The need for identity verification solutions spiking in demand

At present, we are living in a digital world. Everyone is on the internet which is an anonymous space and people can easily hide their identities there. People use pseudo names to hide their real identities. This is the case of many cybercriminal activities taking the internet to a storm. Therefore right authentication and identification of people through digital identity verification solutions have become crucial more than ever now. Cybersecurity is the topic of utmost interest for all businesses online and that is due to the increasing number of high-profile data breaches. Such cyber criminal activities have affected millions of consumers and organizations. Businesses failing to take the right steps and right identity verification services to end up falling in the pit of fraudsters. There are a number of online scams like identity theft, credit card fraud, phishing, account takeover, etc that have everlasting impacts on businesses.
Identity verification is an essential component in order to fulfill the regulatory requirements of KYC and AML checks as well. KYC which stands for know your customer law is mandatory to be fulfilled and refers to authenticating the identity fully before letting him into the system. AML anti-money laundering checks are to screen the individuals against different sanction lists and PEP lists to make sure that they do not hold any criminal history and have never been involved in any kind of money laundering activity. Businesses need to adhere to these regulations to be safe from fraudsters and to provide a sense of security to their customers who are providing them their private data. By deploying identity verification solutions, businesses gain the trust and confidence of their clients as well as they appreciate that businesses have taken all necessary measures to save their personal information from fraudsters.
Businesses have to perform the identity verification solution such that it does not affect the user experience. Digital identity verification solutions provide quick authentication in no time, enhancing the customer’s experience. Unlike manual identification which takes days and a lot of time and effort of both customers and employees, digital solutions are smart and provide seamless authentication in real-time. AI-based identity verification solutions are accurate while on the other hand in manual identification errors and omissions are always expected.
The Rise of Digital ID verification for Business:
Cybercriminals are becoming more sophisticated with time so businesses are arming themselves with solutions to protect themselves against frauds. Identity authentication technology acts as a shield against all such fraudulent activities. Such solutions have evolved using biometrics as a stronger security measure to combat fraudulent activities. Digital ID verification solutions, when installed in a system unequivocally answer the question that the customer is actually who he says he is before starting to deal with him.
Frauds are clamping up day by day so the demand for identity verification technology is also rising. The digital world has brought so many cybercriminal activities to light which has made businesses take stringent measures against fraudsters.
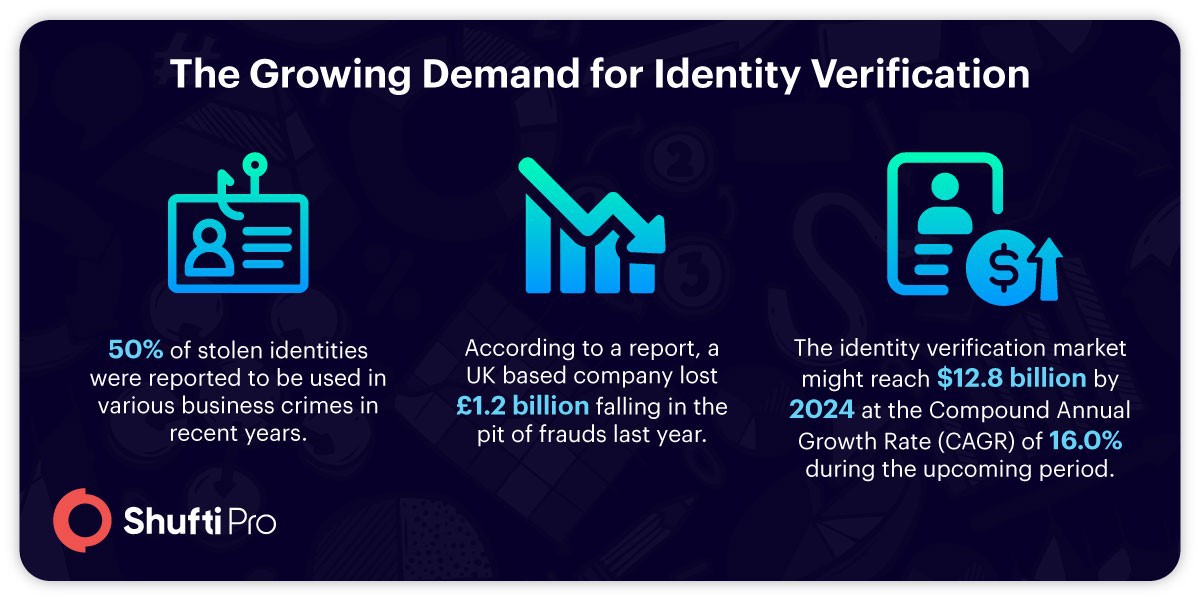
Life is busy and people have no time for face to face communications so digital connections are preferred so is the case with identity checks. Manual identity verification is a thing of the past as they require a lot of time and human effort.
The number of digital frauds has risen due to the presence of users on the internet. So the regulatory authorities have made it mandatory for every business to have sound identity verification solutions integrated into their system to put a halt on a number of crimes like money laundering, terrorist financing, identity theft, credit card frauds, etc. This verification is done by verifying the original documents, addresses, and biometrics of an individual.
Google to extend Identity verification requirements:
Recently John Canfield, Google’s Director of Product Management, Ads Integrity, announced that the company is extending identity verification policy for all advertisers. Back in 2018, the company introduced a feature according to which political advertisers go through a verification of their identity, which was then displayed as part of the ad itself. This was done to increase transparency and to end the mistrust around the sources behind political ad buys. Furthermore, regardless of the topic, the company has announced to make identity verification a required part of the ad buying process. This is done to lessen the ambiguity on the internet. The party will go through proper document verification at the start to know exactly what is posting.
Types of Digital Identity Verification Solutions:
Following are types of digital identity verification solutions
Biometric Verification Solutions:
The biometric verification system is used to perform customer due diligence by using one type of biometrics – face verification, fingerprint scanning, palm recognition. Through a 3D depth perception technique, face verification authenticates an identity in no time. With liveness detection feature originality and presence of a person is verified to combat spoofing attacks.
Document Verification:
Digital document verification scans the document to validate the document is real and original. Document picture is uploaded and using OCR technology, the information can be taken from the document.
Address Verification:
Address verification is a proof of residence for users identity. By using OCR data extraction, it scans utility bills, bank statements, etc.
2-Factor Authentication:
2FA provides quick remote user authentication remotely by sending personalized code. It is an auto-generated code to provide user access.
KYC and KYB Checks:
KYC and KYB are essential for businesses as per regulatory authorities when dealing with other businesses for the partnership to make sure the other business is not a shell company. Because of scams like digital fraudulent activities, data breaches, and ID theft there are some serious digital security concerns for all sorts of businesses.
AML Screening:
AML screening is a process to monitor accounts, detect financial crimes to relevant authorities. To tackle intrinsic money laundering risks the company needs to have customer screening against sanction lists and PEP lists for Anti-Money Laundering (AML) to prevent and deter money laundering and terrorist financing.

 Explore Now
Explore Now













