eKYC: Transforming ID Verification for Enhanced Security and A Seamless Customer Experience

Governments have mandated various businesses, including financial institutions, to thoroughly understand their clientele worldwide to comply with regulations. These regulations, called Know Your Customer (KYC), aim to detect and prevent financial crimes such as money laundering.
The fundamental requirement of KYC is identity verification, which entails ensuring that customers are genuinely who they claim to be. In the past, IDV involved scrutinising information provided through physical forms and documents. However, with the increasing digitisation of the world, KYC policies and practices have had to adapt to meet customer expectations and address risks associated with digital interactions. Thus, electronic KYC (eKYC) came to the rescue.
Understanding eKYC
Electronic KYC is the digital method of verifying identity and other necessary KYC obligations. The approach may vary based on industry, business requirements, and customer preferences. However, it generally encompasses using electronic forms, digital records, and different levels of automation. Similar to conventional KYC procedures, eKYC is typically carried out during the initial account opening process and is subsequently maintained on an ongoing basis.
Different Signals to Use When Performing eKYC
eKYC has the potential to provide businesses with a more comprehensive understanding of their customers’ identities. This is due to the broader range of data and indicators that eKYC can leverage, surpassing what is typically available in traditional KYC procedures. Conventional KYC relies on active indicators, such as Personally Identifiable Information (PII) the user provides and third-party data from watchlist reports. However, eKYC combines these with passive indicators and behavioural signals that are challenging to assess through manual review of physical forms and documents.
Active Signals
Active indicators comprise information directly provided by the individual, including but not limited to:
- Name
- Address
- Date of birth
- Social Security number
- Employment information/source of funds
Furthermore, active indicators encompass any submitted documents and photos, such as government-issued IDs, bank statements, selfies, etc. In addition to the transition towards eKYC, governments like India and Estonia have introduced electronic identification forms, serving the same purpose as physical IDs. Although the concept of eID has yet to gain widespread acceptance at the federal level in the United States, several states have embraced it. States such as Arizona, Colorado, Georgia, and Hawaii, accept digital driver’s licences, which can be securely stored in an app or even an Apple wallet, depending on the state’s provisions.
Third-party Data
Third-party data refers to signals not directly or indirectly provided by the individual but rather obtained from external sources such as government entities, private enterprises, and authoritative databases. These datasets encompass various types, including:
- Government watchlists
- Sanctions lists
- Lists of Politically Exposed Persons (PEPs)
- Phone risk reports
- Email risk reports
- Adverse media reports
During the account opening process, third-party data is typically collected in the background, allowing businesses to enhance their understanding of customers without creating additional obstacles to the KYC process. Furthermore, many companies regularly cross-reference customer profiles with these sources to ensure the individual’s status remains unchanged.
Passive Signals
Passive signals, also known as device signals, are derived from the device that individuals use to undergo the KYC process. These signals are typically obtained in the background without the individual’s awareness. They encompass various data points, including:
- IP address
- Location data
- Device fingerprint
- Browser fingerprint
- Metadata
- Use of a VPN
Passive signals play a crucial role in online KYC as they enable digital verification and cross-referencing of the information provided actively by the individual with the data passively provided by the device. For instance, if someone claims to be in California, but their IP address indicates they are currently in Florida, further investigation may be warranted to ensure their authenticity.
Behavioural Signals
Behavioural signals are derived directly from the actions of individuals as they engage with online forms or applications. Generally, individuals are unaware that their behavioural signals are being monitored, assessed, and analysed. Examples of behavioural signs encompass:
- Detection of hesitations
- Identification of distraction events
- Tracking of mouse clicks and keyboard strokes
- Usage of developer tools
- Implementation of copy-and-paste operations
- The use of autofill functionality
Behavioural signals serve a range of purposes, for example, analysing behavioural data can assist in distinguishing between genuine human users and automated bots when completing a form or application. Similarly, it can contribute to detecting potential identity theft cases, such as when a form is conducted suspiciously. Consequently, behavioural signals, like passive signals, hold significant importance within the domain of eKYC.
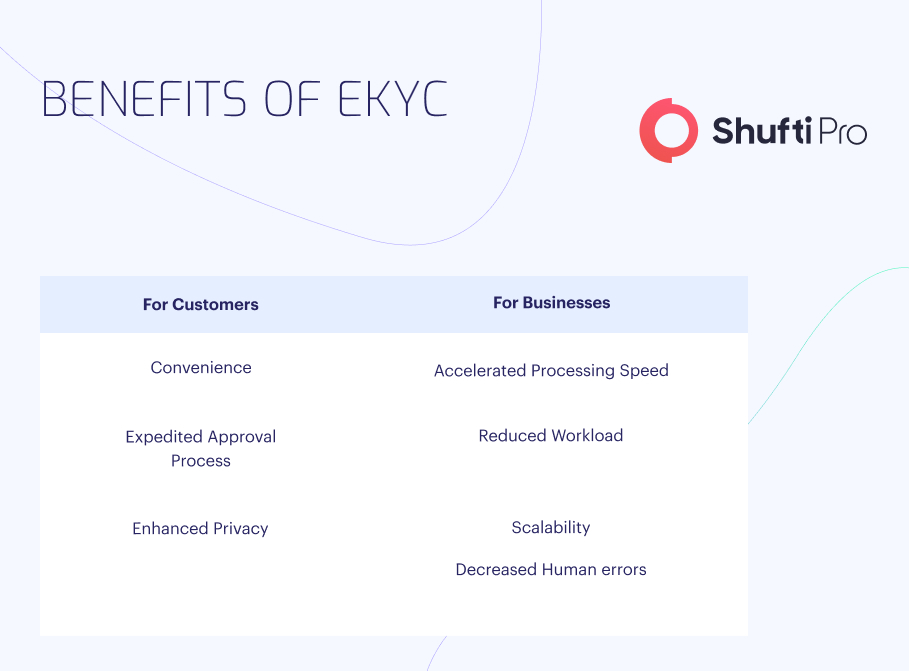
What are the Benefits of eKYC?
eKYC offers numerous advantages, primarily due to its ability to leverage automation more than manual identity verification processes by human personnel.
For customers, the benefits include:
- Convenience: Individuals and businesses can complete forms and applications without the need to scan physical documents, print paper forms, or visit physical branches.
- Expedited Approval Process: Automatic review of electronic data enables customers to enjoy faster approvals for account opening.
- Enhanced Privacy: Embracing eKYC typically entails fewer human individuals reviewing sensitive data as it is processed automatically by the system. This translates into improved overall privacy for customers.
For companies, these benefits include:
- Accelerated Processing Speed: Upon submission of customer information, identity verification can be completed within seconds, significantly faster than manual review. This expedites the process, reducing drop-offs and enhancing conversion rates.
- Reduced Workload: With diminished reliance on manual review, financial institutions require fewer employees dedicated to KYC, enabling the reallocation of resources to other areas.
- Scalability: By minimising the need for hiring and training manual reviewers, eKYC processes facilitate business growth and scalability. Furthermore, the availability of electronic KYC services around the clock ensures continuous business operations beyond regular working hours.
- Decreased Human Errors: The reduced involvement of humans minimises the risk of errors, resulting in more efficient workflows.
How Can Shufti Help?
Shufti offers eKYC solutions to 230+ countries and territories and supports 150+ languages, helping businesses keep scammers away and comply with regulations.
Here’s what makes Shufti’s eKYC solution stand out:
- No document uploading
- Fast customer onboarding
- 99.3% accuracy rate and verifies clients within seconds
- Real-time authentication from government databases
Want to know more about how eKYC helps businesses keep scammers away?

 Explore Now
Explore Now













