Know Your Patient (KYP) | Significance in Fighting Patient Identity Theft & Scams

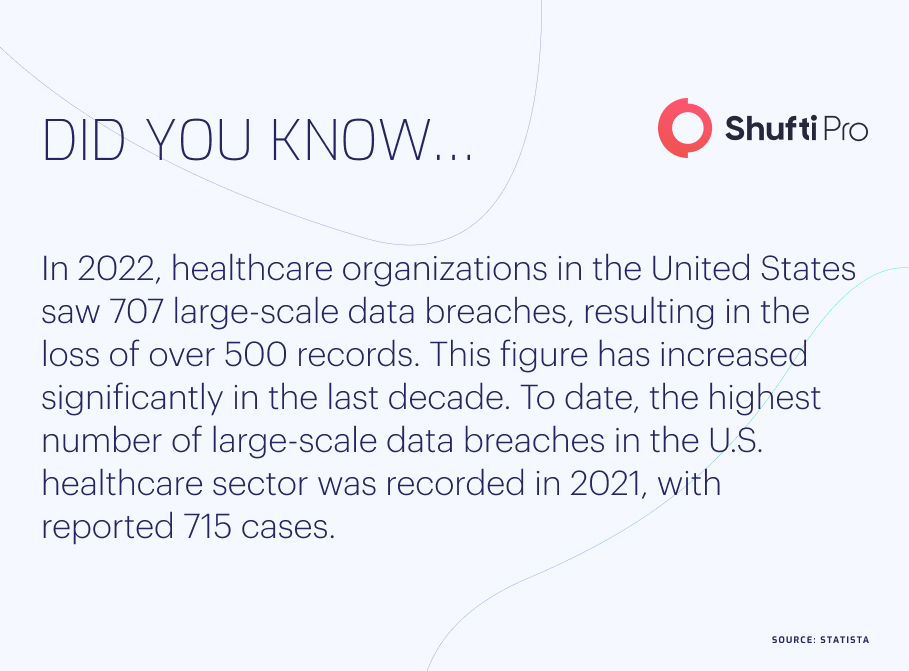
The global medicare industry is a common target for fraudsters looking to gain access to patients’ sensitive information, intending to commit insurance fraud, medical identity theft, or manipulate public health programmes. This alarming situation is an eye-opener for healthcare centres and organisations to remain diligent in verifying their patients, ensuring secure data storage and efficient management of digital procedures. In 2022, nearly 707 healthcare data breaches were recorded, affecting 52 million patients in the US. These emerging risks associated with the industry and the patients have led organisations to embrace know your patient compliance solutions.
As the healthcare industry is massive and complex at the same time and requires dealing with highly sensitive information, it’s crucial for them to carry out proper due diligence procedures whilst ensuring secure data management.
What is Medical Identity Theft?
Medical identity theft refers to unauthorised or fraudulent access of victims’ or healthcare professionals’ personally identifiable information, such as identity numbers, insurance information, and other records to illegally avail Medicare benefits. Medicare fraud comes in multiple forms, including:
- Fraudulent Medical Billing: Fraudsters use stolen medical documents or information to claim bills from insurance companies for fictitious or unnecessary healthcare services, prescriptions, or equipment.
- False Referrals: Usually, identity fraudsters gain access to healthcare professionals’ personally identifiable information to use them to refer patients for additional medicare services.
- Fictitious Healthcare Services: Perpetrators use legitimate patients’ identities to create forged documents regarding medical treatment and services that were never availed.
What puts Patient Data at Risk?
Medicare records and patients’ personally identifiable information contain a lot of sensitive data that can be used for illicit gains. In past years, medical records have been exposed to increased risk of identity theft and other forms of crimes. According to the key finding by HIPAA Journal, over 4,000 medicare data breaches between 2009 and 2022 involved more than 500 patient records.
Following are some of the reasons why the number of data breaches is increasing:
- Digitisation of Health Records: Due to the global digitistion, paper records are no longer in use as they were burdensome to handle, manage, and transmit. With the healthcare shift to fight the first world, the industry has now widely been using digital record-keeping, increasing the risk of data breaches and unauthorised access, leading to identity theft and other rising crimes.
- Increasingly Concentrated Healthcare Organisations: In past years, the healthcare industry globally has become increasingly concentrated due to mergers and acquisitions. This has ultimately increased the number of medicare records under fewer systems, which means one data breach can potentially impact millions of patients simultaneously.
- Advantage of Online Healthcare Services: Due to the pandemic, conventional medicare services have shifted to digital health and telehealth facilities. To access healthcare, patients must create accounts on online platforms through which they need to schedule their appointments or get online prescriptions. Unfortunately, each new account opening paves an opportunity for fraudsters to commit fraud.
Who is Affected by these Risks?
Patients and Beneficiaries: Individuals who become the victims of identity theft face financial consequences, disruption in healthcare facilities, and more. Other than this, they also experience challenges in clearing their names and resolving criminal activities.
Healthcare Providers: Medicare service providers, including health professionals who are the prime targets of fraudsters seeking to use their identities or credentials to bill for unauthorised services and prescriptions. In case of identity theft, healthcare providers can face legal actions, reputational damages, and even termination of licence.
Health Insurance Companies: insurance firms are at high risk of paying criminals for bogus claims resulting in identity theft, leading to increased victim premiums.
Government Healthcare Programs: Public healthcare programs are highly vulnerable to criminal activities, bogus claims, and more, resulting in the loss of millions of taxpayer dollars and the diversion of finance away from legitimate medicare needs.
Credit Reporting Agencies: These authorities may receive reports of medical collection notices and other healthcare crime activities, including patient identity theft, which ultimately affects victims’ credit reports.
What is Know Your Patient (KYP)?
Know your patient is a catch-all phrase that closely relates to the financial industry’s Know Your Customer kyc compliance, which mandates businesses to identify customers whilst ensuring due diligence procedures. However, there are obvious parallels, such as data protection and privacy requirements, risk of fraud, reliance of multiple entities on third-party vendors, different data collection requirements, and much more. In KYP, healthcare service providers need to carry out customer due diligence procedures to determine the risks they pose whilst ensuring a transparent, patient-friendly KYP journey.
Having this in mind, patient identity verification is a simple yet powerful application to fast-track digital healthcare services whilst eliminating the risk of identity theft, etc.
How Does KYP Work?
Following is the precise overview of know your patient verification process:
Initial Verification:
This is the first stage when a patient interacts with the digital health service provider. During onboarding, a patient’s personally identifiable information, including name, date of birth, insurance number, and identity card number, is gathered. The collected data is further cross-matched with the government-issued verification documents whilst screening identities against sanction lists, financial crime databases, and more.
Initial patient screening holds utmost significance, especially to restrict fraudsters from exploiting digital healthcare services.
Ongoing Verification:
When verified patients interact with the platform, their identities should be re-authenticated to ensure risk-free operation. This is accomplished using the same methods that were used in the initial screening. However, in high-risk entities, businesses need to incorporate more streamlined procedures. One such example is facial bio authentication, in which a patient is asked to take a selfie in real-time to prove their authenticity.
Are KYP Checks Mandatory?
Healthcare organisations as well as medicare professionals must conduct know-your-patient checks to ensure legitimate patient onboarding whilst mitigating emerging risks of medical identity theft and other rising scams. Without rigid KYC verification checks, digital healthcare service providers can experience data breaches, ultimately leading to financial loss, reputational damages, and hefty fines.
Here are some of the KYP compliance obligations:
United States: In the US, the Health Insurance Portability and Accountability Act (HIPAA) is the primary body that establishes and enforces KYP requirements, aiming to secure patients’ personally identifiable information from data breaches and other forms of crimes, including identity theft. However, HIPAA doesn’t fully obligate healthcare service providers to verify patients’ identities, but it does require them to implement administrative measures to ensure data privacy remains intact.
United Kingdom: In the UK, the General Data Protection Regulation (GDPR) and the Data Protection Act 2018 (DPA 2018) regulate and oversee the data privacy protocols, information processing, storing and managing measures, including medical records. Under this law, all healthcare organisations operating in the country need to ensure the secure processing of medical information and this may also involve patient identity verification.
Europe: across European Union member countries, the GDPR sets the laws and standards for data privacy and protection, including healthcare data. Medicare service providers operating in the EU need to ensure adherence to GDPR compliance whilst ensuring data confidentiality, integrity, and availability of personally identifiable information. This is the reason why GDPR emphasises the significance of integrating or developing strict data protection strategies, which also include knowing your patient checks.
Know Your Patient with Shufti
Securing patients’ information and data privacy rights has become a global concern, and increasing data breaches require healthcare organisations to implement automated, fool-proof know-your-patient verification solutions. Shufti, a pioneer in identity verification solutions, helps healthcare service providers across 240+ countries and territories fast-track and automate KYP procedures. With our company, your business can cut down on the rising cost of compliance, eliminate the risk of medicare crimes, and onboard patients swiftly – all whilst staying compliant with data protection and privacy laws.
Want to automate your patient verification procedure with Shufti?

 Explore Now
Explore Now













