Know Your Patient | Secure Patient Onboarding and Preventing Healthcare Fraud

- 01 What is Know Your Patient (KYP)?
- 02 Why is KYP Essential for the Healthcare Sector?
- 03 Challenges in KYP Onboarding
- 04 Developing a KYP Programme: Steps to Onboard Patients Securely
- 05 Is Know Your Patient Check a Regulatory Requirement?
- 06 The Benefits of Know Your Patient Checks
- 07 Want to Automate Your Know Your Patient Process?
Technology advancement, automation, and digitisation have paved the way for unprecedented growth within the healthcare sector. Using artificial intelligence and machine learning, manual human effort in the Know Your Patient process is removed, and onboarding can take place in real-time, virtually in seconds.
The increase in healthcare transformation has brought unprecedented data breaches and scams. According to a report, Medicare, on a daily basis, processes $4.5 million in claims. Despite the fact that laws have been enacted to reduce them, it will not stop anytime in the near future.
Healthcare crime not only includes data breaches and financial crimes; it also involves identity theft. The FTC received 27,821 medical identity theft reports in 2022. In July 2023, 11 million HCA patients’ data from over 24 states had been exposed in a data breach. The dataset had 27 million rows, including patients’ personal information and visit records.
What is Know Your Patient (KYP)?
Know Your Patient (KYP) is derived from Know Your Customer (KYC), which healthcare institutions use to verify their patient’s identities and prevent medicare crimes. The healthcare industry has seen a surge in scams requiring modern technology and complete compliance solutions. In this situation, Know Your Patient management comes in handy. The healthcare industry has adopted KYP processes to address the unprecedented surge of prescription and insurance fraud, along with verifying patients’ identities as well as onboarding them.
Why is KYP Essential for the Healthcare Sector?
The healthcare sector has seen exceptional growth in medical-related fraud, prescription forgery, patient identity theft, insurance scams, etc. Advanced technology implementations like artificial intelligence, machine learning, and verification solutions, including e-IDV, and document verification, are essential to prevent health sector fraud. To understand the importance of KYP solutions in healthcare, it is essential to understand the global scams and fraud it faces.

Online identity verification systems enable hospitals, pharmacies, and laboratories to ensure that sensitive health data, reports, or prescriptions are delivered to the correct patient and not an impostor. Furthermore, an appropriate approach can really increase patient service quality and efficiency.
Challenges in KYP Onboarding
Onboarding patients securely, maintaining the reports, and ensuring no imposter has access to any of them seems like an easy task but a daunting thing to do. Whilst onboarding the patient, there is a chance of the other party being a fraud and using a stolen identity to access the patient’s report, prescription, data, or insurance. For this reason, the KYP process helps organisations overcome the following challenges:
- Securely onboarding the patient
- Verifying the patient’s identity during every visit
- Protecting sensitive data from the imposter
- Securely updating the patient data
- Protecting the company’s reputation
- Staying compliant and keeping compliance updated
- Prevent data breaches or other fraudulent and criminal activity
Employing verification in healthcare is unavoidable since it involves various parties with varying data requirements, such as hospitals, doctors, pharmacies, government agencies, etc. The main challenge arises in verifying and securing the patient’s identity when a single patient is enrolled in multiple healthcare institutions due to a particular medical condition and is receiving extensive medical care. Under such circumstances, healthcare sectors must update patients’ data effectively whilst remaining compliant.
Developing a KYP Programme: Steps to Onboard Patients Securely
Know Your Patient identification processes can be automated. Long gone are the days when onboarding was done by verifying the patients’ information from the registers and manually screening them. With technological advancement, the healthcare sector can securely verify and onboard patients. The process includes four steps to onboard the patient ID:
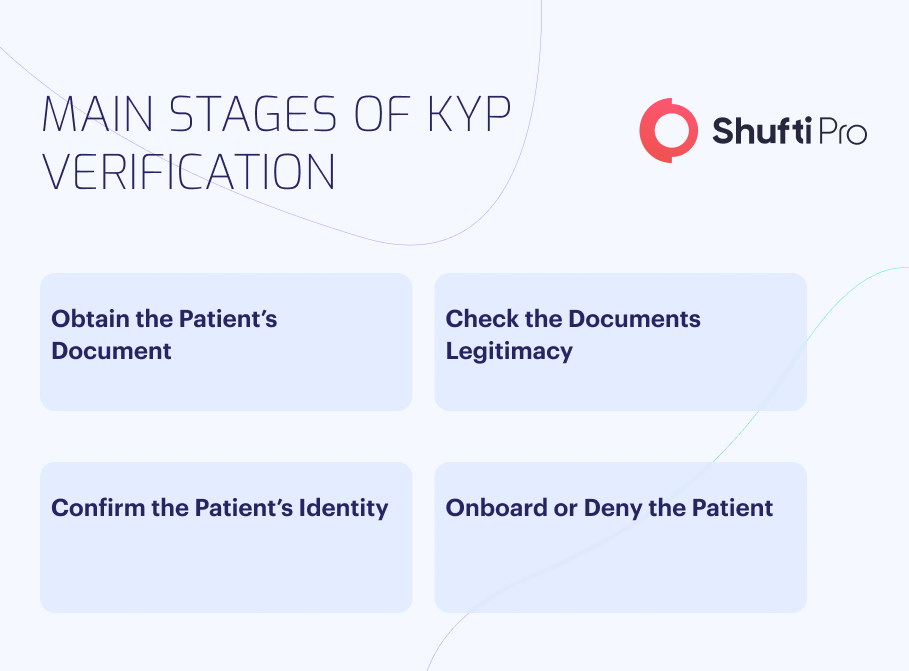
Healthcare institutes must integrate the onboarding and verification processes into their websites, mobile apps, or portals to securely onboard patients. After integration, the patient will be asked to create a profile online and will be asked to provide a government-issued document, including an ID, passport, driver’s licence, certificate, etc. Once the account is created, the document’s legitimacy is verified against the government and private databases. The patient account is created or denied once the document’s legitimacy is confirmed. The process doesn’t stop with the acceptance and rejection. If the patient is onboarded, when they try to access their data through biometric or verification checks, their identity will be validated, and access will be granted or denied. However, the patient information and data will be updated regularly to ensure security and compliance.
Is Know Your Patient Check a Regulatory Requirement?
To prevent the possibility of cyberattacks and potential data breaches, hospitals, laboratories, pharmacies, as well as other healthcare professionals have to screen their patients against KYP checks. Such attacks and data breaches increase the risk of identity theft or fraud. The healthcare industry must comply with industry regulations to avoid identity fraud, data scams, financial losses, and hefty fines. The US National Enforcement Action charged 78 individuals with $2.5 billion in healthcare fraud in June 2023. However, every country has its own healthcare regulatory bodies. Learn more about the US, EU, and UK compliance requirements and regulations.
United States
Every healthcare industry in the United States (US) must comply with HIPAA. The Health Insurance Portability and Accountability Act (HIPAA) is a federal regulatory standard outlining protecting health information’s lawful use and disclosure. However, HIPAA doesn’t set identity verification rules for patients but necessitates that the healthcare sector take precautionary steps to prevent data breaches and implement administrative safeguards to ensure the data confidentiality and integrity of Protected Health Information (PHI).
Europe
Across the European Union (EU), the General Data Protection Regulation (GDPR) sets the data protection regulations. Healthcare organisations in the EU must follow the GDPR’s guidelines, which include protecting the privacy, integrity, and accessibility of personal data. As a result, the GDPR emphasises the necessity of implementing adequate technical and organisational checks to protect personal data. To comply with the GDPR regulations, the healthcare sector must implement KYP checks to verify patient identity, onboard them, and protect healthcare data.
United Kingdom
Know Your Patient in the United Kingdom is governed by the Data Protection Act 2018 (DPA 2018) and GDPR. Both regulatory bodies govern healthcare laws and data processing, including health information. “Data protection principles” ensure that all persons handling personal data follow strict guidelines and that it is used fairly, legally, and transparently.
The Benefits of Know Your Patient Checks
Automated Know Your Patient verification detects the identity in seconds and assesses the risk or fraud associated with it. The process not only saves manual hassle or time but is also simple, budget-friendly, and easy to use for patients. A few benefits of automated Know Your Patient checks include the following:
Sensitive Data Protection
Conducting Know Your Patient checks is crucial for the healthcare industry as it ensures patient data protection whilst helping them stay compliant. With advanced KYP solutions, healthcare sectors can ensure that data is protected and the actual owner has access to the information that is beyond scammers’ and imposter’s access.
Fraud Prevention and Reduction
The data access should only be provided to the patients, staff, and other medical institutes (in cases of rare diseases and if multiple entities are involved). Ensuring that the data is only accessible from reliable sources and away from imposters or scammers is necessary. KYP checks to ensure that access is granted to the right individuals and entities. This will prevent and reduce the occurrence of fraud.
Ensure Accuracy
Know Your Patient checks utilise the advanced OCR technologies that ensure that extracted information is accurate. Other than that, advanced technologies ensure that the provided information is not forged or faked in real time. The KYP process saves time, minimises manual efforts, and reduces human errors; resulting in accurate results.
Reduce Waiting Time
Previously, KYP checks were conducted manually, taking weeks or even months to verify the information. This results in delays and fraudulent activities because the crime had already been committed by the time the identity was being verified. By implementing advanced KYP checks from the right provider, the healthcare industry can reduce the turnaround time and efficiently onboard patients. This saves time for staff and patients during onboarding whilst identity or document verification.
Improve User Experience
Manual KYP processes took weeks and months in the past, resulting in unnecessary delays and patient frustration. By implementing Know Your Patient identifiers, healthcare institutes can reduce unnecessary delays and frustration, improving the overall patient identity verification as well as onboarding experience.
Want to Automate Your Know Your Patient Process?
Shufti is Here to Help
Safeguarding healthcare data and protecting patients’ identities is a global concern, and the sector needs to implement automated KYP processes. Shufti’s identity verification solution automates Know Your Patient processes, making them simple and easy to integrate. With our advanced verification solution, the healthcare sector can combat medicare fraud and securely onboard patients whilst staying compliant.
Shufti’s KYP processes remove friction time, eliminate manual effort, increase transparency, secure sensitive information, and onboard patients seamlessly. Through our AI-powered solution, the patient identity and document are verified in real-time whilst providing the information in less than a thousand seconds with 99.77% accuracy.
Ready to automate KYP processes in seconds whilst staying updated in the regulatory regime?

 Explore Now
Explore Now













