Replay Attacks – Another Rising Threat for Businesses in 2021

As technology advances, more and more solutions are available for making lives convenient. Unfortunately, fraudsters are using technology for their malicious intents as well. Given the rise in the use of technology, various types of frauds have emerged. Identity theft, account takeover, spoof attacks, and deep fakes were already causing a lot of trouble for businesses. In 2020, a new fraud has emerged by the name “replay attacks.”
According to a report from Comparitech, 80.7 per cent of the surveyed organisations experienced successful cyberattack.
Replay attacks were not very common in the past few years. However, the coronavirus pandemic locked everybody in and fraudsters found it a great opportunity to attack organisations with a fraud they were not prepared for. Businesses have lost a lot of money to replay attacks this year and we are predicting that this fraud will increase in 2021. The corporate sector must prepare themselves for replay attacks and take necessary measures to prevent them. Read this blog to know everything about replay attacks.
What is a Replay Attack?
Replay attacks refer to false information provided by one customer multiple times in different forms. For instance, a fraudster submits the same identity document every time for verification but with one or two details changed. In the digital world, these attacks are more sophisticated and hard to trace.
How Do Replay Attacks Work?
With rapid digitisation. Replay attacks have taken the virtual road as well. Digital replay attacks are extremely sophisticated because there are different methods of perpetrating the attack. The different methods target a wide range of devices and networks. Here are the three main ways through which a replay attack occurs.
Changing the Device Information
In the virtual world, tracing the IP of the device is not a problem anymore. This means fraudsters can be easily detected when submitting the same information over and over again. For a successful replay attack, criminals change the device information like IP address to make sure they are not being tracked. They might use a different device or mask their IPs when doing so.
Different Network Information
This is the second way of successful replay attacks. Using the same network can help organisations to identify replay attacks in no time. To stay hidden, fraudsters use different network information like a different internet connection or mobile data for submitting the same data multiple times.
Fraudulent Information for ID Verification
As stated earlier, fraudsters change a piece of information in the documents to perpetrate a replay attack. For instance, once a fraudster changes the date of birth and the next time, he uses a different name and submits the same document.
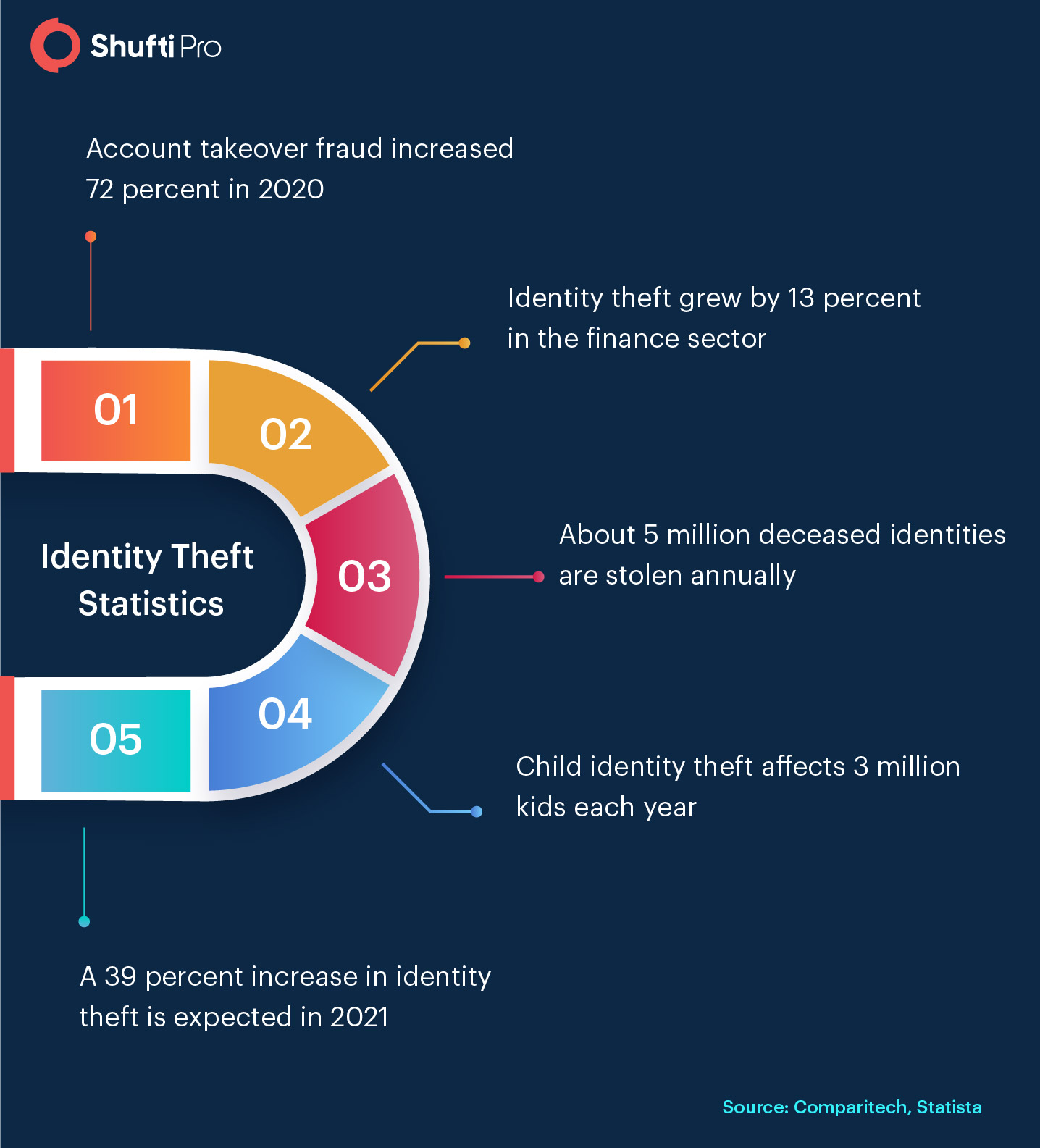
How to Combat Replay Attacks?
Successful replay attacks result in account takeover fraud and identity theft. Since digital replay attacks are an emerging threat for businesses in 2021, there is a dire need for a solution that can combat them. Fortunately, not one but there are various solutions that can secure your business from replay attacks. Take a look at some of these solutions.
Track Customers’ Response Time
First, be sure to track the time your customers take to respond. Legitimate en-users only take a few seconds to upload a selfie or government-issued ID documents. On the contrary, perpetrating a replay attack requires time. Fraudsters require some time to change details within the same document. If your customer is taking a lot of time to respond, perform more robust checks on the documents previously submitted. You can opt for a face verification check as well or video KYC can be an all-in-one solution.
Geolocation Assessment
As mentioned earlier, fraudsters use different location details for replay attacks. With the help of geolocation assessment, you can trace the location that is being used during verification. In case the customer jumps to several different locations within the same verification session, might have a replay attack in the pipeline.
Biometric Authentication
Performing biometric authentication checks is one of the ideal ways to combat replay attacks. You can perform face verification checks or other liveness detection checks to ensure that the user is physically present at the time of verification rather than a fraudster planning spoof or replay attacks on the other end. For better security, you can add extra biometric checks to bring friction in the fraudsters’ processes.
Wrapping It Up
To sum up, replay attacks are an emerging threat for businesses. Due to the pandemic, cybercrime ratio has significantly increased and the year 2021 can expect new kinds of frauds as well. Replay attacks are one of such crimes that businesses can expect in 2021 and businesses need robust solutions to combat them. Geolocation assessment, time tracking, and biometric authentication are few of the best ways to identify replay attacks and combat them before they become a problem for your business.
Get in touch with our experts to know more about biometric checks.

 Explore Now
Explore Now