A Smarter Guide to AML Screening in 2026 for Stronger Compliance and Faster Risk Decisions

What is AML Screening?
AML Screening is a core part of KYC compliance and customer due diligence, where businesses verify customer identities against global sanctions lists, PEP screening lists, watchlists, and adverse media to detect financial crime risk.
Modern AML Screening software goes beyond simple list checks. It enables real-time AML screening, multilingual name matching, and ongoing AML screening and monitoring, so risk doesn’t slip through after onboarding.
Accurate AML name screening helps organizations meet evolving AML Screening requirements, reduce false positives, and prevent exposure to money laundering, terrorist financing, fraud, and regulatory penalties. With an AI-powered AML Screening solution, companies can automate onboarding verifications, run continuous monitoring, and make faster, defensible risk decisions across global and domestic lists.
The Urgency of Dynamic Risk Assessment
On a normal Tuesday morning, a mid-sized Southeast Asian institution granted a corporate banking facility a “low risk” designation with minimal documentation and no flagged PEP or sanctions against that entity. That same day, a series of trivial trades began flowing through the new account, followed just a few hours later by a much more substantial transaction from one of the client’s geographically located partners within the regional area.
Two days later, the compliance department received an alert of a new domestic list from law enforcement of those individuals who had been flagged; it was soon discovered after further investigation that the previously unknown beneficial owner for the subject company had been added just two weeks prior and that domestic list information had not yet made it to the broader global lists.
The bank took proactive steps to freeze the account and report the potential financial issue and advised their internal auditors as to how this apparently “cleared” customer became a “high-risk” customer.
Take a moment and pretend this is your desk. The impact of that moment is not just a failure of technology; it is indicative of the current state of compliance, and all too often the experience remains the same when presented to regulators; it doesn’t take malice to create a serious compliance incident; it takes only an inefficient screening process.
Chapter 1: Sanction Screening
Global Sanctions Look Complete Until They’re Not
The Office of Foreign Assets Control administers and enforces economic sanctions programmes primarily against countries and groups of individuals. The sanctions can be either comprehensive or selective. Many people assume that there is one seamless global system of sanctions that operates in perfect synchronisation, where if someone is added to the sanctions list, all countries and all banks would freeze them immediately.
How Does Sanction Screening Work?
In general, the answer is simple because sanctions are enforceable laws, and to avoid illegal dealings, you screen people against the globally issued sanctioned lists. In practice, it is far more complex than you think. Countries issue sanctions at different times and add individuals or entities earlier than others for reasons such as intelligence, regional political issues, or other specific security concerns.
The fact that the international sanctions regimes like OFAC have lists of sanctioned entities accessible to everyone means the frequency of updates is no longer a differentiating factor in competing for global coverage because a single source for those lists offers no competitive advantage.
Domestic Sanctions Move Faster Than Global Databases
The counterintuitive truth about sanctions is that the first list that matters is not global; it’s domestic, where political systems establish sanctions in local markets and are bound by their own timelines.
Domestic sanctions reflect national security priorities and often bring enforcement logic that doesn’t map clearly onto global frameworks. But domestic sanctions lists don’t come in perfect form and appear inconsistently. They are often:
- Unstructured and hard to parse
- Incomplete and inconsistent identities
- Local language and transliteration issue
- Fragmented and irregularly updated
And because of this complexity, there is a lack of coverage across the local market by most of the industry, where many current vendors for sanctions screening focus heavily on the global sanctions because that is where the majority of sanctioned entities reside, while ignoring the initial identification reality of real risks taking place on a ground level.
Raw Sanctions Data Creates False Positives and Blind Spots
In cases of screening against sanctions, it is not enough to possess data alone. The critical factor is to convert the data into a structured, usable, and actionable format because there are numerous versions of domestic sanctions.
The same sanction listing could be found on multiple records that were fragmented and did not have a clear authoritative source. Furthermore, rules regarding enforcement seem to change continuously, so without cleaning and arranging the data into an operational format, the screening process results in inconsistencies and missing data.
The Interpretation Trap of Primary vs Secondary Sanctions
One of the clearest examples is distinguishing between jurisdictions that have different interpretations of the distinctions between primary and secondary sanctions. Misinterpreting these varying interpretations can result in institutions facing conflicting compliance issues, being non-compliant in some areas, and being over-compliant in others.
Sanctions screening breaks down when interpretation is treated as optional.
If there is no structured interpretation of the results of sanctions screening, the inconsistencies will make it almost impossible to demonstrate compliance or defend against audit scrutiny. It is not the availability of sanctions lists; rather, it is the industry’s tendency to focus on the most static and predictable level of these lists while ignoring the more volatile ones.
How Shufti Delivers Full-Spectrum Sanctions Compliance Coverage
Sanctions screening can only be effective when institutions are aware of the complete picture.

Shufti cross-checks global and domestic sources to find overlaps, conflicts, and missing coverage. It then builds one consolidated sanctions layer instead of leaving lists siloed and incomplete.
Domestic sanctions lists are often fragmented and messy. The same person can appear multiple times across the same list because of different spellings, scripts, or missing identifiers, which makes the data hard to trust as-is.
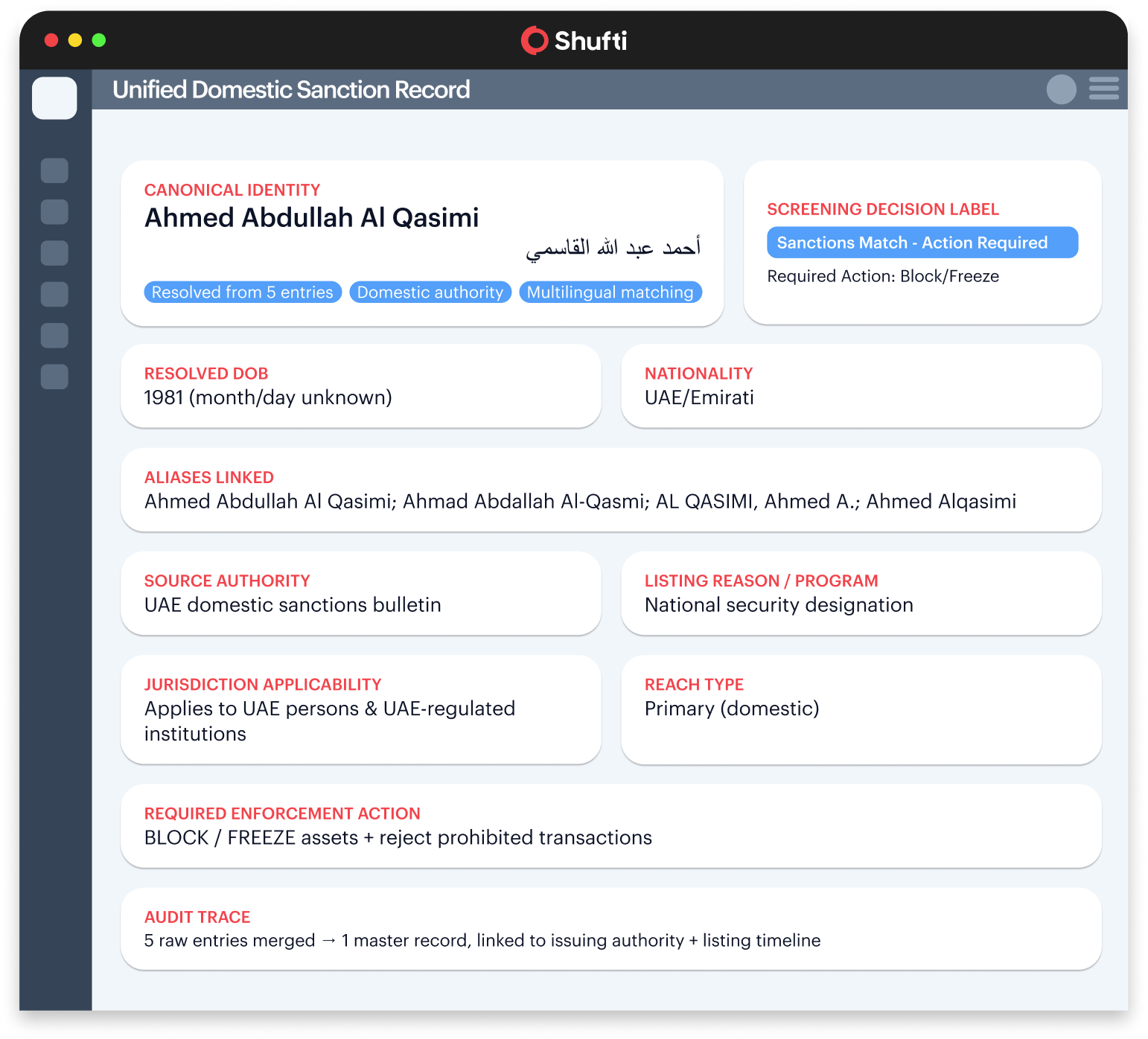
One Person, Five Rcords – A Fragmented List

Shufti solves this by unifying the domestic sanctions data first. It cleans and standardises entries, removes duplicates, and merges matching records into a single master profile, so teams work from one clear, reliable sanctions record instead of several confusing versions.
Instead of five noisy, inconsistent hits, screening teams see
one clear and enforceable decision.
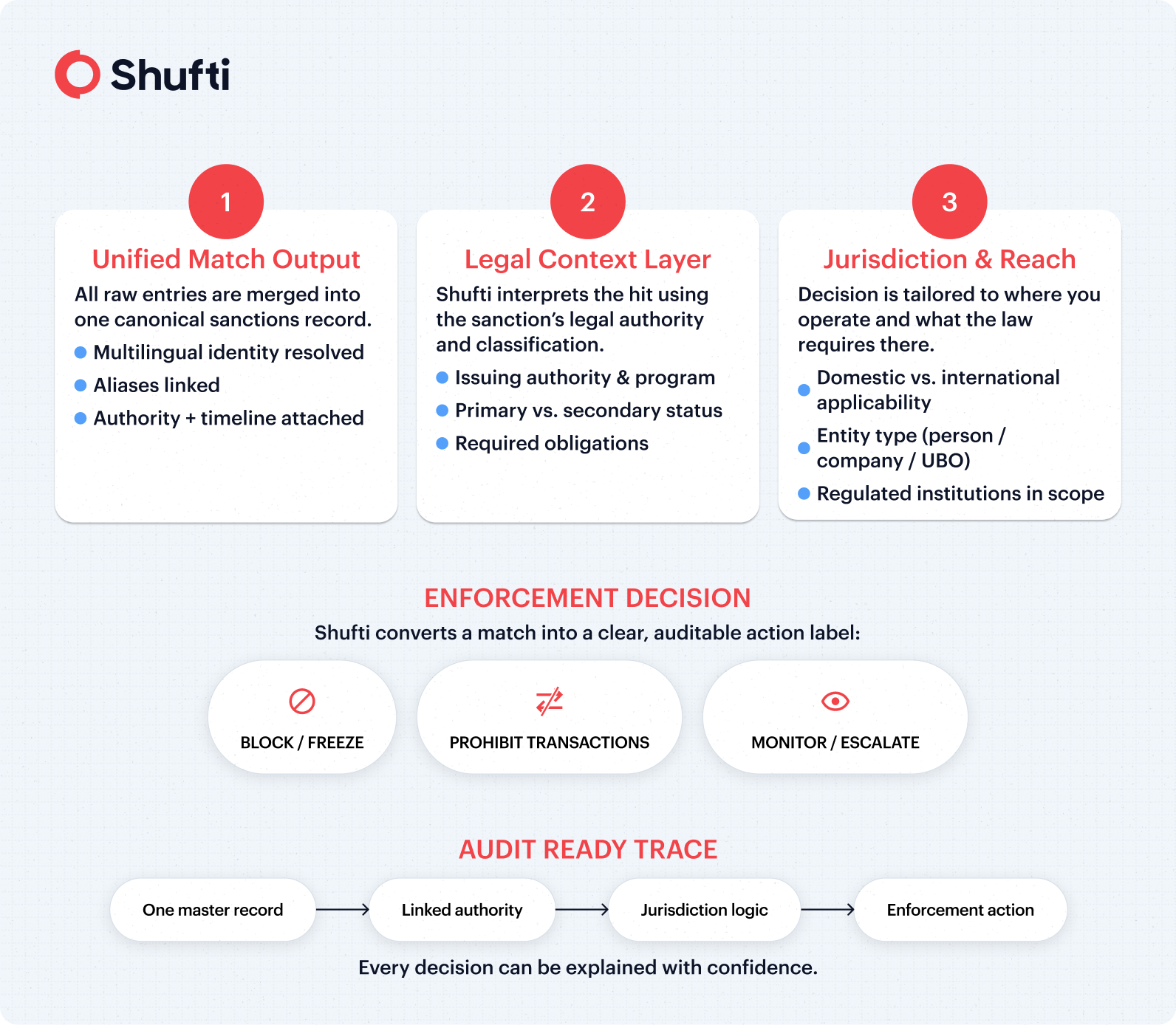
What Shufti Does After Domestic Sanctions Data Unification
Once fragmented sanctions data becomes a single master record, Shufti adds legal and jurisdictional intelligence to produce a decision your team can defend in audits.
Chapter 2: Politically Exposed Persons Screening
Disputed Territories Break PEP Databases
When vendors claim that they offer complete PEP coverage for a particular country or region, the main question consumers should ask is,
What do they do with regard to disputed or contested areas? Do they consider the entire area as part of one country, split it into two zones, or classify them as having dual citizenship?
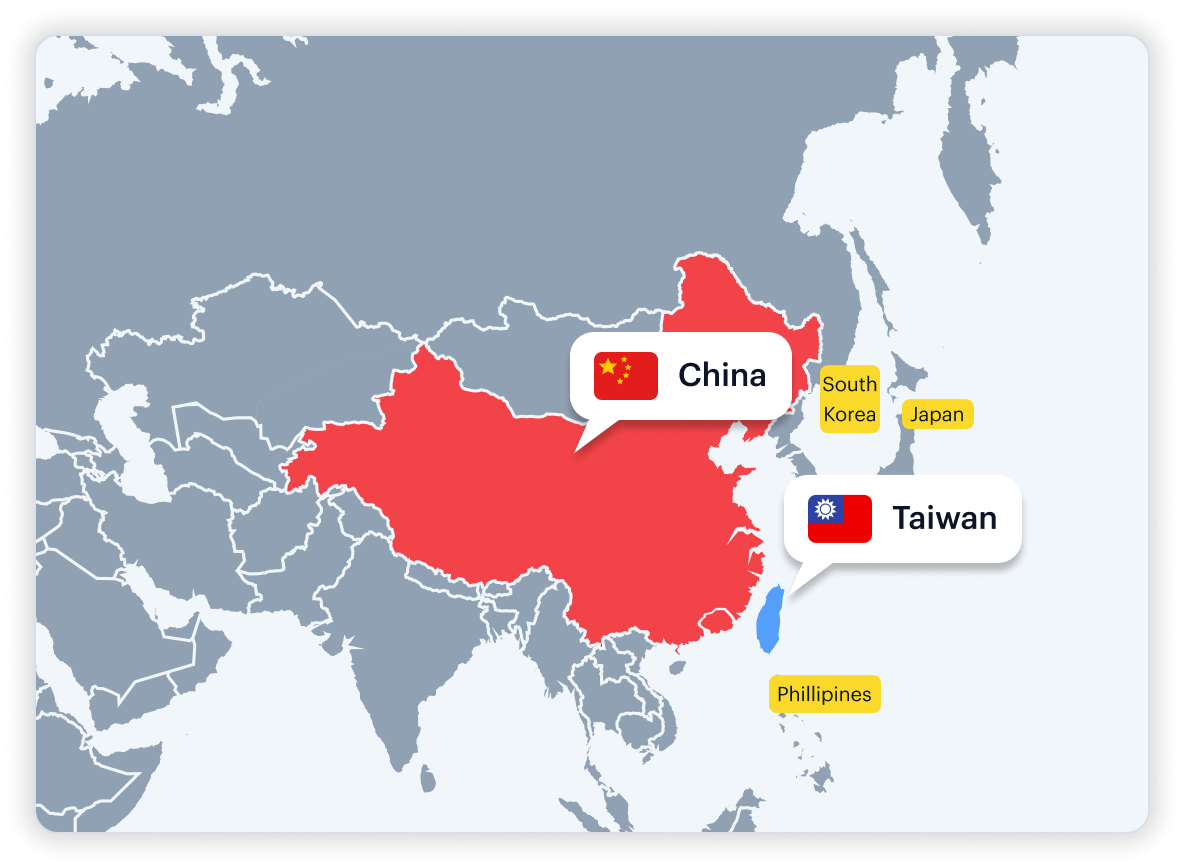
Why Ambiguous: Self-governed state-like system, claimed by China.
Vendor Mismatch: Officials tagged as China PEPs, Taiwan PEPs, or partially omitted.
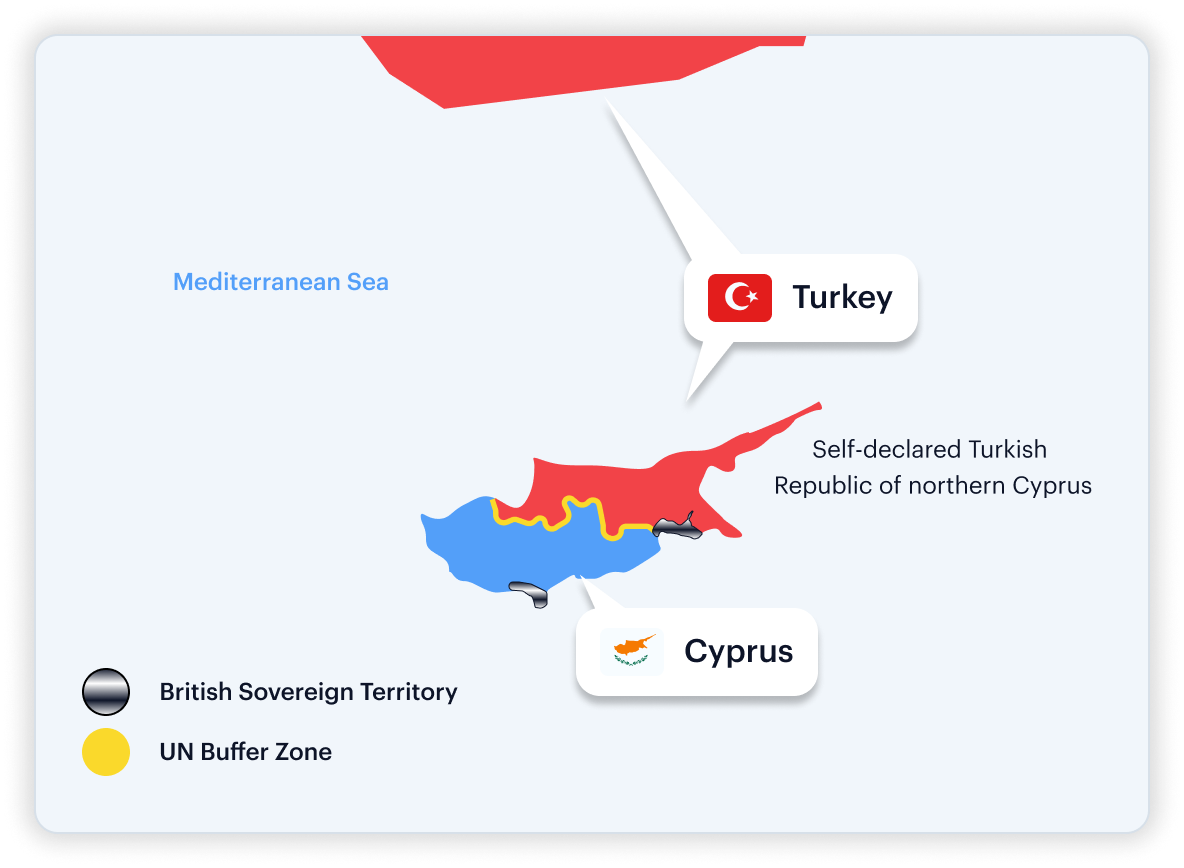
Why Ambiguous: De facto state recognized only by Turkey; most treat it as Cyprus.
Vendor Mismatch: Officials tagged as Turkey‑linked PEPs, Cyprus PEPs, or not tagged.
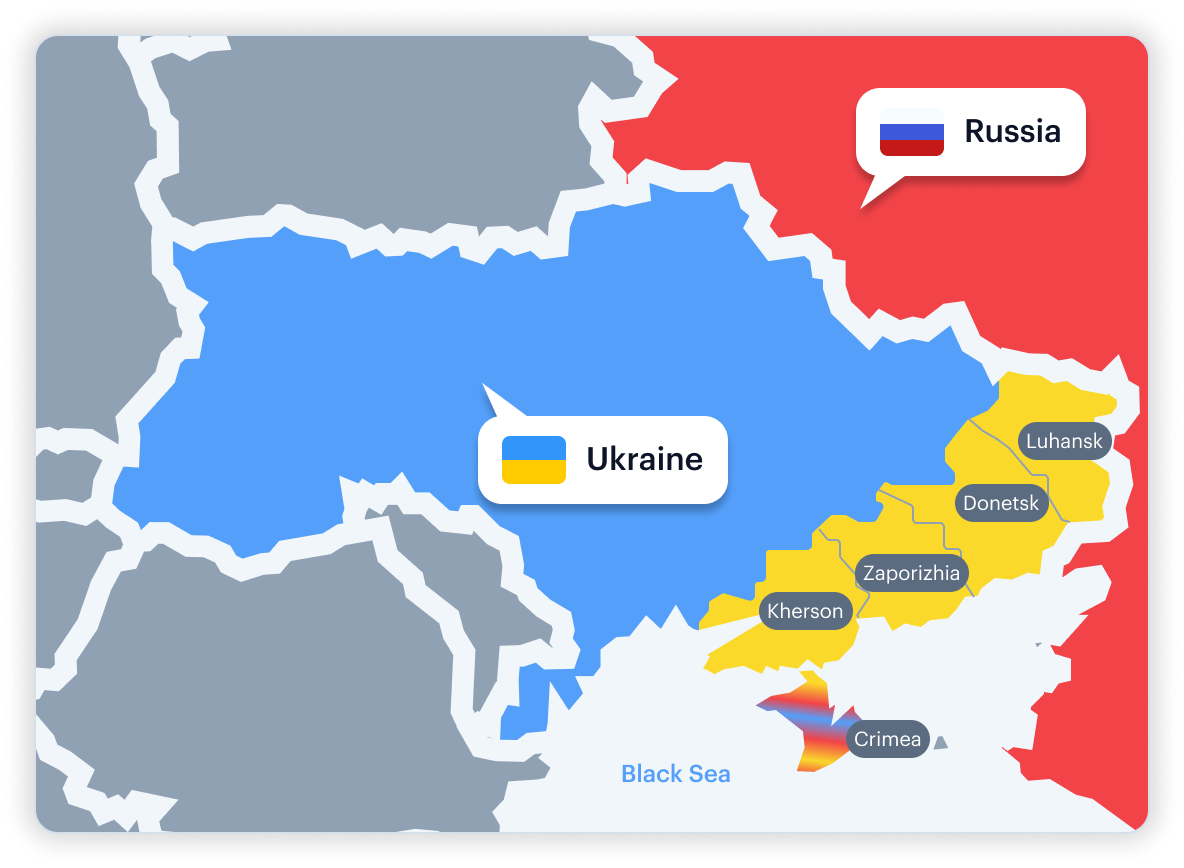
Why Ambiguous: Controlled/annexed by Russia, widely recognized as Ukraine.
Vendor Mismatch: Officials tagged as Russia PEPs, Ukraine PEPs, or “contested”.
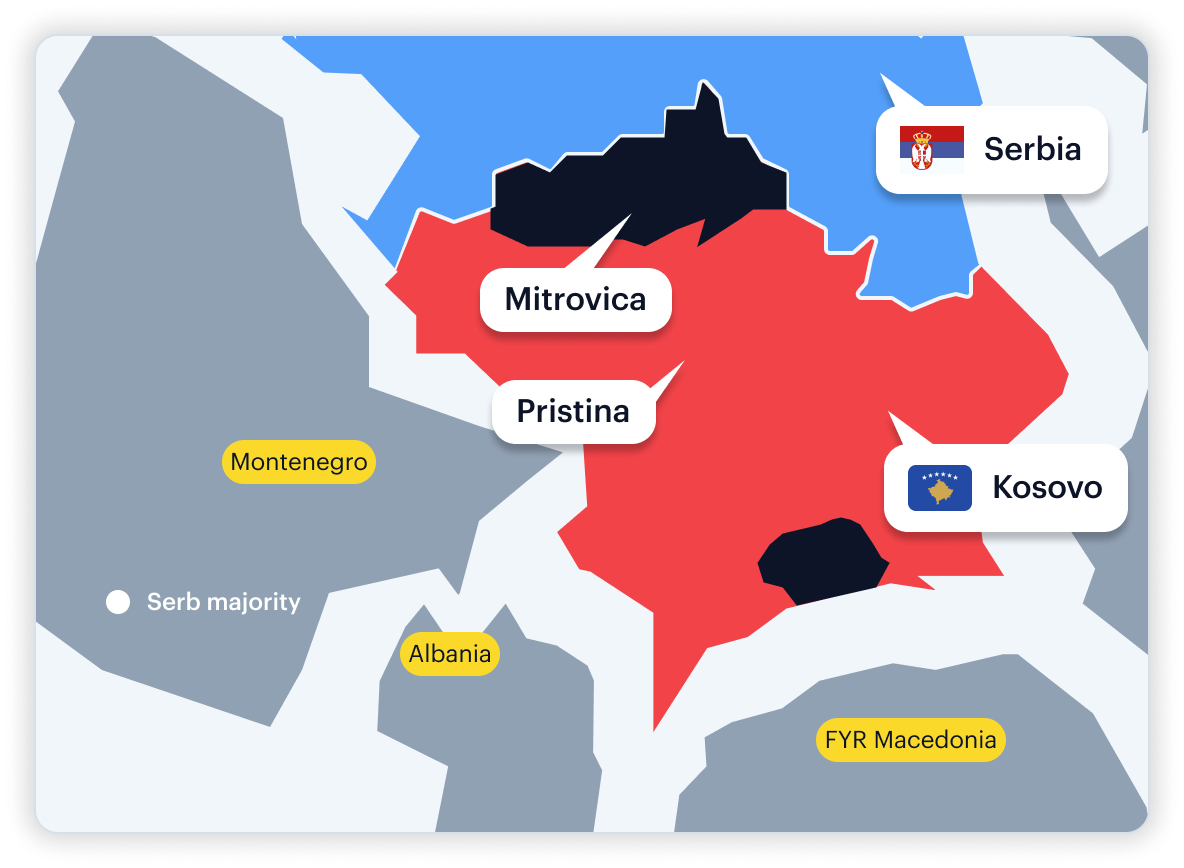
Why Ambiguous: Recognized by many states, not by Serbia/Russia/others; has full government.
Vendor Mismatch: Officials tagged as Kosovo PEPs vs Serbia PEPs; coverage depth varies.
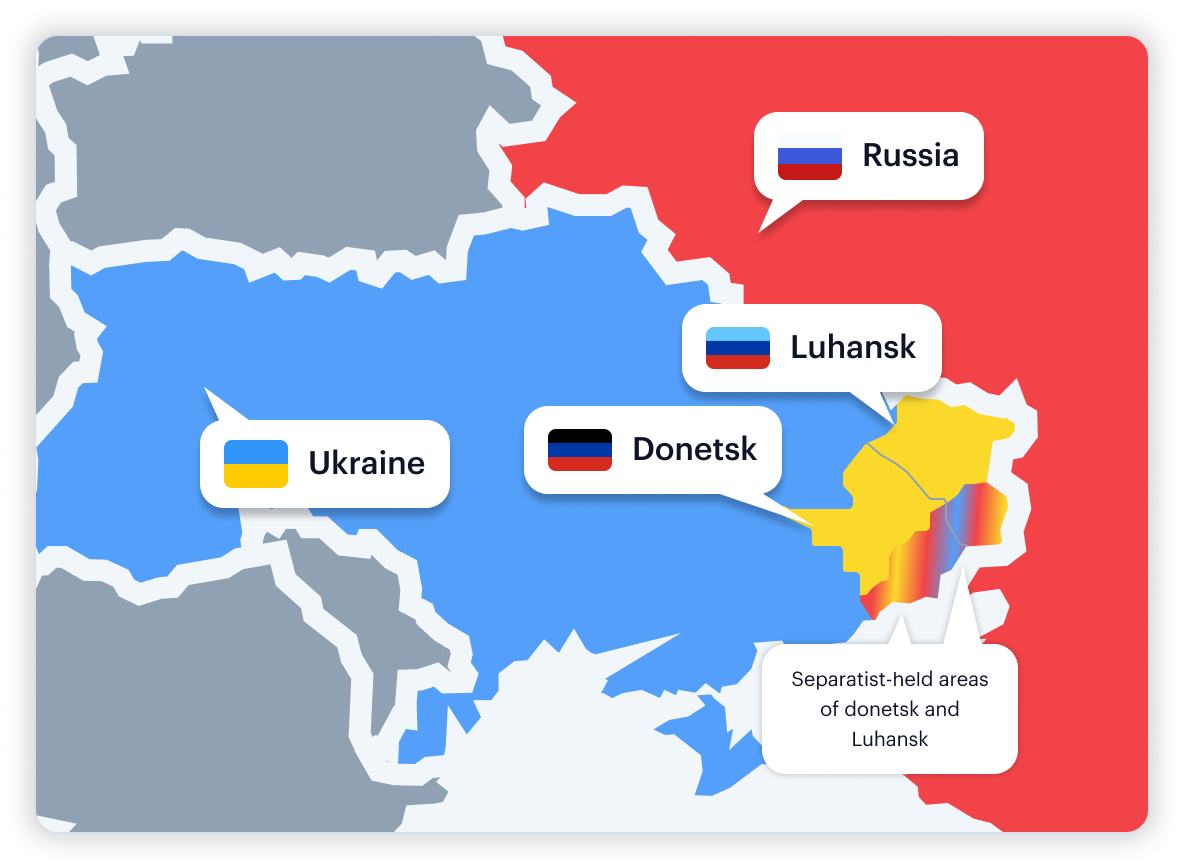
Why Ambiguous: Claimed by Russia via recognition/occupation; legally Ukraine for most states.
Vendor Mismatch: Officials tagged as Russia PEPs, Ukraine PEPs, or treated as non‑state actors.
Different vendors approach such complex issues in different ways based on their own legal regulations, internal regional policies, and their interpretation of geopolitical sensitivities.
Global Coverage Misses Local Depth
Many vendors say their PEP databases are broad in the sense that their coverage extends to many nations worldwide and includes many of the most prominent government leaders throughout the globe.
Most PEP databases do not contain data related to municipal or local officials, who are often the true decision-makers at the local level.
Council members, regional boards, and local political party leaders are often more impactful on local and national policy decisions than any single government official at the highest level of the population. For this reason, when a database flattens all of the people into one single definition based on their current level of authority, the organisations lose sight of where the risk actually begins.
Shufti’s Depth-First PEP Model
Shufti uses a depth-first approach in order to bridge the gaps and build a comprehensive picture of the political landscape at a regional level by mapping political structures within regions, expressing the political systems of each region accurately by classifying and evaluating individual Politically Exposed Persons (PEPs) on their roles.
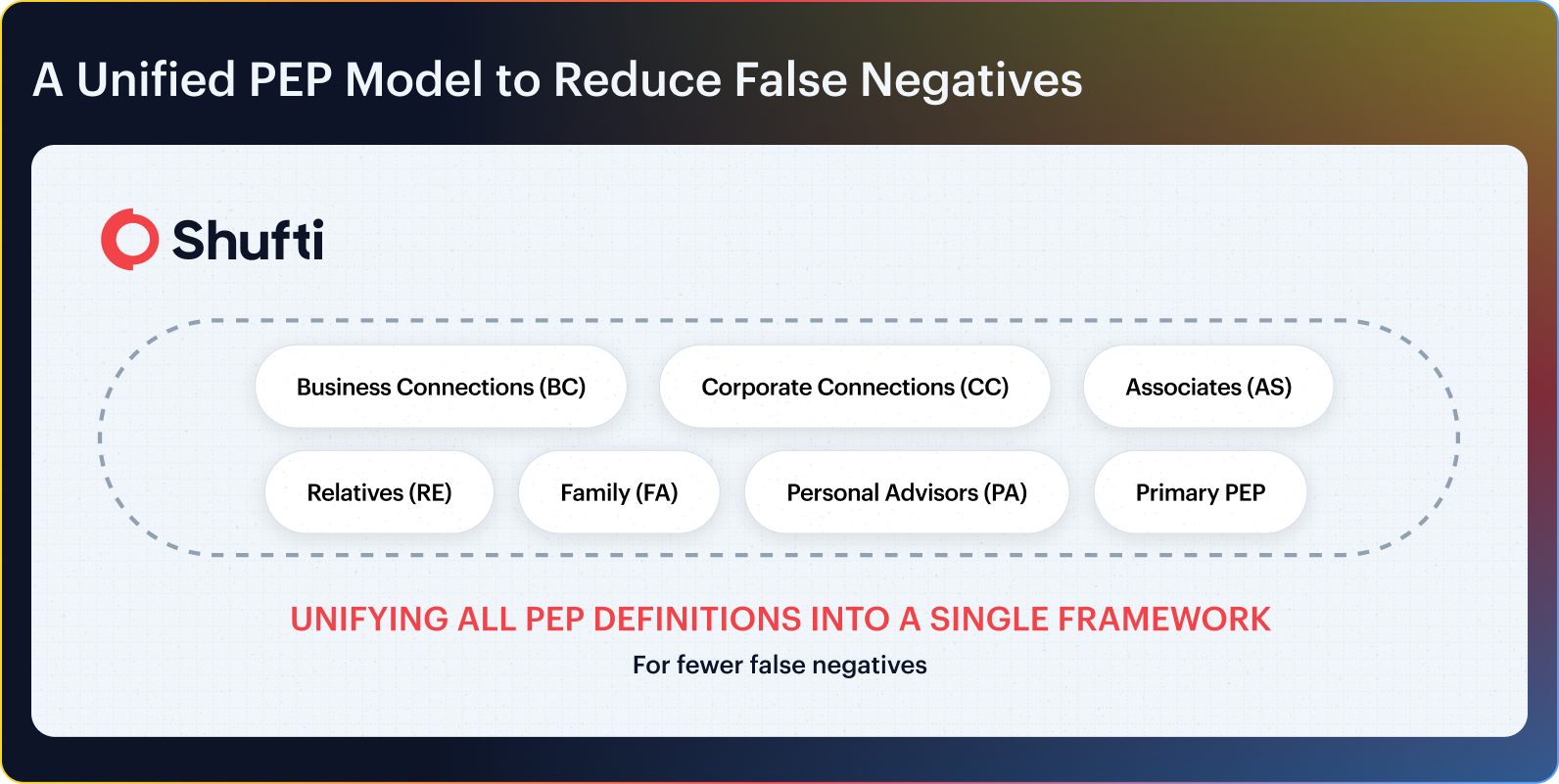
The Shufti’s Differentiator Level 4 PEP Screening
Level 4 includes local-level government officials and municipal authorities who hold public office but carry lower influence and lower corruption risk compared to national-level PEPs.
It is a new classification system that provides greater granularity than existing PEP classifications. It has an extension that extends Relatives and Close Associates (RCAs), contextualising the relative links of influence and risk through a network of RCAs.

This enrichment ensures that local actors, advisory boards, and party structures are included alongside high-profile figures, giving compliance teams comprehensive intelligence and actionable insight across the political spectrum.
This means that AML screening processes must always be in line with the rapid turnover of political officeholders to ensure new influencers are identified and accurately assessed in a timely manner.
Chapter 3: Watchlist Screening
The Most Misunderstood AML Layer
‘Watchlist’ is one of the most casually misused terms in compliance.
A common misconception equates sanctions lists and PEP lists directly with watchlists, as if checking these two sources alone provides comprehensive risk coverage.
Many vendors misclassify watchlists this way, reducing them to a convenient shortcut and avoiding the harder work of collecting and maintaining the broader enforcement ecosystem.
But What Exactly Are Watchlists?
Real watchlists go far beyond sanctions or PEPs. They include
- Fraud warnings
- Regulatory enforcement actions
- Exclusion and debarment lists
- Fugitive and wanted-person bulletins
- Law-enforcement alerts
- Professional disciplinary actions.
When screening an individual’s identity against this comprehensive global watchlist ecosystem, the system identifies any individuals found to be a potential match in any category from the global watchlist ecosystem.
How Shufti Builds Enforcement-Grade Watchlists
The layers of the Global Watchlist include Enforcement Intelligence as a primary layer of intelligence, as it picks up risk indicators which occur prior to being designated as a sanctioned person or PEP on the global watchlist.
The types of risk indicators include, but are not limited to, investigations, regulatory actions taken against entities for fraud alerts, exclusion or debarment initiatives, and professional disciplinary findings.
The issue with enforcement Intelligence is that the information is not readily available in a standardised format in many countries around the world. Where there are a myriad of organisations that generate this information, it typically resides within the policing jurisdiction, the regulatory authorities, professional bodies, or local government and therefore utilises a variety of different data formats when they publish the information.

Chapter 4: AML Name Screening
What Actually Breaks Name Screening?
AML name screening only works when two factors align. The quality of the data you start with and the intelligence of the system interpreting it.
Screening should be straightforward, where one simply compares a subject against a list to determine risk. But it is important to note that lists are not provided in an easy-to-interpret format. The lists received will generally have a lot of variables that are irregular, incomplete, and influenced by local law enforcement’s priorities.
Some regulators may publish their lists in only Latin scripts, whereas other regulators publish in their respective native character formatting. Some regulators may provide lists by using last names first, while there are others that do not follow this type of order.
There are a variety of differences among regulators, including how to include titles and honorifics as part of a Legal Name or how to treat titles as separate from a Legal Name.
These structural inconsistencies make the comparison of information between people lead to confusion, with different individuals looking similar or two records of the same individual appearing completely different.
Why Name Screening Fails In Practice?
If identifiers are present, proper names can complicate the process of identifying a person.
A single individual may have many different linguistic, cultural, or orthographic expressions. Cultural norms differ among countries; each country has its own system for transliterating scripts from one language into another.
The way a name is pronounced may differ from region to region, resulting in a change in spelling. Some cultures use a name’s lineage or honorifics, while others use initials.
As a result, single identities multiply into multiple written forms, which classical fuzzy or phonetic logic cannot reliably unify without context.
The Challenge of Cross-Language Names
In some cases, traditional fuzzy matching may not be able to identify all of the necessary names.
If thresholds are too strict, false negatives rise and critical AML matches are missed. If they’re too lenient. False positives increase sharply and unrelated users get flagged.
Therefore, achieving a proper balance between written and phonetic similarity is very difficult and quite complex, until data is augmented with additional context, i.e., the point of view in which the name was generated, virtually all advanced fuzzy matching methodologies will fail to accurately align an identity across multiple languages, scripts, and cultures, leaving AML teams with too many false alarms or far too many instances where actual AML risk has escaped detection.
The Shufti Advantage in Name Screening
Shufti rectifies identification screening problems by addressing two main problems: the absence of context regarding the identity and the inflexible logic underlying matching. Rather than pushing a multitude of inconsistent lists through a set threshold of confusingly vague criteria, Shufti first augments weak or incomplete records and uses these records to match names according to a complete, flexible, and dynamic identity framework.
1. Advanced Identity Enrichment
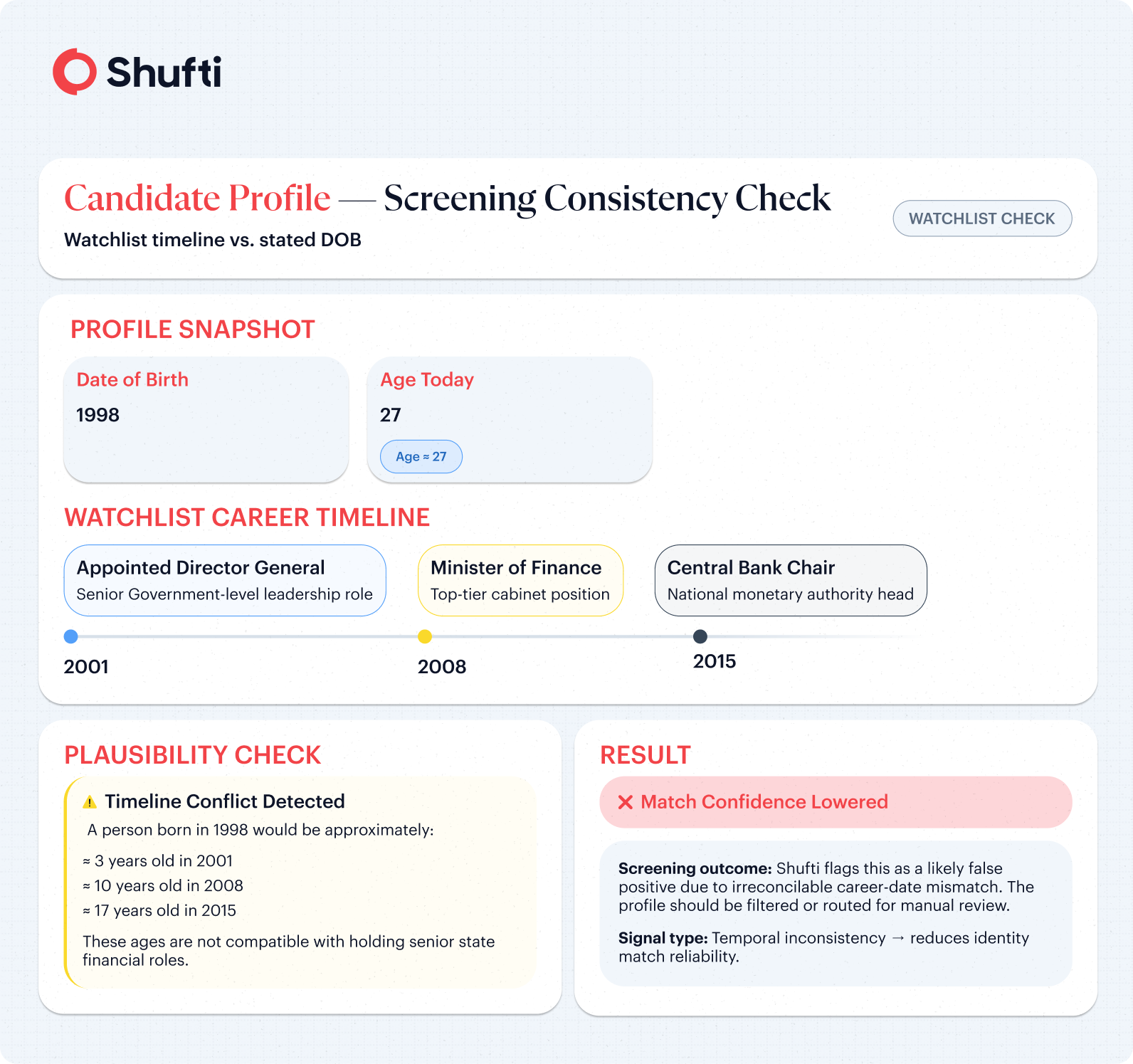
The majority of entries appearing on sanctions and watchlists do not include the individual’s date of birth (DOB) or nationality. Using its innovative approach, Shufti fills in these gaps by identifying indicators of identity through the use of metadata inference, multilingual text extraction, and timeline analysis of developments or activities related to each individual. The use of timeline logic also eliminates some false positives if the person’s age does not correspond to the career history of the profile being screened.
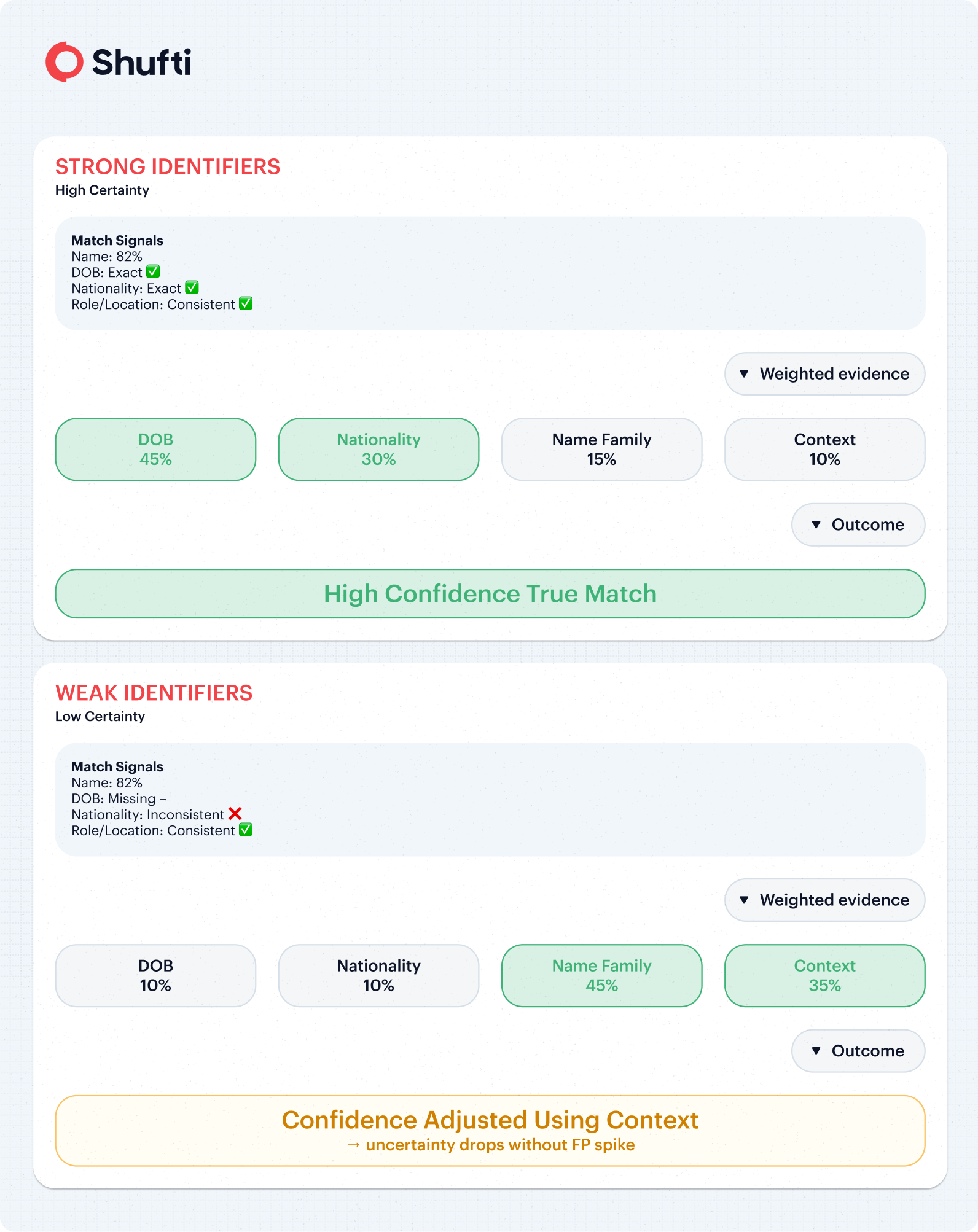
2. Dynamic Weight Allocation
The significance of identifiers varies from case to case. If the DOB and nationality of an individual are both solid and consistent, Shufti assigns more weight to those identifiers. Conversely, if the information is missing or inconsistent, the weight is decreased, and Shufti places increased reliance on other identifiers, which lowers the amount of uncertainty surrounding the individual without increasing the number of false positives.
Benchmark Your Screening Against Real-World Names
As a part of our continued commitment to provide a comprehensive comparison to our competitors, all of our vendors and clients are welcome to contact us to run a side-by-side comparison of any of their screening solutions, using 1,000 of the names of their choosing, including local PEPs, local watchlisted individuals, domestic sanctions, and even sanctions added in the last five minutes. This is a true stress test of their screening solution’s performance on the most challenging and current data.
The 1,000-Name Dataset
Our benchmark dataset of 1,000 records is intentionally constructed to be a mirror of the compliance world, with locally sourced PEPs, regional law enforcement watchlist information, domestic sanctions lists from multiple countries, and multilingual names in approximately 14-15 languages, meaning that the dataset has multiple scripts that can have many different transliterations and that have many different cultural naming patterns, all of which would be exactly the types of conditions that a generic global dataset would not support.
How is it evaluated?
When measuring the results of the side-by-side screening runs of your competitor’s solution versus a proprietary screening solution, we measure only core metrics for the screening process for your company, with false positives, false negatives, true positives and true negatives.
Want to see how your current screening really stacks up?
learn more
What to Demand From an AML Provider Before You Launch
A practical checklist your compliance and growth teams can align on. It outlines the exact questions to ask, evidence to request, and benchmarks to verify so your AML layer works in real onboarding.
Download the checklist


 Explore Now
Explore Now













