Electronic Identity Verification | Forecasts and Predictions

Identities change as the world goes more digital. As more activities, like banking, socialising, interactions, and shopping, are done online, protecting digital identities is more important than ever. The theft of identities is increasing. Consumers reported losing more than $8.8 billion to fraud in 2022, and to which the FTC received 2.4 million reports of identity theft. These statistics show how crucial it is for businesses to set up trustworthy electronic identity verification systems to swiftly and precisely check that clients are who they claim to be. But how does the actual electronic identity verification procedure look? Why are verification systems so important in this process, and what one should expect in the future?
What is Electronic Identity Verification?
e-IDV, which stands for electronic identity verification, is a remote, paperless method that reduces the costs and traditional bureaucracy required in IDV operations. It also validates identity without requiring a person to physically visit the office or stand in a long queue.
Identity, signature, document, and phishing fraud are all quite common. The development of entirely secure e-IDV processes with no margins for committing these counterfeit offences and associated crimes has been the focus of specialised enterprises.
What Advantages Does Electronic Identity Verification Offer?
The benefits of digital identity verification are numerous. The following are some advantages of using electronic identity verification:
Robust Security
Multi-Factor Authentication (MFA) can help improve overall security by adding additional layers of verification to businesses’ present connections. MFA is regarded as the most trustworthy method of user authentication that guards against unauthorised access and ultimately aids in compliance with particular industry laws. For instance, PCI-DSS regulates the usage of MFA in specific circumstances to prevent unauthorised users from accessing networks.
Mitigates Risks Associated with Human Verification Measures
A person’s photograph on an authorised identity document is compared to the person requesting particular services as part of the traditional techniques for confirming an identity, which solely relies on human verification checks.
These methods are frequently employed to determine if an identity is genuine or fraudulent. Unauthorised experts can quickly get around these verification procedures by changing the documents using a variety of market-accessible technologies. Utilising trustworthy identity verification technology lowers the risks associated with human judgement and minimises human mistakes when confirming a person’s identity.
Increases Customer Satisfaction
Client satisfaction is everything, and if it’s supported by the greatest degree of security, it may completely change the game for any business or service provider in the public or private sector. Potential clients can have user-friendly interactions with the state-of-the-art identity verification system, starting with the onboarding process and continuing throughout the whole consumer life cycle.
Using multi-factor authentication and adaptive risk-based identification, the powerful CIAM (Consumer Identity and Access Management) provides secure authentication and adds many layers of security. Customers can easily authenticate themselves using their social network accounts or a One-Time Password (OTP), which improves the user experience overall.
Guarantees Regulatory Compliance
Businesses must be ready to adhere to compliance standards anytime, anyplace, as privacy regulations expand globally, from GDPR to CCPA and more. Electronic identity verification solutions can assist in supplying proof of due diligence and auditable evidence that businesses are taking steps to carefully verify client data before authorising the opening of accounts or approving transactions.
Creates Long-term Relationships
Customers are more likely to stay loyal and have longer relationships when a procedure is quick, automated, trustworthy, reliable, and secure. On the other hand, ID procedures that take too long, are difficult or hard, keep users in the shadows about their current status in the process, or what will happen next will end or reduce the efforts to build other prosperous or long term connections.
Decreases Risk
The risk associated with accepting transactions that can contain stolen money or money laundering can be decreased with the help of electronic identity verification. Instead of trying to rectify situations that have already happened, businesses may avoid fraud by verifying identities.
Boosts Operational Efficiency
Using automation, reliable electronic identity verification systems can also increase productivity. The correct tools can decrease the need for manual review and boost overall decision-making speed without compromising security by utilising smart data evaluation and comparison algorithms.
Increases Consumer Confidence
Customers often give organisations access to their private and financial information to reduce friction rates and speed up processes. To avoid entering their details or private information over and over when they make a purchase, they allow platforms to remember the stored information.
Nonetheless, it is a known fact that people tend to walk away from businesses and entities that don’t practice data privacy and pay attention to securing the identity of their users. By reducing the need for business personnel to manually check customers’ personal information and guaranteeing the security of the data provided, secure and open-source electronic identity verification services can make customers feel more at ease with the procedure.
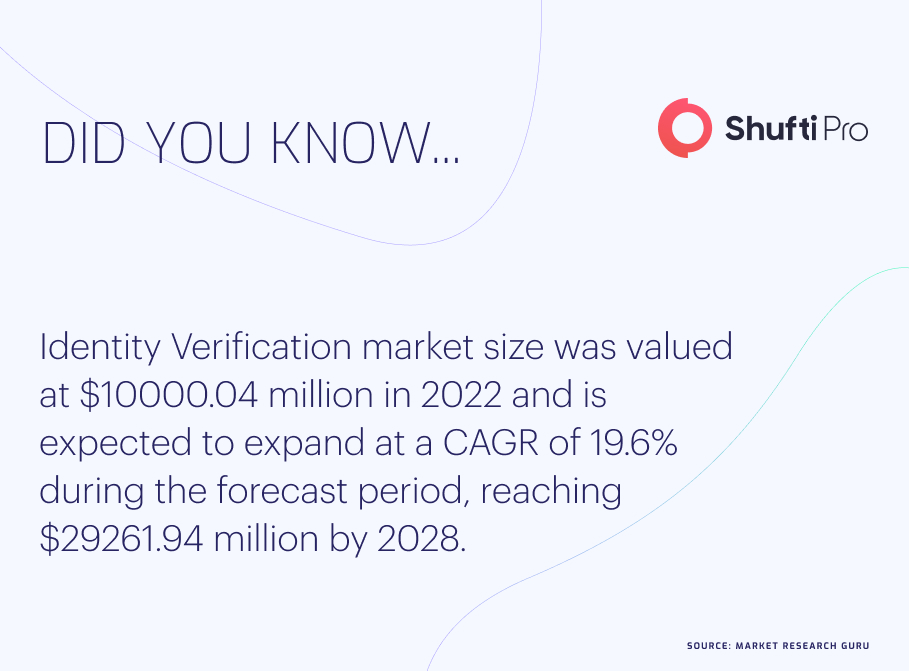
Predictions for 2024
The year will soon come to an end, but the technological industrial revolution will continue. Here are the top electronic identity verification predictions for 2024.
Biometric Authentication will Become Mainstream
Passwords are no longer enough to protect online identities. The use of biometric authentication will increase in 2024 as technical advancements make it simpler and more secure. A more easy and safer user authentication method is provided by biometrics, such as fingerprint and facial recognition. As businesses look to strengthen the security surrounding digital identities, this trend will continue to gain popularity.
Decentralised Identity Solutions Gain Attention
Governments and social media platforms that use centralised identity systems are susceptible to data breaches and cyberattacks. Decentralised identity solutions, which provide consumers more control over their personal data, will continue to gain popularity in 2024 as a result. Users can manage their identity information with the use of decentralised identity solutions, and they can restrict access to it based on a user’s need to know.
Security Frameworks with Zero Trust
In 2024, the usage of zero-trust security frameworks, which treat every user and device as a possible threat until proven secure, will skyrocket. Organisations can safeguard themselves against unauthorised access and data breaches with this security strategy. Organisations can make sure that only authorised people and devices are given access to private information and systems by implementing a zero-trust security framework.
AI and Machine Learning Power Identity Management
Governments and social media platforms that use centralised identity systems are susceptible to hacking and cyberattacks. Artificial intelligence and machine learning will provide consumers more control over their data and will be a trend in 2024. Users can manage their identity information with AI and machine learning identity management tools and ban unidentified users’ access.
Options for Digital ID Verification Systems
As the number of digital transactions increases exponentially, so does the market for identity verification solutions. From manual or traditional IDV solutions to automated all-in-one verification options and more robust ID verification platforms, companies don’t want to choose.
Many companies don’t have the resources to build and maintain their own ID verification infrastructure and prefer not to store Personal Identifiable Information (PII). However, all-in-one solutions aren’t usually customisable enough to handle each company’s unique use cases and customers.
It makes sense to look for solutions that can both suit present needs and adapt to future needs when it comes to electronic verification systems. This includes the capacity to combine and match verification choices, such as submitting a government ID, scanning a database, and using biometric identity, as well as automating crucial procedures and making prompt decisions. Organisations can also profit from systems that can stop known bad actors, spot repeated efforts at verification, and unfold broader fraud rings using surface pattern analysis.
Why Choose Shufti?
Regulations and technology collaborate to redefine electronic identity verification, providing more convenience and security. This changing environment represents a crucial turn towards a future where technology will be more powerful. The ongoing interaction between these elements has the potential to alter the reach of electronic identity verification by striking a balance between innovation and privacy.
Shufti‘s cutting-edge all-in-one e-IDV solution can assist businesses in the swift and precise verification of individuals. By using an online verification solution, businesses can do away with time-consuming paperwork and old traditional KYC procedures. Using centralised e-IDs that are cross-referenced with government databases, remote consumer verification is quick and secure. Shufti values user privacy and uses cutting-edge security tools to safeguard user data. Find out how the future of identity verification will revolutionise remote customer authentication by combining speed, accuracy, and high security. Our solution includes:
- Verification with a unique personal identifier
- No document uploading
- Real-time verification from authorised databases
- Speed up customer onboarding
- 99.77% accuracy rate and verifying identities within seconds
Wondering how to stay updated with the revolutionising eIDV trends whilst maintaining compliance within your budget and time?

 Explore Now
Explore Now













