Identity Verification: A Bulletproof Vest Against Sharing Economy Fraud

Over the previous year, you might have observed how the world has become increasingly dependent on the concept of a “Sharing Economy”. Whether we had food delivered at our doorstep, rented a hut in the hills for a staycation, or ordered a cab through a ride-hailing app, the trend is here to stay. While the journey of this economy has been impressive so far, the path had its share of twists and turns.
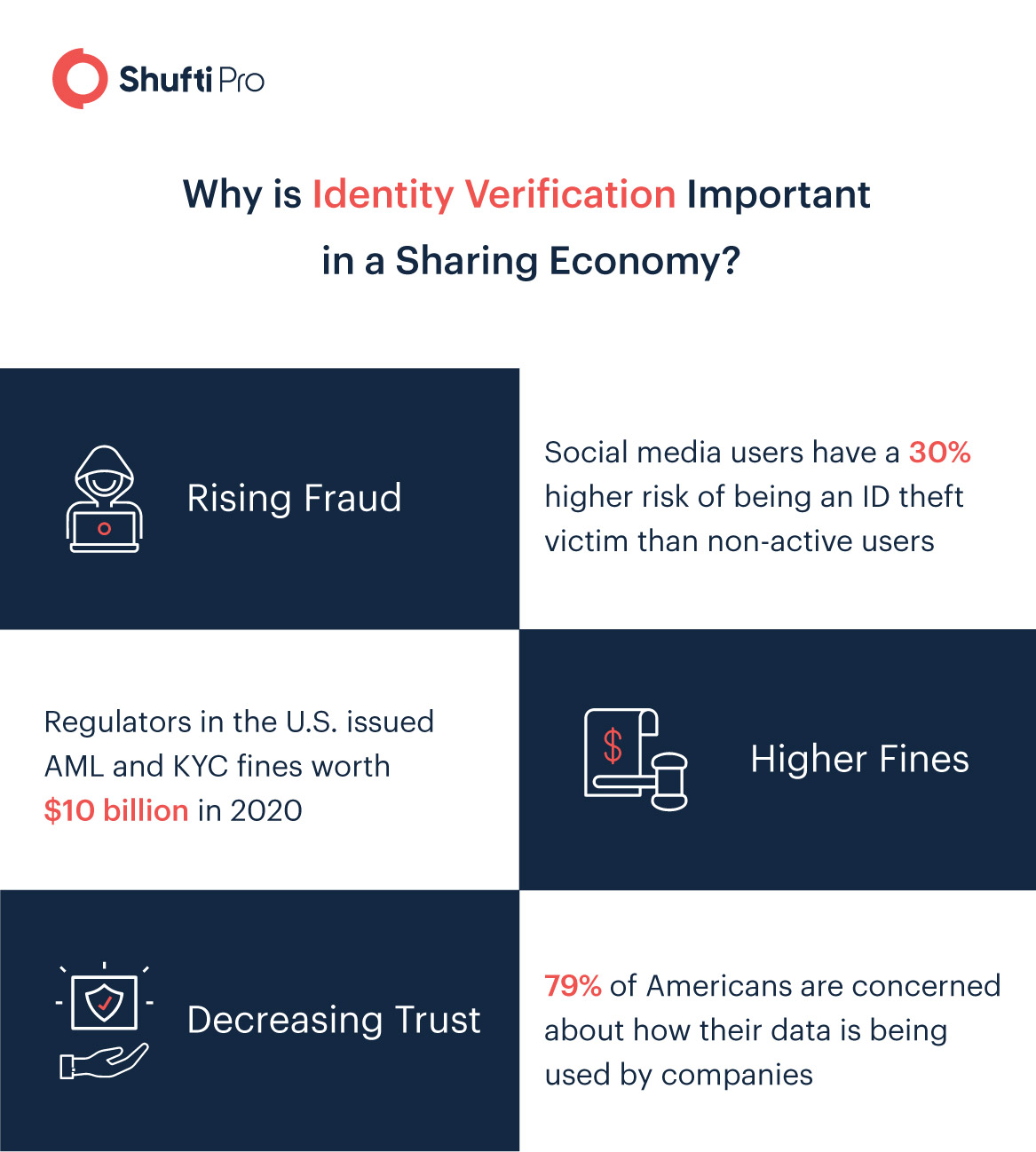
The impact of identity theft, fraud, and regulatory fines resulting from strangers with an unverified identity and accounts cannot be left unnoticed. With identity fraud losses reaching an all-time high of USD 43 billion in 2020, sharing economy companies that fail to implement identity verification on their users are in for a bumpy ride in the upcoming years.
What is a Sharing Economy?
An economic model based on the concept of sharing assets by collaborating over the internet. Instead of hiring employees to produce and sell products, it involves:
- Communication between self-employed interested parties
- Over the web (through social media or an application)
- For the purchase of goods and services (such as a cab or a place to stay)
The sharing economy is synonymous with the terms peer-to-peer economy and collaborative economy. While activities such as rides, accommodation, and talent sharing plummeted in 2020, so did the demand for home-delivered groceries, products, and coworking spaces. As this trend continues to disrupt the way we live, work, and consume, the shared economy industry is estimated to reach a value of USD 335 billion by 2025.
Addressing the Sharing Economy Challenges
With millions of individuals using collaborative services like Airbnb, Lyft, Upwork, etc. today, the sharing economy model has undoubtedly brought convenience into our lives. However, this does not indicate that the sector is immune to any barriers. Although the industry continues to thrive, three major challenges that are emerging include:
1. Manual Onboarding – A Thing of the Past
To perform identity verification during onboarding, companies previously relied on manual identity checks. This included asking users to provide an identity document as proof of address or obtaining an ID card or passport. Sharing economy startups have now realized that these methods of identity verification are no longer sufficient, as they are time-consuming, frustrating, error-prone, and provide poor customer experiences. Therefore, for this model to sustain, an automated identity verification process has to replace the conventional outdated method.
2. Stranger Danger
A major issue that lies at the center of the sharing economy model revolves around the identity of the service provider. After all, why would you allow a stranger into your house or allow them to get in your car when you’re unaware of their true identity?
As the future of this industry depends on robust security measures, accurate identity verification is crucial. At the end of the day, it’s all about knowing who your driver is, that the masseur coming to your house is actually who they claim to be, and whether the apartment you’re renting actually belongs to the owner or not.
3. Identity Theft
Unfortunately, numerous sharing economy platforms are poorly equipped with identity verification technologies to win the battle against frauds such as identity theft. In the U.S., only 24.3% of sharing economy service users are asked to prove their identity when signing up for a new platform. Apart from this, 71.5% of users are simply asked to provide a valid email ID address for identity verification. Although this brings convenience and encourages consumers to sign up with the platform, it also makes it incredibly easy for criminals to pose themselves as legitimate customers.
On the other hand, without a strong security and check mechanism in place, fraudsters can carry out phishing attempts and cyberattacks to steal customer data. This not only leads to devastating consequences for customers but causes reputational damage to the brand as well.
How Identity Verification Removes these Barriers
Identity verification solutions, powered by artificial intelligence models, have the ability to significantly minimize most of the issues that prevail in the sharing economy sector. Since trust and safety are central to the success of this industry, the adoption of an identity verification solution has become essential. Listed below are the major benefits of utilizing such software for the sharing economy industry.
1. Fraud Detection
With the help of an AI-powered identity verification solution, companies can safeguard sensitive customer data and eliminate the risk of fraud. During the onboarding process, users can be identified not just through their ID documents, but also through a selfie. Since biometric information is nearly impossible to replicate, identity thieves can be easily filtered out.
2. Enhanced Security, Confidence, and Trust
Identity verification protocols allow companies to strengthen their security mechanisms. The relentless threat of identity thefts and cyberattacks can be kept at bay, as IDV solutions can detect fake documents and fraudulent players within seconds. Consequently, it helps create a transparent relationship between the service provider and the customer, built on the foundations of confidence and trust.
3. Swift Customer Onboarding
Customers are the key assets of a company. Acquiring them, however, is not always an easy task. Without a rapid verification process during the initial account opening stage, companies can risk losing clients. When advanced identity verification solutions are utilized, users can be validated within seconds, thus improving the efficiency and speed of the entire process.
4. KYC and AML Compliance
Firms that fall in the sharing economy sector are mandated by global regulatory authorities to comply with Know Your Customer (KYC) and Anti-money Laundering (AML) standards. Identity verification can be efficiently utilized during the KYC process for customer identity verification. For AML compliance, customers are automatically verified by scanning their ID details against criminal watch-lists, Politically Exposed Person (PEP) lists, global sanctions, and adverse media stories.
Key Takeaways
- The sharing economy model offers a plethora of advantages for today’s consumers
- As the communication channel is online, fraudsters pose a great threat to the industry
- With a proper identity verification system in place, users can be verified with greater accuracy and criminals can be weeded out
- Such mechanisms lead to timely fraud detection, enhanced security checks, transparency between customers and service providers, and compliance with KYC/AML regulations

 Explore Now
Explore Now













