How to Choose the Best Age Verification Software

- 01 Why do many age checks still disappoint users and businesses?
- 02 What are some highly effective methods used by age verification software?
- 03 What does “highly effective” age assurance process mean according to Ofcom?
- 04 What Is the Key Principle Behind Effective Age Verification?
- 05 What does the best age verification flow feel like to users?
- 06 How to determine the performance of an age verification software?
- 07 How to select age verification software according to your business’s needs?
- 08 How does Shufti deliver privacy-preserving, frictionless age verification?
The central challenge for age verification software is a thin balance between when it must be a fortress against minors while simultaneously being a frictionless gateway for legitimate adults.
Product and risk teams know how easily this balance breaks when controls become heavy enough to hurt conversion, causing a dent in revenue or light enough to facilitate evasion, inviting regulatory scrutiny. The path forward is an age verification design that verifies the specific attribute that matters, which is adulthood at a defined threshold, and that does so with methods that respect privacy, maintain accessibility, and scale across jurisdictions.
Why do many age checks still disappoint users and businesses?
Implementing age verification is a challenge for many reasons, as the assurance level increases, so does the risk of higher friction for users and non-compliance with privacy laws, such as the UK GDPR. Conversely, lowering the guard risks non-compliance with laws like the UK Online Safety Act that require adequate age checks. So the challenge lies in staying compliant with both privacy and online safety laws, as well as providing a smooth user experience.
Older approaches to age verification often force a choice between intrusive data collection and weak gates that are easy to bypass, which leaves users frustrated and companies exposed to compliance and reputational risk. When every visitor is pushed into the same heavy flow of age verification, friction gathers at the first step, and mobile users abandon the process before they ever see the value on the other side.
Evasion from age checks has also become more sophisticated, utilizing borrowed IDs, synthetic faces, face filters, VPN hopping, and emulator use. This means that single-method defenses degrade quickly as attackers continue to experiment with newer approaches. Teams also face a patchwork of obligations that differ by sector and region, so a fixed solution rarely fits every market and product surface.
What are some highly effective methods used by age verification software?
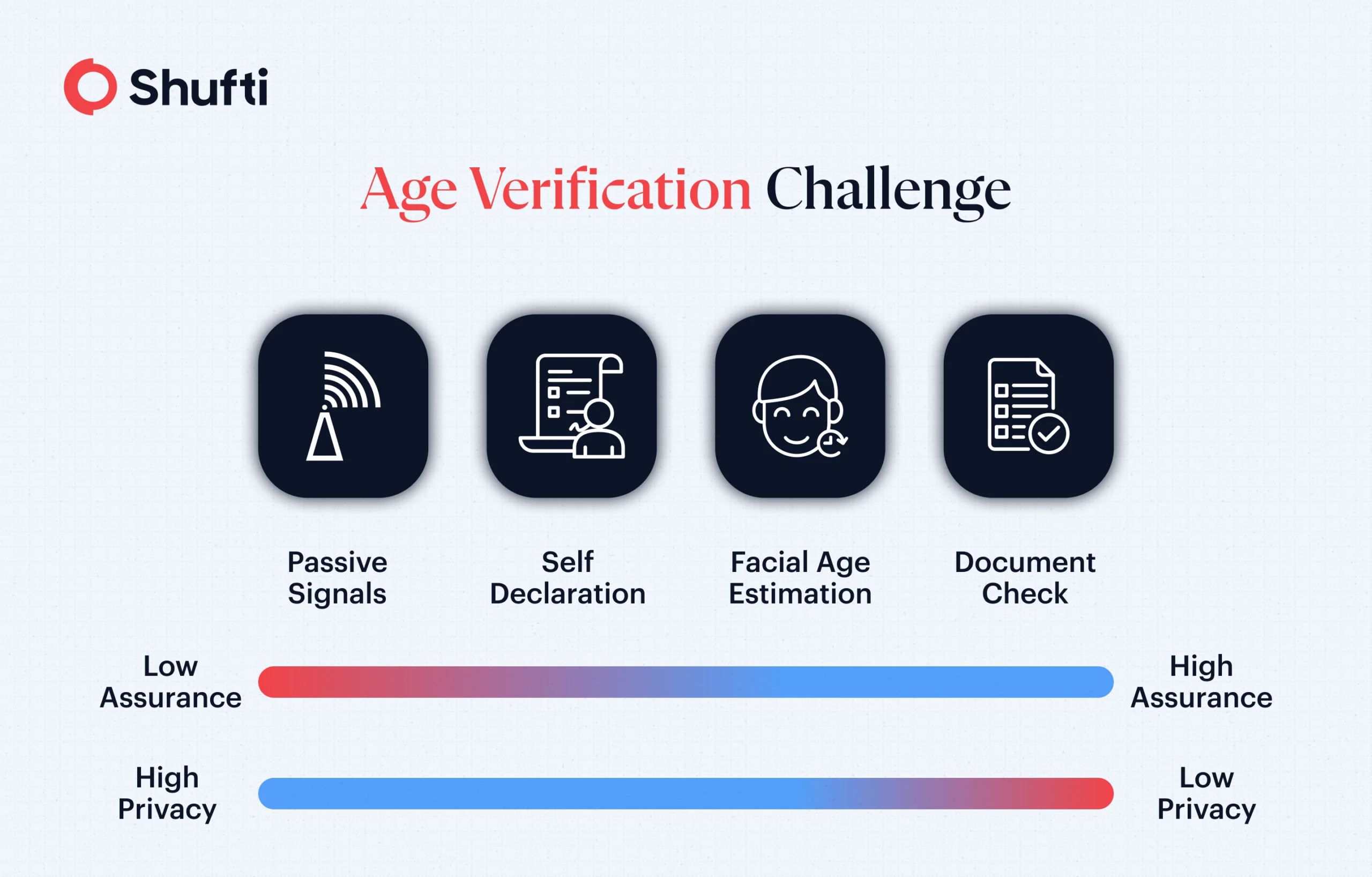
Different methods are used to determine if a user is a child or meets a set age threshold when using an online service, whether through a website or a mobile app. Guidelines from regulators like Ofcom and the Information Commissioner’s Office (ICO) in the UK provide a list of methods that are considered highly effective in age assurance. ICO guidance on UK GDPR compliance recommends that businesses implement an age verification system if they rely on consent for use of users’ personal information (legal age to consent is 13+).
It further suggests that organizations should use risk-based age checks appropriate to the level of risk to children’s rights and freedom. For example, where risks are higher, mere self-declaration of age is not sufficient and needs effective age verification methods. Some of the effective age verification methods as provided by Ofcom and ICO in the UK are:
- Open-Banking APIs
- Credit Card Checks
- Facial Age Estimation
- Document and Photo matching
- Telecom-based age checks
- Online Databases
- Digital Identity Wallets
- Email-based age checks
But this list is not exhaustive, and all of these methods may not be relevant for each business. Therefore, some companies may use other forms of age verification methods adapted to the needs of relevant sectors or industries. Selecting the right method depends on risk, regulatory environment, and user experience expectations. The best approach to age assurance is a waterfall approach.
Regulators like the Information Commissioner’s Office (ICO) suggest using a waterfall approach to age verification. The ICO recommends combining different age assurance methods, such as age estimation, along with the secondary age verification in situations where a higher level of assurance is required.
What does “highly effective” age assurance process mean according to Ofcom?
If you operate in the UK, Ofcom expects age assurance to meet four criteria to count as highly effective. The process must be technically accurate, robust, reliable, and fair.
What does accuracy mean in an age verification tool?
Accuracy means the degree to which a system can correctly separate adults from children at the chosen age threshold under testing conditions. This is important because if a system performs badly in a testing environment, it will be worse in real-time. Systems can produce results as either binary, such as over/under a set age, or continuous, such as an estimation of age. Where age estimation is used, it is recommended to use the challenge age approach. Results should be reviewed periodically so models and thresholds do not drift away from the track. Metrics to be watched out for:
- False accept rate (FAR), false reject rate (FRR), and true positive rate (TPR) for over/under age results
- For age estimation, measure the standard deviation (a low score means results are closer to the mean) and the mean absolute percentage error (MAPE)
- Error rates broken down by age band, device family, browser, and lighting conditions
What is the robustness of age checking software?
Robustness is the ability to resist evasion attempts that appear in the wild. If using facial age estimation, plan for presentation attack detection (PAD), deepfakes, replay, and injection attack detection. Make sure the system is configured to detect emulator or rooted-device use and network masking through VPNs. When risk rises, signals should be combined, and self-declaration should never stand alone.
- Independently evaluated liveness or PAD results and documented red-team exercises
- Controls that detect device and network tampering and trigger step-up when needed
- A maintained playbook that tracks new attack patterns and the countermeasures deployed
What does the reliability of age verification software mean?
The reliability of an online age verification software implies that performance holds steady at scale and at peak customer demand. Solution should ensure that user journeys complete quickly for legitimate adults, with graceful fallbacks and guided recapture when signals are weak. Every decision should generate audit-ready records that link method, confidence, and outcome, and service levels for uptime and latency should be tracked and enforced.
- Stable median and 90th percentile time-to-pass by market, method, and platform
- Clear step-up paths from lighter checks to document verification when confidence dips
- Tamper-evident decision logs, uptime reporting, and latency targets with alerting
How to measure fairness in age verification software?
Fairness requires active monitoring for unequal outcomes and thoughtful alternatives when users lack documents or compatible devices. Vendors should measure error rates across demographic groups and age bands, provide accessible flows and language options, and support human review where automated confidence is low. These actions reduce complaints and create measurable evidence that the system is effective and non-discriminatory in practice. Things that need to be watched:
- Ongoing analysis of false accepts and false rejects by demographic slices and regions
- Alternative paths that preserve access without diluting assurance
- A documented human review process with transparent outcomes and feedback loops
What Is the Key Principle Behind Effective Age Verification?
The guiding principle is that the age verification provider should only prove the attribute (for example, whether a user is 18+) without disclosing the full identity of a person. Hence, the decision becomes a clear yes or no against an age threshold.
Since each digital interaction is unique, the selection of an age verification method should be appropriate to the context because it will have direct consequences for both the end-users and businesses at the same time.
For example, a business like a social media app may need to comply with stricter age verification obligations under the Online Safety Act in the United Kingdom than in a jurisdiction where regulations may not demand a higher level of assurance.
Similarly, requirements for different sectors like e-commerce, adult content, and video gaming may vary within the same jurisdiction as well. One method can’t be the best in all cases; therefore, businesses need a range of techniques that can provide the required assurance.
Effective age verification software implements this concept by selecting the lightest method first that provides reasonable assurance as mandated by laws or a business’s risk appetite and escalating only when softer approaches fail to offer the required confidence level.
For example, age assurance can start with passive biometric signals to determine a user’s age. If this initial step fails, the system steps up to facial age estimation with liveness checks. If required assurance is not met, it continues to scan documents or use other means of verification.
As a result of this approach, raw scans (like biometric templates and document copies) are minimized because only those users who fail initial verification methods will need to present documents. Moreover, these raw scans should be processed locally whenever needed, and only outcomes and audit logs should be stored.
This is the key to strengthened privacy without compromising the ability to explain decisions to regulators and auditors. This principle of “minimum disclosure” ensures that privacy-by-design is built into every user interaction.
What does the best age verification flow feel like to users?
A visitor arrives at a gated feature, and the policy engine reads market, risk, and device context before choosing a path that keeps data collection to the minimum required.
Most adults complete a short face capture with passive liveness and receive an instant pass, while users near the age cut-off threshold (such as 18+, or 21+) are given a clear choice between a reusable proof from a wallet and a document path with clearly guided steps. At completion, the system issues a short-lived decision token that supports reuse within sensible limits, and a quick liveness refresh is requested when signals suggest sharing or a new device. The interface uses plain language, clear progress cues, and visible help, which makes the process feel fair, predictable, and respectful.
How to determine the performance of an age verification software?
Businesses that run age verification as a real product capability measure more than simple pass rates. A business can measure the effectiveness of an age verification software with the following parameters:
- Assess what time it takes users to pass the age verification checks at the median and 90th percentile. This measures if speed is consistent for real users and not limited to demos only.
- Determine what percentage of users successfully pass through the lowest friction age verification method?
- Measure how well the orchestration of the age verification flow is working and whether it’s collecting more data than necessary.
- Check how often a software successfully counters the use of VPNs, emulators, and presentation attacks. This shows whether the system is improving against active threats.
- Evaluate if there are any fairness gaps in the acceptance/rejection of users based on their demographics, influenced by training biases?
- These gaps can be quickly identified by tracking false accept rate (FAR) and false reject rate (FRR) across different demographic groups.
- Check the data minimization score, highlighting how much sensitive data is collected per successful age verification.
- How does it manage metrics like verification statuses, pass rates, and most used verification methods by location and time? This helps map verification methods to local rules and evidence, so audits are manageable.
Tracking these parameters can help you analyze the performance of your age verification vendor, its impact on your business and revenue, and your firm’s readiness for regulatory compliance and audits.
How to select age verification software according to your business’s needs?
When evaluating vendors, ask for evidence that the software offers a reasonable level of assurance based on your market and your risk appetite rather than relying on broad claims that are hard to verify. The second essential thing businesses need to monitor clearly is that the required level of assurance isn’t pre-packed with user privacy concerns. Some of the parameters that a business should look for when selecting an age verification platform include:
- Orchestration (age verification journey building) that you can manage through policy rather than code changes
- Liveness detection feature that has been independently tested against modern presentation attacks
- Document coverage that handles the passports and IDs your users actually present (based on industry and region)
- Selective disclosure options that prove age without revealing date of birth or other identity details
- On-device or ephemeral processing that reduces exposure and latency, and operational telemetry that feeds your dashboards and investigation tools.
Request published fairness testing and remediation plans, together with real latency numbers gathered from production environments that resemble your own.
How does Shufti deliver privacy-preserving, frictionless age verification?
Shufti offers policy-driven orchestration, which teams can manage with a no-code journey builder, allowing them to implement a risk-based waterfall approach that suits their business model. For businesses with returning users, Shufti’s FastID offers instant and secure re-verification for a smooth and hassle-free user experience.
Solution provides the core building blocks that a modern age verification software requires, including biometric verification with certified liveness detection. It supports authentic document and face matching for age checks, where the highest level of assurance is essential.
Shufti’s AI-based age estimation analyzes more than 100 facial vectors and landmarks to estimate the age with precision and accuracy. Solution is trained on highly diverse training data, encompassing all skin tones, facial features, lighting conditions, and temporary appearance changes like glasses, headwear, make-up, facial hair, etc. These characteristics eliminate bias in age estimation and block more than 99% of spoof attempts, such as presentation attacks, making it one of the safest and user-friendly age estimation methods.
Solution supports age proofing with already verified credentials from credible sources, such as government-issued digital identities and open-banking support with leading institutions, such as Monzo, HSBC, and Barclays, where available.
The platform helps product and risk leaders deliver a fast, audit-ready journey without rebuilding their stack. Solution supports age-focused use cases with developer-friendly integration and a design approach that respects privacy while minimizing user drop-offs and protecting conversion.
Discover how your business can continue to grow without fearing compliance risks. Request a demo.
Frequently Asked Questions
What is age verification software?
Age verification software confirms whether a user meets a defined age threshold for age-restricted products or services. Software checks only the age attribute, rather than the full identity, to preserve privacy and reduce friction.
What industries require age verification processes?
Sectors or businesses that serve or need to restrict minors usually require an age verification process. Examples include social media, gaming, gambling, dating, e-commerce for age-restricted goods, alcohol and tobacco, delivery services, fintech, and adult content.
What are the characteristics of the best age verification software?
Age-checking platform should be technically accurate, robust, reliable, and fair. It should use a risk-based waterfall approach that starts light and steps up only when needed, with privacy by design and audit-ready records.

 Explore Now
Explore Now













