Biometric Facial Recognition – Combating Identity Fraud with Shufti’s IDV Solution

Since knowledge-based authentication and passwords were first introduced, security systems in banks and financial institutions have seen significant advancements. A far more dependable technology is always required due to the increased risks of cybercrime, evolving data protection laws, and corporate policies. The best method for data security available today is biometric authentication.
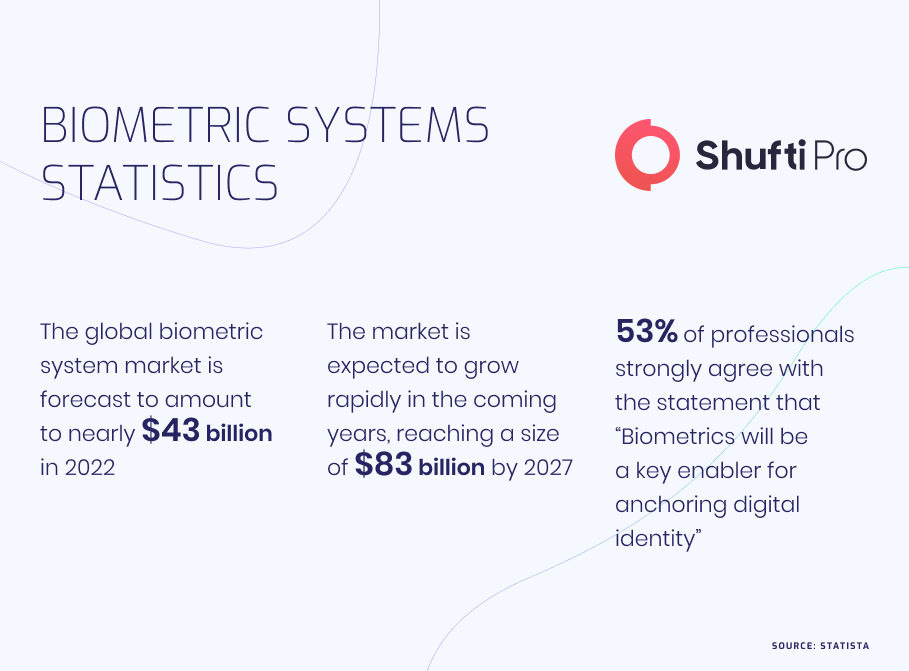
Biometrics used to be considered science fiction a few decades ago, but they are now a common security tool. According to a Visa survey, 46% of consumers say that biometric verification is safer than using passwords or PINs, while 70% of consumers think it is simpler.
Tricks to Evade Identity Verification Measures
The oldest method for defeating biometric authentication tests is to wear a mask. Sophisticated technology is now used by thieves to forge their identities and bypass identity verification checks. The most recent method adopted by scammers is to edit audio and video files with material to justify their fake identities. Fraudsters employ deep learning techniques to create fake videos showing the facial features of another person.
Fraudsters use a variety of sophisticated techniques for spoofing in addition to the usage of face masks and glasses. Getting someone’s photo and exploiting it for illicit purposes is not a problem in the present world. They manipulate images with technology and utilize them for getting through biometric identity verification.
By creating a 2D mask using advanced automated printing or purchasing a 3D mask for a few euros, imposters build a facial artifact. In more sophisticated spoof attacks, con artists check the image on the ID document during biometric verification using masks of real people’s faces. Some methods used to detect such spoof attacks include asking the end-user to move their face, eyes, and grin.
Deepfakes
Deepfakes, in addition to 2D and 3D face masks, are a growing threat to banks and financial institutions. Video and audio files are edited by imposters to suit their illicit purposes and gain unauthorized access to the accounts of legitimate customers. Changing the background or words in a film, for example, can make the demands for information or money seem genuine. Scammers employ deepfakes as they are aware that businesses have created reliable authentication procedures to protect their clients’ accounts.
Use Cases of Biometric Facial Recognition
Security, authentication (identification and verification), and analysis are the current three main applications of biometric facial recognition technology in businesses and financial institutions.
Criminal judicial institutions throughout the world use biometric facial recognition technology. Facial recognition technology is widely adopted in China and the UK, where it is used to track down fugitives and identify criminals. In order to reunite missing adults and children with their families, it is also being used to locate them using both private and public surveillance cameras. Biometric facial recognition is also being used to search through millions of internet advertisements for victims to combat human trafficking.
Biometric facial recognition technology is demonstrating its value as a great tool for preventing fraud and aiding banks, investment firms, and the insurance sector in rooting out criminals. Customers who submitted fake photos in the past to commit fraud now have to bypass biometric checks which are trickier to pull off.
The applications for biometric facial recognition technology in e-commerce are virtually limitless. In order to enhance their service, KFC Beijing has been experimenting with one use of the technology. Customers’ orders are stored in the system along with a biometric record of their faces. The system recognizes the customer’s face and proposes their previous order during their subsequent visit.
It’s a similar case with AliPay, where facial recognition technology is being used to replace traditional payment methods. The world’s first system for accepting payments through facial recognition has already been launched by AliPay. This improves customer service by speeding up the payment process and introducing an additional degree of protection.
The technique is being applied globally in the transportation industry to reduce client wait times. For instance, to shorten check-in lines, Delta Air Lines is testing facial recognition scanners in airports. China is making efforts to adopt facial recognition to shorten the waiting times in subway lines like in the rest of the world. A similar pilot operation is being carried out in train stations in Germany.
Biometric facial recognition is also being used in the healthcare sector to implement a variety of ground-breaking innovations. Software for face comparison is used for sentiment analysis and patient monitoring. This aids medical personnel in figuring out whether patients are at ease and whether they require pain medication. Fascinating use of the technology is the detection of uncommon genetic diseases like Cornelia de Lange syndrome and Angelman syndrome. The healthcare sector, like the financial sector, is using biometric facial technology as a fraud protection strategy.
Why Businesses Should Adopt Biometric IDV
More than 65% of consumers, according to a poll, are familiar with biometrics. Particularly when it comes to facial recognition technology, the majority of individuals are now accustomed to the process. Customers don’t have to put much effort into completing the biometric authentication process; all they need to do is briefly hold still for the webcam or camera on their smartphone. In this way, biometric facial recognition can improve user experience if you incorporate it into your business.
While no technology in use today is completely secure from fraudsters, biometrics is a hard technique to defeat. Adding spoofing and liveness checks makes the procedure considerably more difficult than acquiring a password, which discourages fraudsters.
Passwords continue to be the most used authentication technique, however, they are susceptible to a variety of cyberattacks, like phishing. According to the Verizon Data Breach Investigations Report, stolen and/or weak passwords were used in 81 percent of hacking-related breaches. The use of a document, token, or other similar device is required in order to gain access in other techniques like document and token authentication. If a person loses their token or document, this sort of authentication creates usability issues and leaves room for fraud.
Knowledge-based authentication, however, is considered riskier. Common inquiries are made, including the client’s mother’s maiden name or the name of their pet as a young child. According to reports, many individuals indiscriminately post the answers to these questions on social media.
What Shufti Offers
Verifying that customers are who they say they are has never been more crucial in a world where online fraud and digital hacks are on the rise. Fortunately, improvements in facial recognition technology now make biometric identification and authentication much faster. This entails KYC/AML procedures that make use of biometrics and are the most accurate and one of the fastest solutions to onboard legitimate customers.
By utilizing Shufti’s online identity verification solution, your business has the opportunity to implement biometric facial recognition technology and improve your identity verification procedures.
Want to learn more about biometric facial recognition for your business?

 Explore Now
Explore Now













