Reusable Identity: The Future of Secure and Seamless Digital Verification

- 01 What is Reusable Identity?
- 02 How Reusable Digital Identity Systems Work?
- 03 Why Organizations Need a Reusable Identity Framework?
- 04 Real World adoption of Reusable Digital Identity
- 05 Challenges & Considerations in Reusable Identity Adoption
- 06 Reusable Digital Identity and the Future of Traditional Verification Methods
Digital interactions now shape almost every aspect of modern life, from opening a bank account to availing government services, travelling, shopping online, and proving one’s age or eligibility for certain services. As these interactions grow exponentially, so does the demand for accurate, secure, quick, and privacy-conscious identity verification. Repetitive onboarding processes, recurring document submissions, and traditional verification systems no longer meet the needs of today’s digital-first world.
This is where Reusable Identity emerges as a new approach to identity verification, creating a trusted infrastructure for digital interactions. Instead of verifying individuals repeatedly across various platforms for different purposes, a reusable digital ID allows the reuse of a previously verified identity on multiple occasions. Businesses, governments, and consumers benefit from reusable identity because it reduces identity because it reduces repetitive, lengthy onboarding journeys. Reusable Identity achieves faster verification, lower risk, and stronger privacy protection.
What is Reusable Identity?
Reusable identity is a portable digital identity credential that is verified once through traditional ID documents and can be securely reused across various services or platforms that require Identity Verification, such as fintech, crypto firms, or iGaming. Unlike traditional verification, which requires individuals to re-upload documents, repeat biometric checks, or undergo multiple Know Your Customer (KYC) assessments while onboarding themselves, reusable identity enables a single, trusted identity to be shared without friction.
With reusable identity, users only need to share the information that is required. For example, in order to verify their age, the user can show whether or not they are above a certain age threshold, without sharing their actual date of birth. Therefore, reusable identity not only mitigates the repetitive and prolonged onboarding process but also addresses the privacy concerns that often come with identity document verification.
A reusable identity comprises three core roles:
- Issuer: The institution that verifies the identity for the first time and issues the digital credentials that can not be forged (e.g., a government authority or IDV provider).
- Holder: The user who stores and shares the required information upon request. The credentials are stored in a digital identity wallet (in their mobile app).
- Verifier: Any platform or business that is obligated to verify the identity for various purposes (fraud prevention, legal obligation, etc) confirms the reusable identity to ensure its accuracy and checks for alteration after being issued by the IDV provider. Verifiers may also need to confirm whether the reusable identity belongs to the person using it for identification, in sensitive or high-assurance cases.
This framework ensures that the digital ID is portable, meaning the user, not the provider, controls how it is shared. With these verifiable cryptographic credentials stored in a secure digital wallet owned directly by the users, individuals can provide only what is necessary, supporting both privacy as well as compliance.
How Reusable Digital Identity Systems Work?
Step 1: Initial Identity Verification
The first step begins with a one-time identity check, which typically includes traditional document verification, facial biometrics, and liveness detection. This first step establishes trust. The verified identity is then cryptographically signed to ensure authenticity and tamper-resistance.
Step 2: Issuance of the Digital Reusable Identity
Once the traditional ID documents are verified, the credentials are issued to the user’s digital identity wallet. Only the user has control over how and when these credentials are shared. These credentials are cryptographically signed and fail the verification process if they are altered, ensuring accuracy and speed altogether.
Step 3: Reusing the Credential Across Multiple Services
After issuance of a reusable identity, the digital credential can be reused instantly across various platforms, banks, e-commerce, travel portals, and government services, without repeating the full onboarding flow. However, in high assurance cases user may have to go through traditional biometric verification, like liveness detection, to confirm that he/she is the same person whose identity was verified. Reusable identity allows users to verify their identity both online and offline. This enables frictionless authentication even in low-connectivity environments.

Why Organizations Need a Reusable Identity Framework?
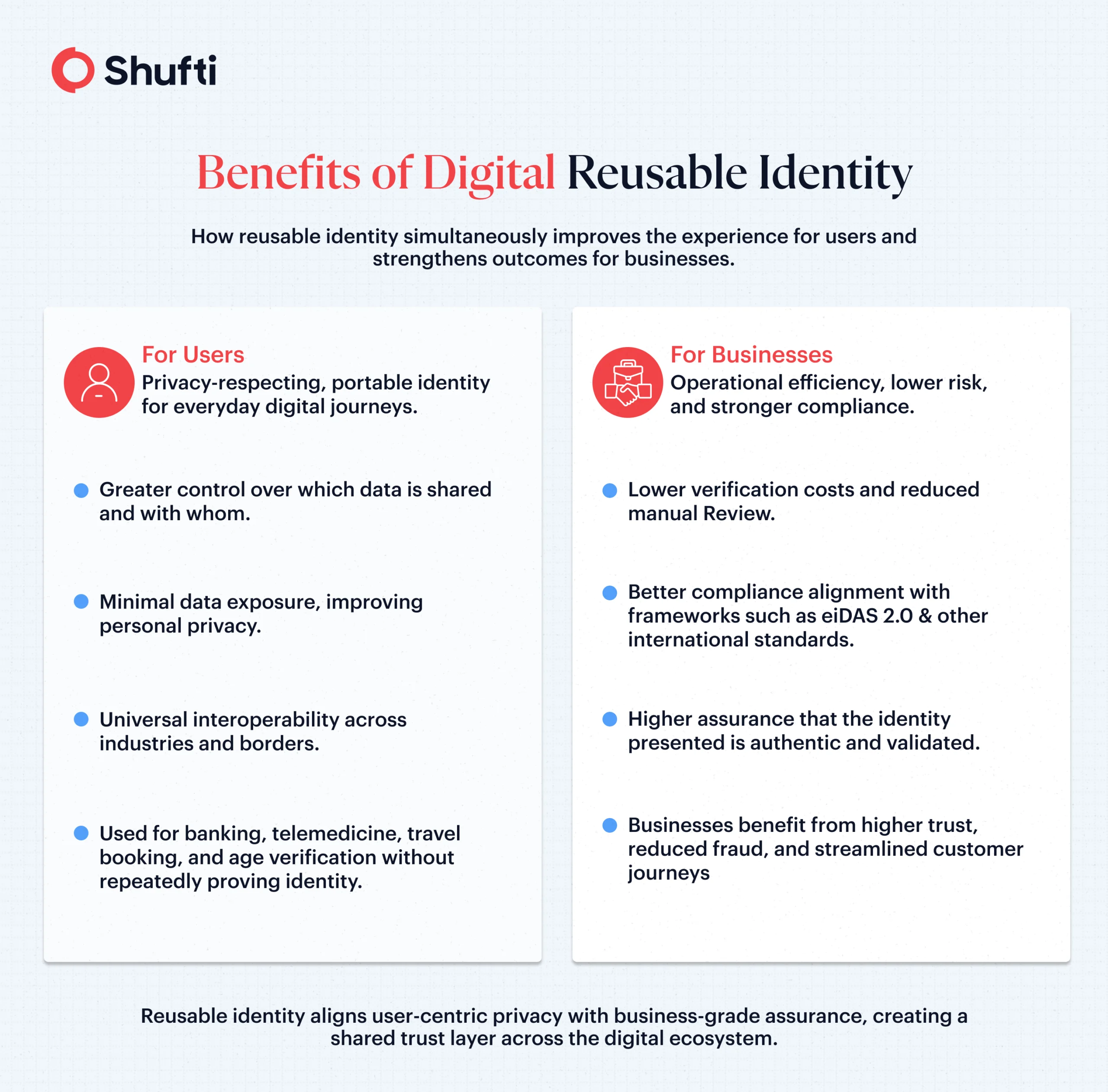
Data Security & Privacy Benefits
For businesses that require identity verification, a reusable identity framework minimizes the need to store sensitive user data, significantly reducing the impact of data breaches. This builds trust between businesses and consumers as the user’s skepticism regarding data sharing is addressed in real time. With fewer documents on file, reusable identity not only excludes the possibility of data theft but also ensures compliance with regulatory obligations under laws like GDPR and emerging digital identity directives.
Faster Customer Onboarding
Reusable identity transforms verification from a slow, repetitive process into an instant, low-friction step. If the onboarding process seems intrusive and slow, users are more likely to abandon the process altogether. Faster onboarding, on the other hand, means higher conversion rates, user satisfaction, and fewer drop-offs.
Fraud Reduction & Improved Assurance
Cryptographic signatures and tamper-evident credentials strengthen identity assurance far beyond traditional verification methods. Identity reuse makes it harder for fraudsters to submit fabricated identities repeatedly across various platforms, eventually reducing fraud and enhancing trust.
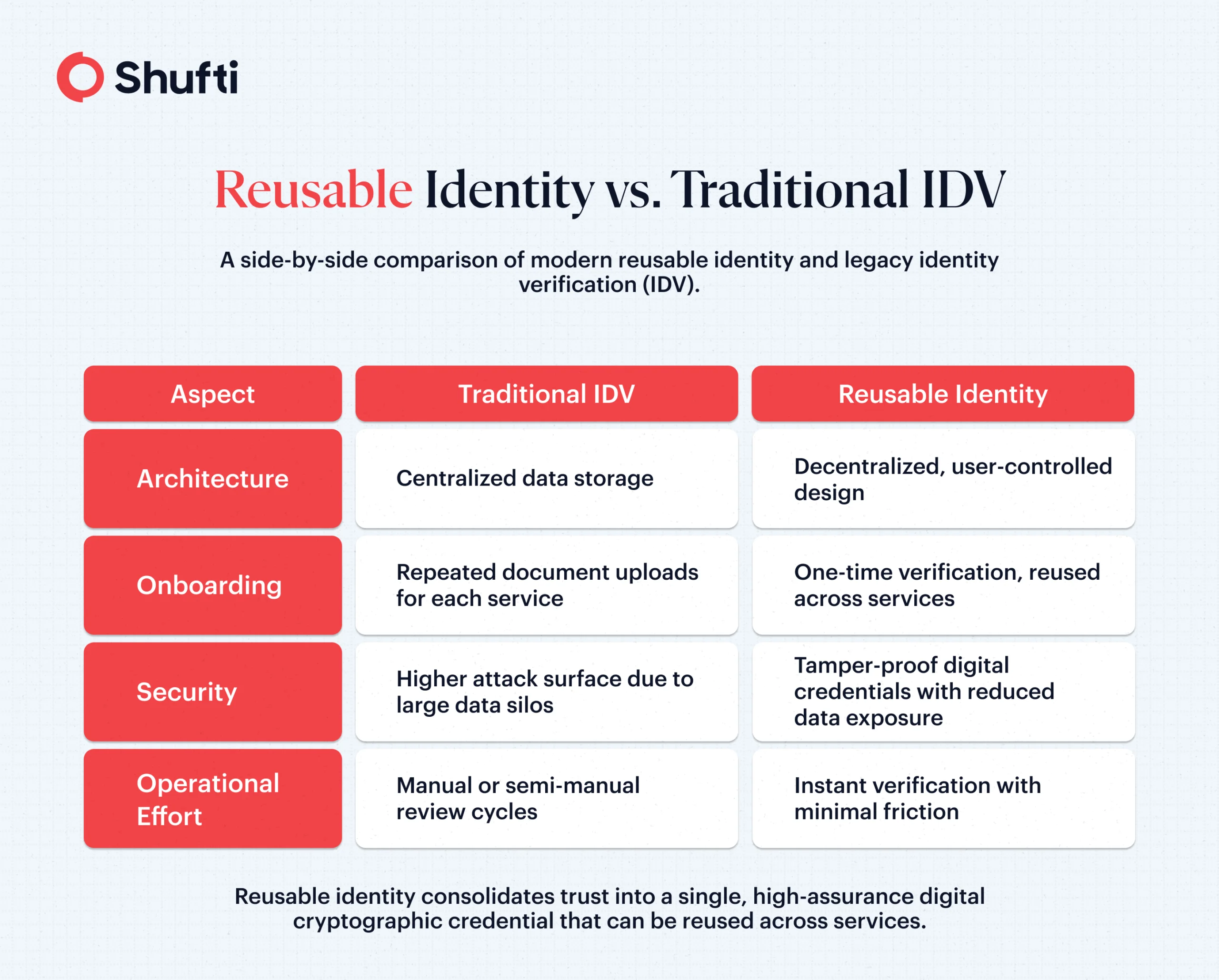
Reusable identity does not replace traditional identity verification. It works alongside existing processes and complements them. Users still undergo an initial verification process through traditional identity documents and biometrics; once this high-assurance check is complete, they can reuse their verified digital credential wherever identity verification is required, be it a fintech or a crypto platform. The integration of traditional identity documents and reusable ID reduces operational load while, at the same time, delivering a stronger, more modern security model that aligns with today’s digital-first world.
Real World adoption of Reusable Digital Identity
Reusable identity is not theoretical; it is already being deployed globally, as it addresses the concerns of users and regulators while at the same time easing the process for businesses as well.
- EU’s EUDI Wallet: Under the eIDAS 2.0 regulation, Europe is building a continent-wide digital identity wallet allowing users to access services across the European Union with verifiable cryptographically signed credentials.
- Singapore’s Singpass: Singapore’s Singpass is a reusable digital identity that allows citizens to access more than 2,000 government and private sector services.
These examples demonstrate increasing trust across both private and public sectors.
Challenges & Considerations in Reusable Identity Adoption
Reusable identity benefits users, businesses, and regulators; however, several practical challenges need attention to fully realize these benefits. Addressing these challenges is necessary for a seamless verification process. Interoperability across various sectors relies on consistent use of shared standards, particularly Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs). Without this standardization, reusable identity risks becoming fragmented and losing much of its value.
User education is equally important for an efficient verification process. Individuals must have an understanding of how to manage, secure, and selectively share their digital identification wallet. At the same time, the ecosystem, issuers, verifiers, and wallet providers must be ready with secure, compatible integrations that support end-to-end trust. These challenges are not blockers but natural steps in the maturation of the reusable identity landscape.
Reusable Digital Identity and the Future of Traditional Verification Methods
Reusable Identity marks a fundamental shift in how digital identity is created, managed, and reused. It allows faster onboarding, stronger security, improved privacy, and a smooth user experience flow. Instead of replacing traditional IDV outright, reusable identity enhances it, creating a comprehensive verification ecosystem that benefits not only the individual users but also the organizations.
Organizations now actively look for ways to reduce repetitive KYC checks, protect user privacy, and benefit from emerging digital identity frameworks. Shufti supports these goals with its Fast ID verification solutions that can form the foundation of reusable identity models while meeting global compliance expectations.
To discuss implementation options for reusable identity and modern verification, request a demo with Shufti’s team.