KYC Analysts: The First Line of Defense Against Identity Theft and Fraud

An upsurge in financial transactions has led to heightened money laundering risks and terrorist funding in our current era of widespread digitisation. Consequently, banks and financial institutions must fortify their security measures against such threats. This has led to a global demand for KYC analysts who play a pivotal role as the first line of defence in thwarting financial fraud.
What is KYC?
KYC, an acronym for “Know Your Customer,“ plays a critical role for businesses and financial institutions in verifying the identity of their customers before establishing any business connections. This process is an essential component of Anti-Money Laundering (AML) and Countering Terrorism Financing (CTF) strategies aimed at preventing financial crimes and safeguarding businesses against potential risks arising from money laundering, terrorist financing, fraud, and other illegal activities.
What is a KYC Analyst?
KYC analysts are responsible for verifying customer documents when they open a new account, identifying high-risk accounts, and analysing the policies and processes related to new clients. They also monitor market trends thoroughly and analyse the behaviour patterns of clients within their organisation. Additionally, a KYC screening analyst evaluates new product proposals and conducts risk and compliance assessments for these offerings. Their expertise primarily revolves around AML processes and procedures.
Banks or lending institutions primarily employ these professionals, although they may also find opportunities in other industries like manufacturing, technology, or consulting firms. As per the Bureau of Labor Statistics, the estimated job growth rate of the analysts conducting market research, such as KYC analysts, will reach 19% by 2031. This optimistic outlook is primarily driven by the increasing demand for analysing customer behaviour, enhancing customer satisfaction, monitoring sales trends, and optimising product placement to boost sales and expand customer bases.
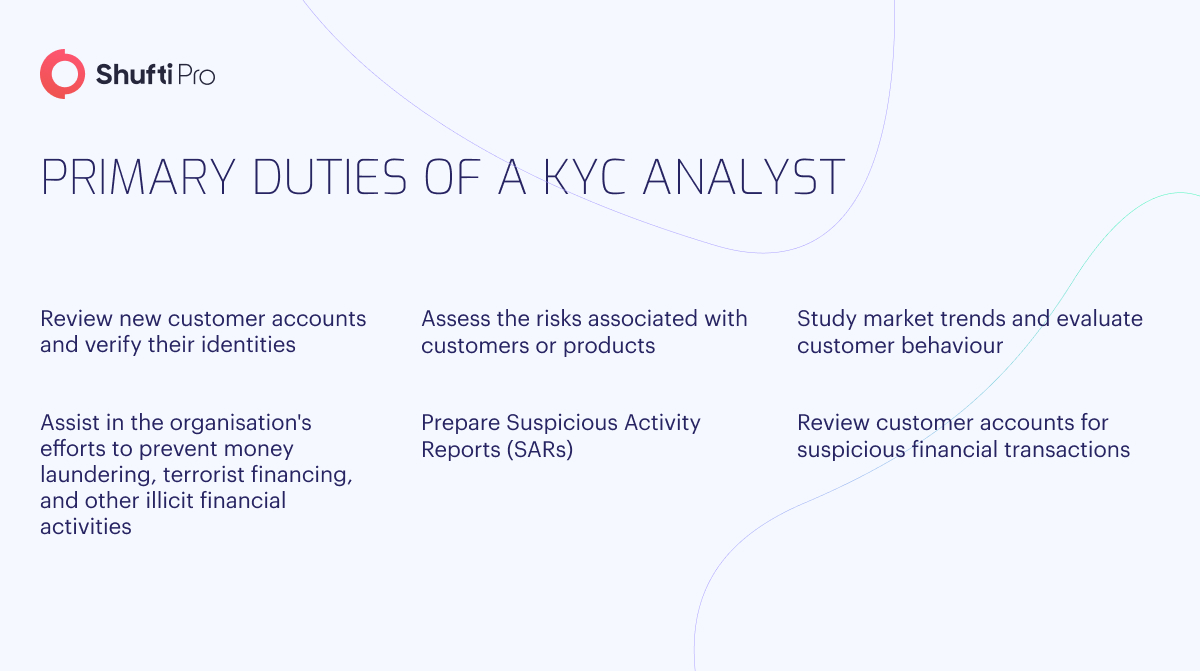
Duties and Responsibilities of a KYC Analyst
The role of a KYC analyst includes doing multi-tasks to ensure great performance in this position. A thorough examination of multiple job postings for KYC analysts reveals a set of duties and responsibilities commonly identified by employers in this occupation.
1. Evaluate New Account Documentation
A KYC analyst conducts in-depth research to authenticate the data provided in the new account documentation. They also check that new account holders aren’t high-risk clients and don’t have any restrictions or engage in illicit activities that could impact their eligibility for opening a new account.
2. Review Policies and Procedures
A KYC compliance analyst analyses the existing procedures and policies related to new client research and account analysis. This scrutiny ensures compliance with regulations and aids in proposing improvements to enhance these processes. Subsequently, they generate comprehensive reports based on their findings and engage with senior management personnel to assess existing procedures and offer potential changes.
3. Analyse Market Trends and Customer Behaviour
By thoroughly checking market trends and monitoring customer behaviour, a KYC onboarding analyst can make decisions and suggestions regarding marketing and customer satisfaction. They regularly collaborate with teams in marketing, production, and customer service, presenting their findings on market trends and seeking opportunities to enhance the overall customer experience and attract new clientele to the company.
The Skills of the KYC Analyst
Possessing strong verbal and written communication skills is crucial for a KYC analyst working in the field of data analysis, research, and reporting. Moreover, a KYC analyst must have time management, above-average decision-making, and organisational abilities. Familiarity with project management and team-building processes, as well as various research methodologies and resources, is essential. Furthermore, a KYC analyst should be detail-oriented, adept at multitasking, and capable of working independently with minimal supervision.
Employers seeking to hire a KYC analyst will also prioritise candidates with the following proficiencies:
- Ability to utilise diverse resources to verify account details and identify potential risks associated with new applicants.
- Proficiency in generating regular reports on market trends and sales, aiding companies in making informed decisions regarding marketing, new product development, pricing, and product placement.
- Skilled in preparing accurate reports, reflecting risk assessments of new clients and complying with internal and external policies related to analysis processes.
How Can Shufti Help?
Shufti, a renowned leader in identity verification and KYC solutions on a global scale offers businesses a comprehensive and automated approach to KYC analysis. Let’s explore how Shufti’s proficient KYC analysts aid businesses in overcoming KYC-related challenges:
- Biometric Face Recognition for Enhanced Security: Shufti employs face detection biometrics, taking KYC analysis to the next level. Customers must provide a selfie or live video alongside their identification documents. The KYC analysts then compare the live image with the photo on the document, adding a layer of security to thwart impersonation attempts.
- Comprehensive AML and PEPs Screening: Shufti’s KYC/AML analysts conduct robust AML checks by scrutinising customer information against global watchlists and databases. Additionally, Politically Exposed Persons (PEPs) screening helps identify high-profile individuals and potential risks associated with their public positions.
- Real-time Risk Assessment: Shufti’s KYC solution incorporates real-time risk assessment, evaluating the overall risk associated with each customer. By analysing transaction behaviour, location, and other pertinent factors, businesses can make well-informed decisions and ensure compliance without hindering legitimate transactions.
- Swift and Seamless Customer Onboarding: One of the paramount benefits of Shufti’s KYC solution is its seamless and rapid customer onboarding process. By verifying identities in real time, businesses can efficiently onboard customers without compromising security. Shufti’s KYC analysts utilise advanced document verification techniques to authenticate identification documents like passports, driver’s licences, and national IDs, ensuring their authenticity and safeguarding against forgery.
Still confused about how a KYC analyst does the job for you?

 Explore Now
Explore Now