AML Analytics that Turn Data into Defense Against Financial Crime

- 01 What are AML Analytics tools?
- 02 What Are the Different Types of AML Analytics?
- 03 Why Legacy Systems Burnout Your Productivity and Resources?
- 04 Key Methods and Technologies Used for FinCrime AML Analytics
- 05 What are the core components of an AML analytics software?
- 06 What do authorities think about AML CFT Analytics?
- 07 How AML compliance analytics benefit Financial Institutions?
- 08 How Shufti Supports AML Analytics and the Risk-Based Approach?
“Suspicious activity rarely looks suspicious on its own”. Because a single payment resembles routine business when looked at in isolation. However, the same payment emerges as risk when thousands of points connect across time, entities, and channels. AML analytics is the lens that makes those connections visible, understandable, and actionable for Anti-Money Laundering compliance teams.
What are AML Analytics tools?
Anti-money laundering (AML) analytics is the disciplined use of data science and AI to detect, predict, and prevent financial crime. AML analytics software analyzes transactions, customer profiles, counterparties, devices, and open-source intelligence to identify hidden connections that fixed rules can’t catch. This approach fits the risk-based model advocated by leading authorities, where monitoring intensity matches actual exposure rather than one-size-fits-all thresholds.
Financial Action Task Force (FATF) advocates the use of new technology as a way to improve the effectiveness of a risk-based approach while maintaining strong governance. Major regulators have also encouraged the use of innovative techniques that are explainable and strengthen AML outcomes.
What Are the Different Types of AML Analytics?
AML analytics tools can be divided into three categories based on the type of function they perform:
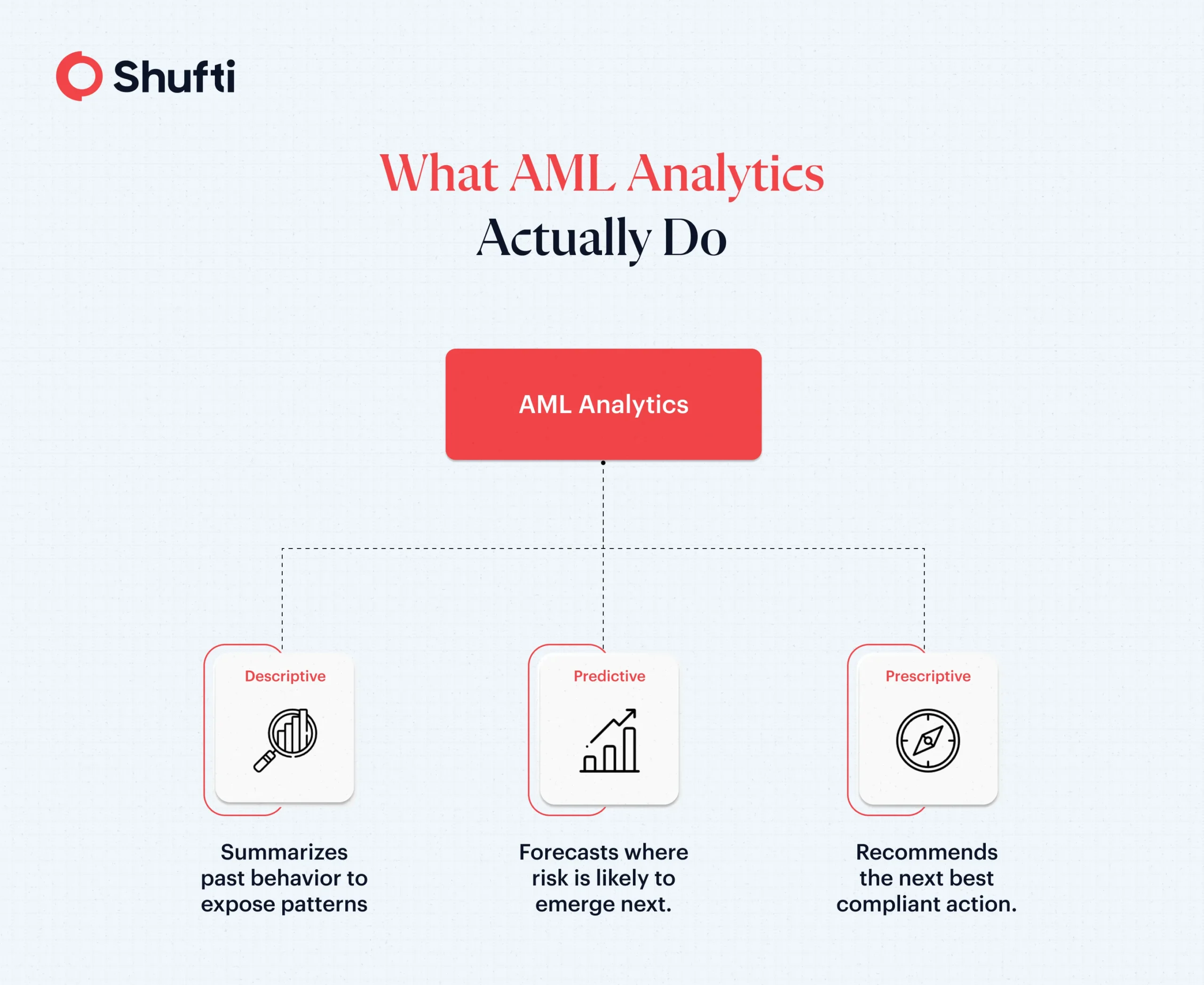
1. Descriptive analytics
It explains what happened by summarizing a valuable resource of an organization, its historical data. AML teams identify patterns in past alerts, behaviors, products, or geographies to understand where risk has concentrated. MIT Sloan defines descriptive work as retrospective pattern finding that turns raw records into insight.
For example, it can identify cross-border transactions in specific foreign jurisdictions as the most common pattern in the majority of suspicious activity reports (SARs) filed in previous years. This provides an opportunity to calibrate the controls to mitigate such specific risks.
2. Predictive analytics
A step forward from descriptive models, AML predictive analytics estimates what is likely to happen next. Models use historical signals to forecast the probability of future events, such as the chance an account will produce a suspicious activity report. These analytics usually use statistical analysis of historical data and machine-learning methods to reach a conclusion. These findings help AML teams align monitoring intensity with genuine exposure rather than one-size thresholds.
3. Prescriptive analytics
These analytics enter the next domain, recommending what to do. Tools combine predictions with constraints and objectives to suggest actions such as escalate, apply enhanced due diligence, throttle limits, or hold a payment.
Constraints here mean not only statistically the next best step, but one that is also practical and compliant. This helps AML compliance teams choose an optimal next step. IBM characterizes prescriptive analytics as determining the best course of action given predictions and goals.
These three modes work as a continuum in AML compliance. Descriptive builds understanding, predictive adds foresight, and prescriptive turns foresight into decisions.
Why Legacy Systems Burnout Your Productivity and Resources?
Legacy programs depend on static rules and fixed thresholds. That design catches known patterns and sanctioned names but fails to handle clever behavior changes, multi-hop layering (sequential transfers between accounts, countries, currencies, asset types), coordinated networks, and crypto-to-fiat flows. These systems generate large alert volumes, which consume review capacity while still missing novel typologies. On the contrary, a data-driven AML program reduces noise and brings context forward—who transacted with whom, through which intermediaries, with what velocity, and how that compares to peers.
Key Methods and Technologies Used for FinCrime AML Analytics
1. Network and graph analytics
Money laundering is a social thing thriving on complex and distant connections between criminal origins and its beneficiaries. Funds move through webs of related entities, sometimes disguised as ordinary commerce.
Graph analysis maps relationships among accounts, directors, addresses, devices, and counterparties to reveal clusters, hubs, and cycles that align with typologies such as round-tripping or funnel accounts. Visual network views help investigators move past isolated transactions and focus on connected risk.
2. Machine learning
Machine learning (ML) is a technique where computers learn to program themselves by training on large amounts of data. The data can be in any form, like numbers, text, or pictures, or even a higher level like customer activity and patterns in transactions. ML models learn what “normal” looks like for each customer segment and spot individuals deviating from it with context.
This analysis then helps in capturing behavior-aware signals, for example, abnormal transaction value spikes, sudden corridor shifts, or counterparties that rarely interact with the segment in question. The ML-based risk scoring engine then combines those various weak signals into a stronger indicator.
3. Blockchain analytics
Almost every crypto transaction leaves a permanent trace on a public blockchain. Though the data is public, it’s pseudonymous and can’t be linked to a real-world entity just by looking at a blockchain transaction. This is the reason on-chain analysis is required.
Advanced blockchain analytics in the AML cluster related to wallet addresses and linking them to known real individuals, entities, mixers, or exchanges. Analysis traces hops to highlight exposure to mixers, ransomware affiliates, darknet markets, or sanctioned infrastructure. When a fiat currency is converted to crypto or vice versa, blockchain analysis provides teams with a unified view.
4. Natural language processing (NLP)
The text that seems plain and unstructured can provide valuable insights into risk signals. NLP turns adverse media, court filings, regulator notices, and SAR narratives into structured features. NLP tools help fincrime analysts to track name variants, extract entities, assign sentiment or severity, and feed those signals into ongoing risk reviews.
5. Statistical and behavioral modeling
Clustering, regression, and time-series methods segment populations, identify outliers, and track drifts. Peer-group analytics provide a fair baseline, so an alert reflects genuine deviation rather than ordinary business for a given cohort.
No single technique solves AML challenges on its own. The best way is to combine different techniques and tune them according to a firm’s risk exposure based on its products, customers, and jurisdictions, etc.
Therefore, selecting the right AML analytics software or AML analytics tool is critical. The chosen system should integrate with existing onboarding, screening, and case management platforms.
What are the core components of an AML analytics software?
The anti-money laundering analytics use different techniques and serve different objectives, but the underlying architecture is built on some common components:
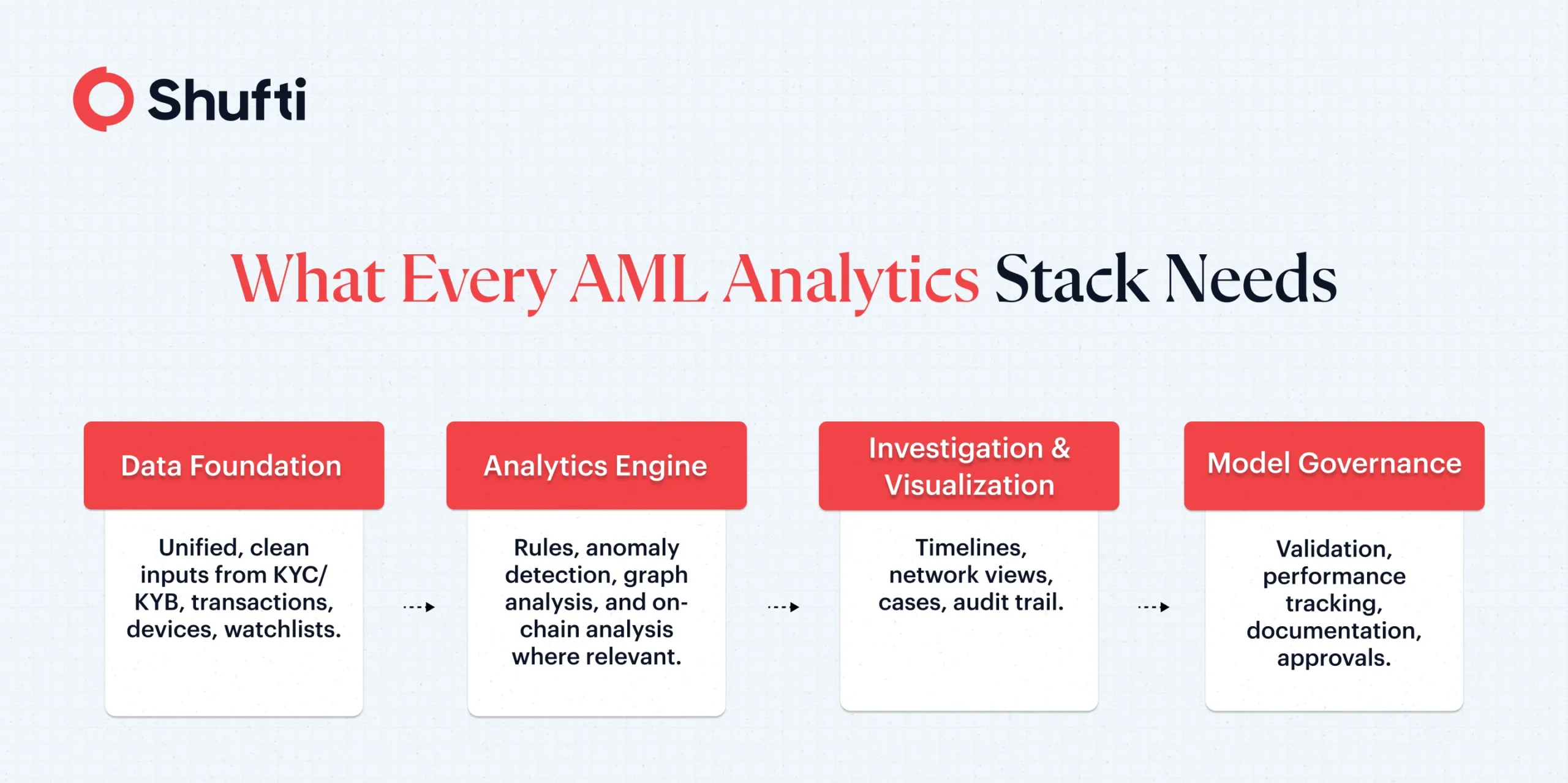
Data foundation
Data is a prerequisite, but good data provides a strong foundation for any analytics tool. Most tools need unified, clean data from transactions, Know Your Customer (KYC), Know Your Business (KYB), devices, payments metadata, watchlists, and open sources.
Analytics engine
This is the layer that decides the underlying technique to be used in analysis. This could be an engine with rules for known patterns, prediction & anomalies detection models, AML graph analytics, or blockchain analytics, where applicable.
Investigation & visualization
These components are necessary for conducting and managing investigations. It includes dashboards, network maps, risk timelines, and case workflows that reduce triage time.
Model governance
It is mostly the implementation layer that sets clear goals and defined responsibilities for management and employees. This includes model validation techniques, performance tracking, bias testing, documentation, and clear approval paths. FATF stresses that technology adoption should be within sound governance so programs remain explainable and ready for regulatory audit.
What do authorities think about AML CFT Analytics?
FATF, the standard setter, calls the risk-based approach “central” and has published guidance on the opportunities and challenges of new technologies for AML/CFT. That guidance encourages adoption of technology where controls, transparency, and accountability are strong.
- FinCEN (USA): The agency launched an Innovation Initiative and Innovation Hours to engage with AML technology, understand what tech is already available, identify implementation challenges, provide guidance, and facilitate responsible testing under the Bank Secrecy Act framework.
- FCA (UK): The FCA has run AML and financial crime TechSprints and published research showing machine learning’s growing role in AML and fraud detection within UK financial services.
- Wolfsberg Group: The industry body’s principles emphasize good governance, transparency, and risk-based controls, concepts that map well to analytics-driven programs.
One common theme in all these regulatory initiatives is that more intelligent detection with stronger governance performs far better with the same thresholds.
How AML compliance analytics benefit Financial Institutions?
AML data analytics help financial institutions achieve high true-positive rates, thereby speeding up investigations and review processes. This frees up resources that would be consumed in reviewing false positives. Available resources can then focus on areas where risk actually exists, resulting in timely and faster decisions. Speedier decisions minimize customer drop-offs due to unnecessary or delayed reviews. Thus, AML analytics not only protects FIs from fraud risks and compliance failures but also contributes to revenue generation.
How Shufti Supports AML Analytics and the Risk-Based Approach?
The performance of any AML analytics tool relies heavily on the data input it receives. Shufti’s IDV suite not only provides that strong data foundation but also establishes ground trust by linking each data point to a verified identity.
Risk signals don’t end at transaction details. Shufti captures device fingerprinting attributes such as IP, OS, browser, and hardware, as well as geolocation, which form the basis of link/graph analytics.
Analytics tools need all customer context in one place. Shufti’s REST API lets teams pull identity, KYB, and transaction verification or monitoring data through a single endpoint, so models and rules can correlate events without stitching multiple feeds.
Analytics still require human decisions. Shufti’s back-office provides a case management portal with dashboards and customer records that consolidate verification outcomes and screening results, giving investigators a complete view.
These capabilities support risk-based AML programs encouraged by regulators, as well as AML CFT analytics that operate on explainability and governance principles.
Businesses seeking to use AML analytics and move toward intelligence-led compliance can book a demo to see how Shufti’s platform supports analytics that enable risk-based AML compliance.