Initial Exchange Offerings (IEOs) – A Detailed Insight

The advent of the Crypto industry brought decentralized and innovative fundraising ways. One of them through Blockchain projects is Initial Coin Offerings (ICOs). Security tokens are like digital financial securities such as bonds and stocks. Since the first ICO presented by Mastercoin in the year 2013, there are hundreds of ICOs today. The industry is undergoing a notable transition with similar other models such as Security Token Offering (STO) and Initial Exchange Offering (IEO).
STOs are security tokens that are issued and sold to the investors just the way using crowdfunding methods such as ICOs, digital tokens are sold. Security tokens seem to reinvigorate the landscape of the crypto industry.
What is Initial Exchange Offering (IEO)?
An Initial Exchange Offering is a token sale that is supervised by some cryptocurrency exchange instead of the issuer’s platform. IEOs are available to users of the exchange, some IEOs take place in various exchanges. If an exchange has its own token, contributors would have to purchase token units before participating in IEO.
Just like ICOs, with IEOs, investors can get new tokens (or cryptocurrencies) while raising funds for cryptocurrency projects. IEO is currently the most dominant trend in the crypto industry. In crypto exchanges, funds are raised on behalf of startups while taking in place due diligence and other commitments. On the exchange platforms, cryptocurrency projects conduct a sale of tokens where token issuers are supposed to pay a listing fee to exchange. Crypto projects then sell their token with listing on exchange platforms.
The major drawback here for IEO is that it is not available to open public. Only the users of that particular exchange can participate no one else can. The others who want to participate would have to open an account with the exchange platform that is hosting IEO.
How does IEO work?
Initial Exchange Offering (IEO) process is basically divided into four stages; Plan preparation, Pre-IEO stage, IEO, and Post-IEO stage. All these processes separately discuss how IEOs are launched and how one can do them without any hassle.
Plan preparation
This is the first stage in which tokens need to listed for IEO project. The startup needs to come up with the idea, check its feasibility, conduct a survey regarding its market need and position. Then look at the budget and investment plan to launch an IEO. For all this process, proper planning and experience in the relevant project niche are needed. Moreover, consultation with field and market experts can help better in analyzing the scope. The project should be remarkable to get listed on crypto exchange platforms.
Once you come with the plan, look for partners that have experience in the field. A strong and talented team is really important as it helps in gaining more investors in the project. In order to launch the IEO project on a crypto exchange, there should be some work done beforehand to impress the exchange and get the project listed.
Pre-IEO stage
In this stage, choose some crypto exchange platform to pitch an IEO project. For this, there are some things to consider, make sure that you are well-aware of the committee and exchange’s norms while onboarding an IEO project. Keep everything ready and running while presenting, this increases the chances of getting selected by the crypto exchange.
After selecting an exchange platform, write up a proposal document to present it to investors. That document should contain each and everything, from the purpose to market survey, stats and figures to development strategy, a roadmap to investment overview, budgeting to future scope. This helps impress the investors when a complete overview of an idea will be given, the chances of a project to get listed on the exchange platform increase. When ready with documentation, you are well to go with the development of tokens.
IEO
In this stage of token developments, make sure that your budget meet teh requirements well. Funding hardcopy should be formed to present the investors that idea is achievable with this much development cost and market adaptability. When token get minted, the next step is to list those token onto the selected crypto exchange platform. If that exchange selects your project idea and you pass the KYC and AML stage, your tokens will list onto exchange platforms.
Post-IEO stage
This stage is important as your tokens are listed by exchange. The next step is to market the product. Outreach your audience, promote the product by running several social media marketing strategies.
Difference between ICO and IEO
Initial Exchange Offerings and Initial Coin Offerings are crowdfunding techniques. In ICOs token issuers are responsible whereas for IEOs startups look for exchanges to raise funds. In IEOs, a third-party in the form of a crypto exchange is involved whereas, in ICOs, crypto projects approach investors directly.
IEO mechanism establishes trust between investors and token issuers more than it does in ICO. This is done by filtering out the bad actors in the early stages during the process of Customer Due Diligence. Identity verification beforehand helps exchanges build a healthy relationship between two entities. It helps eliminate bad actors, money launderers, terrorist financiers and other criminal entities from misusing the IEOs.
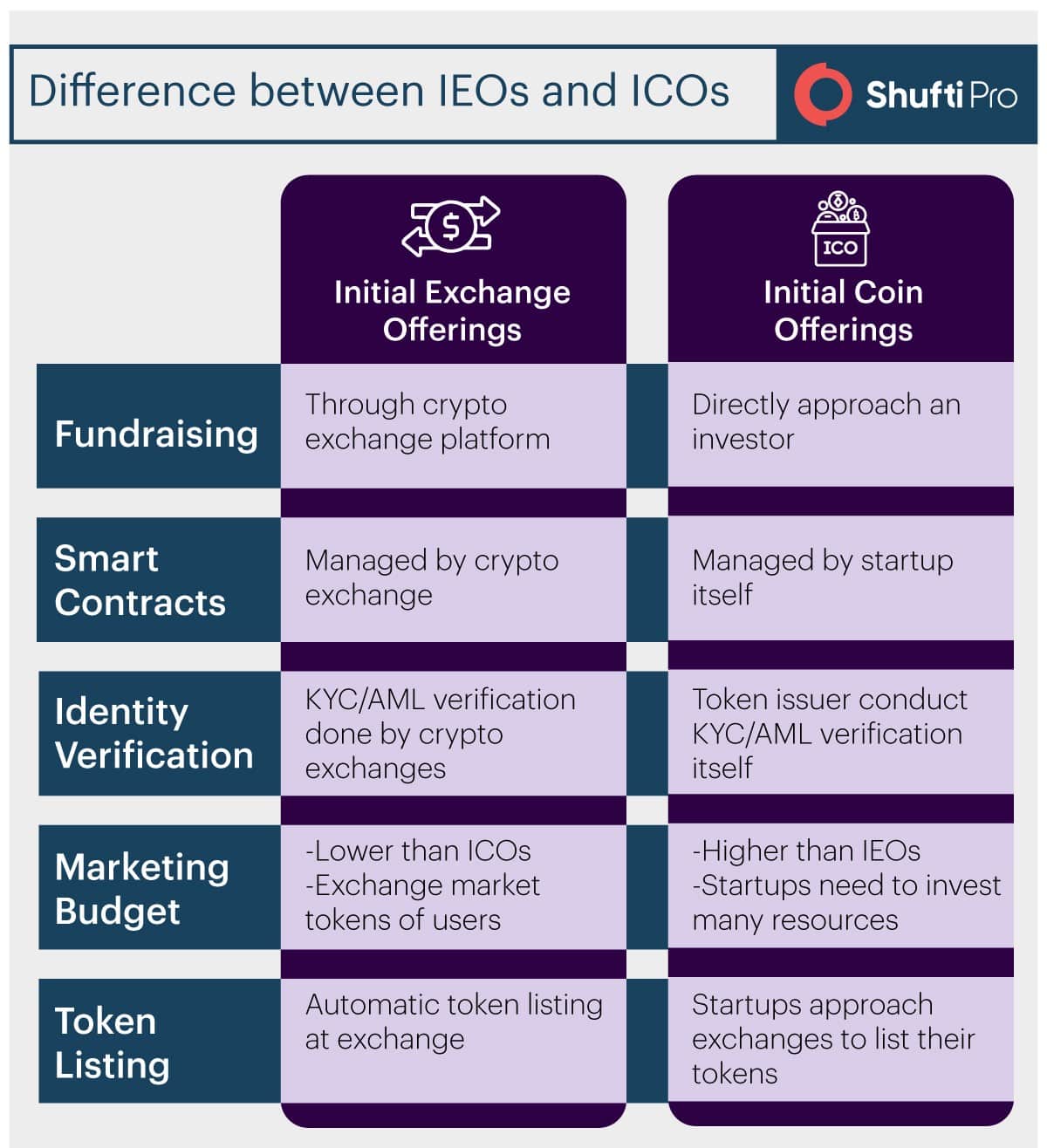
In ICO, it is the duty of token issuer to manage smart contracts whereas, in IEO, exchanges themselves do this task. This gives a security advantage in the crowd sale. At the exchange side, all mandatory KYC (Know Your Customer) and AML (Anti-money Laundering) checks are implemented against each identity. These checks are conducted to ensure that no fraudulent identity is facilitated through the exchange. Investors and token issuers are identified and a healthy relationship is built being exchanges as an intermediary.
Collaboration with crypto exchange platforms helps token issuers reduce marketing efforts. As compared to ICOs, startups get better savings with IEOs. Moreover, startups can continue better contributions to their projects with stable customer base exchanges provide.
With respect to efficiency and security, IEOs take edge over ICOs. One needs to register on the exchange platforms going through the stages of identity verification that include KYC and AML checks in which along with an entity’s identity verification, it is screened against various global watchlists and criminal databases. Being this primary advantage IEO exchanges are considered secure investment platforms.
Once the entity is verified, the next step is to just fund the wallet with IEO supported cryptocurrencies However, the cost of IEOs could be a bit higher than ICOs. Nevertheless, IEO’s merits outweigh that cost.
Why IEO over ICO?
There are many ICOs available today. Still why the team needs a different way of fundraising? The thing is IEO provides benefits over ICO that could be depicted by the percentage of population transitioning towards it. Running an exchange has always been a profitable business from trading fees alone. Following are some of the advantages of IEOs for exchange platforms:
- Both IEO and listing fee can significantly vary between exchanges
- Intermediary platforms between exchanges and token issuer reduce frauds and scams
- The joint market is established with IEO team
Intermediary platforms serve as an additional layer of security that helps identify and authenticate investors before making investments. Before token sale, exchanges thoroughly authenticate the credibility of token issuers.

 Explore Now
Explore Now