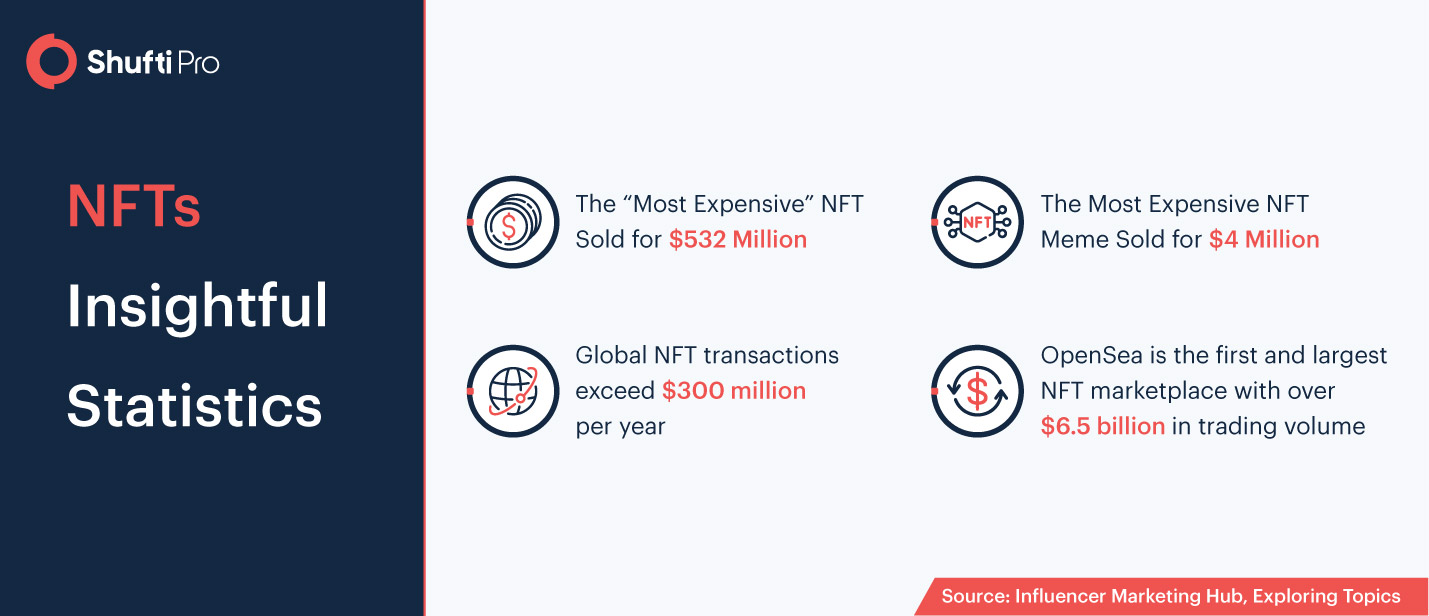
Influence of NFTs on Cybersecurity and Identity Management
As businesses are going digital, keeping sensitive information secure and tamper-proof is becoming more difficult than ever. However, Non-Fungible Tokens (NFTs) are one of the crucial ways to make cybersecurity and identity management systems secure and unhackable. Many global firms are adopting NFTs to secure their client data.
The following are a few examples of how NFTs can be used to promote cybersecurity:
Integrated Security Features
NFTs aren’t directly used but are combined with other security measures to increase the productivity of cyber security systems. This includes, encrypting the messaging services, and generating digital ownership signatures on transactions. Other than this, NFTs also interact with identity verification services through authentication, to assure the customers are onboarding with legit identities. Despite all benefits, NFTs are also being used to uplift security measures as they are hard to replicate and link to other virtual assets. The cryptographs also improve data protection. Furthermore, NFTs can also provide an extra level of security for businesses and individuals, aiming to secure their transactions or operations.
Smart Encryption and Validation
NFTs come up with a “smart encryption and validation” method that enhances the effectiveness of security systems, making them secure. This system is particularly designed for the businesses that are providing trading services. NFTs smart encryption and validation uplift the identification and security of public as well as private blockchain databases.
Thus, the encryption and validation technology of NFTs is inevitable. It imprints digital signatures to each asset or transaction making it impossible for criminals to replicate it. This is how NFTs are preventing stealing of assets in the digital ecosystem.
How Shufti Can Help
NFTs and blockchain technology are considered as the optimum ways to overcome identity fraud and financial crimes. Proof of ownership and digital signatures ensure that the data remains unbreachable. This concept will allow SaaS providers to enhance online identity verification solutions and cyber security protocols.
Shufti’s state-of-the-art online identity verification services are an ideal solution for every type of business providing digital services. AI-backed ID verification services enable companies to determine the identities of customers before getting them onboard with 98.67% accuracy in less than a second.
Want to know more about the identity verification solution?

 Explore Now
Explore Now













