User as Owner: Why KYC Software Needs to Respect Privacy Laws?

User as Owner is a simplistic concept that stipulates that all the data of any user collected by businesses and companies via any digital channel for any number of reasons is the property of the user. Privacy Laws form the major portion of the legislation that tends to protect “User as Owner” concept. Now with many KYC software collecting personal information of end-users on behalf of their original customers, it becomes binding on these KYC solutions to also respect the principle of User as Owner. There are a number of advantages for Know your customer services once they start aligning Digital KYC checks with privacy laws and overall user-centric data privacy practices
Users are concerned
Although there are many AML KYC software offering KYC & AML services to a global clientele, hardly anyone has formulated any strategy keeping user grievances in mind. How much digital users are worried about their overall digital privacy are explaine in following charts
When asked what was the most concerning issues about their usage of online services and different digital resources, users mentioned following threats as substantial:
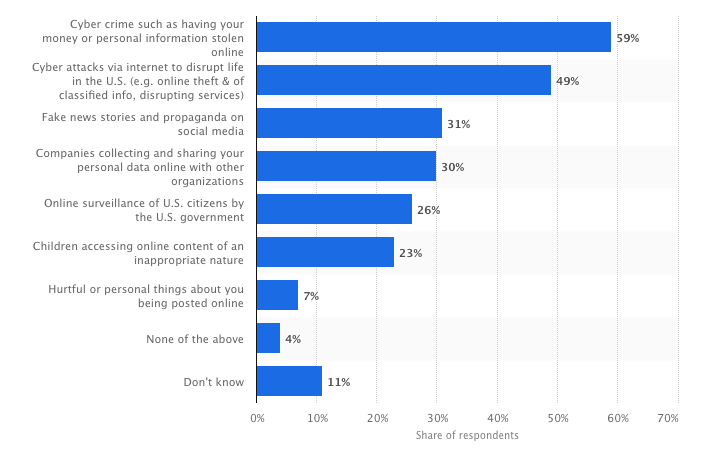
Source: Statista
In another survey, digital users were asked their opinion about different issues related to online privacy and data privacy. As respondents were asked to answer in affirmative in the mentioned survey, here are the figures that show how much importance is given by online users to their digital rights and dataprivacy.
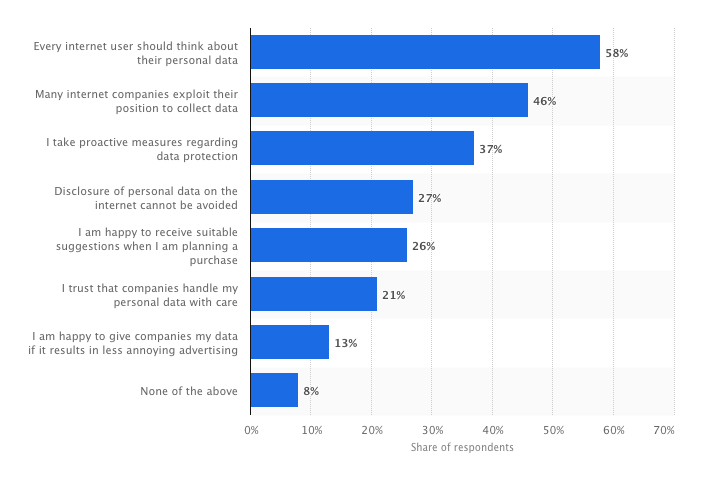
Source: Statista
Now interestingly, 46% of the users said that they consider that many internet companies exploit their position to collect data. Now unlike many other digital services, a KYC solution is not designed to collect information or personal data from users as a source of exploitation. If anything, KYC provider ensures that online marketplace is free of online identity theft, digital scams, and cyber frauds. So it is time for companies offering KYC as a service to their customers, start jumping on User As Owner service.
Better chance with new Customers
There are many businesses that are also looking for KYC validation services that can help them take up this more user-friendly approach of User as Owner. Certainly, a KYC provider, that has no regard for privacy laws or that intends to exploit the personal data collected from end-users will find it hard to earn the trust of a business that wants to adopt transparency in its operations.
So with the focus shifting on customer-centric services and higher regard for user data, a typical KYC provider is better suited to ensure that the collected verification data is not only secured properly but it also is never used for any other purpose, except for verifying the identity of end-user.
On its own part, Shufti cares deeply and fully recognizes “User as Owner” principle. We only collect personal information from end-users on behalf of our customers. All the KYC & AML checks are performed in a fully transparent manner and data is transmitted through PCI certified data transfer channels. Shufti Pro is fully compliant to GDPR, which means that we adhere completely to all the policy guidelines that apply to us during the data processing and verification of end-users’ credentials. We have properly outlined our business practices and all the necessary steps that we have taken to comply with GDPR, in our GDPR compliance policy, that is available on our website.

 Explore Now
Explore Now













