How Does Layering in Money Laundering Work and How to Stop It?

- 01 What Is Layering in Money Laundering?
- 02 The Mechanics of Layering
- 03 Practical Examples of Layering
- 04 Layering Between Traditional and Digital Financial Ecosystems
- 05 Industry Risks and Trends
- 06 Key Red Flags that Can Signal Layering Activity
- 07 AML Steps for Detection of Layering in Transactions
- 08 The Role of Compliance Teams & Regulators in Disrupting Layering
- 09 Layering Detection and Prevention Strategies
- 10 How Shufti Helps Businesses Strengthen Their AML Defenses
- 11 FAQs
Dirty money rarely moves in a straight line. After placement brings illicit funds into the financial system, criminals build a maze of transactions to break the audit trail. That maze is layering, the second (and most complex) stage of money laundering. This is where funds are obscured through rapid movement, asset conversions, and deliberately opaque ownership structures. For banks, fintechs, PSPs, and DNFBPs (e.g., real estate, casinos, dealers in precious metals and stones, and the art market), understanding layering is critical to effective AML.
What Is Layering in Money Laundering?
Layering is the second stage of money laundering, between placement and integration. This is where illicit funds are moved across accounts, entities, jurisdictions, and asset classes to break the audit trail and obscure their origin. Unlike placement (which leaves an obvious footprint), layering relies on rapid movement, complex ownership, and conversions of value to cut off links to the predicate offense.
The Mechanics of Layering
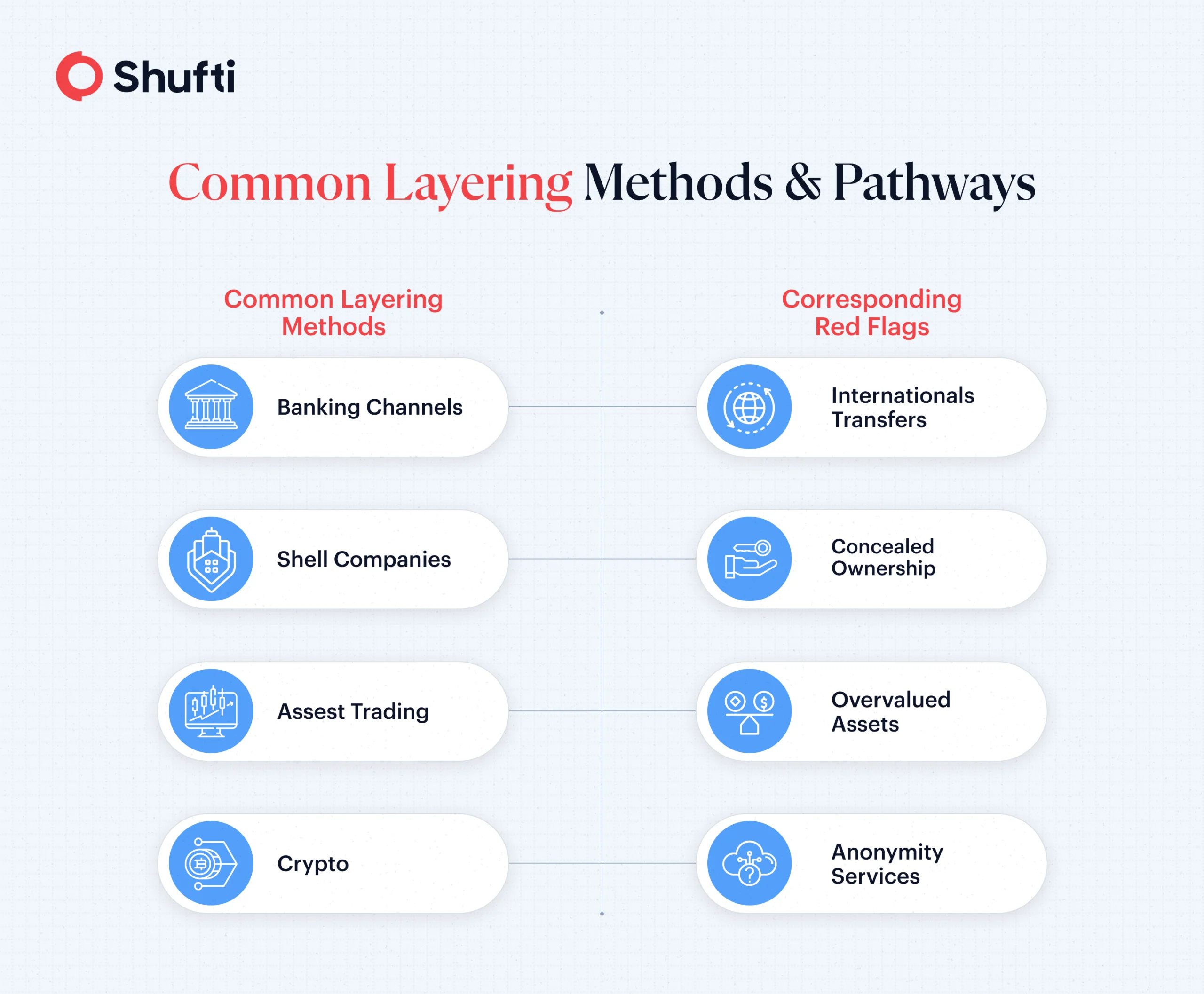
Criminals exploit gaps in financial controls to add “layers” of transactions and ownership. Common methods employed for layering include high-velocity transfers across banks and PSPs, use of shell and front companies with nominee directors, and buying/selling real estate, luxury goods, or securities. As technology is evolving, money launderers are leveraging digital tactics such as mixers, privacy coins, and cross-chain swaps (“chain-hopping”). The goal is not profit on each step, it’s the distance from the source.
Banking channels
Criminals may begin by transferring money in large amounts by wire transfers, offshore accounts, and remittance services. All these measures are meant to muddle investigators. Imagine that money flows through a dozen jurisdictions, exploiting jurisdictional loopholes and lax oversight. Banking layering is perfect, owing to its multidimensionality, pace, and international coverage. Let’s explore these mechanics in detail:
Shell companies and front businesses
Shell companies (entities that exist only on paper) add another layer of obscurity. The existence of shell companies makes it even more obscure; they are companies on paper only. These business fronts are used by criminals to transfer money across borders, blending illegal cash with legitimate business dealings. It may involve purchasing, selling, and even writing counterfeit invoices, all aimed at obscuring the waters of the auditors and compliance departments.
Asset trading and investments
Money doesn’t just move through accounts; it can become condos, paintings, jewelry, or stocks. Criminals may purchase real estate above market value, acquire luxury vehicles, or trade in commodities and artwork. Markets with less scrutiny often see high-value goods purchased and resold, keeping the original source of wealth shrouded in secrecy.
Technology-driven methods
Layering money laundering thrives in the digital era. FATF has published reports on risks of abuse linked to new technologies, particularly virtual assets, and new payment methods that enhance anonymity. Cryptocurrency transactions, fintech platforms, prepaid cards, and electronic transfers all offer new spaces for criminals to maneuver. Changing one cryptocurrency into another across blockchains, sometimes called chain-hopping, makes tracing the money even more challenging. Online assets are easy to move, hide, and “wash.”
Practical Examples of Layering
Picture a mortgage company laundering dirty money through a check-cash operation, and then through brokerage and trade finance business in the guise of loans. Or, picture a criminal purchasing luxury condos in multiple cities, without a paper trail through money transfers overseas and shell companies.
The hypothetical scenarios make it simpler to grasp the concept. Imagine an individual who buys art anonymously, retains paintings overseas, and sells the art months later in “clean” money.
Such scenarios portray the manner in which criminals act in a complex manner in a bid to dissociate themselves from the results of their criminal acts.
Layering Between Traditional and Digital Financial Ecosystems
Banks, complete with their worldwide infrastructure, continue to be the focus of money laundering layering, but digital assets and fintech platforms are broadening the field. Fintech can sometimes lack robust know your customer (KYC) controls or fail to monitor asset conversions in real-tim, often due to contradictory cross-border regulations. Comparing traditional banking to the swift, anonymous world of crypto shows how layering adapts to changing technology.
Industry Risks and Trends
Some sectors are especially susceptible to layering:
- Size and speed in banking make it an attractive target
- Real estate markets, especially where surveillance is low
- Casino, money, and chips go well together
- The art market, prized for anonymity
- Cryptocurrency sites, facilitating quick, hassle-free, borderless transactions
The recent developments are increased electronic activity, rising cross-border transactions, and sustained demands for effective compliance programs. The size of the issue itself is a reminder that we have to be on our guard concerning the most recent techniques.
Key Red Flags that Can Signal Layering Activity
Detecting layering isn’t simple; it requires noticing patterns others miss. Watch for:
- International wire transfers with no clear business purpose.
- Rapid pass-through activity between related accounts/entities.
- Ownership structures that appear intentionally confusing or opaque.
- Use of shells with no physical presence, staff, or web footprint.
- Round-tripping: funds return to the origin after several intermediaries.
- Sudden spikes in volume/velocity without corresponding business activity.
Each of the red flags might appear normal in itself. Together, however, they are a warning.
AML Steps for Detection of Layering in Transactions
The layering stage of the AML life cycle involves layering using robust tools and procedures:
- KYC procedures that dig deeper into identity and ownership. Read more about Shufti’s CDD approach.
- UBO verification to identify risks attached to legal structures
- Using analytics and transaction monitoring to pick out abnormal patterns in real time
- AI and ML technologies are used to scan for signs of financial crime
- Using tools like continuous media monitoring and negative news
A strong AML approach isn’t just about ticking boxes; it’s about proactively tracking transactions, linking data, and partnering across teams.
The Role of Compliance Teams & Regulators in Disrupting Layering
Regulators provide guardrails, but they stand on the front lines with compliance teams, who are raising the flag on suspicious behavior and getting much more skilled at the methods of risk. Banks, regulators, and law-enforcement bodies can dismantle complex layering schemes through collaborative information sharing.
These measures are supported by effective public-private collaboration and multinational collaboration, which have contributed to maintaining trust in the financial system.
Layering Detection and Prevention Strategies
To be ahead of the game consists of acting on more than one front:
- Transactions monitoring to identify high-risk transactions or movement of assets.
- Improved due diligence, particularly in the case of a customer or a high-risk business.
- Collaboration with regulators, data sharing with other FIs, coordinating strategies, and whistleblowing.
- Education and training of employees on suspicious behavior.
- The shift to digital detection ML risks using advanced AML technologies to replace manual review.
These measures may not be ideal, yet they increase the chances of arresting criminals before they can conceal the money.
For more practical resources, check out Shufti’s recent guide on the three stages of money laundering and how AML checks combat fraud.
How Shufti Helps Businesses Strengthen Their AML Defenses
Layering in money laundering involves complex and intelligent techniques, and so should be your AML solutions.
Disrupt layering before it takes root. Shufti unifies AI-powered KYC/IDV, KYB with UBO verification, and real-time AML screening & watchlist monitoring (sanctions, PEPs, adverse media) to expose shell companies, high-risk links, and hidden ownership, at onboarding and continuously. With Shuft, businesses meet regulatory expectations, cut false positives, and keep illicit funds out without slowing good customers. Book a demo to see how fast you can pierce the maze.
FAQs
What is the stage of layering in money laundering?
Layering money laundering is simply the process of covering up the source of illegally acquired funds by transferring them through a sequence of transactions- banking transfers, asset transfers, and business transactions such that their origin can no longer be traced.
What are the red flags that can be used to identify layering in transactions?
The common international remittances, utilization of various accounts, shell companies, vague ownerships, and buying or selling of assets without clear business reasons are all thought of as essential red flags of layering in money laundering.
How do modern AML solutions disrupt layering attempts?
The complex layering activities are easily spotted and reported with automated transaction monitoring, in-depth identity checks, analytics, and AI-driven tools in real-time, bridging the risk between manual review and digital crime-fighting.

 Explore Now
Explore Now













