6 Reasons eIDV Fails and What Businesses Must Require for Reliability
What to Expect in this Blog?
An eIDV is like a bridge between intent and activation. It gets real users across instantly, but when one support pillar cracks, the whole span wobbles, and that shows up as no-matches, fallbacks, and lost conversions.
This blog will help you understand where eIDV typically breaks, what those failures mean for onboarding performance, and how to identify risks before launching in a new market. You’ll get a clear breakdown of the most common no-match drivers, plus practical criteria to evaluate any eIDV setup with confidence.
Understanding Electronic ID Verification and Why It Fails in 6 Ways
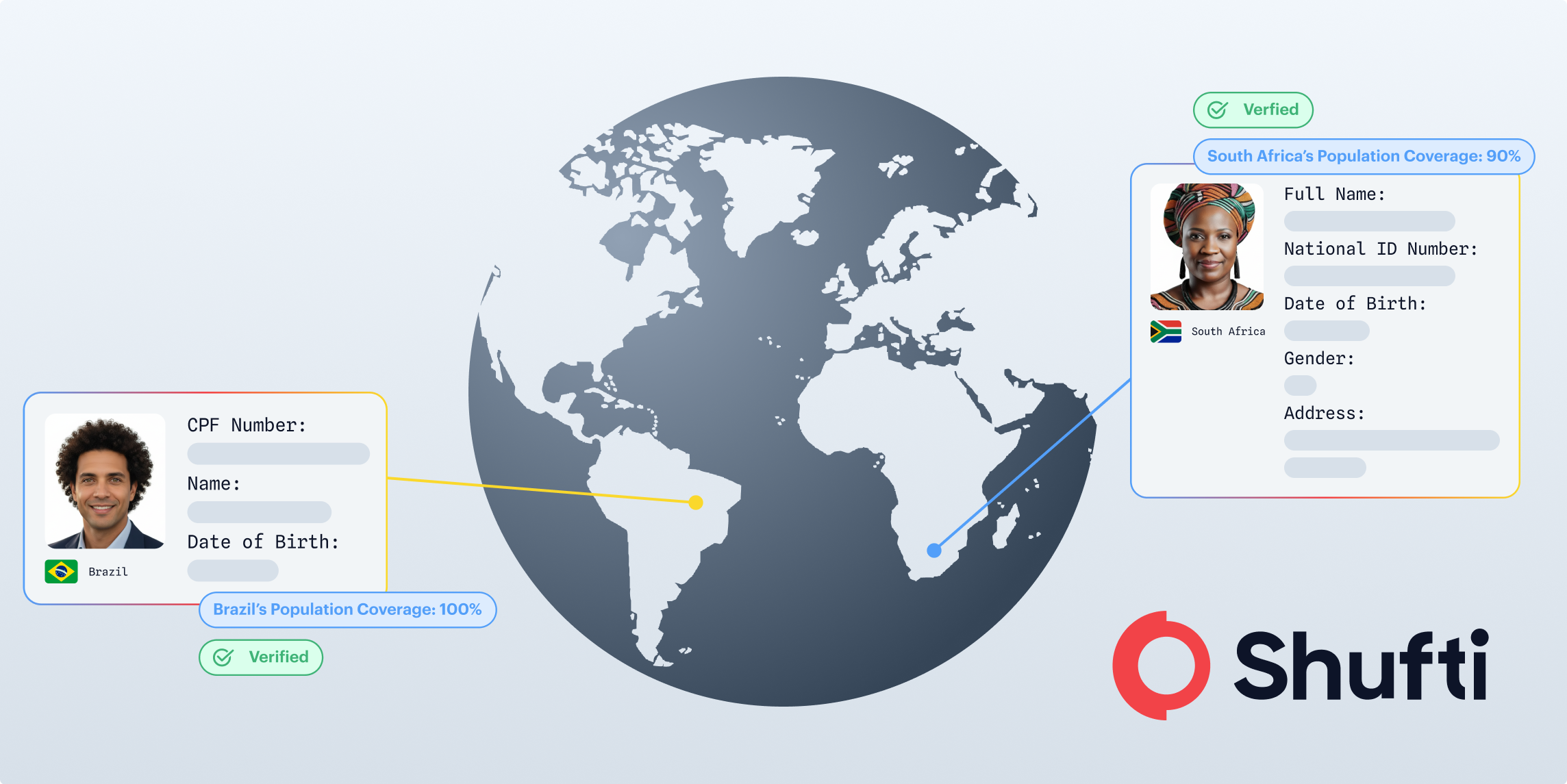
An Electronic Identity Verification (eIDV) is an identity verification process that does not require the use of documentation. Users are verified using their personal details, such as name, date of birth, national identification number, or address, which are cross-referenced with trusted digital platforms.
In many instances, instead of requiring the customer to present identity verification documents, eIDV uses a series of databases owned by governments, credit bureaus, telephone companies, and other reliable sources to verify the customer’s identity.
When implemented properly, eIDV can help improve the speed of customer onboarding, eliminate unnecessary impediments, and enable businesses to be in compliance while continuing to grow. In practice, however, eIDV does not provide these advantages due to the weak foundation that many companies have regarding the rails supporting electronic identification implementation. The six primary patterns of failure are as follows:
1. Coverage Gaps Create Real-User Failures
In order to confirm if an applicant is a real person, electronic ID Verification (eIDV) can only use the data that is available in the databases and search through for validation of existence. Unfortunately for many markets, this means that the available data contains only a partial representation of the population. As a result, legitimate users will fail no-match verifications, even when they are indeed legitimate. Therefore, a business will have a high failure rate at the time of signup and be unable to rely on a no-documentation process to fully execute their onboarding process.
2. Unreliable Sources Make Outcomes Unpredictable
Most eIDV checks heavily rely on government-created registries. Therefore, when the source of check data is periodically unavailable, is in political unrest, or is not consistently reliable as a result of technical glitches, businesses experience erratic outcomes of timeouts or fluctuation rates of successful verifications, creating a layer of verification that businesses cannot depend upon.
3. Single-Source Setups Fail Without Orchestration
This includes setup configurations that are dependent on one data source or routed directly to third-party databases. Excluding the presence of vendor-managed multi-source routing, fallback logic and match-confidence controls/products creates an unstable eIDV product for businesses to work with, allowing them to incur hard failure points as opposed to providing the businesses with controlled choices.
4. Performance Breaks Under High Throughput
Strong eIDV infrastructures can suffer from low performance when an organisation experiences significant increases in volume during their onboarding process. If an eIDV provider is unable to perform at scale, the result will be increased latency and lower success rates. This can be especially evident in organisations that onboard thousands of users daily, which will manifest as slower signup flows for end users, an increase in frustrated customers, and high abandonment rates.
5. Low Match Rates Undermine the Promised ROI
An eIDV can only provide a real return on investment for companies if it can reliably identify each legitimate user; otherwise, it will lead to repeatedly providing “no match” responses, resulting in users being forced into doc KYC fallback options, thus forfeiting the friction savings that eIDV was intended to provide.
6. Incorrect Payloads Trigger False Failures
As a result, every country has its own distinct identity rules and data requirements. When the required fields, payload formats, or local validation standards are not adequately defined, there will be avoidable mismatches resulting from poor or a lack of proper integration. Companies will subsequently experience false negatives based on poor integration efforts, continuing to encounter discrepancies in decision-making between various compliance teams responsible for performing due diligence on the same set of applicants.

An eIDV failure triggers a chain reaction across your business, weakening compliance, slowing growth, straining resources, and driving operational loss.
Practical Requirements Businesses Should Demand Before Launching eIDV in Any Market
Before launching eIDV, businesses should determine whether the data array supports sufficient levels of the actual population they intend to onboard. This is not about whether a provider can say “the country is supported”, but rather whether there are actual users in the target market segments who will be consistently matched today and whether that coverage is adequate to make eIDV feasible as businesses start to scale up beyond pilot operations.
Requirement 1:
Real Population Coverage for your Target Segments
To use a benchmark, if coverage isn’t able to eliminate most of my authentic and revenue-driving customers, instead forcing them into falling back to another method, eIDV will not alleviate friction. It will merely transfer friction into an occurrence of no matches. However, how deep that coverage is across a population is important, and that aspect is what Shufti has as an advantage compared to the rest because of live eIDV across more than 60 markets and over 4 billion global identities, providing companies with the global coverage needed to enable smooth implementation of the eIDV process on a large scale.
Requirement 2:
Stable Multi-Source Orchestration
Businesses must never rely on one single database source for eIDV. They should have at least several independent sources for each market, including multiple independent databases, and all of these independent databases must be integrated through provider-managed orchestration. This orchestration includes features such as smart routing, fallback handling, and trust-based matching to prevent verification failure from stemming from a degradation or disconnection of one data source.
Requirement 3:
High Uptime and Performance at Scale
The practicality of launching eIDV is contingent upon its maintaining a high level of reliability and speed, even with a large volume of traffic. Therefore, the uptime, latency, and throughput resiliency of the eIDV must be proven to support onboarding activities at a high volume or rate. If an eIDV’s performance drops during a promotional campaign or peak traffic period, it will create a bottleneck in the verification process, forcing users into document verification fallback, which is likely to result in a high rate of abandonment and lower conversion rates.
Requirement 4:
High Non-Doc Clearance in Real Conditions
The value of global eIDV is determined by whether it effectively identifies true users with little to no chance of falling back to other identity verification methods. Companies must have confirmed historical “match” performance and low levels of avoidable “no match” outcomes for their own customers and the ability to monitor and continuously adjust and optimise pass rates for specific marketplaces and geographic areas. Otherwise, eIDV is merely a means to create a doc funnel under the guise of facilitating customer identification.
Requirement 5:
Clear Country-Level Payload Alignment
Every market has individual identity guidelines that require completing specific fields as well as complying with their formatting standards. Businesses must clearly state the requirements for their country, including the payload requirements, validation requirements for local use, and integration best practices to avoid false mismatches. Most of the failed attempts to use eIDV verification systems are not due to fraud but rather to the use of illegitimate or ambiguous payload logic, and those issues can multiply quickly if not addressed at the outset.
How Does Shufti Solve eIDV Failures with Global-Ready Benchmarks?
Shufti’s unique blend of live market access, coordination/organization depth, and production-level performance makes it possible to meet these needs.
For Coverage, Shufti provides eIDV services to businesses in over 60+ countries and allows companies to validate against 4.29 billion global identities, allowing for standardized onboarding flows worldwide. Clients can activate eIDV in any areas where access to local data is strong.
For reliability, Shufti’s system for eIDV uses multi-database matching, coupled with dual-source checks (2×2) to ensure that verification does not depend on any single registry. This way, if any one source fails, verification will continue to work smoothly.
For speed across all markets, Shufti is positioned as a real-time electronic identity verification (eIDV) system designed to return decisions fast enough to keep users moving through onboarding without delays. This speed is essential for businesses to minimize signup friction during peak onboarding.
Scale globally with a solution interoperable with government eIDs
Know what each country supports, what data you'll get, and how to route users — so you can expand with precision, not guesswork.

 Explore Now
Explore Now














