A Complete Guide To SMS Verification

- 01 What is SMS Verification?
- 02 How SMS Verification Works?
- 03 Why do Businesses Use SMS Text Verification?
- 04 What are the Strengths of SMS verification?
- 05 The Limitations in SMS Text Verification
- 06 Where Does Text Verification Fall?
- 07 How to decide what role SMS verification should play?
- 08 What are the alternatives to SMS Verification?
- 09 How Shufti can help institutions authenticate user identity?
There are multiple methods to authenticate users, each with its own strengths and challenges. Some of these methods are more user-friendly, but provide less authentication. Other methods, such as live selfies or biometric authentication, provide greater security but may create friction if not implemented proportionally.
So, where does SMS verification lie on this spectrum?
SMS verification lies on the user-friendly side of this scale, offering a straightforward process that provides a reasonable level of identity verification.
The type of authentication method you adopt is largely dictated by the specific IDV requirements of your businesses. Whether you’re an e-commerce website platform or a digital bank, this article covers everything you need to know about SMS text verification, how it works, the use-cases, and implementation strategies – so you can determine whether this method of authentication is helpful for your business.
What is SMS Verification?
SMS verification refers to a method whereby a unique SMS verification code, usually a six-digit number, is sent to a user’s mobile device for the confirmation of identity. Upon entering the correct number on the platform, the user’s identity is authenticated, and the action, such as a login or a transaction, is completed.
Primarily due to the widespread availability of mobile phone devices across the world, SMS verification is one of the most widely adopted methods for user authentication. It works on any phone with an active SIM card, with no additional requirements.
On many online platforms and services, from e-commerce to financial institutions, SMS verification is part of a broader system known as SMS authentication or SMS 2FA (two-factor authentication).
How SMS Verification Works?
The technical process begins when a user triggers a security-sensitive action such as creating an account, logging in, or completing a transaction. The system generates a unique one-time password (OTP) tied to that specific session. It sends this code by interfacing with mobile carriers via an SMS gateway or Application Programming Interface (API) to deliver the message to the user-provided phone number.
When the user enters the correct code on the platform within the stipulated time, the system validates it and grants the requested access or action. This flow supports a familiar user experience: input mobile number, receive code via SMS text verification service, and respond.
Yes, SMS verification really is that straightforward.
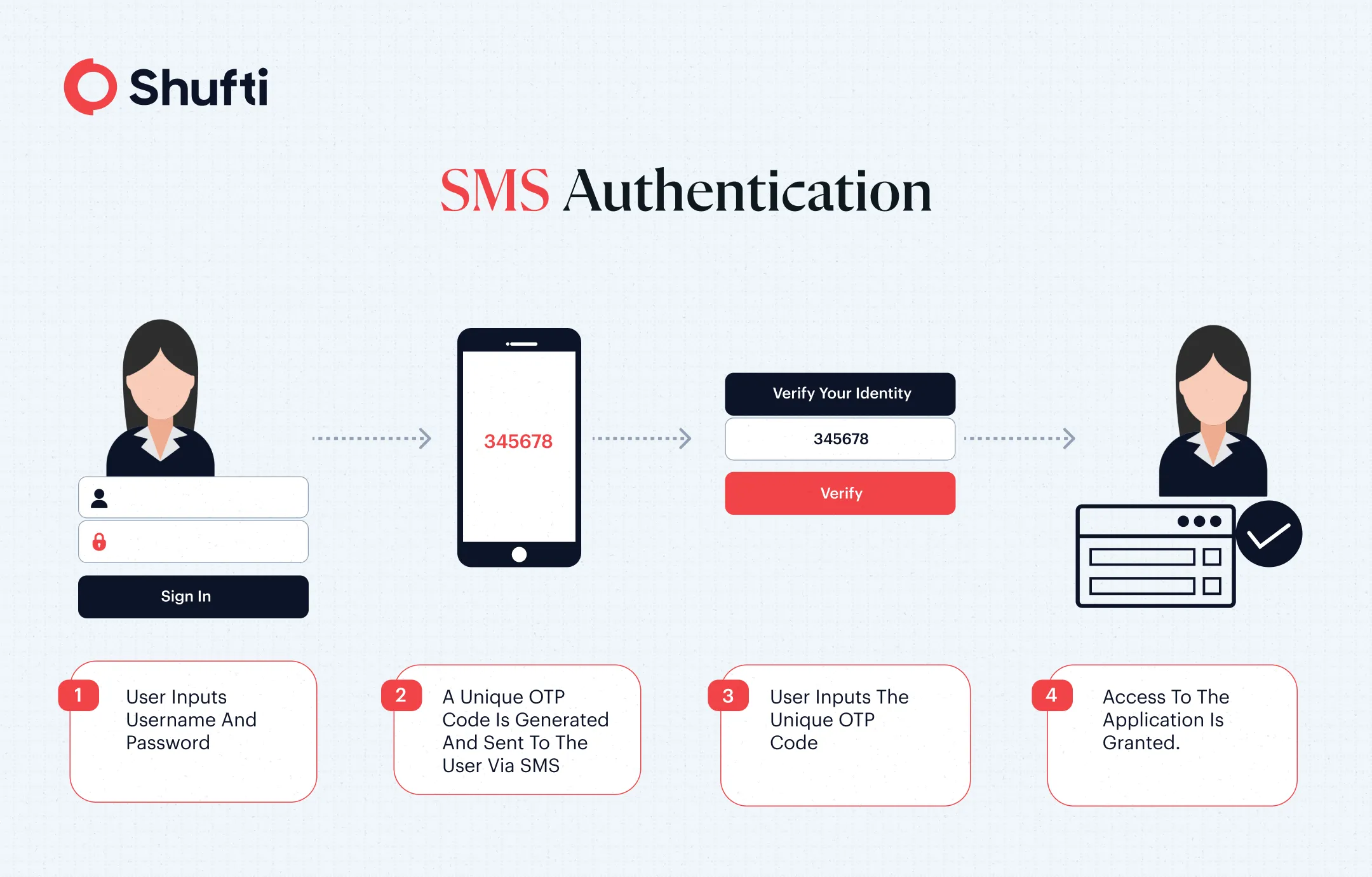
Why do Businesses Use SMS Text Verification?
Institutions use SMS text verification services because they balance ease of use with a practical improvement over password-only login. For many businesses, especially those with global audiences or varying levels of device sophistication, SMS is universal. Users do not need smartphones, additional apps, or the latest tech, and the behaviour of entering a code is already familiar from services such as banking, e-commerce, and account registration.
For customer onboarding, SMS authentication helps verify that a mobile number belongs to the user claiming it. This simple check reduces risks associated with fake accounts, bots, and credential stuffing attacks, where stolen passwords are replayed on other sites.
What are the Strengths of SMS verification?
SMS text verification remains widely used because:
- It is easy to implement with text verification service APIs and integrates quickly into existing user flows.
- It operates on virtually all mobile phones without requiring additional software.
- It significantly increases security compared with passwords alone, requiring access to both credentials and the physical device that receives the verification message.
- Delivery is often fast and reliable, even in regions with basic cellular coverage.
- It is a user-friendly account recovery method for users who have forgotten their login credentials.
These benefits explain why SMS verification service offerings continue to grow as part of multi-layered identity authentication processes in regulated sectors and platforms with large numbers of users.
The Limitations in SMS Text Verification
While SMS verification has proved to be a user-friendly identity authentication measure, it carries with it inherent weaknesses tied to the nature of text messaging and mobile networks:
-
Vulnerabilities in mobile networks:
The SMS service usually does not have end-to-end encryption. Data protocol vulnerabilities allow attackers to intercept messages, giving them direct access to any OTP code received on that mobile number.
-
SIM swapping and number hijacking risks:
Fraudsters can exploit mobile provider processes to transfer a victim’s number to a device they control. If they succeed, they receive the SMS verification code and can bypass authentication entirely.
| Did You Know?
The FBI Internet Crime Report of 2024 reported that a total of 982 complaints were made for SIM swapping, which caused a total loss of almost $26 million! That means a single SIM on average resulted in $26,460 per incident. |
-
Spoofing and Phishing Techniques:
Bad actors may manipulate individuals into sharing OTP codes through deceptive messages and emails. Usually, such fraudsters try to access the user’s sensitive personal information, such as account logins, by manipulating the user into believing that the OTP was actually sent by the fraudster. Consequently, users sometimes unknowingly share secure OTP codes directly with criminals.
-
Technical Flaws:
A technical standard that facilitates services like OTP codes by way of SMS messages can be exploited by hackers. Signalling System No.7 (SS7), the protocol used for SMS messages, is a flawed protocol that allows bad actors to intercept incoming messages, including OTP codes, directly.
These vulnerabilities highlight that while the user-friendly nature of SMS verification has rendered it extremely popular, it is not suitable for sensitive use cases. Indeed, the National Institute of Standards and Technology (NIST) has extensively listed the limitations of SMS verification in setting the standard for its cybersecurity framework.
Where Does Text Verification Fall?
SMS-based systems can struggle when a higher level of identity assurance is required. For example:
- High-value financial services may need stronger methods resistant to phishing and SIM attacks.
- Healthcare systems handling sensitive personal data may require authentication that meets stricter compliance requirements.
- Regulatory compliance regimes for Know Your Customer (KYC) verification demand multi-factor checks that combine document validation and biometrics with communication-based factors.
In these scenarios, relying solely on SMS 2FA or SMS authentication can leave gaps in risk coverage and expose systems to sophisticated attacks.
How to decide what role SMS verification should play?
The choice of whether to use SMS as primary authentication, secondary verification, or only at specific points in the flow depends on risk appetite and compliance needs. Lower-risk services with minimal regulatory oversight may rely on SMS alone for initial identity checks. Higher-risk environments will require combining the SMS verification service with stronger, cryptographically resistant factors.
Institutions considering SMS should evaluate threat models, regulatory obligations, user base demographics, and fraud risk profiles before adopting it as a core identity factor.
What are the alternatives to SMS Verification?
For businesses that require more secure identity authentication methods, there are multiple alternatives that provide credible identity verification.
-
Face Detection and Liveness Verification:
This method ensures that the individual attempting to authenticate their identity is physically present by detecting facial features and confirming the authenticity of the live image, preventing the use of photos or videos.
-
Fingerprint Biometrics:
This approach uses the unique patterns in a person’s fingerprint for authentication, offering a high level of security that is difficult to replicate or forge.
-
Document verification:
Users can upload government-issued identification or other official documents for document verification. The system checks for authenticity, including validating holograms, text, and other security features to ensure the document’s legitimacy.
-
Voice biometrics:
By analyzing unique voice patterns, this method authenticates a person’s identity based on how they speak, offering an additional layer of security for phone-based verifications.
These alternative methods provide more robust protection compared to SMS verification, especially for high-risk transactions and environments requiring enhanced identity assurance.
How Shufti can help institutions authenticate user identity?
Institutions facing the challenges of balancing user-friendliness with robust identity assurance benefit from adopting a layered verification framework that combines communication-based checks with stronger, compliance-aligned methods.
Shufti provides SMS verification as a part of its wider 2FA authentication and Multi-Factor Authentication solutions that are specifically engineered for Fintechs, banks, iGaming, and other regulated industries.
This approach enables institutions to trigger a one-time text verification step early in the onboarding process to confirm a user’s phone number, support anti-fraud checks, and reduce fake accounts without introducing undue friction.
Where higher identity assurance is required, Shufti’s platform can seamlessly integrate additional verification checks such as document authenticity scans and biometric matching. This ensures that when a phone number is confirmed via SMS code, it is complemented by deeper identity evidence compliant with KYC and AML expectations.
By combining SMS with stronger identity layers tailored to the organisation’s compliance needs, institutions can strike the right balance between user experience and risk management.
Request a demo to explore how Shufti’s identity verification ecosystem can improve onboarding outcomes and meet regulatory requirements.

 Explore Now
Explore Now