KYC and Blockchain – The Foundation of a Secure Crypto Landscape

Blockchain technology has demonstrated fast-paced growth throughout the world and now faces the challenge of financial compliance due to the anonymity it provides. Although blockchain technology has not entered the mainstream in terms of adoption, its use has grown in the past years. The decentralised structure of blockchain attracts investors to secure their money through cryptocurrencies and other digital assets.
As cryptocurrencies are not issued by central banks, investors are provided additional privacy. However, this anonymity does give way to financial criminals who look for ways to launder their ill-gotten funds. For this reason, the protection of crypto users’ data has become more significant.
Protection of Blockchain Data
The blockchain industry in general faces compliance challenges because of its decentralised structure. The system of decentralised ledgers that was designed to keep user data private has created a potential safe haven for money launderers in the crypto space. In light of the rising instances of financial crime in the crypto sector, world governments are raising questions regarding the anonymity of the decentralised system.
The EU and the US have stated that there needs to be more regulation and oversight on the industry. To achieve that, one of the most important aspect is Know Your Customer (KYC) compliance. The importance of KYC standards has repeatedly been stressed by global financial regulators to bring the crypto sector under the same umbrella as banks and other financial institutions.
In the cases where KYC verification has already been applied, it has made customers realise the loopholes and privacy concerns in blockchain central trading platforms. That being said, industry experts still believe that if blockchain technology is used in the right way along with KYC, the privacy concerns can be resolved.
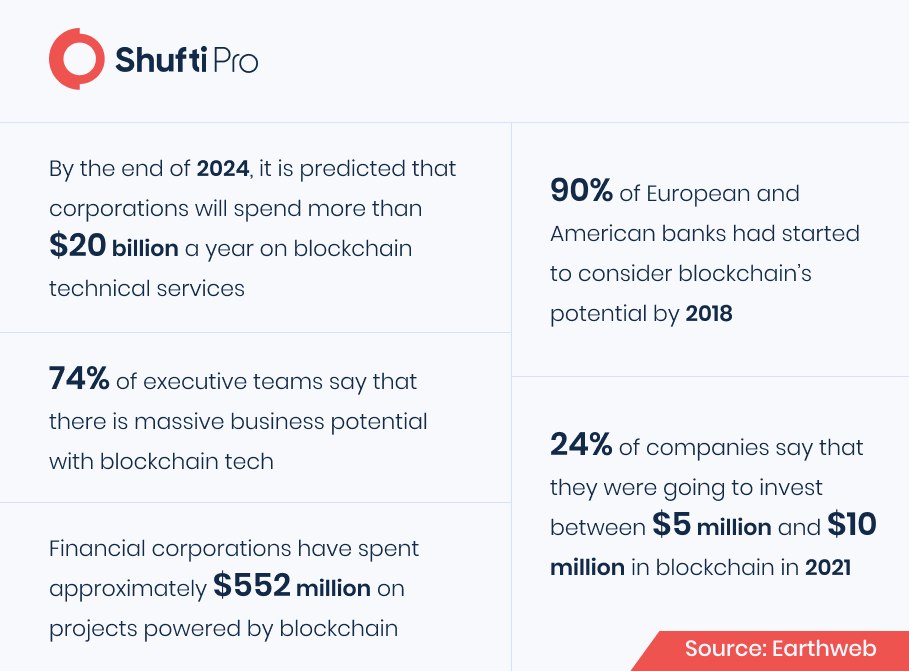
KYC and Blockchain to Prevent Financial Crime
The real aim to ensure KYC compliance in any type of financial institutions is to secure it from financial crimes. In the case of cryptocurrencies and other digital assets like Non-fungible Tokens, this can be achieved by ensuring that the blockchain itself is KYC compliant. Not only will this build trust among crypto customers, but it will also eliminate the chances of fines due to money laundering.
Once customers begin to understand that their crypto data is protected, the chances of blockchain becoming a mainstream technology will also increase. Several crypto trading firms have already adopted the concept of KYC verification as it has proven to eliminate financial crime in banks and investment firms for years.
Why KYC is Important
The US Financial Crimes Enforcement Network (FinCEN) and other global financial regulators like the Financial Action Task Force (FATF) have made it mandatory for financial institutions to incorporate KYC measures within their systems. KYC requirements from regulatory authorities include the monitoring of customers’ transactions and report suspicious activities. Along with KYC verification, financial institutions are also required to implement anti-money laundering (AML) measures to conduct background screening of customers.
However, anonymous transactions in cryptocurrencies enable financial criminals to get away with their illicit activities. Although the decentralised structure of blockchain provides legitimate crypto investors the privacy the need, KYC verification requires the sharing of personal information so that crypto firms can secure their interests. As of today, the majority of crypto transactions are not subject to KYC or AML measures. While the crypto sector grows at a reasonable rate, the lack of regulation and checks can have a negative impact on its growth.
The rate at which crypto is being used to launder money is alarming, especially during the Russia-Ukraine conflict when Russian oligarchs are looking for ways to hide the origins of their ill-gotten funds. For this reason, governments around the world are developing regulations to oversee crypto transactions in a more detailed way. The common ways crypto investors use to purchase crypto are through crypto ATMs and peer-to-peer exchanges, where there is a lack of KYC requirements. This allows anyone with enough money to purchase crypto, including money launderers looking to legitimise their illicit funds.
Looking on the bright side, regulations to oversee the crypto sector are constantly evolving in Europe and the US. FinCEN has urged crypto exchanges to follow KYC standards and implement AML measures to ensure compliance with international standards. Compared to the US, the EU’s KYC requirements are not that stringent. Although the EU also requires compliance procedures to be implemented, firms that offer only crypto trading services are not subject to any particular legislation.
How KYC and Blockchain Can Be Used Together
While crypto investors and traders have prioritized privacy over everything, criminal minds have capitalised on the anonymity for their own benefit. Crypto buyers want to keep their personal data private from service providers and government, but the real protection comes with KYC compliance. Although KYC checks in blockchain systems may initially seem to be unnecessary, they can potentially improve the protection of crypto data by a significant margin. Besides, identity verification is the most basic security check in any kind of financial operation. Legitimate customers who have previously carried out transactions through the traditional banking system are familiar with the use of KYC and AML measures for fraud prevention. The combined use of KYC and blockchain can increase the rate of adoption by easing the integration into existing financial systems. Moreover, it will also encourage crypto firms that have previously not adopted these checks to use them and secure their customers’ interests. On the other hand, blockchain and KYC can together improve the system of identifying and eliminating deviations in trends and suspicious activities.
What Shufti Offers
Although the currently available KYC solutions are technology advanced, there are other aspects to consider before combining them with blockchain technology. In any case, the benefits of both blockchain and KYC compliment each other to improve the security of crypto transactions. Protection of customers’ data is essential for crypto firms in order to comply with regulations like the General Data Protection Regulation (GDPR) of the EU.
Proof of ownership and digital signatures in blockchain ensure that crypto users’ data remains unbreachable, which allows SaaS providers to enhance online identity verification solutions and cyber security protocols.
Shufti’s state-of-the-art online identity verification services are an ideal solution for every business providing digital services. AI-backed ID verification services enable companies to determine the identities of customers before getting them onboard with 98.67% accuracy in less than a second.
Want to know more about the identity verification solution?

 Explore Now
Explore Now













