Identity Proofing – 7 Reasons Why Businesses Need it Now!

Modern-day cyberspace has effortlessly diminished the boundary between the real-life and digital identity of a person. The online marketplace is transforming the daily life routine of mankind by enabling customers to use their identity to make purchases, avail services and even have a meaningful existence on social media platforms. But the risk of identity theft is far greater on the internet and various online services as compared to physical scenarios. Identity proofing seems to be the legit answer for businesses operating via online channels that want to avoid registering users with fake identities and stolen identity information.
Most businesses, having a digital presence on the internet, consider the importance of online identity proofing but fail to recognize the specific form of ID verification and KYC compliance that can help them choose an appropriate business fraud prevention tool from a large list of KYC solutions.
But before we dwell into the importance of an identity proofing solution in the modern-day digital world, let us explain what does it mean when we talk about Identity proofing.
What is Identity Proofing?
Identity proofing is used to establish uniqueness and validity of an individual’s identity. It helps businesses to ensure that the identity claimed to be owned by an incoming user or potential client is actually owned by that particular individual. Identity proofing and authentication can be performed by digital KYC that uses identity documents, biographic information, biometric information, and knowledge of personally relevant information.
The emergence of new technologies such as biometric sensors, OCR technology and high-resolution cameras in smartphones are helping businesses to adopt identity verification and digital authentication. Identity proofing is a great tool to achieve risk-based decision making based on concrete data collected through identity proofing services and solutions.
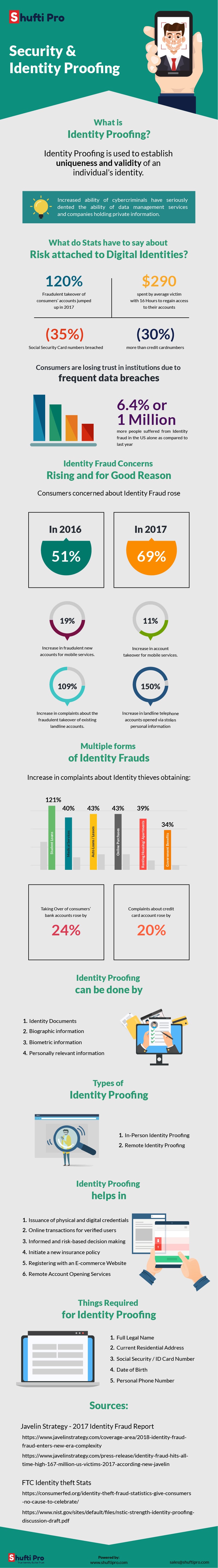
Requirements for Identity Proof
Now depending on the individual or regulatory KYC compliance guidelines, there are a number of identifying factors that can be used for identity proofing and authentication. Most of the KYC solutions require following personal details as identity proof:
- Full legal name
- Current Residential Address
- Social Security Number/ID Card Number
- Date of Birth
- Personal Phone Number
In some cases, even before an identity proofing process starts off, privacy law requires companies and governments to collect consent of their users. This consent allows businesses to collect personal information of their customers only for identity proofing. Several laws have been introduced in various territories – like GDPR in EU – that prohibit the use of such collected information anything instead of verification purposes.
Types of Identity Proofing
There are two main formats of identity proofing that can be used by industry as well as governments for identity verification:
In-Person Identity Proofing – Such kind of identity proofing is carried out by physical evidence of identity being provided to verifying authority or a company. Based on the KYC compliance requirements, ID verification is performed to validate the personal information. Most Know Your customer solution are fully compatible with existing software allowing for digital KYC to be completed in a few minutes, even in case of in-person identity proofing and authentication.
Remote Identity Proofing – Also known as online identity proofing, this kind of digital authentication does not require the physical presence of the person who is performing digital KYC. Personal information, also known as Identity Proof, can be sent in the form of digital communication to the business that wants to authenticate the identity of their new or existing customer. Some versions of online identity proofing also include virtual sessions where a user can digitally present documents for identity proofing and authentication. Scalability of such identity proofing solutions is greatly dependent upon the amount and type of confirmation data that is required for remote or online identity proofing.
Challenges for In-Person Identity Proofing
Now although in-person identity proofing is considered the gold-standard to perform best identity proofing, there are some issues that undermine the utility of this format, such as:
- The cost of in-person identity proofing is too high for service providers, as it requires the need for physical employees to collect identity proof from incoming users, not to mention to have multiple physical locations to facilitate the incoming customers and users who want to perform digital KYC.
- In-Person identity proofing is really inconvenient in this modern day and age where digital resources are used to perform even the minimal tasks.
- In-person identity proofing and authentication is also dependent upon the level of training received by the person performing ID verification
- In the absence of digital KYC solutions or even technologically sound identity proofing service, even a human verifying operator will be unable to check for finest tampering caused by refined technical methods.
Online Identity Proofing Challenges
Now there are many KYC solutions and identity verification services available on the internet claiming to be the best identity proofing services but even the most reliable identity proofing and authentication software face some tough challenges such as:
- A significant amount of personal data available on dark web collected by sophisticated and hard to track data breaches
- The growing threat of social engineering from big tech giants
- Traditional methods of collecting identity proof have not evolved according to recent cyber threats.
- A grave threat of privacy breach resulting from a centralized data resource.
Now that we have discussed in great detail, each aspect of Identity proofing and how it is used by businesses around the world to authenticate the identity of their users and what kind of personal information is collected for an identity proof, here are 7 reasons why businesses need to start taking identity proofing and authentication seriously in the near future.
-
Smarter Cyber Criminals
Recent years have witnessed a substantial surge in the ability of cybercriminals to seriously dent the overall security of data management services and companies holding private information. Even the most famous names of the tech world have been outsmarted by the data bandits who have adapted complicated and hard to detect methods of cyber crimes.
Even the non-tech world, ranging from e-commerce to banking organizations, have failed time and again to implement reliable digital authentication solutions that can ensure the safety of personal data of their millions of customers. An authentic identity verification solution that can adapt to the changing landscape of online identity proofing, is the only way to secure your digital resources and never lose the trust of your customers.

-
Issuing Secure Access
Recent times have seen a substantial surge in identity theft cases in which users have complained that their identity proof was actually misused by someone else, to avail services on their behalf or gained access to restricted channels. Account takeover ratio in most countries has doubled over the years which means that cybercriminals are able to use personal information of real-users to otherwise inaccessible digital resources.
Recent surveys have also shown that the majority of internet users have now started shifting the responsibility of securing their identity from their own self to the companies that are offering them various services. Users believe that despite using all possible tactics to secure their identity, it is the weak strategies of Banking organizations, e-commerce websites and social media platforms that are leading to frequent data breaches. So it is important for businesses to adopt a more vigilant approach towards providing access to their users and implement best identity proofing strategies to not only make their customers feel secure but to safeguard their own business interest as well.
-
Risk-Free Payment Gateways
Recently, several banking organizations, credit card companies, and even the most reputable digital payment giants have become victims of large-scale data breaches. Most companies and service providers still rely on 3rd party payment gateways but the most innovative ones have even started launching their own payment gateway in order to make payment systems not only secure for their customers but to make the entire purchase cycle frictionless for their customers. An in-house payment gateway integrated with identity proofing solution can serve to safeguard the business interest and enhance payment processing speed at the same time. A glimpse into the history of identity proofing can give you an apt idea that online payment systems are the most perfect use case for any online identity proofing service.
Using a third party identity proofing services and solutions, such as Shufti, can make the entire payment cycle, a business supporting process rather than business disruptive process.
-
Informed Decisions about the clientele
Any business executive that have utilized ID verification or any other KYC solutions can vouch that these know your customer systems are not only super-effective in handling identity theft prevention and anti-fraud protection, but they also help a lot in collecting verified information regarding customers. When fed into a CRM or Customer Support Desk, these identity proof collected from customers can become a goldmine of Big Data.
Based on this collected set of data, business executives can not only track activities of their users across multiple channels but also chart out new strategies to capitalize on the existing number of users and even formulate growth plans for future expansion.
-
Remote Account Opening
Now not all business can relate to this reason to integrate an online identity proofing solution into their business practices, but those who want to establish a stronger user base like banks, FinTech products, crowdfunding websites and many other industries, identity proofing services and solutions are the most important facilitator that can not only help build trust among its customers but ensure that only verified customers are able to open a remote account with them
-
Eradicate False Financial Claims
Starting off from cashback requests on e-commerce platforms and going till false insurance claims, identity proofing has the ability to solve many problems for a large number of businesses. Each transaction performed using digital resources can be vetted by appropriate identity verification service. When a business decides to collect identity proof for every transaction performed by its customers, the rate of fraudulent financial claims is virtually reduced to zero.
-
Reliable Customer Base
Identity proofing solutions have the ability to reduce the overall workload of businesses and digital platforms, by checking the identity proof of a customer right at the time of registration. Identity verification and identity proofing solutions such as Shufti can perform several verifications ranging from age verification to biometric verification, in order to ensure that only a verified customer is able to register on a digital platform. It surely has the downside of reduced incoming users, but one the most amazing benefit of this approach is that identity proofing with help you collect 100% verified and reliable customer base, opening vast avenues of expansion in the future.
Now, if you need a highly sophisticated identity proofing solution that is not just efficient in detecting identity theft and digital fraud but also cost-effective for your business operations, then there is no better option then Shufti. It offers real-time verification results for a large number of identity verification services such as Face verification, document verification, ID verification, handwritten note verification, customized document verification, address verification, and 2-factor authentication. AML background checks provide even a higher layer of financial risk protection to companies and businesses that want a reliable identity proof from their customers.
Artificial intelligence and human intelligence hybrid make the entire identity proofing and authentication process hassle-free for Shufti customers. With competitive price model and a Restful API that makes integration smooth with pre-existing software, platforms, and applications, Shufti is one of the most reliable identity proofing solution that a company can use to reduce identity fraud cases.

 Explore Now
Explore Now














